In the ever-evolving landscape of digital security, staying ahead of potential threats is paramount for both individuals and organizations alike. One powerful tool that has become synonymous with robust security measures is Microsoft's state-of-the-art operating system.
By harnessing the myriad features and functionalities offered by this sophisticated platform, users can bolster their security training initiatives to new heights. In this comprehensive guide, we will delve into the step-by-step process of leveraging the advantages and capabilities of Microsoft's operating system for an enhanced security training experience.
Employing a user-friendly interface, backed by cutting-edge technology, Microsoft empowers users with an array of tools and resources to fortify their understanding of cybersecurity principles. Through this guide, we will explore the various techniques and methodologies that can be harnessed to effectively train individuals or teams while utilizing the immense potential of Microsoft's operating system.
From utilizing enhanced encryption methods to implementing advanced access control mechanisms, this step-by-step guide will equip readers with the knowledge and skills needed to effectively navigate the security landscape using Microsoft's powerful operating system. So, join us on this transformative journey as we unlock the secrets to leveraging Windows for configuring unparalleled security training.
Understanding the Significance of Security Education

In the digital age, knowledge of security measures plays a pivotal role in safeguarding sensitive information and ensuring the smooth functioning of computer networks. This section delves into the importance of security training and the key benefits it provides.
Enhanced Awareness and Vigilance In an ever-evolving landscape of cyber threats and attacks, security training equips individuals with the necessary knowledge and skills to identify potential risks and stay vigilant. By understanding various attack vectors and vulnerabilities, participants become more adept at identifying and responding to security breaches effectively. | Efficient Incident Response Through comprehensive security education, individuals gain insights into the fundamental principles of incident response. Armed with this knowledge, they can effectively analyze and mitigate security incidents, minimizing the potential impact on the organization and preventing future occurrences. |
Protection of Confidential Data Security training empowers individuals to understand the significance of safeguarding confidential data. By learning about data encryption, access control mechanisms, and secure communication protocols, participants can implement robust security measures to protect sensitive information from unauthorized access and potential breaches. | Establishing a Security Culture Security training fosters a culture of security awareness within organizations. By promoting the importance of security policies, best practices, and compliance regulations, individuals become active participants in minimizing security risks and safeguarding valuable resources. This collective effort contributes to a more secure overall environment. |
Understanding the significance of security training is essential in today's interconnected world. The knowledge gained through comprehensive education equips individuals with the necessary skills and mindset to protect vital information, respond effectively to incidents, and contribute to a secure organizational culture.
Understanding and Evaluating Security Risks and Vulnerabilities
In this section, we will delve into the process of comprehending and assessing the potential threats and weaknesses that can compromise the security of a system. By gaining a comprehensive understanding of the risks and vulnerabilities, you will be better equipped to develop effective security measures and strategies.
By exploring the various factors that pose a threat to the system's security, we can identify potential weaknesses and vulnerabilities. It is crucial to recognize that security risks are not limited to external sources such as hackers or malware; they can also originate from internal factors like user errors or system misconfigurations. Understanding the diverse range of risks enables us to develop a holistic approach to security.
Moreover, evaluating the severity and potential impact of these risks is essential for prioritizing security measures. This involves analyzing the likelihood of a threat occurring and the potential damage it can cause. By categorizing risks based on their significance and potential harm, security professionals can allocate resources effectively to address the most critical vulnerabilities.
Throughout this section, we will explore a variety of techniques and tools for assessing security risks and vulnerabilities. These include conducting comprehensive security audits, utilizing penetration testing to identify potential entry points for attackers, and analyzing system logs and events to identify anomalous activities. By employing such techniques, you will be able to identify and mitigate potential threats before they can exploit system vulnerabilities.
In summary, this section focuses on the critical step of assessing security risks and vulnerabilities. By understanding the diverse range of factors that can compromise system security and evaluating their severity, you will be empowered to develop robust security strategies and effectively protect your system against potential threats.
Configuring User Accounts and Password Policies
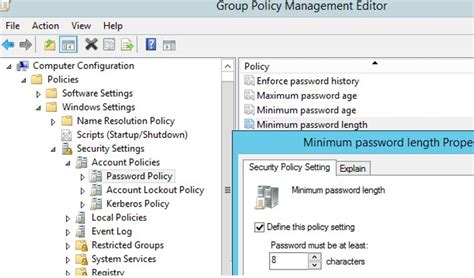
In this section, we will explore the process of customizing user accounts and establishing password policies within the Windows operating system. By tailoring user account settings and defining strong password requirements, you can enhance the security of your system and protect sensitive information from unauthorized access.
Customizing User Accounts:
Windows provides various options for customizing user accounts to meet specific security needs. You can assign different user roles and permissions, create unique account settings, and define restrictions to control user access to resources. By configuring user accounts, you can ensure that individuals have appropriate privileges and only access relevant data.
Establishing Password Policies:
Implementing effective password policies is crucial for safeguarding sensitive data. Windows allows you to set password complexity requirements, including minimum length, the inclusion of numbers and special characters, and regular password expiration. By establishing strong password policies, you can mitigate the risk of unauthorized access and strengthen the overall security of your system.
Enforcing Password Best Practices:
In addition to configuring password policies, it is important to educate users about password best practices. This includes emphasizing the importance of choosing unique, complex passwords, avoiding dictionary words or easily guessable information, and not sharing passwords with others. By promoting password hygiene among users, you can further enhance the security of your system.
Implementing Multi-Factor Authentication:
To add an extra layer of security, Windows offers the option to enable multi-factor authentication. This authentication method combines something the user knows (password) with something they possess (e.g., a fingerprint or a mobile device) to verify their identity. By implementing multi-factor authentication, you can significantly reduce the likelihood of unauthorized access to user accounts.
Monitoring and Auditing User Account Activity:
Windows provides tools to monitor and audit user account activity, enabling administrators to track and analyze user behavior. By monitoring logon and authentication events, administrators can detect suspicious activity, identify potential security breaches, and take appropriate action to protect the system.
In conclusion, configuring user accounts and password policies in Windows is essential for maintaining a secure computing environment. By customizing user accounts, establishing strong password requirements, enforcing password best practices, implementing multi-factor authentication, and monitoring user account activity, you can enhance the overall security posture of your system.
Enhancing Security: Implementing Firewall Configuration
Implementing firewall settings is an essential step towards enhancing security on your system. By configuring the firewall, you can control and monitor incoming and outgoing network traffic, protecting your system from unauthorized access and potential threats. In this section, we will explore the necessary steps to successfully implement firewall settings and ensure enhanced security for your Windows system.
- Assess your network requirements: Before implementing firewall settings, it is crucial to assess your network requirements and understand the potential security risks. Identify the specific needs of your system and define the scope of access that should be allowed or restricted based on your network architecture.
- Select a suitable firewall software: Choose a reliable and robust firewall software that aligns with your system's security requirements. Consider factors such as ease of use, compatibility, and reputation when selecting a firewall solution for your Windows system.
- Configure firewall rules: Once you have selected the appropriate firewall software, it is time to configure the firewall rules. Define rules that determine which network traffic is allowed and which should be blocked. Create rules based on different criteria such as IP addresses, ports, protocols, and applications.
- Monitor and update firewall settings: Regularly monitor and update your firewall settings to stay ahead of emerging security threats. Keep track of any changes in your network environment, and adjust firewall rules accordingly. Stay updated with the latest security patches and software updates to ensure the effectiveness of your firewall configuration.
- Regularly test your firewall configuration: To ensure the integrity of your firewall settings, it is essential to regularly test its effectiveness. Perform comprehensive security assessments and penetration testing to identify any potential vulnerabilities or weaknesses in your firewall configuration.
- Educate and train users: Enhancing security is a collective effort, and it is crucial to educate and train users about the importance of firewall settings and safe browsing practices. Raise awareness about potential security risks and provide guidance on how to identify and report suspicious activities.
By following these steps and implementing firewall settings effectively, you can significantly enhance the security of your Windows system. It is important to remember that a well-configured firewall is just one piece of the security puzzle, and a holistic approach should be adopted to ensure comprehensive system protection.
Securing Network Connections and Wireless Networks

In this section, we will explore strategies and techniques for enhancing the security of your network connections and wireless networks. By implementing appropriate measures, you can protect your network from unauthorized access, data breaches, and potential security threats.
- Secure your Wi-Fi network by changing the default SSID and password.
- Enable encryption protocols, such as WPA2, to ensure the confidentiality of data transmitted over your wireless network.
- Regularly update the firmware of your wireless router to fix security vulnerabilities and improve overall network security.
- Disable SSID broadcast to make your wireless network less visible to potential attackers.
- Implement MAC address filtering to allow only specific devices to connect to your network.
- Enable a firewall on your router to filter incoming and outgoing network traffic.
- Consider using a virtual private network (VPN) to create a secure connection when accessing your network remotely.
- Regularly monitor your network for any unauthorized devices or suspicious activities.
By following these recommendations, you can significantly strengthen the security of your network connections and wireless networks, ensuring the protection of valuable data and sensitive information.
Managing and Monitoring Security Events
In this section, we will explore the vital importance of managing and monitoring security events. Effectively monitoring and auditing security events is essential for maintaining the security and integrity of systems and networks. By actively monitoring and analyzing security events, organizations can detect and respond to potential threats, identify vulnerabilities, and ensure compliance with security policies and regulations.
- Identifying Security Events: The first step in monitoring and auditing security events is to identify the types of events that need to be monitored. This includes activities such as login attempts, changes to user privileges, network traffic, and system modifications. By establishing a comprehensive list of security events, organizations can focus their monitoring efforts on the most critical areas.
- Implementing Security Event Monitoring: Once the types of security events have been identified, organizations can implement tools and technologies to monitor these events. This can include the use of intrusion detection systems (IDS), security information and event management (SIEM) platforms, and log analysis tools. These tools provide real-time monitoring and alerting capabilities, allowing organizations to promptly respond to potential security incidents.
- Analyzing Security Events: The analysis of security events involves reviewing and interpreting the collected data to identify patterns, anomalies, and potential threats. This analysis may require the use of advanced analytics and machine learning techniques to detect unknown or evolving threats. By analyzing security events, organizations can gain valuable insights into the effectiveness of their security measures and identify areas for improvement.
- Responding to Security Incidents: When a security event is identified as a potential incident, organizations must have well-defined incident response processes in place. These processes outline the steps to be taken, the responsible parties, and the necessary actions to mitigate the impact of the incident and prevent further compromises. Timely and effective incident response is crucial in minimizing the potential damage caused by security incidents.
- Regular Auditing and Reporting: In addition to real-time monitoring, regular auditing and reporting of security events are essential for maintaining a strong security posture. Audits help identify weaknesses and potential gaps in security controls, while reports provide a comprehensive overview of the organization's security status. By conducting regular audits and producing detailed reports, organizations can demonstrate compliance with regulatory requirements and identify areas for continuous improvement.
By actively managing and monitoring security events, organizations can proactively detect and respond to potential threats, ensuring the confidentiality, integrity, and availability of sensitive data and systems. Implementing robust monitoring and auditing practices is a critical component of any comprehensive security strategy.
Conditional Access With Microsoft 365 - A Step By Step Guide
Conditional Access With Microsoft 365 - A Step By Step Guide by Jonathan Edwards 10,622 views 1 year ago 14 minutes, 22 seconds
FAQ
What is the purpose of the article "Using Windows for Configuring Security Training: Step-by-Step Guide"?
The purpose of the article is to provide a step-by-step guide on using Windows for configuring security training.
Why is it important to configure security training on Windows?
Configuring security training on Windows is important because it helps users understand how to protect their systems and data from potential threats and attacks.
What are the main steps involved in configuring security training on Windows?
The main steps involved in configuring security training on Windows may include setting up user accounts with appropriate permissions, enabling firewalls and antivirus software, configuring network settings, installing security updates, and implementing suitable password policies, among others.
Is prior experience with Windows necessary to follow this guide?
Prior experience with Windows can be helpful but is not absolutely necessary. The guide is designed to provide step-by-step instructions and explanations, making it accessible for both beginners and those with some experience.




