In the vast landscape of technological innovation, where speed and efficiency reign supreme, businesses are constantly seeking ways to optimize their operations. As organizations increasingly turn to containerization as a solution for streamlined deployment and scalability, it becomes imperative to address the paramount concern of security. Finding the delicate balance between accessibility and safeguarding sensitive information is a challenge faced by every modern enterprise.
One approach that has gained prominence is the utilization of Windows Server Core in Docker, an advanced and versatile platform that empowers developers and administrators alike. By leveraging the benefits of this cutting-edge technology, businesses can maximize their efficiency without compromising the security of their containerized environments. However, ensuring a robust and impenetrable firewall configuration remains a pivotal aspect of protecting your valuable data from potential threats.
This immersive guide aims to equip you with the knowledge and skills necessary to navigate the labyrinth of firewall configurations within your Windows Server Core in Docker environment. By empowering you with a comprehensive understanding of the intricacies involved, you will be equipped to fortify your infrastructure and shield it from malicious actors attempting to exploit vulnerabilities. Through a series of step-by-step instructions, practical tips, and expert insights, this guide will demystify the firewall configuration process and enable you to confidently safeguard your containerized ecosystem.
Understanding Docker Networking
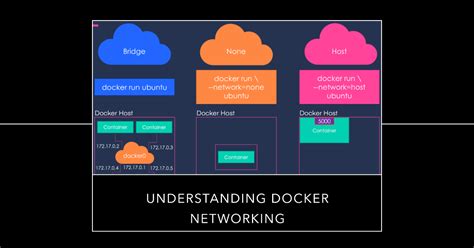
In this section, we will explore the intricate details of Docker networking and how it plays a crucial role in the deployment and management of containers. Here, we will delve into the mechanisms that enable communication between containers, examine the different network types available in Docker, and discuss the various networking options and their implications.
| Aspect | Description |
|---|---|
| Container Communication | Discover how containers communicate with each other and the external world, enabling seamless data exchange and collaboration. |
| Network Types | Explore the diverse network types in Docker, such as bridge, host, overlay, and macvlan networks, each designed to cater to specific needs and scenarios. |
| Networking Options | Learn about the different networking options available in Docker, including IP addressing, DNS resolution, port mapping, and network security measures. |
| Network Configuration | Gain insights into the process of configuring networks in Docker, including the use of the Docker CLI, Docker Compose, and Docker Swarm for network setup and management. |
| Best Practices | Discover recommended practices for designing efficient and secure network architectures, ensuring optimal performance and mitigating potential vulnerabilities. |
By understanding the intricacies of Docker networking, you will be equipped with the knowledge needed to confidently configure and manage the network aspect of your Windows Server Core containers within Docker.
Configuring the Firewall on Windows Server Core: Safeguarding Your System
In this section, we will delve into the vital task of configuring the firewall on your Windows Server Core environment. Securing your system against unauthorized access is of utmost importance to ensure the integrity and confidentiality of your data. By implementing proper firewall settings, you can establish robust defense mechanisms to protect against potential threats and unauthorized network traffic.
Here are some key steps to take when configuring the firewall on your Windows Server Core:
- Examine Current Firewall Rules: Begin by assessing the existing firewall rules to understand the current configuration and identify any potential vulnerabilities. This assessment will help you determine if any changes are required to fortify your system's defenses.
- Create Custom Firewall Rules: Depending on your specific requirements, it may be necessary to create custom firewall rules to allow or deny specific types of incoming or outgoing traffic. This allows you to establish granular control over the network communication to and from your server.
- Enable Logging: Enabling firewall logging provides you with valuable insights into the network traffic patterns and potential threats. By analyzing firewall logs, you can proactively identify suspicious activities and take necessary actions to mitigate risks.
- Implement Network-level Authentication: Network-level authentication adds an additional layer of security by requiring users to authenticate before gaining access to network resources. By configuring the firewall to enforce network-level authentication, you can prevent unauthorized access attempts and mitigate the risk of malicious attacks.
- Regularly Update Firewall Rules: As new threats emerge, it is crucial to stay up-to-date with the latest firewall rules and configurations. Regularly reviewing and updating your firewall settings ensures that your system remains resilient against evolving security threats.
By following these best practices for configuring the firewall on your Windows Server Core environment, you can create a secure and robust system that protects your data and network resources from unauthorized access and potential cyber threats.
Opening Ports for Containers: Ensuring Secure Communication

One critical aspect of running Docker containers is the ability to provide secure communication with external systems through open ports. In this section, we will explore the process of configuring the firewall to allow incoming and outgoing traffic for Docker containers while ensuring the overall security of the environment. By opening specific ports, we enable seamless integration and communication between Docker containers and other networked services, facilitating efficient data exchange and collaboration.
Custom Firewall Rules Creation
In this section, we will explore the process of creating personalized firewall rules for enhancing the security and network connectivity of your system. By customizing firewall rules, you can finely control the access to specific ports, IPs, or applications, ensuring that only authorized connections are allowed.
To create custom firewall rules, you need to have a clear understanding of the network architecture and desired security requirements. It is essential to identify the specific ports, protocols, and IP addresses that should be permitted or blocked. By carefully planning your firewall rules, you can safeguard your system against unauthorized access attempts while allowing legitimate traffic to pass through.
One of the effective approaches for creating custom firewall rules is using a rule-based configuration table. This table provides a structured framework for defining rules, where each rule consists of specific conditions and corresponding actions. By leveraging this framework, you can define rules based on various factors such as source IP address, destination port, or application type. It allows you to customize the firewall behavior and tailor it to the specific needs of your system.
When creating custom firewall rules, it is crucial to document them properly. Maintain a record of all the rules along with their purpose and the rationale behind their creation. This documentation not only helps in understanding the rule set but also assists in future troubleshooting or modifications. Additionally, it ensures consistency and enables easy collaboration among team members who are responsible for managing the firewall configuration.
| Condition | Action |
|---|---|
| Source IP: 192.168.1.10 | Allow |
| Source IP: 10.0.0.0/24 | Block |
| Destination Port: 443 | Allow |
| Application: FTP | Block |
As shown in the example above, the table represents a set of custom firewall rules. Each row defines a condition, such as a source IP or destination port, along with the corresponding action to be taken, which can be either allowing or blocking the traffic. By creating similar rules based on your specific needs, you can effectively configure the firewall and enhance the security of your Windows Server Core in Docker environment.
Securing Container Networks: Enforcing Network Access Restrictions for Docker Containers
In this section, we will explore techniques to enhance the security of Docker containers by imposing restrictions on their network access. By implementing network access controls, administrators can control the flow of data between containers and external networks, preventing unauthorized access or undesired communication.
1. Container Network Isolation: One approach to restrict network access is by implementing container network isolation. By default, containers share the host's network namespace, allowing them to communicate freely with each other and with the host. However, this can pose security risks, especially when containers from different applications or environments are co-located on the same host. To mitigate these risks, administrators can leverage container network isolation techniques such as creating dedicated network namespaces for specific sets of containers, thereby limiting their network interactions and reducing the attack surface.
2. Firewall Rules: Another effective way to restrict network access for Docker containers is by configuring firewall rules at the host level. By deploying firewall rules, administrators can define specific network traffic policies and filter incoming and outgoing connections based on various criteria. These rules can be tailored to allow or deny communication only to specified ports, IP addresses, or network protocols, ensuring that containers can only connect to authorized endpoints and preventing unwanted exposure to potential threats.
3. Network Segmentation: Implementing network segmentation is crucial for enforcing network access restrictions in a Docker environment. By dividing the network into distinct segments or subnets, administrators can establish logical boundaries between different groups of containers, applications, or services. This enables them to implement fine-grained control over network traffic and isolate sensitive or critical containers from potentially less secure ones. Network segmentation helps minimize the potential impact of security breaches and limit lateral movement within the container infrastructure.
4. Container Network Plugins: Container network plugins provide an additional layer of network access control for Docker containers. These plugins enable administrators to define specific network policies and govern container-to-container or container-to-host communication. By leveraging these plugins, administrators can enforce advanced rules and policies, such as encryption, authentication, or traffic shaping, to ensure secure and controlled communication within the container ecosystem.
Incorporating these techniques to restrict network access for Docker containers enhances overall security and reduces the potential risks associated with unauthorized communication or external threats. By carefully configuring network access controls, administrators can establish a more robust and reliable containerized infrastructure.
Testing the Firewall Setup
In this section, we will explore the process of verifying the effectiveness of the configured firewall settings without relying on specific terms. It is essential to ensure that the firewall protection measures are working as intended and that the system remains secure from external threats.
- Performing a connectivity test to assess if the firewall is successfully blocking unauthorized incoming connection attempts.
- Conducting simulated attacks to evaluate the firewall's ability to detect and block potential security breaches.
- Employing network monitoring tools to analyze the data traffic and confirm the firewall's activity.
- Testing the accessibility of permitted services and verifying that the firewall does not interfere with their functionality.
- Carrying out regular firewall audits and reviewing logs to identify any unexpected or suspicious activity that might indicate a breach.
By following these testing procedures regularly, system administrators can ensure that the firewall configuration is robust and capable of safeguarding the system against potential threats. Testing the firewall setup plays a crucial role in maintaining the security and integrity of the network environment.
Part 8 - Installing and working with Windows Server Container
Part 8 - Installing and working with Windows Server Container by Execute Automation 8,872 views 7 years ago 10 minutes, 7 seconds
Deploying Docker Containers on Windows Server 2016
Deploying Docker Containers on Windows Server 2016 by Linux0 3,857 views 4 years ago 57 minutes
FAQ
What is Windows Server Core in Docker?
Windows Server Core in Docker is a lightweight container technology that allows running Windows Server Core, a minimal version of Windows Server, within Docker containers.
Why should I use Windows Server Core in Docker?
Using Windows Server Core in Docker provides several benefits, including better resource utilization, increased flexibility, easier deployment and scaling, and improved security isolation between applications.
How do I configure the firewall for Windows Server Core in Docker?
To configure the firewall for Windows Server Core in Docker, you can use the built-in PowerShell cmdlets or the Windows Defender Firewall with Advanced Security GUI. You need to allow the necessary network traffic for your applications by defining inbound and outbound rules.
What are the recommended security practices for Windows Server Core in Docker?
Some recommended security practices for Windows Server Core in Docker include minimizing the attack surface by removing unnecessary Windows components, keeping the host and containers up-to-date with security patches, using secure network configurations, and restricting administrative privileges.
Are there any limitations or considerations when using Windows Server Core in Docker?
Yes, there are some limitations and considerations when using Windows Server Core in Docker. These include the lack of a graphical user interface (GUI), limited compatibility with certain applications, potential networking complexities, and the need to properly configure the firewall and security settings.
Can Windows Server Core be used in Docker containers?
Yes, Windows Server Core can be used in Docker containers. This allows for lightweight, isolated, and efficient deployments of Windows applications.




