As modern systems become increasingly complex, the need for robust logging solutions has become paramount. Effective log recording is not merely a mundane task but rather a skillful art that requires finesse and attention to detail. Today, we delve into the depths of syslog, a versatile messaging protocol, and explore how it facilitates seamless log management in the Linux ecosystem.
Embedded deep within the core of every Linux distribution, syslog acts as a silent sentinel, quietly collecting and archiving vital system information. While it may often go unnoticed, this unassuming messaging service holds the key to unlocking a treasure trove of insights. From detecting critical errors to auditing system activity, syslog affords administrators an unparalleled glimpse into the inner workings of their Linux systems.
But what exactly is syslog? At its core, syslog serves as a standardized method for capturing and transmitting system messages, enabling efficient log aggregation across a myriad of devices and applications. Whether it's a critical system event or a routine service status update, syslog diligently captures these messages, providing a rich tapestry of data for post-analysis. Moreover, syslog boasts a modular structure, granting flexibility in customizing logging preferences to meet specific needs.
So, why is syslog the golden standard for log recording in Linux? One of its major advantages lies in its ability to centralize log management. With syslog, system administrators can efficiently gather all relevant log data into a centralized location, simplifying the process of analysis and troubleshooting. Furthermore, syslog promotes compatibility and interoperability, allowing different systems and applications to seamlessly communicate and exchange log messages without language barriers.
Understanding the Importance of Logging and the Role of syslog
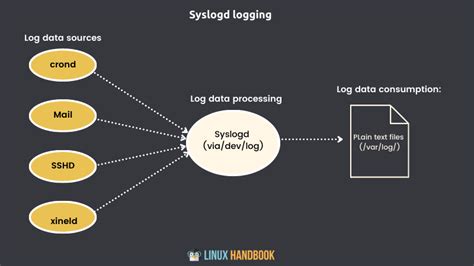
Logging is an essential aspect of system administration as it allows the recording of critical events, activities, and errors for troubleshooting, performance analysis, and security audits. The syslog protocol, widely used in Linux environments, plays a crucial role in managing and aggregating log data.
Logging serves as a digital trail that provides a comprehensive record of system activities, including user actions, system events, and network communications. This documentation offers valuable insights into the operational status, performance, and security of a Linux system.
The syslog protocol, short for system logging, provides a standardized method for gathering and transmitting log messages across a network. It enables the centralized collection and processing of log data from various sources, facilitating easier monitoring, analysis, and storage. By employing syslog, administrators can efficiently manage logs from multiple devices or applications without the need to examine individual log files manually.
Syslog operates based on a client-server model, where the log entries are generated by the sending devices or applications (syslog clients) and then forwarded to a central syslog server responsible for storing and managing the logs. The syslog server uses specific facilities and severity levels to categorize the log messages, allowing better organization and filtering based on their importance and urgency.
Understanding how logging and syslog work together is essential for Linux system administrators, as it provides them with a powerful tool to monitor and maintain the health of their systems more effectively. By harnessing the capabilities of syslog, administrators can gain deeper insights into system behavior, detect anomalies, and respond promptly to potential issues or security threats.
Configuring syslog as a reliable tool for storing logs
In this section, we will explore the process of setting up syslog to effectively capture and store important system logs for analysis and troubleshooting purposes. By configuring syslog to act as a robust logging solution, you can ensure the availability and reliability of valuable log data for monitoring and auditing.
Firstly, we will discuss the steps involved in configuring syslog to receive and record logs from various sources within your Linux environment. This includes understanding the importance of log sources, such as applications, services, and system components, and how to accurately identify and configure them.
Next, we will delve into the customization options available in syslog, allowing you to tailor the logging behavior to meet your specific requirements. This may include setting log levels, defining log formats, and implementing filters to categorize and prioritize logs based on their relevance and severity.
In addition to configuration, we will also explore best practices for managing and organizing log files within syslog. This involves establishing a proper log rotation strategy to prevent disk space issues, implementing mechanisms to archive and compress older log files, and securely storing logs to protect them from unauthorized access.
Lastly, we will discuss the importance of regularly monitoring and reviewing syslog logs to identify anomalies, troubleshoot issues, and gather valuable insights. We will provide guidance on leveraging syslog utilities and tools for efficient log analysis, including real-time monitoring and log visualization techniques.
By following the techniques and recommendations outlined in this section, you will be able to establish a reliable syslog setup that effectively captures and stores crucial log data, enabling you to proactively manage and secure your Linux environment.
Configuring syslog for efficient log management
Ensuring effective log management is essential for maintaining the stability and security of your Linux system. One powerful tool that aids in this process is syslog. By properly configuring syslog, you can efficiently collect, store, and analyze log data, enabling you to quickly identify and troubleshoot potential issues.
In this section, we will explore the various steps involved in configuring syslog for effective log management. We will discuss the importance of setting up log filtering and forwarding rules, highlighting the significance of defining specific log levels and destinations. Additionally, we will delve into the concept of log rotation and how it can prevent log files from becoming excessively large and difficult to manage.
Furthermore, we will delve into the configuration of syslog servers and clients, providing insights into the process of setting up centralized log management. This approach allows for simplified log monitoring and analysis, making it easier to identify patterns and trends across multiple systems.
Throughout this section, we will showcase best practices and provide practical examples to illustrate the concepts. We will also address potential challenges and offer solutions to ensure smooth implementation and utilization of syslog for effective log management on your Linux system.
By the end of this guide, you will have gained a solid understanding of how to configure syslog to optimize log management, allowing you to leverage log data effectively to enhance the overall performance and security of your Linux environment.
Choosing the appropriate log levels for your system
In the realm of system logging, selecting the appropriate log levels holds paramount importance in ensuring effective monitoring and troubleshooting processes. Log levels serve as a crucial classification mechanism, enabling system administrators to prioritize and filter log messages based on their relevance and severity. This article will delve into the significance of log levels, explore the different levels available, and provide guidance on choosing the most appropriate levels for your specific system.
| Log Level | Description |
|---|---|
| Emergency | Denotes system-wide catastrophic failures requiring immediate attention. |
| Alert | Indicates conditions that should be addressed urgently to prevent further damage. |
| Critical | Signifies critical conditions that may lead to system instability or a loss of functionality. |
| Error | Highlights errors resulting in the failure of specific tasks or components. |
| Warning | Comprises potentially harmful situations that may impact the system's performance or functionality. |
| Notice | Indicates normal but significant events requiring attention and potential investigation. |
| Informational | Helpful messages that provide insight into the system's operation. |
| Debug | Provides detailed information for debugging purposes, typically used in development environments. |
Choosing the appropriate log levels entails evaluating the priorities and requirements of your system. Determining the criticality of different events, understanding the potential impact on system performance, and considering the level of detail necessary for troubleshooting are all essential factors. Finding the right balance between generating sufficient logs for analysis while minimizing log volume is crucial for efficient log management.
Additionally, it is essential to establish a clear log level policy that aligns with your organization's best practices. This policy should outline the responsibilities of system administrators, define the log levels to be used for different types of events, and ensure consistency across the system.
By selecting the appropriate log levels, system administrators can streamline the monitoring and troubleshooting processes, enabling faster identification and resolution of critical issues. A well-defined log level strategy contributes to the overall stability, reliability, and security of a system, promoting efficient and effective log recording and analysis.
Filtering and sorting log messages with syslog
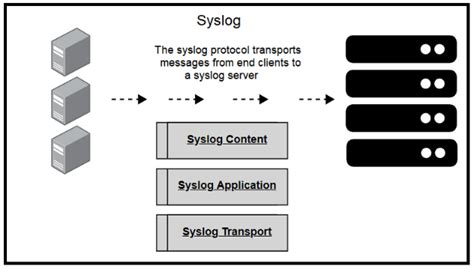
The ability to filter and sort log messages is crucial in managing and analyzing system logs effectively. In this section, we will explore various techniques and strategies to apply filters and sorting mechanisms to syslog, enabling administrators to focus on specific log events, troubleshoot issues, and gather valuable insights.
Filtering allows us to narrow down the logs to a specific criteria, such as time range, severity level, specific applications or services, or specific keywords. By applying filters, we can reduce the noise and focus on the relevant log events that require our attention.
Sorting log messages helps in organizing the log data in a structured manner. With syslog, we can sort logs based on different attributes, such as timestamp, severity level, hostname, or application name. Sorting logs allows us to easily identify patterns, detect anomalies, and identify trends over time.
In this section, we will delve into the various filtering techniques available in syslog, including filtering by severity level, facility, and keywords. We will also explore the sorting capabilities of syslog and how to sort logs based on different attributes. Additionally, we will discuss the configuration options and best practices for utilizing these filtering and sorting features effectively in syslog.
By mastering the art of filtering and sorting log messages with syslog, administrators can streamline their log analysis process, significantly improve troubleshooting efficiency, and gain valuable insights for system optimization and security enhancement.
Advanced strategies for leveraging syslog capabilities
In this section, we will explore innovative techniques to harness the full potential of syslog, the powerful log management tool in a Linux environment. By adopting these advanced tactics, you can enhance the efficiency and effectiveness of log recording and analysis, gaining valuable insights into system performance, security incidents, and troubleshooting scenarios.
Elevating log filtering precision:
Discover how to finely tune log filtering mechanisms to extract the most relevant information from syslog entries. Explore techniques such as leveraging wildcards, regular expressions, and negation operators to target specific events or eliminate noise. These advanced filtering strategies enable you to focus on critical log data, significantly improving the accuracy and efficacy of your analysis.
Unleashing the power of complex log parsing:
Delve into the intricacies of parsing complex log messages in syslog. Uncover techniques for handling nested structures, multi-line logs, and unconventional data formats. Learn how to utilize sophisticated parsing libraries and custom scripts to extract valuable insights and transform unstructured log data into a rich source of actionable intelligence.
Implementing syslog optimization techniques:
Enhance the performance and scalability of your syslog infrastructure by implementing various optimization techniques. Discover the benefits of load balancing, distributed syslog architectures, and log rotation strategies. By fine-tuning the configuration and deploying efficient syslog infrastructure, you can ensure seamless log recording and storage, even in high-volume environments.
Integrating syslog with centralized log management systems:
Explore advanced syslog integration techniques to seamlessly connect syslog with centralized log management systems. Learn how to stream syslog data to tools like Elasticsearch, Logstash, or Graylog for advanced log analytics, real-time monitoring, and long-term log storage. By leveraging the capabilities of centralized log management systems, you can unlock comprehensive log analysis and improve overall system visibility.
Mastering these advanced techniques will empower you to maximize the value of syslog as a log recording and analysis tool, taking your Linux log management capabilities to new heights.
Creating custom log files with syslog

In the realm of managing and organizing system logs, syslog plays a crucial role. While syslog is commonly used for recording system logs in Linux, it also offers the capability to create custom log files tailored to specific needs. This section discusses how to customize syslog configuration to generate personalized log files, empowering users to efficiently track and manage log data without relying solely on default logging mechanisms.
| Table: | Contents |
|---|---|
| 1. | Understanding the syslog configuration file |
| 2. | Creating custom log file entries |
| 3. | Defining log levels and priorities |
| 4. | Assigning specific facilities to custom log files |
| 5. | Configuring log rotation for custom log files |
| 6. | Verifying and troubleshooting custom log file creation |
By delving into the syslog configuration file, users gain a deeper insight into the different parameters and directives that can be modified to create custom log files. Understanding how to define log levels and priorities enables users to categorize log entries based on their importance. Moreover, assigning specific facilities to custom log files ensures that log data from different sources can be efficiently stored in separate files.
To prevent log files from growing excessively large, configuring log rotation becomes crucial. This section explores various techniques for configuring log rotation specifically for custom log files, ensuring that log data is consistently managed and archived effectively.
Finally, this section provides methods for verifying and troubleshooting the creation of custom log files, allowing users to validate their syslog configurations and ensure that the desired log entries are successfully recorded in the specified log files.
Utilizing syslog for transmitting logs to remote servers
In the realm of log management, a crucial aspect is the ability to transmit logs from local systems to remote servers efficiently. This facilitates centralized log monitoring, analysis, and archiving. This section explores the practical application of syslog as a mechanism for sending logs to remote servers.
As part of the syslog protocol, a configuration can be implemented on Linux systems to forward log messages to a remote syslog server. By leveraging this capability, administrators can consolidate and manage logs from multiple sources in a centralized location, simplifying the troubleshooting and analysis process.
| Benefits of using syslog for remote log transmission |
|---|
| 1. Centralized log storage: |
| Syslog enables the collection of logs from various systems into a single location, making it easier to access and analyze the data. |
| 2. Reduced network traffic: |
| By consolidating logs on a remote server, the volume of log data transmitted over the network can be minimized, optimizing network performance. |
| 3. Enhanced security: |
| Syslog allows logs to be securely transmitted over encrypted protocols, ensuring the integrity and confidentiality of sensitive information. |
| 4. Scalability: |
| With syslog, it is possible to scale log storage separately from individual systems, accommodating an expanding log volume without impacting the performance of local systems. |
In the subsequent sections, we will delve into the configuration details and considerations for setting up syslog to transmit logs to remote servers. By harnessing this capability, organizations can effectively manage log data, improve troubleshooting efficiency, and enhance overall system security.
[MOVIES] [/MOVIES] [/MOVIES_ENABLED]FAQ
What is syslog in Linux?
Syslog is a standard logging protocol that allows Linux systems to collect, store, and manage log messages from various software and devices.
How can I configure syslog in Linux?
To configure syslog in Linux, you need to modify the configuration file located at /etc/rsyslog.conf. You can specify the log files, their format, and destinations in this file.
What are the different log levels in syslog?
Syslog defines 8 different log levels: emergency, alert, critical, error, warning, notice, info, and debug. These levels indicate the severity of log messages and help in prioritizing the events.
Can I send syslog messages to a remote server?
Yes, you can send syslog messages to a remote syslog server by specifying the server's IP address or hostname in the configuration file. This allows centralized log storage and analysis.
How can I filter and search syslog messages?
You can filter and search syslog messages by using tools like grep and awk. These tools allow you to specify criteria such as log level, time range, or specific keywords to narrow down the search results.
What is syslog in Linux?
Syslog is a standard logging system in Linux that allows various programs and devices to generate log messages. It helps in recording and managing logs for system monitoring and troubleshooting.




