Delving into the realm of computer networking, where arcane terms like "tcp://localhost:2375" and "demon" are thrown around, can be both intimidating and fascinating. In this article, we embark on an enlightening journey to unravel the enigma of establishing a connection without encryption in the Windows 7 operating system. Embracing the power of Docker, a cutting-edge technology for virtualization, we unlock a world of possibilities.
Connectivity. A word that resonates omnipresent in today's tech-driven landscape. We yearn for efficient and secure connections that enable the seamless flow of information. However, venturing beyond the realm of encryption (or tls for short) can be a daunting endeavor. Windows 7, with its idiosyncrasies and idiosyncratic technologies, adds a layer of complexity to this pursuit. Yet, fear not, as we navigate these uncharted waters together.
The Gateway to the Unknown. Imagine a door that leads to a hidden world of untapped potential and limitless experimentation. This is precisely what the tcp://localhost:2375 address embodies. Serving as a portal to the Docker platform, it allows us to harness the power of containers and the splendid freedom they offer. With meticulous steps and a dash of technical finesse, we will pry open this gateway, enabling us access to an array of magnificent possibilities.
Caution: This guide will forego the usage of tls, or transport layer security, as it can be an impediment to unlocking the full potential of our journey. We understand the importance of security, but for the sake of exploration, we shall temporarily set it aside. Rest assured, the wisdom gained from this expedition will empower you to make informed decisions regarding network security in the future.
Understanding Docker and its Advantages
In the realm of modern software development, Docker has emerged as a powerful tool that offers numerous benefits to developers and businesses alike. Docker enables the creation and management of containers, which are lightweight, isolated environments capable of running applications across different operating systems.
One of the key advantages of Docker is its portability. Containers can be easily packaged with all the necessary dependencies and configurations, allowing them to run consistently on any machine or cloud infrastructure. This eliminates the common issue of "it works on my machine" and streamlines the deployment process.
Furthermore, Docker promotes scalability by allowing applications to be divided into separate containers, each handling a specific component or service. This modular approach facilitates the efficient utilization of resources and enables the easy scaling of individual components to meet changing demands, reducing costs and improving performance.
Another important benefit of Docker is its ability to isolate applications within containers. This isolation ensures that applications do not interfere with each other, providing a consistent and predictable environment for development, testing, and production. Additionally, containerization helps to enhance security by reducing the attack surface and preventing malicious activities from spreading.
Docker also simplifies the software development process through its efficient resource utilization. By utilizing the underlying resources optimally, Docker allows developers to create and test applications quickly and efficiently, leading to faster development cycles and reduced time-to-market.
Lastly, Docker provides an extensive ecosystem of pre-built images and containers, known as Docker Hub, that can be easily accessed and shared. This vast repository allows developers to leverage existing containers, saving time and effort in building applications from scratch and promoting collaboration within the developer community.
In conclusion, Docker revolutionizes software development by providing benefits such as portability, scalability, isolation, security, resource efficiency, and an extensive ecosystem. Understanding these advantages is crucial for developers and businesses looking to optimize their workflow, streamline deployment, and stay ahead in the competitive digital landscape.
Step 1: Verification of Compatibility and Installation of Docker
In order to begin using Docker on your Windows 7 operating system, it is essential to first verify the compatibility of your system and then proceed with installing Docker. This section will guide you through the steps required for this process.
Before proceeding with the installation, it is important to ensure that your Windows 7 operating system meets the necessary requirements for running Docker. Check the system requirements specified by Docker to confirm compatibility.
Once you have verified compatibility, you can proceed with the installation process. Download the Docker installation package compatible with Windows 7 from the official Docker website. Ensure that you download the appropriate version for your system architecture.
After the download is complete, locate the downloaded installation package and double-click on it to start the installation process. Follow the on-screen instructions provided by the Docker installer to complete the installation.
Once the installation is finished, verify the successful installation by opening the Command Prompt or PowerShell and running the command "docker --version". If Docker is installed correctly, this command will display the version of Docker installed on your system.
With Docker successfully installed on your Windows 7 system, you are now ready to proceed with further configurations and utilize the Docker platform for your containerization needs.
Step 2: Configuring Docker to Utilize tcp://localhost:2375 without TLS Security
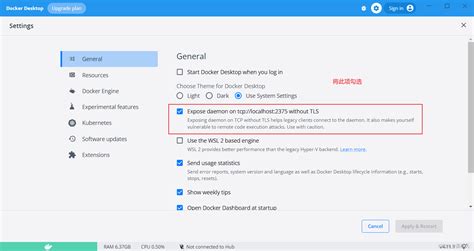
In this section, we will explore the necessary steps to configure Docker for seamless communication without Transport Layer Security (TLS) encryption on the TCP endpoint tcp://localhost:2375. By following the instructions provided, you will be able to establish a connection with Docker without having to enable TLS security, ensuring a streamlined and simplified Docker environment.
- Access Docker Configuration Files:
- Locate the Docker Configuration File:
- Modify the TCP Endpoint Configuration:
- Save and Apply the Changes:
- Test the Configuration:
Initially, you need to locate the Docker configuration files on your system. These files contain the necessary settings to modify Docker's behavior. By accessing these files, you will be able to make the changes required to utilize Docker on the specified TCP endpoint without TLS.
After gaining access to the Docker configuration files, locate the specific file where the TCP endpoint configuration is stored. This file contains various settings related to Docker's network functionality. By pinpointing the correct file, you will be able to modify the relevant configuration for using the tcp://localhost:2375 endpoint without TLS encryption.
Inside the identified configuration file, look for the section that manages the configuration of the TCP endpoint. Within this section, you will find the necessary options to modify the endpoint's behavior. By following the provided guidelines, make the required changes to ensure that Docker can operate on tcp://localhost:2375 without enforcing TLS security.
Once you have modified the TCP endpoint configuration, save the changes made to the configuration file. After saving the modifications, you need to apply the changes to Docker for them to take effect. This process ensures that Docker will utilize the specified TCP endpoint without requiring TLS encryption.
To verify that the configuration was successful, you can perform a test to ensure that Docker can utilize the tcp://localhost:2375 endpoint without TLS security. By following the provided instructions, you will be able to confirm that Docker is now configured to communicate on the specified TCP endpoint without enforcing TLS encryption.
By following the above steps, you can configure Docker to utilize the tcp://localhost:2375 endpoint without the need for TLS encryption. This configuration allows for simplified and streamlined communication with Docker, providing a more efficient and flexible Docker environment for your Windows 7 system.
Step 3: Verifying Docker Connectivity
After setting up the necessary configurations and ensuring a secure connection, it is time to test the connectivity of your Docker environment. This step will help you determine if your Docker client can successfully communicate with the Docker daemon on your local machine.
Follow the steps below to perform the connectivity test:
- Open a command prompt or terminal window on your Windows 7 machine.
- Type in the command to check if the Docker daemon is running:
docker version - If the Docker daemon is running correctly, the command should display the version of Docker that is installed on your system. This indicates that your Docker client is successfully connected to the Docker daemon.
- If you encounter any errors or the command does not display the version information, you may need to troubleshoot the Docker setup and configuration before proceeding further.
By successfully verifying the connectivity between your Docker client and the Docker daemon, you can proceed with confidence to use Docker and leverage its capabilities for your development or deployment needs.
Troubleshooting Common Issues: Overcoming Common Challenges

Even though opening a demon on a specific port without the need for tls may seem straightforward, there can be certain roadblocks that you may encounter along the way. Knowing how to troubleshoot these common issues can save you time and frustration in the process.
- Failure to Connect: If you are unable to establish a successful connection to the desired demon, it could be due to various factors. Common reasons include incorrect port configuration, firewall restrictions, or conflicting software on your Windows 7 system. Checking your network settings and ensuring that the port you're trying to open is available can help resolve this issue.
- Permission Denied: Sometimes, you may encounter permission-related errors when trying to open a demon without tls. This usually happens when the user account you're using doesn't have the necessary privileges to access or modify the required files. To overcome this, you can try running the command prompt or PowerShell as an administrator or adjust the permissions accordingly.
- Security Concerns: It's important to note that bypassing tls and opening a demon on a specific port can pose potential security risks. By disabling tls, you are essentially allowing unencrypted communication, which makes your system vulnerable to attacks. If security is a top concern, consider enabling tls or exploring other secure alternatives.
- Compatibility Issues: Another challenge that may arise is compatibility issues between Docker and your Windows 7 operating system. Docker may not be fully compatible with older systems, resulting in errors or instability. Checking for updated versions, patches, or alternative solutions tailored for Windows 7 can help overcome this obstacle.
By understanding and addressing these common issues, you can increase the likelihood of successfully opening a demon without tls on tcp://localhost:2375 in a Windows 7 environment using Docker. Troubleshooting effectively allows you to optimize your workflow and ensure smooth operation of your Docker containerized applications.
Step 5: Ensuring the Security of the Docker Connection
Protecting the integrity and confidentiality of the Docker connection is crucial to ensure the safety of your system. In this step, we will explore measures that should be taken to secure the communication between the Docker client and the Docker daemon.
Enabling Transport Layer Security (TLS)
To establish a secure connection, enabling Transport Layer Security (TLS) is highly recommended. TLS provides encryption and authentication mechanisms to guarantee that the communication between the Docker client and the Docker daemon remains confidential and secure.
Generating TLS Certificates
In order to enable TLS, you will need to generate TLS certificates. These certificates will be used to authenticate the Docker client and the Docker daemon during the communication process. It is crucial to generate strong and unique certificates to prevent unauthorized access to your Docker environment.
Configuring Docker to Use TLS Certificates
Once you have the TLS certificates generated, you will need to configure Docker to utilize these certificates for secure communication. This involves updating the Docker daemon configuration to specify the path to the TLS certificates and configuring the Docker client to use the appropriate certificates as well.
Implementing Client Authentication
In addition to encryption, implementing client authentication provides an extra layer of security. By enabling client authentication, only authorized clients with valid certificates will be able to access the Docker daemon. This helps to prevent unauthorized access and protects your system from potential threats.
Regularly Updating and Rotating Certificates
Maintaining the security of your Docker environment requires regular updates and rotation of TLS certificates. Over time, certificates may become compromised or outdated, so it is crucial to periodically generate new certificates and rotate them to ensure the ongoing protection of your system.
Continuously Monitoring the Docker Environment
Lastly, it is important to implement a monitoring system to continuously monitor the Docker environment for any security breaches or abnormalities. This will help detect and respond to any potential threats or vulnerabilities promptly, ensuring the overall security and stability of your Docker deployment.
How to Enable HTTPS on your Docker Application
How to Enable HTTPS on your Docker Application by Winston Codes On 74,052 views 5 years ago 8 minutes, 53 seconds
cannot connect to the docker daemon at unix ///var/run/docker.sock. is the docker daemon running
cannot connect to the docker daemon at unix ///var/run/docker.sock. is the docker daemon running by 5-Minute DevOps 48,554 views 3 years ago 1 minute, 36 seconds
FAQ
Is it possible to open a demon on tcp://localhost:2375 without tls in Windows 7 using Docker?
Yes, it is possible to open a demon on tcp://localhost:2375 without tls in Windows 7 using Docker. However, it is important to note that this method is not recommended for production environments due to security concerns.
What is Docker?
Docker is an open-source platform that allows developers to automate the deployment and management of applications using containers. It provides a lightweight and portable environment for running applications.
Why would someone want to open a demon on tcp://localhost:2375 without tls in Windows 7 using Docker?
There can be various reasons why someone would want to open a demon on tcp://localhost:2375 without tls in Windows 7 using Docker. One possible reason is for testing or development purposes where security is not a primary concern. Additionally, some legacy systems may require this setup.
What are the potential risks of opening a demon on tcp://localhost:2375 without tls in Windows 7 using Docker?
Opening a demon on tcp://localhost:2375 without tls in Windows 7 using Docker can pose security risks. Without TLS encryption, communication between the client and the Docker daemon is not secured, making it susceptible to eavesdropping and unauthorized access. It is important to assess the potential risks and consider securing the setup if deploying in a production environment.
Are there any alternatives to opening a demon on tcp://localhost:2375 without tls in Windows 7 using Docker?
Yes, there are alternatives to opening a demon on tcp://localhost:2375 without tls in Windows 7 using Docker. One alternative is to enable TLS encryption for secure communication between the client and the Docker daemon. Another alternative is to use different networking modes or ports to ensure a more secure setup.




