Delving into the depths of Linux's network capabilities, we embark on a journey that unveils the intricate web of connections and communication that underlies the digital realm. Igniting the flames of curiosity, we navigate this vast landscape armed with nothing more than the command line interface.
With every keystroke, we unlock a door to a world of connectivity, where networks converge and data flows like a chorus of harmonious bytes. Being masters of our virtual domain, we harness the power of the command line to configure, troubleshoot, and optimize the labyrinthine networks that intertwine at the heart of Linux.
Leaning on a delicate balance between precision and creativity, we dip our fingers into the rich palette of command line tools. Armed with the sword of knowledge, we traverse the realms of IP addresses, subnets, and routing, orchestrating a symphony of network commands that shape the very fabric of digital communication.
In this article, we seek to demystify the enigma that is Linux networking, breaking it down into bite-sized chunks of information. With an arsenal of command line techniques at our disposal, we empower ourselves to conquer any networking challenge that comes our way, navigating the ever-changing seas of connectivity with elegance and finesse.
Understanding the Fundamentals of Networking

In this section, we will explore the essential concepts and principles that form the foundation of networking. Through a series of discussions and examples, we will delve into the intricacies of how devices communicate and exchange information over a network.
By gaining a comprehensive understanding of key networking terminologies and protocols, you will be equipped with the knowledge necessary to effectively navigate the world of network administration and troubleshooting.
| Topics Covered: |
|---|
| 1. Networking Protocols |
| 2. IP Addressing and Subnetting |
| 3. Routing and Switching |
| 4. Domain Name System (DNS) |
| 5. Network Security Fundamentals |
| 6. Network Troubleshooting Techniques |
By familiarizing yourself with these fundamental aspects of networking, you will be better prepared to navigate and manipulate networks using the command line in Linux, enabling you to optimize performance, enhance security, and simplify network management processes.
Configuring Network Interfaces in Linux
Setting up and managing network interfaces is an essential task in Linux systems. This section explores the process of configuring network interfaces, enabling you to establish and maintain network connections seamlessly.
Before diving into the configuration details, it's important to understand the significance of network interfaces. Network interfaces act as bridges between a computer and the network it is connected to, allowing the transfer of data between devices. They serve as the entry and exit points for network communication and play a crucial role in establishing and maintaining network connectivity.
Linux provides various tools and commands to configure network interfaces, with each option catering to different requirements and preferences. One of the most commonly used tools is ifconfig, which allows you to view and configure network interface settings. The ip command is another robust utility that provides extensive functionality for managing network configurations.
When configuring network interfaces, you have the flexibility to define various settings such as IP addresses, netmasks, gateways, and DNS servers. These settings are specified in configuration files located in specific directories, such as /etc/network/interfaces or /etc/sysconfig/network-scripts/. Understanding the structure and syntax of these files is crucial for accurate and efficient network interface configuration.
In addition to manual configuration, Linux also supports automatic network configuration through protocols such as DHCP (Dynamic Host Configuration Protocol). DHCP allows network devices to automatically obtain IP addresses and other network settings from a DHCP server, simplifying the configuration process and ensuring consistency across network devices.
- To configure a network interface manually, you can use the ifconfig command followed by the desired options, such as setting the IP address or netmask.
- The ip command provides more advanced functionality for network interface configuration, allowing you to create or remove interfaces, assign IP addresses, set up VLANs, and manage routing tables.
- Configuration files play a crucial role in network interface configuration. They store network settings and are used by various tools and utilities to apply the desired configurations.
- DHCP enables automatic network configuration by allowing devices to obtain network settings dynamically from a DHCP server.
Mastering the art of configuring network interfaces in Linux empowers you with the ability to establish reliable network connections and customize network settings to suit your specific needs. By understanding the available tools, commands, and configuration files, you can confidently set up and manage network interfaces in various Linux distributions.
Navigating and Managing Network Connections
In this section, we will explore the various aspects of effectively navigating and managing your network connections in a Linux environment. Understanding how to interact with and control network connections is essential for efficiently maintaining and troubleshooting your network infrastructure.
One of the key elements of managing network connections is being able to identify and monitor the different devices, interfaces, and protocols that make up your network. By developing a clear understanding of the terminology and concepts surrounding network connections, you can navigate the network landscape more effectively.
Additionally, we will discuss the importance of establishing and configuring network connections correctly. Whether it's setting up a wired or wireless connection, knowing the necessary steps and commands can save you time and prevent potential network issues. We will delve into the key configuration files and command-line tools that enable you to establish and modify network connections.
Furthermore, managing network connections involves troubleshooting and resolving issues that may arise. With the help of various command-line utilities, we'll explore techniques for diagnosing and rectifying problems such as IP address conflicts, DNS resolution failures, and network connectivity errors. Understanding how to effectively troubleshoot network connections is crucial for maintaining a stable and reliable network environment.
Finally, we will cover advanced topics related to network connections, such as network bonding, VLAN configuration, and firewall management. These advanced concepts expand your capabilities in managing and optimizing network connections, allowing you to adapt your network infrastructure to meet evolving requirements.
| Topics Covered in this Section: |
|---|
| 1. Understanding Network Terminology |
| 2. Establishing and Configuring Network Connections |
| 3. Troubleshooting Network Connection Issues |
| 4. Advanced Network Connection Management |
Exploring IP Addresses and Networks
In this section, we will delve into the fascinating world of IP addresses and networks. Understanding these fundamental concepts is essential for anyone working with computer systems and network administration.
Let's start by examining the various components of an IP address. An IP address serves as a unique identifier for devices connected to a network. It consists of a series of numbers separated by periods.
- First, we have the network address, which indicates the network to which the device belongs.
- Next, we have the host address, which identifies the specific device within the network.
IP addresses can be classified into different types, such as IPv4 and IPv6, each with its own structure and limitations. While IPv4 addresses are more commonly used, IPv6 addresses offer a larger pool of unique addresses to accommodate the increasing number of devices connected to the internet.
Furthermore, we will explore subnetting, a technique employed to divide a network into smaller subnetworks. Subnetting allows for efficient allocation of IP addresses and better utilization of network resources.
To assist in managing IP addresses, we will also discuss the concept of subnet masks. Subnet masks serve as a guide for devices to determine whether an IP address belongs to the same network or a different one. They are represented as a series of binary numbers, with each bit indicating the boundaries of the network and host addresses.
Additionally, we will touch on the topic of classless inter-domain routing (CIDR), which is a more flexible way of assigning IP addresses and specifying network boundaries. CIDR notation allows for more granular control over network configurations and is widely used in modern networking.
By the end of this section, you will have a solid understanding of IP addresses, networks, subnetting, subnet masks, and CIDR. Armed with this knowledge, you will be well-equipped to navigate the intricacies of networking at the command line.
Implementing Network Routing in Linux
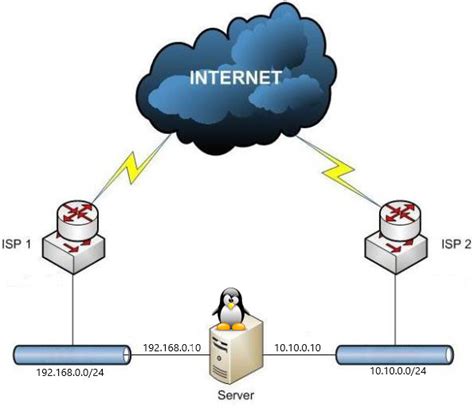
In this section, we will explore the process of establishing efficient and reliable network routes in a Linux environment. Network routing is a crucial aspect of managing network traffic, allowing data to flow seamlessly between different networks or subnets. By configuring routing tables and implementing routing protocols, administrators can ensure optimal data transmission and facilitate communication between devices within a network.
The foundation of network routing lies in the concept of forwarding packets - the fundamental units of data exchange in a network. Linux provides various tools and techniques to manipulate packet routing, allowing administrators to control the flow of data across networks. One of the primary methods is through the use of routing tables.
| Routing Table | Description |
|---|---|
| Destination | The destination network or subnet for the packet. |
| Gateway | The IP address of the gateway device used to forward the packet. |
| Netmask | The subnet mask used to determine the network range of the destination. |
| Interface | The network interface through which the packet should be transmitted. |
By configuring the routing table entries, administrators can define the path a packet should take to reach its destination. This process involves identifying the destination network, specifying the appropriate gateway, and specifying the outgoing network interface for optimal routing.
In addition to static routing, Linux also supports dynamic routing protocols such as OSPF (Open Shortest Path First) and BGP (Border Gateway Protocol). These protocols enable automatic exchange of routing information between routers, allowing them to dynamically adjust their routing tables based on network changes. Implementing dynamic routing protocols ensures efficient routing and redundancy in large-scale networks.
Furthermore, Linux provides several command-line tools for managing network routing, such as "route" and "ip route." These utilities allow administrators to view and modify routing tables, add or delete routes, and troubleshoot network routing issues.
Implementing network routing in Linux requires a comprehensive understanding of routing principles and the available tools and techniques. By effectively configuring routing tables and utilizing dynamic routing protocols, administrators can establish a robust and efficient network infrastructure.
Securing Your Linux Network with Firewall Rules
In today's interconnected world, ensuring the security of your Linux network is of utmost importance. One effective way to protect your network is by implementing firewall rules. By utilizing these rules, you can control incoming and outgoing network traffic, preventing unauthorized access and potential security threats.
Understanding Firewall Rules
Firewall rules act as a barrier between your network and the outside world, allowing or blocking specific types of traffic based on predefined criteria. These rules define which connections are allowed or denied based on factors such as source and destination IP addresses, ports, protocols, and more. By properly configuring firewall rules, you can establish strict security measures to safeguard your Linux network.
Implementing Firewall Rules
There are various firewall software options available for Linux systems, such as iptables and ufw. These tools allow you to define rules and apply them to specific network interfaces or system-wide. When crafting firewall rules, it is crucial to thoroughly analyze your network's requirements and potential security risks. Remember to consider both inbound and outbound network traffic to ensure comprehensive protection.
Example Rule: Blocking Unauthorized Access
One common scenario is to create a rule that blocks incoming SSH connections from unauthorized sources. This is essential in preventing brute-force attacks and unauthorized access attempts. By specifying source IP addresses and restricting the allowed port to the SSH port (typically 22), you can effectively secure your Linux network against potential threats.
Regular Monitoring and Maintenance
Securing your Linux network with firewall rules is an ongoing process. It is essential to regularly monitor the effectiveness of your rules and adjust them as necessary. Additionally, staying informed about emerging security vulnerabilities and adopting best practices is crucial in maintaining a strong defense against potential threats. Regularly updating your firewall software and checking for any suspicious activities can go a long way in keeping your Linux network secure.
In conclusion, by implementing firewall rules and continuously monitoring their effectiveness, you can significantly enhance the security of your Linux network. It is important to remember that while firewall rules provide a valuable layer of protection, they should be considered as one part of a comprehensive security strategy for your network.
Troubleshooting Common Networking Issues

In this section, we will explore solutions for frequently encountered problems related to establishing connections and communication between devices in a Linux network environment. By identifying and resolving these issues, you will be able to ensure smooth network operations and optimal performance.
1. Connectivity Problems: If you are experiencing connectivity problems, it is crucial to determine whether the issue lies with the network hardware, software configuration, or external factors. Common troubleshooting steps include checking cable connections, verifying IP configuration, and testing network connectivity using tools like ping or traceroute.
2. DNS Resolution Failures: When devices are unable to resolve domain names to IP addresses, it can cause browsing and communication issues. Troubleshooting steps involve verifying DNS server settings, checking hostname resolution using 'nslookup' or 'host' commands, and ensuring proper DNS caching.
3. Firewall and Security Restrictions: Network issues can arise due to firewall rules, security policies, or access restrictions. Troubleshooting includes reviewing firewall configurations, checking ports and protocols, and verifying access control lists (ACLs) to identify any misconfigurations or blocked traffic.
4. Slow Network Performance: Slow or inconsistent network performance can be caused by various factors, including bandwidth limitations, congestion, or hardware/software issues. To resolve this, troubleshooting steps may involve measuring network throughput, identifying potential bottlenecks, optimizing network settings, or upgrading network infrastructure.
5. Wireless Connection Problems: Troubleshooting wireless networking issues often involves checking wireless adapter configurations, signal strengths, and interference from other devices. Additional steps may include verifying encryption settings, resetting the wireless router, or updating device drivers.
6. VLAN and Network Segmentation Issues: If VLANs or network segmentation are in use, misconfigurations or compatibility problems can affect network connectivity. Troubleshooting involves validating VLAN configurations, checking network device compatibility, and ensuring proper routing and tagging of VLAN traffic.
7. Network Service Failures: Problems with critical network services like DHCP, DNS, or NTP can disrupt network operations. Troubleshooting steps may include verifying service configurations, checking server statuses, and diagnosing potential software errors or conflicts.
8. IP Address Conflict: If two devices have the same IP address, conflicts occur, causing network connectivity issues. Troubleshooting involves identifying conflicting IP addresses, updating IP configurations, and ensuring proper DHCP lease management.
By effectively troubleshooting these common networking issues, you will be equipped to solve problems efficiently and maintain optimal network functionality, ensuring seamless communication and connectivity within your Linux network environment.
IP Command | Configure Network Interfaces on Linux
IP Command | Configure Network Interfaces on Linux by KeepItTechie 27,974 views 3 years ago 14 minutes, 48 seconds
The Top 10 Linux Command Line Tools You Need to Know
The Top 10 Linux Command Line Tools You Need to Know by Nielsen Networking 3,854 views 1 year ago 29 minutes
FAQ
How can I view the network interfaces on my Linux system?
You can use the command "ifconfig" to view the network interfaces on your Linux system. It will display information about each interface such as IP addresses, MAC addresses, and network statistics.
Is it possible to configure network settings using the command line?
Yes, you can configure network settings using the command line. The main tool for this task is "ip" command, which allows you to assign IP addresses, set network routes, and manage various aspects of networking.
How can I troubleshoot network connectivity issues in Linux?
If you are facing network connectivity issues in Linux, you can start by using the "ping" command to check if you can reach other network devices. Additionally, you can use tools like "traceroute" to trace the route taken by network packets, and "netstat" to view active network connections and listening ports.
What is the purpose of the "ifup" and "ifdown" commands?
The "ifup" and "ifdown" commands are used to bring up and bring down network interfaces, respectively. They allow you to enable or disable network connectivity for specific interfaces on your Linux system. These commands are commonly used when configuring network connections manually.




