In today's digital landscape, ensuring the security of sensitive data and resources has become a paramount concern for organizations of all sizes. As the sophistication of threats continues to grow, businesses are turning to robust access control systems to safeguard their assets from unauthorized access. While there are various solutions available in the market, Linux emerges as a versatile and highly customizable operating system that can be leveraged to configure and enforce access control policies effectively.
Harnessing the potential of Linux opens up a world of possibilities for organizations seeking to implement a comprehensive access management framework. By utilizing the extensive range of tools and capabilities offered by Linux, administrators can tailor access control systems to their specific requirements and achieve a highly secure environment. This comprehensive guide dives into the intricacies of using Linux to configure access control systems, providing an in-depth exploration of concepts, methodologies, and best practices.
Throughout this guide, we will delve into the foundations of access control, shedding light on the principles and principles that underpin effective security measures. By understanding the core concepts of access control, administrators can establish a solid groundwork for constructing a robust access management system. Moreover, we will explore the significant benefits of employing Linux as the operating system of choice, highlighting its flexibility, scalability, and compatibility with a wide range of hardware and software architectures.
Understanding the Significance and Operation of Access Management Mechanisms
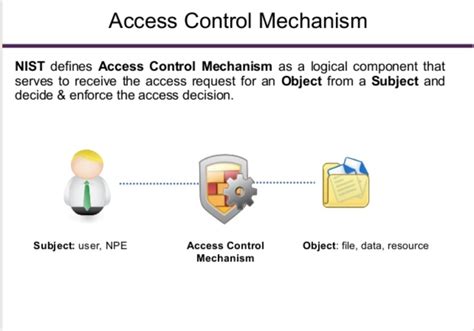
The ability to regulate and monitor access to various resources is a fundamental aspect of maintaining security and privacy within any organization or system. Access control systems play a crucial role in ensuring that only authorized individuals can enter specific premises, access sensitive information, or utilize certain functionalities.
These systems provide a comprehensive framework that enables administrators to define and enforce access policies, granting or denying permissions based on various factors such as user roles, time restrictions, or location. By employing advanced authentication and authorization protocols, access control systems ensure that the right people are granted the appropriate level of access while safeguarding against unauthorized activities.
An understanding of the importance and functionality of access control systems is essential for individuals responsible for designing, implementing, and maintaining secure environments. By comprehending the intricacies of these mechanisms, professionals can effectively configure access controls using Linux or other appropriate technologies, mitigating potential risks, and enhancing overall security posture.
The functionality of access control systems encompasses various components such as authentication, authorization, and accountability. Authentication procedures validate the identity of individuals attempting to access a resource, ensuring that they are who they claim to be. This can involve the use of passwords, biometric scans, or smartcards.
Authorization mechanisms, on the other hand, manage the permissions granted to authenticated individuals. This involves defining access levels or roles and specifying the actions or resources that each role can interact with. By implementing granular permissions, access control systems can restrict certain users from performing sensitive operations or accessing confidential data.
Lastly, accountability ensures that all access-related activities are logged and auditable. Access control systems maintain detailed records of user actions, including login attempts, resource accesses, and modifications made. These audit logs enable organizations to investigate security incidents, track user behavior, and comply with regulatory requirements.
In conclusion, grasping the importance and functionality of access control systems equips individuals with the knowledge necessary to implement robust security measures. By utilizing Linux or similar technologies, administrators can leverage the capabilities of these systems to protect valuable resources, maintain privacy, and establish a secure environment.
Benefits and Advantages of Linux in Access Control Systems
Enhancing security measures through advanced technology is a crucial aspect of any organization's success. In this section, we will explore the benefits and advantages of implementing Linux-based solutions for access control systems. Leveraging the power of open-source software, Linux provides numerous advantages that optimize security, scalability, flexibility, and cost-effectiveness.
- Strong Security: Linux is renowned for its robust security measures, making it an ideal choice for access control systems. With its built-in security features and regular updates, Linux ensures a stable and secure environment, safeguarding the organization's critical data. Additionally, Linux benefits from a large community of developers who actively contribute to security enhancements and bug fixes.
- Customizability: Linux offers unparalleled customizability, allowing organizations to tailor access control systems to their specific requirements. Whether it's implementing unique authentication methods or customizing user access levels, Linux provides the flexibility needed to design and develop tailored solutions.
- Scalability and Performance: Linux systems are known for their scalability and ability to handle large amounts of data efficiently. By leveraging the strengths of Linux, access control systems can seamlessly accommodate the growing needs of an organization without compromising on performance or security.
- Resource Efficiency: Linux is designed to utilize system resources optimally, resulting in better resource management and overall system performance. This ensures that access control systems running on Linux are efficient and reliable, even under high workloads.
- Cost-Effectiveness: Implementing Linux-based access control systems significantly reduces licensing costs when compared to proprietary solutions. Since Linux is an open-source operating system, organizations can enjoy not only cost savings but also the freedom to modify and share the software according to their unique requirements.
In conclusion, when it comes to access control systems, Linux offers a wide range of benefits and advantages. Its strong security measures, customizability, scalability, resource efficiency, and cost-effectiveness make Linux an ideal choice for organizations looking to optimize their security infrastructure. By leveraging Linux-based solutions, businesses can ensure a secure and reliable access control system that meets their specific needs.
Exploring the Advantages of Linux as a Preferred Operating System for Access Control

In this section, we will delve into the reasons why Linux holds a significant position as a preferred operating system when it comes to access control. By examining its key qualities and features, we can gain a deeper understanding of the advantages it offers in this domain.
- Prominent Security Features: Linux has established itself as a stalwart in the realm of security. With its robust architecture and well-regarded reputation for stability, Linux provides a secure foundation for access control systems. Its open-source nature allows a community of developers to constantly identify and address vulnerabilities, resulting in swift and effective patching.
- Flexibility and Customization: The inherent flexibility of Linux is a major reason for its popularity in access control. Its modular design enables the creation of tailored solutions that adapt to the specific needs and requirements of individual access control systems. Administrators can customize access rules, permissions, and protocols, empowering them to create a finely-tuned and secure environment.
- Exceptional Performance and Scalability: Linux is known for its exceptional performance and scalability, attributes that make it an ideal choice for access control. The lightweight nature of the operating system ensures optimized resource utilization, enabling access control systems to effectively handle high volumes of user requests without compromising performance or stability.
- Cost-Effective and Open Source: Linux's open-source nature eliminates the need for expensive licensing fees, providing a cost-effective solution for access control systems. This accessibility encourages a broader community of developers and researchers to contribute to its continuous improvement. Moreover, the vast array of open-source tools and utilities available for Linux simplifies the integration and customization of access control systems.
- Reliability and Long-Term Support: Linux's reliable and long-term support is a key factor in its preference for access control systems. The active development community, combined with the prominent presence of commercial vendors offering support, ensures that Linux remains well-maintained and regularly updated. This reliability translates into enhanced stability and longevity for access control systems.
By exploring these reasons why Linux is a preferred operating system for access control, we can grasp the immense value it brings to this critical aspect of security management. Its security features, flexibility, exceptional performance, cost-effectiveness, and reliability make Linux an ideal choice for organizations seeking robust access control solutions.
A Step-by-Step Walkthrough for Setting up Access Management in Linux
In this section, we will explore the step-by-step process of configuring an access control system using the power and flexibility of a Linux operating system. Throughout the walkthrough, we will cover the various aspects of access management, ensuring secure entry to restricted areas or sensitive files. We will delve into the intricate details of Linux commands, utilities, and configurations needed to establish a robust access control system.
To begin, we will first examine the authentication mechanisms available in Linux, including user-based, group-based, and role-based access control. This comprehensive evaluation helps determine the most suitable approach for the specific requirements of your organization or project. We will illustrate the key differences between these methods and provide guidelines on implementing each one effectively.
Next, we will dive into configuring permissions within the Linux environment. We will explore the concept of discretionary access control (DAC), which provides users with control over their own files and directories. We will discuss how to set file ownership and permissions using the appropriate Linux command-line tools, ensuring that only authorized individuals can read, write, or execute certain files.
In addition to DAC, we will also explore mandatory access control (MAC), which gives the system administrator more granular control over access rights. We will walk you through the process of enabling and configuring mandatory access control frameworks such as SELinux (Security-Enhanced Linux) or AppArmor. These frameworks allow you to define strict security policies, limiting the actions that users and processes can perform within the system.
An integral part of access control systems is the implementation of access control lists (ACLs), which provide a more flexible and fine-grained approach to managing permissions. We will guide you through the process of enabling and utilizing ACLs, allowing you to define additional access rules based on user and group attributes.
Finally, we will explore the importance of periodic audits and monitoring in maintaining an effective access control system. We will discuss various Linux tools and utilities that can help you track and analyze access patterns, detect suspicious activities, and ensure compliance with security policies.
| Key Topics Covered: |
| - Authentication mechanisms in Linux |
| - User-based, group-based, and role-based access control |
| - Configuring discretionary and mandatory access control |
| - Enabling and utilizing access control lists (ACLs) |
| - Auditing and monitoring access control systems |
Practical Tips and Techniques for Effective Configuration of Access Control Systems using Linux
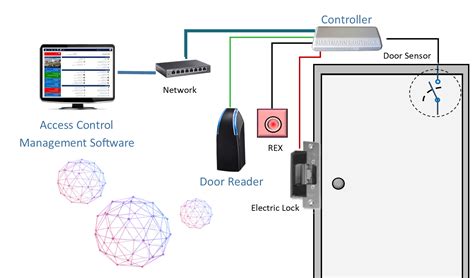
When it comes to configuring access control systems using Linux, there are several practical tips and techniques that can greatly enhance the effectiveness of the system. These tips focus on maximizing security, streamlining administration, and optimizing performance.
- Simplify User Authentication: Enhance security by implementing strong password policies and enforcing multi-factor authentication.
- Implement Fine-Grained Access Control: Use Linux's robust permission system to define access controls at a granular level, ensuring only authorized individuals have access to specific resources.
- Utilize Role-Based Access Control: Streamline administration by assigning roles to users instead of managing access rights individually, making it easier to control permissions across multiple systems.
- Regularly Update and Patch: Stay vigilant against potential vulnerabilities by promptly applying security patches and updates to the Linux system, reducing the risk of unauthorized access.
- Implement Logging and Monitoring: Enable comprehensive logging and monitoring capabilities to track access attempts, detect anomalies, and promptly respond to potential security breaches.
- Secure Remote Access: Safeguard the system by employing secure remote access methods such as encrypted connections and strong authentication mechanisms.
- Regularly Audit Access Controls: Conduct regular audits to review access control configurations, identify any weaknesses, and make necessary adjustments to maintain a robust security posture.
- Implement Intrusion Detection Systems: Enhance the Linux environment's security by deploying intrusion detection systems that actively monitor and alert administrators to potential security threats.
By following these practical tips and techniques, administrators can effectively configure access control systems using Linux, ensuring the highest level of security, streamlined administration, and optimal performance.
How To Set Up an Access Control System: Complete Step-By-Step Guide for Beginners
How To Set Up an Access Control System: Complete Step-By-Step Guide for Beginners by Nelly's Security 238,886 views 4 years ago 30 minutes
60 Linux Commands you NEED to know (in 10 minutes)
60 Linux Commands you NEED to know (in 10 minutes) by NetworkChuck 1,297,523 views 1 year ago 10 minutes, 50 seconds
FAQ
What is this article about?
This article is a comprehensive guide on how to use Linux to configure access control systems.
Why should I use Linux for configuring access control systems?
Linux is known for its robust security features and flexibility, making it an ideal choice for configuring access control systems. It provides various tools and options to ensure efficient access control and enhanced security.
What are the benefits of using Linux for access control system configuration?
There are several benefits of using Linux for access control system configuration. Firstly, Linux offers strong security measures to protect your system from unauthorized access. Secondly, it provides extensive customization options, allowing you to tailor access control settings according to your specific requirements. Lastly, Linux is open-source, meaning it is constantly updated and improved by a large community of developers.
Are there any specific Linux tools mentioned in the article for configuring access control systems?
Yes, the article mentions several Linux tools that can be used for configuring access control systems, such as SELinux (Security-Enhanced Linux), AppArmor, and iptables. Each tool has its own set of features and advantages, so you can choose the one that best suits your needs.
Is prior knowledge of Linux required to configure access control systems?
While prior knowledge of Linux can be beneficial, it is not necessarily required to configure access control systems. The article provides a comprehensive guide that explains the necessary steps and commands in detail, making it accessible even for beginners. However, a basic understanding of Linux operating system and command-line interface would definitely be helpful.




