Imagine a world where the complexities of authenticating Windows in a Linux container are effortlessly resolved, paving the way to streamlined operations and enhanced productivity. In our technological landscape, where the boundaries between operating systems converge, finding a seamless and robust solution to bridge this gap is essential for businesses and developers alike.
Introducing Docker.net 5, a transformative toolset that revolutionizes the way Windows authentication is handled within a Linux container. By abstracting the intricacies of authentication protocols and leveraging innovative techniques, Docker.net 5 empowers users to effortlessly authenticate their Windows applications in a Linux environment, without compromising on security or performance.
Through the power of Docker.net 5, developers can unlock a new level of productivity, as they no longer have to wrestle with the complexities of integrating Windows-specific authentication mechanisms into a Linux container. This groundbreaking solution intelligently bridges the gap between Windows and Linux, enabling seamless communication and authentication between the two systems.
Understanding the Challenge of Authenticating Windows Containers in a Linux Environment
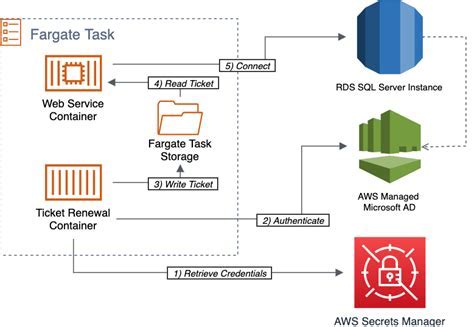
In the world of containerization, authenticating Windows containers in a Linux environment presents a unique set of challenges. This article aims to explore the difficulties and complexities that arise when trying to establish the authenticity of Windows-based containers within a Linux-based framework.
One of the primary hurdles is the inherent differences between Windows and Linux operating systems. Windows and Linux have distinct authentication mechanisms and protocols, making it difficult to seamlessly authenticate Windows containers within a Linux ecosystem.
Another challenge lies in the need for interoperability between Windows and Linux authentication systems. Integrating the authentication processes of these two disparate systems requires a deep understanding of their inner workings and the ability to bridge the gap between them effectively.
To complicate matters further, the containerization platform, such as Docker.net, used for managing these containers, adds another layer of complexity. It is crucial to ensure that the authentication process is compatible with the specific framework being utilized while maintaining the integrity and security of the containers.
Furthermore, the need for a flexible and scalable authentication solution becomes apparent when considering the dynamic nature of containerized environments. As containers are frequently created, updated, and destroyed, the authentication process must be able to adapt and scale accordingly without compromising security.
In conclusion, authenticating Windows containers in a Linux environment is an intricate task that requires deep knowledge of both operating systems, their authentication systems, and the containerization framework being utilized. Addressing the challenges posed by this unique scenario necessitates innovative solutions and a thorough understanding of the intricacies involved.
Introducing Docker.net 5: A Solution for Authenticating Windows Containers in Linux
In this section, we will explore the capabilities of Docker.net 5 and how it addresses the challenge of authenticating Windows containers within a Linux environment. We will delve into the concept of container authentication and discuss the benefits of using Docker.net 5 for this particular use case.
Implementing Authentication with Docker.net 5
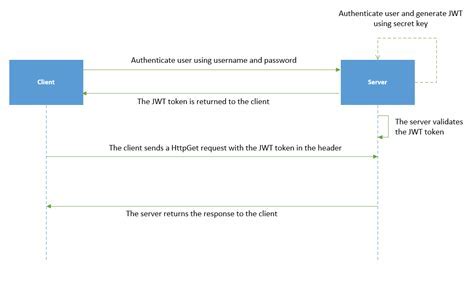
In this section, we will explore the process of implementing authentication with Docker.net 5. Authentication is a crucial aspect of any application, as it ensures that only authorized users can access the system. By implementing authentication in your Docker.net 5 application, you can enhance security and protect sensitive data from unauthorized access. In this section, we will discuss the various authentication mechanisms and approaches that can be used with Docker.net 5, enabling you to choose the one that best suits your application's requirements.
Secure User Authentication
Implementing secure user authentication is essential to protect your application from unauthorized access. Docker.net 5 provides various authentication mechanisms, such as username/password authentication, token-based authentication, and federated authentication. Each mechanism has its own advantages and considerations, and it is important to understand how they work and choose the most appropriate one for your application.
Token-Based Authentication
Token-based authentication is a popular choice for modern web applications. It involves issuing a token to authenticated users, which they can then use to authenticate subsequent requests. Docker.net 5 provides built-in support for token-based authentication, allowing you to easily implement this mechanism in your application. We will explore the process of generating and validating tokens, as well as storing them securely to prevent unauthorized access.
Federated Authentication
Federated authentication allows users to authenticate using external identity providers, such as Microsoft Azure Active Directory or Google. This mechanism simplifies user management and improves user experience by leveraging existing credentials. Docker.net 5 supports federated authentication through various authentication providers, and we will discuss how to configure and implement this mechanism in your application.
Multi-Factor Authentication
Multi-factor authentication adds an extra layer of security by requiring users to provide multiple forms of authentication, such as a password and a one-time code sent to their mobile device. Docker.net 5 offers support for multi-factor authentication, enabling you to enhance security and protect sensitive data from unauthorized access. We will explore the process of implementing multi-factor authentication in your Docker.net 5 application, including the different authentication factors and how to validate them.
In conclusion, implementing authentication in your Docker.net 5 application is crucial for ensuring secure access and protecting sensitive data. By choosing the appropriate authentication mechanism and following best practices, you can enhance the security of your application and provide a seamless user experience.
Step-by-Step Guide: Authenticating Windows Containers in Linux with Docker.net 5
In this section, we will explore a detailed step-by-step guide on how to authenticate Windows containers in a Linux environment using Docker.net 5. The focus will be on the authentication process, without delving into the specific definitions and technicalities of Windows, Linux, containers, or Docker.net.
To ensure secure and reliable communication between Windows containers and Linux, authentication becomes a crucial aspect. By following the steps outlined in this guide, you will be able to establish a seamless and authenticated connection between Windows containers and a Linux platform, facilitating smooth interoperability and data transfer.
Step 1: Installation and Configuration of Docker.net 5
Firstly, we need to install and configure Docker.net 5 on the Linux machine where the containers will be hosted. This step involves downloading and setting up the necessary packages, configuring the network settings, and ensuring compatibility with the Linux environment. Refer to the Docker.net 5 documentation for detailed instructions.
Step 2: Generating and Managing Authentication Certificates
In this step, we will generate and manage the authentication certificates required for establishing a secure connection between Windows containers and Linux. These certificates will be used to verify the identities of the containers and encrypt the communication between them. Proper management and distribution of these certificates are crucial for a successful authentication process.
Step 3: Configuring Windows Containers for Authentication
Once the necessary certificates are generated, the next step is to configure the Windows containers to enable authentication. This involves updating the container configurations, such as specifying the authentication method and providing the required authentication certificates. These configurations will ensure that the containers can properly authenticate themselves when communicating with the Linux system.
Step 4: Establishing a Secure Connection
In this step, we will establish a secure connection between the authenticated Windows containers and the Linux platform. This involves validating the certificates, verifying the identities of the containers, and establishing an encrypted communication channel. By following the proper procedures and ensuring the correct configuration, a secure and authenticated connection can be established.
Step 5: Testing and Troubleshooting
Finally, we will conduct thorough testing and troubleshooting to ensure the successful authentication of Windows containers in the Linux environment. This step involves verifying the functionality of the authenticated connection, identifying and resolving any potential issues or errors, and ensuring the overall reliability and security of the setup.
By following this step-by-step guide, you will be able to overcome the challenges of authenticating Windows containers in a Linux environment using Docker.net 5. With a solid understanding of the authentication process and careful configuration of both the Linux platform and the Windows containers, you can achieve a seamless and secure integration between the two systems.
Best Practices for Successful Authentication in Docker.net 5

In this section, we will explore the most effective strategies and techniques for achieving successful authentication in Docker.net 5. By implementing these best practices, you can ensure a secure and seamless authentication process for your Windows and Linux containers.
- 1. Implement Robust Authentication Mechanisms
- 2. Employ Multi-Factor Authentication
- 3. Regularly Update and Patch Container Images
- 4. Monitor and Log Authentication Attempts
- 5. Follow Least Privilege Principle
It is crucial to employ strong and reliable authentication mechanisms when authenticating Docker containers. By leveraging cryptographic protocols, secure tokens, and encryption algorithms, you can protect sensitive data and prevent unauthorized access.
Incorporating multi-factor authentication adds an extra layer of security to your Docker containers. By requiring users to provide multiple forms of authentication, such as passwords, biometrics, or one-time codes, you can significantly reduce the risk of unauthorized access.
Keeping your container images up to date with the latest security patches and updates is essential for maintaining a secure environment. By regularly updating your Docker images, you can address any known vulnerabilities and ensure that your authentication process remains robust.
Implementing proper logging and monitoring mechanisms allows you to track and analyze authentication attempts in your Docker.net 5 environment. By monitoring login activities, you can quickly detect and respond to suspicious behavior, potential security breaches, and unauthorized access attempts.
Adhering to the principle of least privilege is essential when configuring authentication for Docker containers. By granting only the necessary permissions and privileges to users and applications, you can minimize the potential impact of security breaches and limit the attack surface.
By adopting these best practices and considering the unique requirements of your Windows and Linux containers, you can establish a secure and reliable authentication framework in your Docker.net 5 environment.
The Advantages and Possible Applications of Verifying Authenticity of Windows Containers within Linux using Docker.net 5
When it comes to the process of ensuring the legitimacy and integrity of Windows containers running on a Linux environment with the utilization of Docker.net 5, there are several compelling benefits and numerous potential use cases to consider.
Firstly, by successfully authenticating Windows containers within a Linux setting, organizations can enhance the overall security and trustworthiness of their application deployment processes. This enables them to confidently run Windows-based workloads on a Linux infrastructure, leveraging the flexibility and reliability of Docker.net 5, while also ensuring that only authorized and validated containers are allowed to execute.
Furthermore, the ability to authenticate Windows containers within a Linux environment can bring significant cost savings and operational efficiencies. By utilizing Docker.net 5 to seamlessly integrate Windows containers into existing Linux-based infrastructures, companies can consolidate their hardware resources, streamline their management processes, and reduce the complexity and expenses associated with maintaining separate Windows and Linux environments.
In addition, the authentication of Windows containers in a Linux environment using Docker.net 5 opens up a wide range of use cases and possibilities. Organizations can leverage this capability to develop hybrid applications that incorporate both Windows and Linux components, allowing for seamless integration and interoperability. This enables the deployment of diverse solutions across various industries, such as cross-platform development, cloud-native applications, and multi-cloud deployments.
In conclusion, the benefits and potential use cases of verifying the authenticity of Windows containers within a Linux environment using Docker.net 5 are manifold. From enhancing security and reducing costs to enabling cross-platform compatibility and facilitating diverse application deployments, this capability provides organizations with a powerful tool to optimize their containerized workflows and meet their specific business requirements.
Docker Tips - Full Ubuntu GUI in a Container Displayed on Windows (XServer)
Docker Tips - Full Ubuntu GUI in a Container Displayed on Windows (XServer) by AgileDevArt 49,198 views 2 years ago 8 minutes, 31 seconds
Docker Tips - GUI Windows Apps in Container (2022)
Docker Tips - GUI Windows Apps in Container (2022) by AgileDevArt 39,038 views 1 year ago 14 minutes, 44 seconds
FAQ
Can I authenticate Windows in a Linux container using Docker.net 5?
Yes, it is possible to authenticate Windows in a Linux container using Docker.net 5. The article explains how to achieve this by using the Windows container mode in Docker.
What are the benefits of authenticating Windows in a Linux container?
Authenticating Windows in a Linux container allows you to leverage the benefits of both Windows and Linux environments. It provides flexibility in choosing the best platform for your specific needs and enables seamless integration between Windows and Linux-dependent applications.
Does Docker.net 5 provide built-in support for authenticating Windows in a Linux container?
Yes, Docker.net 5 comes with built-in support for authenticating Windows in a Linux container. This feature simplifies the process and ensures smooth integration between the two environments.
Are there any limitations or compatibility issues when authenticating Windows in a Linux container with Docker.net 5?
While Docker.net 5 offers seamless authentication between Windows and Linux containers, there might be compatibility issues with certain applications or specific functionalities that heavily rely on the underlying operating system. It is recommended to thoroughly test and verify compatibility before implementing this setup.
Can you provide step-by-step instructions on how to authenticate Windows in a Linux container using Docker.net 5?
Unfortunately, the article does not include step-by-step instructions. However, it provides a comprehensive overview of the process and highlights key considerations. It is recommended to refer to the official Docker documentation and resources for detailed implementation steps.
What is Docker and what is its relation to Linux containers?
Docker is an open-source platform that allows developers to automate the deployment of applications inside software containers. Linux containers are a lightweight and isolated execution environment, provided by the Linux kernel, where Docker runs.




