With the ever-increasing reliance on digital communication and data security, it becomes imperative to explore robust and efficient methods for remote access and file transfer. One such method that has gained considerable attention in the tech community is Secure Shell, commonly referred to as SSH. This powerful protocol stands as a shield, safeguarding sensitive information from unauthorized access and ensuring seamless connectivity between different devices.
SSH operates through the use of cryptographic mechanisms, guaranteeing confidentiality, integrity, and authenticity of data transmitted over a network. By employing public key authentication, SSH makes it possible for users to establish secure connections with servers while reducing the risk of eavesdropping, tampering, or masquerading. With SSH, you can go beyond traditional username/password combinations, enhancing your Linux experience with stronger protection.
When utilizing SSH in a Linux environment, you gain access to a plethora of functionalities. These include the ability to execute remote commands, transfer files securely, and even tunnel your network connections. SSH provides a flexible and efficient approach to managing remote Linux systems, streamlining administrative tasks and enabling seamless collaboration across different locations. Whether you are a system administrator or an avid Linux enthusiast, understanding how to leverage SSH can significantly empower your workflow and enhance the overall security posture of your digital environment.
In this article, we will delve into the intricacies of SSH, exploring its underpinnings, practical applications, and configuration options on Linux systems. By delving into real-world examples and best practices, we aim to equip you with the knowledge and skills necessary to harness the full potential of SSH and elevate your remote access and file transfer capabilities. Join us as we dive into the world of Secure Shell and unlock a world of possibilities!
The Significance of SSH in Linux
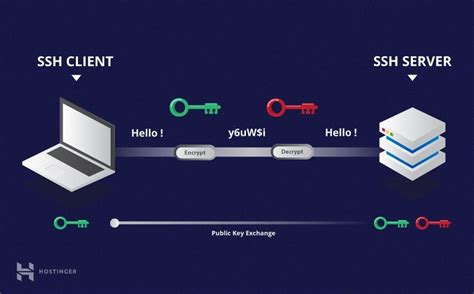
In the realm of Linux operating systems, there exists a powerful tool that plays a vital role in secure remote access and communication. This tool, widely known as SSH, brings forth a multitude of advantages and functionalities, ensuring the integrity, confidentiality, and authenticity of data transmission.
Undoubtedly, SSH holds great importance in the Linux environment due to its unique capabilities. With its secure and encrypted connection, SSH allows users to establish remote connections to Linux systems, enabling them to remotely execute commands, transfer files, and manage the remote system with the utmost confidentiality.
Furthermore, SSH acts as a safeguard against unauthorized access by utilizing cryptographic techniques such as public-key cryptography and symmetric encryption algorithms. Through these mechanisms, users can authenticate themselves securely, preventing potential threats and maintaining the security of the Linux system.
Another essential feature of SSH lies in its ability to create secure tunnels for various applications, enabling protected access to services running on remote machines. This added layer of security prevents sensitive information from being intercepted or compromised during transit, providing a reliable and secure communication channel.
Additionally, the flexibility of SSH allows for the ease of use and seamless integration with other tools and protocols for authentication and authentication forwarding. Its compatibility with various operating systems and the support of advanced options like port forwarding further enhances its significance in the Linux ecosystem.
In conclusion, the importance of SSH in the Linux environment cannot be overstated. Its ability to offer secure remote access, confidential data transmission, and protection against unauthorized access contributes to the overall integrity and security of Linux systems, making it an indispensable tool for administrators and users alike.
| Benefits of SSH in Linux: |
| - Secure remote access |
| - Encrypted data transmission |
| - Protection against unauthorized access |
| - Creation of secure tunnels |
| - Compatibility with various operating systems |
The Essential Elements of Secure Shell (SSH)
In this section, we will explore the fundamental components that make up the Secure Shell (SSH) protocol. Understanding these key elements is essential for anyone looking to establish secure communication and perform various tasks on remote Linux systems without exposing sensitive information.
- Cryptography: Security lies at the heart of SSH, and cryptography plays a crucial role in achieving this. Through the use of encryption algorithms, SSH ensures that data transmitted over the network remains confidential and protected from unauthorized access.
- Authentication: SSH employs multiple methods for authentication, ensuring that the remote server can verify the identity of the client before granting access. These methods can include passwords, public key authentication, and even more advanced techniques such as two-factor authentication.
- Key Exchange: When establishing a connection, SSH employs a secure key exchange mechanism to negotiate and establish a symmetric encryption key. This process enhances the confidentiality and integrity of the communication channel.
- Server and Client: SSH operates in a client-server model, where the client initiates the connection and the server hosts the SSH service. Both the client and server components implement the SSH protocol, allowing for secure communication and remote administration.
- Command Execution: One of the key features of SSH is the ability to execute commands on a remote Linux system. This allows users to perform various tasks, manage files, configure settings, and remotely control the system using the SSH command line interface.
- Tunneling: SSH provides the ability to create secure tunnels, forwarding network traffic through an encrypted channel. This feature is particularly useful for accessing remote services securely or bypassing network restrictions.
By understanding the key components of SSH, users can gain a deeper insight into how this powerful protocol operates and utilize it effectively to secure their remote administration and communication needs.
A Step-by-Step Walkthrough: Implementing SSH for Secure Remote Access

Providing a secure, encrypted connection for remote access to your Linux machines is an essential aspect of maintaining the integrity and confidentiality of your data. In this step-by-step guide, we will explore the process of setting up and using the Secure Shell (SSH) protocol on your Linux system.
Step 1: Install and Configure SSH Server
Firstly, you need to install and configure an SSH server on your Linux system. This will allow you to receive incoming SSH connections from remote clients. The server software should be installed and properly configured to ensure secure communication.
Step 2: Generate SSH Keys
To establish secure communication between the client and server, you will need to generate SSH key pairs. These keys consist of a private key, which should be kept secure and never shared, and a public key, which can be freely distributed to clients. This step is crucial in ensuring authentication and encryption.
Step 3: Connect to SSH Server
Once the server is set up and the key pair is generated, you can connect to the SSH server using your preferred SSH client. Enter the appropriate command, specifying the SSH server address and your login credentials. You may also need to specify the location of your private key if it's not located in the default directory.
Step 4: Configure SSH Access Controls
To enhance security, it is recommended to configure access controls for SSH connections. This can be done by modifying the SSH server configuration file to allow or restrict specific users or IP addresses from accessing the server. By implementing these controls, you can further safeguard your system against unauthorized access.
Step 5: Secure SSH Communication
For added security, it is advisable to disable certain insecure SSH protocol versions and configure stronger encryption algorithms. This can be achieved by modifying the SSH server configuration file to disable outdated versions and enable stronger ciphers. By ensuring secure communication, you can protect your data from potential eavesdropping or tampering.
Step 6: Enable SSH Port Forwarding
SSH port forwarding allows you to securely access services on a remote server, even if they are not directly exposed to the internet. You can set up local ports on your client machine to forward traffic to specific ports on the remote server, enabling you to access those services securely.
Step 7: Monitor and Log SSH Access
To maintain visibility and track SSH access, it is essential to enable logging and monitoring for SSH connections. By reviewing logs, you can detect any suspicious activity or unauthorized access attempts. Implementing this step helps in maintaining the overall security of your Linux system.
In conclusion, understanding and effectively using SSH on your Linux system is crucial for secure remote access. By following this step-by-step guide, you can establish a secure SSH connection, protect your data, and ensure the integrity of your system.
[MOVIES] [/MOVIES] [/MOVIES_ENABLED]FAQ
What is SSH and why is it important for Linux users?
SSH stands for Secure Shell, it is a protocol that enables secure remote access to a Linux system. It provides strong encryption and authentication methods, making it a crucial tool for securely connecting to and managing Linux systems.
How can I install SSH on my Linux system?
To install SSH on your Linux system, you can use the package manager specific to your distribution. For example, on Ubuntu or Debian-based systems, you can run the command "sudo apt-get install openssh-server" to install the OpenSSH server. On Red Hat or CentOS systems, you can use "sudo yum install openssh-server".
What is the default port for SSH and can it be changed?
The default port for SSH is 22. However, it is recommended to change the default port to enhance security and mitigate potential attacks. The port can be changed by modifying the SSH server configuration file, usually located at "/etc/ssh/sshd_config". Look for the "Port" directive and set it to the desired port number, then restart the SSH service.
How can I generate SSH keys for authentication?
To generate SSH keys for authentication, you can use the "ssh-keygen" command. Simply run "ssh-keygen" and follow the prompts. By default, the keys will be saved in the ".ssh" directory in your home folder. The generated keys include a public key that needs to be copied to the remote server's authorized_keys file to allow authentication without a password.
Can SSH be used for file transfer between local and remote Linux systems?
Yes, SSH provides secure file transfer capabilities through the use of the "scp" (secure copy) command. To copy a file from a remote server to your local system, you can use the command "scp username@remote_ip:path_to_remote_file path_to_local_directory". To copy a file from your local system to a remote server, the command is "scp path_to_local_file username@remote_ip:path_to_remote_directory".
What is SSH and why is it important for Linux systems?
SSH stands for Secure Shell and it is a cryptographic network protocol that allows secure communication between two computers. It is important for Linux systems because it provides a secure way to remotely access and manage a server or a computer. With SSH, you can securely log in to a remote system, transfer files, execute commands, and manage network devices.




