In this era of technological advancements, where information exchange has become an integral part of our daily lives, ensuring the protection and integrity of our data has become paramount. It is no secret that cyber threats are on the rise, targeting unsuspecting individuals and organizations alike. One such crucial layer of defense that safeguards our digital fortress is the powerful shield known as the Windows Firewall.
Whether you're a casual user or an IT professional, understanding the importance and functionality of the Windows Firewall is instrumental in fortifying the security posture of your system. Acting as a digital gatekeeper, it monitors the incoming and outgoing network traffic, identifying potentially harmful connections and blocking them. By providing an additional layer of protection against unauthorized access and malicious activities, the Windows Firewall acts as a virtual guardian, protecting your system from cyber threats and keeping your sensitive information safe from prying eyes.
But how can you ensure that your Windows Firewall is configured optimally to effectively shield your system? With a myriad of settings and options available, it can be overwhelming to navigate through the intricacies of its configuration. Fear not, as this article aims to demystify the process and guide you through the steps of configuring the Windows Firewall to suit your specific needs. From defining trusted applications to establishing appropriate inbound and outbound rules, you will learn how to tailor the Windows Firewall to provide a personalized security shield. So, let us embark on this journey to unleash the full potential of your Windows Firewall and bolster your digital defense!
Understanding the Fundamentals of Windows Firewall
Exploring the essential concepts of safeguarding your system and network from unauthorized access and potential threats.
- Introduction to Windows Firewall: Discovering an indispensable security feature offered by the operating system.
- Network Protection: Understanding how Windows Firewall defends your system from malicious activities on both public and private networks.
- Inbound and Outbound Traffic: Examining the distinction between incoming and outgoing data and how Windows Firewall manages and filters them.
- Application Control: Exploring the ability of Windows Firewall to regulate network traffic based on specific applications, ensuring enhanced security and control.
- Setting Up Firewall Rules: Learning the process of configuring rules to allow or block incoming and outgoing connections based on predefined criteria.
- Advanced Firewall Settings: Diving into the advanced options and customizations provided by Windows Firewall to fine-tune its behavior according to your needs.
- Logging and Monitoring: Discovering the logging capabilities of Windows Firewall, enabling you to track and analyze network activity for troubleshooting and security purposes.
- Best Practices for Firewall Configuration: Gaining insights into recommended practices and strategies to optimize the effectiveness of your Windows Firewall setup.
By comprehending the fundamentals of Windows Firewall, you can harness its power to fortify your computer against potential threats and ensure a robust security posture.
Why Ensuring Computer Security is Crucial for Optimal Performance
In today's digital age, protecting your computer from various online threats has become more important than ever. Maintaining a secure online environment is essential to ensure the optimal performance and longevity of your machine. Safeguarding your personal data, sensitive information, and critical system files should be a top priority for every computer user.
Implementing a reliable and effective firewall is one of the fundamental steps you can take to enhance your computer's security. By acting as a barrier between your computer and potential network intrusions, a firewall serves as a gatekeeper that filters out malicious traffic and unauthorized access attempts.
Without a robust firewall in place, your computer becomes vulnerable to a wide range of cyber threats, such as viruses, malware, ransomware, and hacking attempts. These malevolent entities can exploit vulnerabilities in your system, compromise your personal data, disrupt your daily operations, and even cause irreparable damage to your computer.
By configuring and utilizing the Windows Firewall correctly, you can fortify your computer's defense against these threats. This powerful security feature allows you to control incoming and outgoing network traffic, block unauthorized access to your system, and identify and neutralize potential risks.
Windows Firewall empowers you to create custom rules and exceptions, enabling you to specify which programs and services are allowed to communicate over your network. This ability to fine-tune the firewall settings according to your specific needs ensures that your computer remains protected without hindering its daily functionality.
Moreover, Windows Firewall provides you with real-time notifications, which alert you to potential security breaches and suspicious activities, allowing you to take immediate action to mitigate any risks. By actively monitoring your network traffic, you can promptly identify and address any potential security threats before they can cause significant harm to your computer.
Investing time and effort into understanding and properly configuring Windows Firewall is a crucial step in safeguarding your computer and enhancing its overall security posture. By implementing the right security measures, you can provide yourself with peace of mind, knowing that your computer is protected from the ever-evolving landscape of online threats.
Understanding the Various Types of Firewall Rules
In the realm of network security, an important aspect is the implementation of firewall rules. These rules act as a gatekeeper for your computer or network, controlling the flow of data in and out. By understanding the different types of firewall rules, you can effectively safeguard your system from various threats without compromising its performance.
One type of firewall rule is the open rule, which allows specified inbound and outbound traffic based on predefined criteria. This rule is similar to opening a door, enabling certain types of data to pass through while blocking others. It is crucial to define the criteria precisely to avoid any unintended security vulnerabilities.
On the contrary, the closed rule acts as a virtual barrier, denying all traffic that does not meet the specified criteria. This rule enforces a strict policy of blocking any unknown or unauthorized access attempts. The closed rule is like a locked door that only grants access to permitted entities.
Another essential type of firewall rule is the default rule, which determines the behavior when no other rules match the incoming traffic. This rule acts as a fallback option, ensuring that no data is left unattended or goes unnoticed. By defining the default rule appropriately, you can dictate whether to permit or deny traffic that does not match any other predefined rules.
Furthermore, the stateful rule, also known as the dynamic rule, is a type of firewall rule that monitors the state of a connection. It keeps track of the established connections and allows only related traffic to pass, minimizing the risk of unauthorized access. This rule enhances security by validating the legitimacy of incoming and outgoing traffic based on the ongoing communication.
Lastly, the specific rule refers to a granular rule that targets a particular application, service, or port. This type of rule grants precise control over the flow of data, allowing or denying access to specific resources. By implementing specific rules, you can fine-tune the firewall's behavior and tailor it according to the unique requirements of your system or network.
In conclusion, firewall rules are critical components of network security, enabling you to regulate the flow of data and protect your system from unauthorized access. Understanding the different types of firewall rules, including open, closed, default, stateful, and specific rules, empowers you to configure your firewall effectively and enhance the overall security posture of your environment.
Step-by-Step Guide: Setting up Windows Security Barrier on Windows 10
In this section, we will explore the detailed instructions on how to configure the built-in security barrier of the Windows operating system on your Windows 10 computer. By following this step-by-step guide, you will learn how to customize the settings of the security barrier to enhance your system's protection.
To begin, we will first discuss the initial steps required to access the configuration settings. Once you have accessed the settings, we will guide you through the process of identifying the different types of security profiles available. The next step will involve configuring the rules and exceptions for inbound and outbound traffic. Additionally, we will provide you with insights on how to manage notifications and authorized applications. Finally, we will conclude with a section on troubleshooting common issues that may arise during the configuration process.
- Accessing the Windows Security Barrier Configuration Settings
- Understanding Security Profiles
- Configuring Inbound and Outbound Traffic Rules and Exceptions
- Managing Notifications and Authorized Applications
- Troubleshooting Common Configuration Issues
By following this step-by-step guide, you will gain a comprehensive understanding of how to navigate and configure the Windows Security Barrier on your Windows 10 operating system. Utilizing this knowledge, you can customize the security settings to meet your specific needs and ensure optimal protection for your computer.
Customizing Firewall Settings to Suit Your Security Requirements
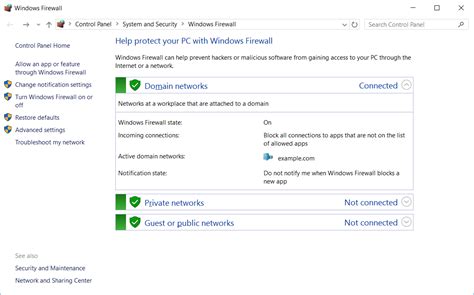
In this section, we will explore the various ways in which you can personalize and adjust the settings of your firewall to effectively meet your specific security needs. By tailoring the firewall configurations to suit your requirements, you can enhance the protection of your system and network against potential threats and vulnerabilities.
| Setting | Description |
| Application Rules | Manage and control the access permissions for individual applications or processes running on your system. By creating specific rules, you can allow or block certain programs from accessing the network, ensuring that only trusted applications are allowed to communicate. |
| Inbound and Outbound Traffic Filtering | Define the rules for incoming and outgoing network traffic to regulate the flow of data. By setting up filters, you can specify which types of connections are allowed or denied, thus preventing unauthorized access and potential attacks. |
| Port and Protocol Management | Manage the ports and protocols used by your firewall to control network traffic. By configuring specific port and protocol settings, you can selectively allow or block certain types of communications, such as restricting access to vulnerable ports or enabling secure communication protocols. |
| Logging and Notifications | Enable logging features to keep track of firewall activities and receive notifications about any suspicious or blocked events. By reviewing the logs, you can identify patterns or anomalies, ensuring that your firewall is effectively guarding your system against potential threats. |
| Advanced Configuration Options | Explore the advanced options available in your firewall settings to further customize the behaviors and functionality. These options may include fine-tuning network profiles, configuring advanced security features, or integrating with other security tools for comprehensive protection. |
By customizing your firewall settings according to your unique security requirements, you can have a granular control over the network traffic, safeguarding your system and sensitive data from potential attacks and unauthorized access. Regularly reviewing and updating these configurations will ensure that your firewall remains effective in mitigating emerging threats in the ever-evolving digital landscape.
Troubleshooting Common Issues with Windows Firewall
When it comes to working with your computer's security measures, it's essential to be aware of potential roadblocks that can occur. In this section, we will examine some common problems that users may experience while dealing with their system's protection settings and delve into effective troubleshooting strategies to overcome them.
One prevalent issue that users may encounter is difficulty in establishing network connections or experiencing intermittent connectivity. This obstacle can be a result of misconfigured firewall settings that inadvertently block incoming or outgoing network traffic. By identifying and rectifying these settings, network connectivity can be restored and uninterrupted.
Another typical issue is software programs or applications being classified as potential threats by the firewall, resulting in restricted access or failure to run entirely. This problem often arises when the firewall's interface fails to recognize trusted applications, leading to unnecessary false alarms. We will guide you through the process of configuring firewall rules to allow specific applications, mitigating such issues and ensuring smooth program execution.
Furthermore, a frequent concern among users is the inability to access network resources or share files and printers due to firewall restrictions. This can occur when the firewall interferes with the necessary communication protocols, preventing seamless data transfer between devices. To address this, we will explore methods to adjust firewall settings and allow network sharing, thereby enabling collaboration and file exchange among connected devices.
In addition to these issues, we will also investigate cases where the firewall itself becomes unresponsive or fails to start, leading to compromised system security. We will discuss potential causes for such occurrences, including conflicts with other security software or corrupted firewall files, and provide step-by-step instructions to troubleshoot and resolve these problems, restoring the firewall's function and safeguarding your system.
By understanding and effectively troubleshooting common issues with your Windows firewall, you can ensure optimal performance and security for your computer, allowing you to browse the internet, run applications, and share resources without restrictions or concerns.
| Common Issues | Troubleshooting Strategies |
|---|---|
| Network connectivity problems | 1. Check firewall settings and allow necessary network traffic 2. Verify network adapter configurations |
| Software programs blocked by firewall | 1. Configure firewall rules to allow specific applications 2. Add trusted applications to firewall exceptions |
| Restricted network resource access | 1. Adjust firewall settings to enable network sharing 2. Verify network sharing permissions |
| Unresponsive or non-starting firewall | 1. Identify conflicts with other security software and disable or adjust accordingly 2. Repair or reinstall firewall files |
Using Third-Party Antivirus Software in Conjunction with Windows Firewall

Enhancing Your Digital Security
When it comes to safeguarding your digital presence, a robust and multi-layered approach to security is of utmost importance. While Windows Firewall provides a solid first line of defense against unauthorized network access, combining it with third-party antivirus software offers enhanced protection against an ever-evolving landscape of cyber threats.
The Synergy of Windows Firewall and Third-Party Antivirus Software
Windows Firewall, in its role as a network security feature, performs an essential function by monitoring incoming and outgoing network traffic and blocking potential threats. However, it primarily focuses on managing network connections based on pre-defined rules and lacks the comprehensive malware detection and removal capabilities found in dedicated antivirus solutions.
By integrating a third-party antivirus software alongside Windows Firewall, you can leverage the strengths of both security layers. The antivirus software will provide real-time scanning, proactive threat detection, and advanced malware removal features, while Windows Firewall remains responsible for monitoring network traffic and managing connection policies.
Selecting the Right Third-Party Antivirus Software
Choosing the appropriate third-party antivirus software that complements Windows Firewall requires careful consideration. Look for antivirus solutions that offer seamless integration with Windows operating systems, effective malware detection and removal, regular updates, and a user-friendly interface. Additionally, consider the software's compatibility with Windows Firewall and its ability to work in harmony without conflicts.
Configuring Windows Firewall and Third-Party Antivirus Software
Once you have chosen and installed a compatible third-party antivirus software, you may need to configure both the antivirus software and Windows Firewall to ensure proper functioning without any conflicts. It is essential to consult the user guides or documentation provided by the antivirus software vendor and follow the recommended configuration settings.
In most cases, the antivirus software will integrate with Windows Firewall automatically during installation, allowing necessary communication and granting appropriate permissions. However, if any issues arise, you may need to manually adjust firewall rules or settings to ensure the smooth operation of both security components.
Maintaining Vigilance for Optimal Protection
Using Windows Firewall in conjunction with third-party antivirus software provides a powerful defense against a wide range of cyber threats. However, it is crucial to keep both the antivirus software and Windows Firewall up to date, regularly perform scans, and stay informed about emerging security risks to maintain optimal protection for your system.
Understanding the Vital Role of Windows Firewall in Enhancing Network Security
Introduction: In today's interconnected world, where every device is just a click away from potential threats, network security plays a paramount role in safeguarding sensitive information. One crucial component in fortifying network defenses is the Windows Firewall, an indispensable software built-in to the Windows operating system. This article aims to shed light on the central role that Windows Firewall plays in protecting networks and the vital functions it performs.
Enhancing Network Protection: The Windows Firewall operates as a protective barrier between a computer network and the outside world, monitoring the traffic and communication flow. By scrutinizing incoming and outgoing data packets, Windows Firewall actively prevents unauthorized access and shields the network from potential threats, such as viruses, malware, and malicious intrusions.
Network Access Control: Windows Firewall exercises granular control over network access permissions by analyzing the source and destination of data packets. It empowers users to define rules and policies, allowing or denying specific actions or connections from different networks or IP addresses. This level of control aids in mitigating the risks associated with unauthorized access and ensures a safer computing environment.
Port and Application Filtering: Moreover, Windows Firewall utilizes port and application filtering capabilities to further enhance network security. It enables administrators to specify which ports are open or closed, preventing unauthorized access to specific services or applications. By actively monitoring and controlling network traffic, Windows Firewall helps detect and isolate potential vulnerabilities, reducing the risk of exploitation and unauthorized data leakage.
Notification and Logging: Windows Firewall maintains a log of all its activities, providing administrators with valuable insights into network threats and attempted intrusions. By logging blocked connections or suspicious activities, administrators can identify patterns, analyze trends, and take proactive measures to strengthen network security. Additionally, it can generate real-time notifications, alerting users of potential threats and allowing them to respond promptly to any security breaches.
Conclusion: A robust and well-configured Windows Firewall is an essential component of any network security strategy. Understanding its significant role in protecting networks from external threats and preventing unauthorized access can help organizations establish a secure computing environment. By leveraging the functionalities provided by the Windows Firewall, businesses and individuals can ensure the integrity and confidentiality of their network resources.
Enhancing Security of Remote Desktop Connections Using Windows Firewall
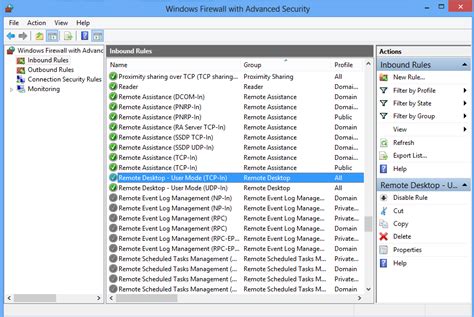
In this section, we will explore the steps to improve the security of remote desktop connections through effective configuration of the built-in firewall in the Microsoft operating system.
With the increasing need for remote access to computer systems, securing remote desktop connections becomes critical for safeguarding sensitive data and preventing unauthorized access. Windows Firewall, an essential component of the Microsoft operating system, offers a robust solution for fortifying the security of remote desktop connections.
By configuring Windows Firewall to specifically allow and restrict network traffic for Remote Desktop Protocol (RDP), we can create a secure communication channel between remote devices and the host system. This ensures that only authorized users with valid credentials can establish remote desktop connections, minimizing the risk of unauthorized access.
- Step 1: Open the Windows Firewall Settings
- Step 2: Create an Inbound Rule for Remote Desktop
- Step 3: Customize Remote Desktop Rule Settings
- Step 4: Enable Network Level Authentication (NLA)
- Step 5: Test the Secure Remote Desktop Connection
These steps not only enhance the security of remote desktop connections but also provide administrators with greater control over network access, reducing potential risks and vulnerabilities. By following these guidelines, organizations can ensure the confidentiality, integrity, and availability of their remote desktop infrastructure.
Windows Firewall vs. Third-Party Firewalls: Pros and Cons
Choosing the right firewall solution is crucial in safeguarding your computer and network from potential threats. While Windows Firewall and third-party firewalls both offer protection against unauthorized access and malicious activities, they differ in terms of features, ease of use, and overall effectiveness. Understanding the pros and cons of each option can help you make an informed decision on which firewall to use for your specific needs.
Windows Firewall, also known as Microsoft Defender Firewall, is the default firewall solution provided by the Windows operating system. It comes pre-installed on all Windows devices and provides a basic level of protection by monitoring inbound and outbound network traffic based on predefined rules. One of the main advantages of Windows Firewall is its seamless integration with the operating system, which ensures compatibility and minimal system resource consumption. However, its limited customization options and basic feature set may not meet the advanced security requirements of some users.
On the other hand, third-party firewalls are developed by independent software vendors and offer a broader range of features and customization options. These firewalls often include advanced intrusion detection and prevention systems, application-specific rules, and more robust logging and reporting capabilities. Third-party firewalls are known for their user-friendly interfaces and enhanced configurability, allowing users to fine-tune security settings according to their specific needs. However, the drawback of using third-party firewalls is the potential for conflicting with the Windows operating system or other security software, leading to compatibility issues and increased resource usage.
In summary, Windows Firewall provides a basic level of protection with minimal system impact, making it a suitable choice for casual users or those who prioritize system integration and simplicity. Third-party firewalls, on the other hand, offer advanced features and customization options, making them ideal for power users or organizations with stricter security requirements. Ultimately, the choice between Windows Firewall and third-party firewalls depends on individual needs, preferences, and the level of security desired.
Remember, regardless of the firewall solution you choose, regular updates, strong passwords, and safe browsing practices are essential in maintaining a secure computing environment.
How to Fix Firewall Blocking Internet Windows 11
How to Fix Firewall Blocking Internet Windows 11 by Ground Zero 15,981 views 1 year ago 2 minutes, 49 seconds
FAQ
What is Windows Firewall?
Windows Firewall is a security feature in Microsoft Windows operating systems that monitors and controls incoming and outgoing network traffic. It acts as a barrier between your computer and potential hackers or malicious software by allowing only authorized connections and blocking unauthorized access.
Why should I configure Windows Firewall?
You should configure Windows Firewall to customize its settings according to your specific needs. By configuring it, you can allow or block certain programs, ports, or protocols, ensuring that your computer is protected from potential threats while still allowing necessary network communication.
How can I access Windows Firewall settings?
To access Windows Firewall settings, go to the Control Panel, then navigate to the "System and Security" section and click on "Windows Defender Firewall." From there, you can configure the firewall settings, enable or disable it, and manage inbound and outbound rules.
What are inbound and outbound rules in Windows Firewall?
Inbound rules in Windows Firewall control the incoming network traffic, allowing or blocking connections to your computer. Outbound rules, on the other hand, manage the outgoing network traffic, determining which programs or services are allowed to initiate connections to external networks. Both inbound and outbound rules play a crucial role in securing your computer.
Can I create custom rules in Windows Firewall?
Yes, you can create custom rules in Windows Firewall. By creating custom rules, you have more control over what network traffic is allowed or blocked on your computer. You can define specific criteria such as programs, ports, IP addresses, or protocols to create rules that suit your specific needs.
What is Windows Firewall?
Windows Firewall is a software program developed by Microsoft to act as a security measure for computers running on the Windows operating system. It helps in blocking unauthorized access to and from your computer, protecting it from potential threats and malicious activity.
Why is it important to configure Windows Firewall?
Configuring Windows Firewall is important as it allows you to have control over which programs and services are allowed to communicate through your computer's network. By configuring it properly, you can enhance the security of your computer and prevent unauthorized access or potentially harmful connections.




