In today's digitally-driven world, the seamless functioning of network infrastructure has become paramount for businesses to thrive. Adequate monitoring of network activities helps ensure optimal performance, mitigates risks, and safeguards sensitive data. To attain this level of oversight, it is crucial to fine-tune the various settings within the Windows operating system, making use of its robust capabilities.
Streamlining Network Management: A well-configured network monitoring system empowers administrators to identify and resolve issues promptly, minimizing downtime and maximizing productivity. As the digital landscape continues to evolve, tailored settings within the Windows environment can enhance network surveillance, providing comprehensive insights into network traffic, security threats, and resource allocation.
Optimizing Network Efficiency: By customizing Windows settings, system administrators can optimize network performance by efficiently managing bandwidth allocation and improving data transmission rates. This proactive approach enhances network stability and responsiveness, reducing latency and ensuring seamless connectivity.
Harnessing Advanced Security Measures: The prevalence of cyber threats necessitates a robust network security framework. Properly configuring Windows settings enables the implementation of industry-leading security measures. By utilizing built-in features such as firewall settings, secure remote access, and encryption protocols, administrators can fortify their network against potential breaches and unauthorized access.
Step 1: Install Network Monitoring Software
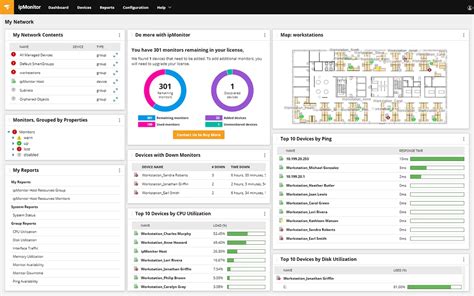
In the initial stage of setting up a network monitoring system, the first step is to install the necessary software for monitoring and managing network activities. This crucial step lays the foundation for effectively monitoring, analyzing, and optimizing a network's performance, security, and reliability.
Start by identifying reliable network monitoring software that suits your specific requirements. Look for software that provides comprehensive features, such as real-time monitoring, traffic analysis, and alert notifications. Once you have chosen the software, follow the installation instructions provided by the vendor.
During the installation process, ensure that all necessary dependencies and system requirements are met. Depending on the software, this may entail checking compatibility with your operating system, hardware specifications, and additional software components. Adhering to these requirements will guarantee smooth installation and optimal performance of the network monitoring software.
Step 2: Establish Network Device Configuration for Monitoring
To successfully implement an effective network monitoring system, it is crucial to properly configure and set up your network devices. This step focuses on establishing the necessary configurations on your network devices, ensuring they can be seamlessly integrated into the monitoring system.
Device Preparation:
Before diving into the configuration process, it is important to ensure that all network devices intended for monitoring are compatible and meet the system requirements. Check for firmware updates or any necessary hardware upgrades, ensuring the devices are capable of providing the required data for comprehensive reporting and analysis.
Network Discovery:
Begin the configuration process by performing network discovery, which involves identifying all devices currently connected to your network. This can be achieved by utilizing network scanning tools or implementing protocols such as SNMP (Simple Network Management Protocol) to gather device information. It is essential to have an accurate inventory of all network assets to effectively monitor and manage the network.
Access Control and Authentication:
Next, establish and configure appropriate access controls and authentication mechanisms to ensure only authorized personnel can access the network devices for monitoring purposes. This may involve implementing strong passwords, enabling multi-factor authentication, or utilizing role-based access control (RBAC) to manage user privileges and permissions.
Performance Monitoring Configuration:
Each network device must be individually configured to enable the necessary performance monitoring capabilities. This typically involves enabling specific protocols, such as NetFlow or SNMP, to collect data related to network traffic, bandwidth utilization, errors, and other key performance indicators. Additionally, configuring thresholds and notifications for proactive monitoring and alerting is crucial to effectively manage potential network issues.
Data Collection and Storage:
Finally, configure the network devices to send the collected monitoring data to the central monitoring system. This may involve configuring data export protocols, such as SNMP traps or syslog, to transmit the data securely. Consider implementing appropriate data encryption mechanisms during transmission to ensure data integrity and confidentiality. Additionally, establish an appropriate data storage solution, such as a network monitoring database, to store and organize the collected data efficiently.
By following these steps and properly configuring your network devices, you will establish a solid foundation for your network monitoring system, enabling comprehensive visibility and efficient management of your network infrastructure.
Step 3: Set Up Windows Firewall to Monitor Network Activity
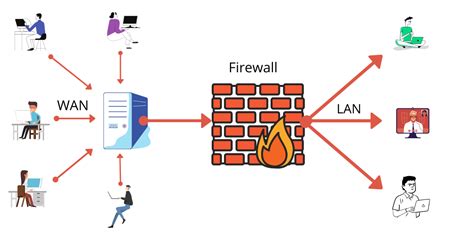
After completing the initial configurations for your network monitoring system, the next step is to ensure that your Windows Firewall is properly configured to allow for effective monitoring of network activity. By configuring the Windows Firewall, you can enable the necessary communication channels and permissions to capture and analyze network traffic.
To begin, open the Windows Firewall settings by following these steps:
- Click on the Start menu, then select "Control Panel."
- In the Control Panel, locate and click on the "Windows Firewall" option.
- Within the Windows Firewall settings, click on the "Allow an app or feature through Windows Firewall" link.
Once you have accessed the Windows Firewall settings, you will need to configure the following:
- In the "Allowed apps and features" section, click on the "Change settings" button.
- Scroll through the list of apps and features to locate your network monitoring system software.
- Check the box next to your network monitoring system software to allow it through the Windows Firewall.
- Click the "OK" button to save the changes.
Additionally, it may be necessary to configure specific ports and protocols within the Windows Firewall to ensure that your network monitoring system can properly capture network traffic. To do this:
- Navigate to the "Advanced settings" section within the Windows Firewall settings.
- Click on the "Inbound Rules" option in the left-hand menu.
- Locate and select the "New Rule" option.
- Follow the prompts to configure the rule based on the specific ports and protocols required by your network monitoring system.
- Repeat these steps for the "Outbound Rules" option as well.
By properly configuring the Windows Firewall settings, you can ensure that your network monitoring system has the necessary access and permissions to effectively monitor and analyze network activity. Regularly reviewing and updating these settings will help keep your network security robust and allow for accurate monitoring of your network environment.
Section 4: Enhancing Windows Performance for Efficient Network Observation
In this segment, we focus on refining the overall functionality of your operating system to optimize its performance capabilities for effective network analysis. By implementing specific adjustments, you can enhance your Windows-based environment to ensure seamless monitoring and observation of network activities without compromising system efficiency. This section will provide valuable insights and recommendations on how to fine-tune your Windows settings.
1. Streamline Background Processes:
By minimizing unnecessary background processes, you can allocate more system resources towards network monitoring operations. Identify and disable non-essential services, applications, and tasks that consume CPU and memory resources but do not contribute to networking analysis. Prioritizing network monitoring programs and allocating higher system priority ensures that crucial tasks receive optimal attention.
2. Optimize Network Adapter Properties:
To maximize network monitoring performance, configure your network adapter settings appropriately. Fine-tuning parameters such as receive and transmit buffers, network packet sizes, and interrupt moderation can significantly impact the capture and analysis of network traffic. Adjusting these properties according to your specific monitoring requirements will optimize data collection accuracy and effectiveness.
3. Utilize Performance and Resource Monitoring Tools:
Windows offers various built-in performance monitoring tools that allow you to track resource utilization and identify potential bottlenecks. These tools enable real-time monitoring of CPU usage, memory consumption, disk activity, and network traffic. Analyzing these metrics helps pinpoint specific areas requiring optimization, ensuring your system is equipped to handle the demands of network monitoring.
4. Implement Power Management Settings:
Power management settings play a crucial role in maintaining system stability during prolonged network monitoring sessions. Adjusting power mode settings to prevent system sleep or hibernation ensures uninterrupted network observation. Selecting optimal power plans can also prevent CPU throttling, enhancing overall performance and responsiveness.
5. Update and Patch the Operating System:
Regularly updating your Windows operating system with the latest patches and security updates is critical for network monitoring performance. These updates address vulnerabilities, improve system stability, and introduce enhancements that boost overall efficiency. Keeping your system up to date safeguards against potential issues that may impact network monitoring capabilities.
Step 5: Secure Your Network Monitoring Solution
Ensuring the safety and protection of your network monitoring system is crucial in order to maintain the integrity and confidentiality of your network data. In this step, we will explore effective strategies for securing your network monitoring solution.
| 1. Implement Access Controls | Granting appropriate access levels to users and administrators is essential in preventing unauthorized access to your network monitoring solution. Utilize strong passwords, two-factor authentication, and role-based access control to safeguard against potential security breaches. |
| 2. Regularly Update and Patch | Staying up-to-date with the latest software versions and security patches is crucial to address any known vulnerabilities and ensure the overall security of your network monitoring solution. Regularly check for updates and apply patches promptly to protect against potential security risks. |
| 3. Encrypt Network Traffic | Encrypting network traffic is essential in protecting sensitive information from being intercepted or tampered with. Implement secure protocols, such as SSL or TLS, to encrypt communications between your network monitoring solution and other devices on the network. |
| 4. Enable Firewall and Intrusion Detection Systems | Deploying a firewall and intrusion detection systems (IDS) adds an extra layer of security to your network monitoring solution. Configure the firewall to allow only necessary network traffic and enable IDS to detect any suspicious activity and anomalies in real-time. |
| 5. Regularly Monitor and Audit | Continuously monitoring and auditing your network monitoring solution allows you to identify and address any security issues or potential vulnerabilities. Implement logging and alerting mechanisms to keep track of user activities and detect any unauthorized access attempts. |
By following these steps, you can establish a secure network monitoring solution that protects your network from potential threats and ensures the confidentiality, integrity, and availability of your network data.
How to monitor your network for free with Zabbix
How to monitor your network for free with Zabbix by CryptoTech 201,652 views 3 years ago 14 minutes, 29 seconds
How To Install Free Network Monitoring Tool(Cacti) in Windows 10
How To Install Free Network Monitoring Tool(Cacti) in Windows 10 by Tricknology 28,689 views 2 years ago 7 minutes, 23 seconds
FAQ
What is a network monitoring system?
A network monitoring system is a software or hardware tool that allows users to monitor and manage their computer networks. It helps to identify and resolve network issues, track network performance, and ensure network security.
Why is network monitoring important for Windows?
Network monitoring is crucial for Windows because it allows administrators to track network performance, detect and resolve issues, and ensure the security and stability of the network. It helps to identify potential bottlenecks, monitor bandwidth usage, and identify any unauthorized access or security breaches.




