The rapidly evolving landscape of technology has given rise to increasingly complex and dynamic data management scenarios. As enterprises strive to embrace the potential of Docker on the Windows platform, it is crucial to delve into the realm of data permissions to ensure the security and integrity of sensitive information.
Unveiling the Underlying Challenges
The seamless integration of data-centric operations within Docker on Windows calls for a meticulous understanding of the intricate web of access control mechanisms. Building upon the foundation of the Docker engine, the intricate interplay between data containers, host systems, and network resources necessitates a robust system of data permissions that can mitigate potential vulnerabilities.
Enterprises encapsulating their data and applications within Docker containers are confronted with the ever-present challenge of achieving a fine-grained control over access privileges.
Forging an Impenetrable Shield
To guard against unauthorized access and potential breaches, meticulous attention must be given to establishing robust data permission frameworks. By setting up granular access controls, deploying secure authentication mechanisms, and implementing effective authorization protocols, organizations can fortify their Docker environment and elevate their security posture to new heights.
By meticulously curating the data permissions landscape, organizations can foster a culture of data integrity, safeguarding their assets and ensuring compliance with regulatory frameworks.
Understanding Access Control in the Docker Environment
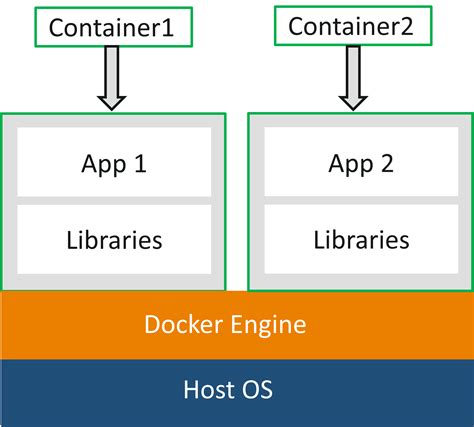
In the realm of containerization technology, it is crucial to comprehend the intricacies of managing access control for data within Docker environments. Access control, being a fundamental aspect of container security, defines the privileges and restrictions granted to various entities within the ecosystem.
Through a finely-tuned access control framework, Docker ensures that only authorized entities are allowed to interact with sensitive data, thus safeguarding the overall integrity and confidentiality of the system. This article aims to provide a comprehensive understanding of the concepts and mechanisms behind data permissions in Docker, shedding light on the best practices to secure containerized environments.
| Section | Description |
|---|---|
| User Identity and Authentication | Exploring the significance of user identity and authentication techniques, such as usernames, passwords, and access tokens in Docker. This section delves into the various methods and tools available for controlling user access within containers. |
| Role-based Access Control | An in-depth look at the role-based access control (RBAC) approach in Docker. This section elucidates the mechanism of assigning roles and permissions to different entities based on their responsibilities and the principle of least privilege. |
| Container Isolation and Resource Limitations | Examining the relationship between data permissions and container isolation, emphasizing the impact of isolation on access control. Additionally, this section delves into the significance of resource limitations and how they contribute to securing Dockerized environments. |
| Vulnerability Management | Addressing the importance of vulnerability management as a key component of data permissions in Docker. This section explores techniques such as vulnerability scanning, image updates, and vulnerability remediation to proactively mitigate potential security risks. |
| Container Monitoring and Logging | An overview of the significance of container monitoring and logging in ensuring data permissions within Docker. This section describes the role of monitoring tools, logging frameworks, and centralized log management solutions in providing visibility into access events and identifying potential threats. |
Understanding Access Rights: Windows and Docker
This section delves into the intricacies of access rights and privileges on Windows when using Docker. It explores the various levels of permissions and discusses how they work within the Docker environment.
Windows operating system provides a robust set of access control mechanisms that govern the interactions between different entities, such as users, processes, and files. When Docker is installed on Windows, it inherits these access rights and adds an additional layer of security and control over containerized applications.
One fundamental concept to comprehend is the principle of least privilege, which states that entities should only have the minimum level of access required to fulfill their tasks. This principle holds true in both Windows and Docker, as limiting the permissions granted to containers and their associated processes enhances overall security and reduces potential attack surfaces.
Permissions within Windows and Docker are granular and can be applied to various components, including containers, volumes, networks, and executables. These permissions determine who can perform specific actions, such as reading files, writing to directories, or interacting with network resources.
It is essential to understand how permissions are inherited and propagated across Windows and Docker environments. Permissions granted to a parent object, such as a directory, can be inherited by its child objects, such as files within that directory. Docker leverages this inheritance model to ensure that containers launched from a specific image inherit the necessary permissions required to operate within the intended boundaries.
In summary, comprehending the access rights within Windows and Docker is crucial for establishing a secure and controlled environment. Understanding the principles of least privilege and the inheritance model helps administrators define appropriate permissions and protect sensitive data from unauthorized access and manipulation.
Configuring Access Control for Windows Containers
In this section, we will explore the process of setting up access control for containers running on the Windows operating system. By customizing access permissions, you can ensure that your containers have the appropriate level of security and protect your data from unauthorized access.
To configure access control for Windows containers, you need to understand the different components involved. One crucial element is user account management, which allows you to define specific permissions for different users or groups. Additionally, you can leverage built-in security features, such as Windows security namespaces and access control lists (ACLs), to further refine access control for your containers.
- Manage User Accounts: Create and manage user accounts within the Windows operating system to control access to containers and their data. By assigning appropriate permissions, you can restrict access to certain containers or specific files within a container.
- Utilize Windows Security Namespaces: Windows provides security namespaces to isolate processes and resources, allowing for granular control over access. By utilizing these namespaces, you can enforce separate access permissions for different containers or groups of containers.
- Implement Access Control Lists (ACLs): ACLs enable you to define detailed access rules for files and directories within a container. By setting up ACLs, you can ensure that only authorized users or groups can read, write, or execute specific files.
- Monitor and Audit Access: Regularly monitor and audit access to your containers to identify any potential security breaches. Implementing logging and monitoring mechanisms can help you detect and respond to unauthorized access attempts swiftly.
By following best practices and configuring access control settings effectively, you can maintain a secure environment for your Windows containers. Proper access control ensures that sensitive data remains protected and only accessible to authorized individuals or processes.
Effective Strategies for Managing Data Access in the Docker Environment
In the realm of containerization, ensuring proper control and permissions over data is paramount. This section discusses essential best practices and effective strategies for managing data access within Docker, promoting secure and reliable data handling.
- Implementing Access Control Measures: Establishing granular access controls is crucial for protecting sensitive data within a Docker environment. By employing authentication mechanisms, such as user accounts or API tokens, access can be restricted to authorized individuals or systems.
- Utilizing Role-Based Access Control (RBAC): RBAC provides a structured approach to managing data permissions, allowing administrators to define specific roles and associated privileges. This streamlines access management and ensures that users only have the necessary permissions required to carry out their tasks.
- Implementing Least Privilege Principle: Adhering to the least privilege principle limits the exposure of sensitive data by granting users the minimum level of access necessary to perform their duties. By reducing unnecessary privileges, the risk of accidental or malicious data leaks can be mitigated.
- Applying Containerization Frameworks: Utilizing containerization frameworks that integrate robust data access controls ensures that data permissions remain intact throughout the Docker environment. Implementing solutions like Kubernetes or Docker Swarm facilitates centralized management and enhances security.
- Regularly Auditing and Monitoring Data Access: Conducting regular audits and monitoring data access helps identify potential vulnerabilities or unauthorized activities. Implementing logging mechanisms and utilizing security tools can provide real-time insights into data access activities, enabling timely detection and response to any anomalies.
- Encrypting Sensitive Data: Protecting data at rest and in transit using encryption techniques adds an extra layer of security. Implementing encryption mechanisms within Docker containers ensures that even if unauthorized access occurs, the data remains unreadable without the decryption keys.
By adopting these best practices for managing data access in Docker, organizations can establish strong security measures and promote trustworthy data handling within their containerized environments.
Controlling Access: Configuring User and Group Privileges
In this section, we will explore the methods for restricting access to data and managing user and group permissions within the Docker environment on the Windows platform. By configuring user and group privileges, organizations can maintain tighter control over the resources available to different individuals or teams.
One way to limit access is by assigning specific user and group permissions, determining who can view, modify, or delete data within Docker. These permissions act as a layer of security to safeguard sensitive information and prevent unauthorized access or accidental data loss.
By setting user privileges, administrators can allocate specific rights to individual users, allowing them to perform certain actions within Docker containers. Meanwhile, group permissions offer the ability to assign a common set of privileges to multiple users, ensuring consistent access levels across teams or departments.
With the ability to configure user and group permissions, organizations can maintain control over their Docker environments, safeguarding information and protecting against potential security breaches. By carefully managing access rights, organizations can improve data integrity and minimize the risk of unauthorized actions within their Docker installations.
Overall, understanding how to limit access by setting user and group permissions is essential for organizations using Docker on the Windows platform. By implementing these measures, organizations can enhance security and prevent unauthorized access to valuable data within Docker environments.
Managing Ownership of Files in Docker on Windows
In the world of containerization, managing file ownership can be a challenging task. When working with Docker on the Windows platform, it is important to have a clear understanding of how file ownership is handled within the container environment. This section will explore the concepts and techniques for effectively managing file ownership in Docker on Windows, ensuring that the right permissions are granted to the right individuals or processes.
Understanding File Ownership
File ownership refers to the user or group that has control over a specific file or directory. In a Docker environment, the ownership of files within a container will depend on various factors, including the image used, the user account running the container, and the file system being utilized.
Setting File Ownership
When running Docker on Windows, it is crucial to understand how to set the ownership of files to ensure that they can be accessed and modified by the appropriate users or processes. This can be achieved by using the appropriate commands and syntax within the Dockerfile or by leveraging the chown command within the container itself.
Managing File Permissions
In addition to ownership, file permissions play a vital role in controlling access to files and directories within a Docker container on Windows. Understanding the different permission levels, such as read, write, and execute, is essential for granting the necessary access to files without compromising security.
Best Practices for File Ownership and Permissions
To effectively manage file ownership and permissions in Docker on Windows, it is important to follow best practices. This includes using unique user and group IDs, leveraging built-in file system permission controls, and regularly auditing and updating file ownership and permissions to align with security requirements.
In conclusion, managing file ownership in Docker on Windows is a crucial aspect of ensuring proper access and security within a containerized environment. By understanding the underlying concepts and implementing appropriate practices, developers and system administrators can maintain control over their files and protect sensitive data.
Securing Data in Docker: Encryption and Access Controls
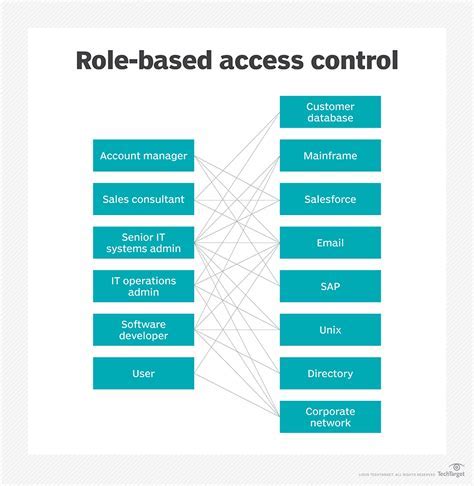
In this section, we will explore various strategies and techniques for ensuring the security of data within Docker containers. By implementing robust encryption and access controls, organizations can protect sensitive information from unauthorized access or tampering.
Encrypting Data: One effective approach for securing data in Docker involves encryption. Encryption works by transforming data into a format that can only be accessed with a corresponding decryption key. By encrypting data both at rest and in transit, organizations can safeguard it from potential threats such as data breaches or unauthorized access.
Access Controls: Implementing access controls is crucial for ensuring that only authorized individuals have the necessary permissions to access and interact with data within Docker containers. Access controls can be enforced through various mechanisms, such as user authentication, role-based access control (RBAC), or mandatory access control (MAC) policies. These measures help prevent unauthorized users from gaining unauthorized access to sensitive data.
Container Isolation: Another important aspect of securing data in Docker is container isolation. Docker provides features that allow containers to be isolated from each other, limiting their ability to interact or access each other's data. By implementing appropriate container isolation techniques, organizations can minimize the risk of data leakage or unauthorized data sharing between containers.
Monitoring and Auditing: To ensure the ongoing security of data in Docker, it is important to implement robust monitoring and auditing practices. Monitoring can help detect any suspicious activities or unauthorized access attempts, while auditing provides a record of all actions taken within the Docker environment. By regularly reviewing logs and monitoring system behavior, organizations can quickly identify and respond to any security incidents.
Educating Users: Finally, educating users about the importance of data security and best practices for working with Docker containers is essential. By promoting a culture of security awareness, organizations can reduce the risk of human error or negligence that may lead to data breaches. Training programs and guidelines can help users understand and follow proper data security protocols.
Troubleshooting Access Control Problems in Containers on Microsoft Windows
When working with containers on the Microsoft Windows operating system, it is essential to understand the potential challenges that can arise when it comes to managing access control for the data within those containers. In this section, we will explore common issues related to data permissions and provide solutions to troubleshoot these problems.
Future Developments: Enhancing Access Privileges in Docker Environment for Windows
In this section, we will explore potential advancements and future directions for improving the management and control of user permissions within the Docker ecosystem on the Windows platform. By addressing the complexities and limitations of data access and security, these developments aim to provide a more efficient and secure environment for containerized applications.
To enhance the data permissions framework in Docker on Windows, one potential development revolves around refining the access control mechanisms for individual containers. Through the implementation of advanced authentication and authorization protocols, such as role-based access control (RBAC) or attribute-based access control (ABAC), administrators can establish fine-grained permissions, effectively restricting the actions and data available to different container users.
Another aspect that requires attention in the future development of data permissions for Docker on Windows is the integration of secure container isolation technologies. By leveraging features like hypervisor-based isolation or hardware-assisted virtualization, the Docker platform can provide enhanced security measures, isolating containerized applications at a deeper level from the underlying host system. This can significantly reduce the potential for unauthorized access or data breaches.
Furthermore, the evolution of data permissions in Docker on Windows could involve the implementation of more robust logging and auditing mechanisms. This would enable administrators to monitor and review all data access and permission changes, facilitating regulatory compliance and providing valuable insights for security analysis and incident response. Integrating centralized logging and auditing solutions could streamline these processes and further strengthen the overall security posture.
| Potential Future Developments: | Benefits |
|---|---|
| Enhanced integration with existing identity management systems | Simplified user management and improved consistency in access controls |
| Support for encrypted data volumes | Enhanced data confidentiality and protection against unauthorized access |
| Automated vulnerability scanning and security assessments | Proactive identification and mitigation of potential security risks |
These suggestions represent a glimpse into the potential future developments for enhancing data permissions in Docker on the Windows platform. By continuously addressing the challenges associated with data access and security, the Docker ecosystem can establish a more robust and trustworthy foundation, fostering a secure and efficient environment for containerized applications.
Run Docker in Windows - Setup, Docker Compose, Extensions
Run Docker in Windows - Setup, Docker Compose, Extensions by Raid Owl 47,701 views 1 year ago 16 minutes
FAQ
What are data permissions for Docker on Windows?
Data permissions for Docker on Windows refer to the access controls and privileges set for the data and resources used by Docker containers running on the Windows operating system.
How are data permissions managed in Docker on Windows?
Data permissions in Docker on Windows are managed through the use of access control lists (ACLs) and user/group permissions. These permissions can be set at the file system level or through Docker-specific commands.
What are the default data permissions for Docker on Windows?
The default data permissions for Docker on Windows depend on the underlying file system being used. For example, if Docker is running on NTFS, the permissions will be inherited from the host system's ACLs, while on ReFS, a more simplified permission model is used.
Can data permissions be customized in Docker on Windows?
Yes, data permissions can be customized in Docker on Windows. By using Docker-specific commands, such as "docker run" with the appropriate options, users can specify permissions for files and directories within Docker containers.
Are there any security considerations when managing data permissions in Docker on Windows?
Yes, there are several security considerations when managing data permissions in Docker on Windows. It's important to ensure that only trusted users have access to sensitive data, and to regularly audit and review permissions to identify any potential security vulnerabilities.




