Empower Your Digital Security with Windows
Enhancing your digital security is essential in the modern world, where cyber threats lurk around every corner. In the realm of data protection, digital certificates play a vital role in safeguarding sensitive information and ensuring secure communication over networks. With Windows, the leading operating system renowned for its user-friendly interface and robust features, you have a powerful tool at your disposal for configuring digital certificates and fortifying your online defenses.
Discover the Secrets of Windows Certificate Configuration
Unlock the potential of digital certificates with Windows, as we unveil the hidden treasures and intricacies of configuring these essential security assets. This comprehensive guide will arm you with the knowledge and techniques needed to navigate the certificate management landscape effortlessly. From generating and installing certificates to configuring trust settings and revocation checks, we will delve into the depths of Windows' certificate tools, empowering you to take control of your digital security like never before.
From Novice to Expert: A Journey Into Digital Certificate Configuration
Whether you are a novice seeking to establish a secure online presence or an experienced professional looking to fine-tune your certificate configuration skills, this article is your ultimate resource. With step-by-step instructions and detailed explanations, we will guide you through the intricate process of configuring digital certificates in Windows. Empower yourself with the ability to tailor certificates to meet your specific needs, ensuring optimal security while minimizing potential vulnerabilities.
Understanding Certificate Configuration in Windows
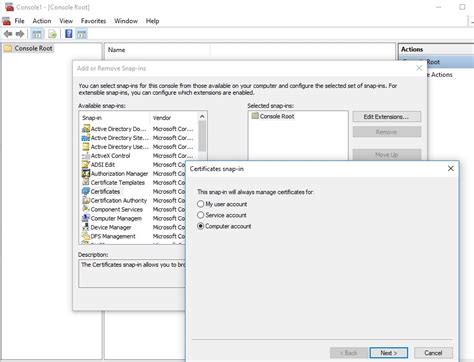
In this section, we will delve deeper into the intricacies of configuring certificates in the Windows operating system. By gaining a comprehensive understanding of certificate configuration, you will be equipped to effectively manage the security and authentication of your Windows-based systems.
Throughout this discussion, we will explore the various aspects of certificate configuration, including the purpose and significance of certificates, the role they play in establishing secure communication channels, and the steps involved in managing and configuring certificates in a Windows environment.
Certificates serve as digital credentials that verify the identity of involved parties in secure online communications. By leveraging cryptographic methods, certificates establish the authenticity and integrity of data transmitted over networks, ensuring that sensitive information remains confidential and unaltered.
Through the process of configuration, certificates are customized and tailored to match the specific needs of individual organizations and systems. This involves tasks such as creating, importing, and exporting certificates, configuring certificate authorities, and managing trust relationships.
Understanding the certificate hierarchy is crucial to grasp the complexity and trust model that underlies certificate configuration. Certificates are organized in a hierarchical structure, with trusted root certificate authorities at the top, intermediate certificate authorities in the middle, and end-entity certificates at the bottom. This hierarchy ensures the propagation of trust throughout the system.
Furthermore, we will explore the key concepts related to certificate configuration, including public key infrastructure (PKI), certificate stores, trust chains, and revocation mechanisms. Understanding these concepts will provide you with a solid foundation to effectively configure and manage certificates in your Windows-based infrastructure.
By the end of this section, you will have a comprehensive understanding of certificate configuration in Windows, enabling you to confidently navigate the intricacies of securing and authenticating your systems through proper certificate management.
Checking Installed Certificates
Verifying the presence of installed certificates is essential for maintaining the security and proper functioning of a Windows system. This section will guide you through the necessary steps to ensure that the required certificates are in place and functioning correctly.
First, it is crucial to determine the ability to access the certificate store within the Windows operating system. This can be achieved by navigating to the appropriate section in the system settings or using command-line utilities. Once in the certificate store, it is important to verify the presence of certificates that are relevant to your specific needs, such as root certificates, intermediate certificates, and personal certificates.
After confirming the existence of the necessary certificates, it is vital to verify their integrity. This involves checking the validity period, ensuring they have not expired, and examining any warning or error indicators related to the certificates. Additionally, it may be necessary to cross-reference the installed certificates with trusted certificate authorities or third-party resources to confirm their authenticity and legitimacy.
In some cases, it may be necessary to inspect the details of specific certificates to gather additional information or troubleshoot certificate-related issues. This can involve examining the certificate's subject, issuer, public key, or other relevant attributes. Understanding the details of installed certificates can aid in identifying any anomalies or potential security risks.
Regularly auditing and reviewing the installed certificates on a Windows system is crucial to maintain a secure and reliable environment. By following the steps outlined in this section, you can ensure that the necessary certificates are present, functioning correctly, and meeting the required security standards.
Exploring and Managing Certificates in Windows
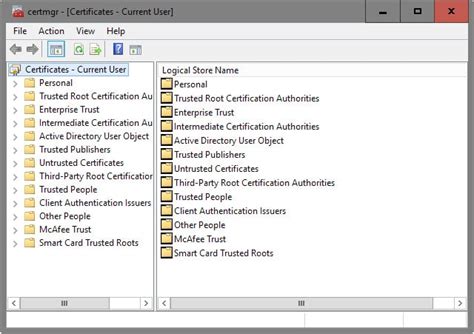
Introduction: In this section, we will delve into the process of viewing and managing certificates in the Windows operating system, offering valuable insights into this crucial aspect of digital security. Certificates play a vital role in verifying the authenticity and integrity of digital information, ensuring secure communication and transactions.
Viewing Certificates: Windows provides users with various tools and utilities to view and examine certificates. This enables users to identify the validity and trustworthiness of certificates associated with websites, software, and other digital entities. By using these tools, users can access detailed information about certificates, including their subject, issuer, validity period, and associated public keys.
Managing Certificates: Windows also offers robust features to manage certificates effectively. Users can perform tasks such as importing and exporting certificates, installing trusted root certificates, revoking certificates, and configuring certificate stores. These management capabilities ensure that users can maintain an up-to-date and secure certificate infrastructure within their Windows environment.
Securing Communications: Understanding how to view and manage certificates in Windows is crucial in securing various forms of communication. Whether it's encrypting emails, securing web browsing, or implementing secure remote access, certificates serve as the foundation for establishing a trustworthy connection. By following the recommended practices in this section, users can enhance their overall digital security posture.
Conclusion: Effectively viewing and managing certificates in Windows is essential for maintaining a secure and reliable digital environment. By utilizing the available tools and capabilities, users can ensure proper certificate validation, enhance communication security, and protect against potential threats. Stay informed and proactive in managing certificates to safeguard your digital assets and mitigate risks effectively.
Importing Certificates from External Sources
In the realm of digital security, it is oftentimes necessary to incorporate certificates obtained from external sources into the operating system. This process, known as certificate importation, allows for the seamless integration of trusted certificates that can bolster the authentication and encryption capabilities of the system. In this section, we will explore the steps involved in importing certificates from external sources, ensuring that the system is fortified with the necessary credentials to establish secure connections.
The first step in importing certificates from external sources is to locate the desired certificate files. These files can be obtained from various sources such as third-party certificate authorities, partnering organizations, or even self-signed certificates generated by individuals or small businesses. Once the appropriate certificate files have been identified, they must be securely transferred to the Windows operating system for further processing.
After the certificate files have been successfully transferred to the system, the next step is to navigate to the Windows Certificate Manager. This powerful tool provides a centralized location for managing certificates and serves as the hub for certificate importation. Within the Certificate Manager, users can access the necessary functions to import, export, view, and manage certificates for different purposes.
To import certificates from external sources, users must select the "Import" function within the Certificate Manager. This will prompt a dialogue box where the user can browse and select the desired certificate files previously transferred to the system. Once the appropriate files have been chosen, the system will guide the user through the importation process, verifying the authenticity and validity of the certificates before incorporating them into the system.
Upon successful importation, the certificates from external sources will be added to the system's certificate store and become available for various cryptographic operations, including secure communication protocols and digital signatures. These imported certificates can then be utilized by applications and services within the Windows environment to establish secure connections and verify the authenticity of remote entities.
In conclusion, the process of importing certificates from external sources plays a vital role in enhancing the security posture of a Windows operating system. By incorporating trusted certificates obtained from trusted sources, users can ensure that their system is equipped with the necessary credentials to establish secure connections and authenticate remote entities. The Certificate Manager serves as the central hub for managing these certificates, providing users with the tools to import, export, view, and manage certificates for different purposes. Through the proper importation of certificates, Windows can maintain a strong foundation of digital security and protect sensitive information from unauthorized access.
Working with the Windows Certificate Store
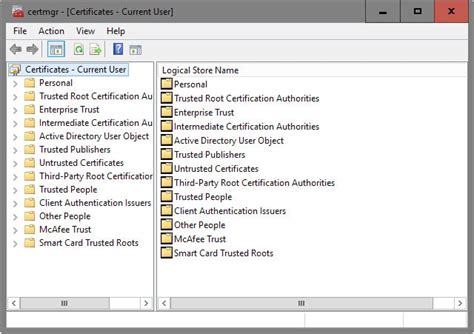
Enhancing the security of your system involves the addition of trusted digital certificates to the Windows Certificate Store. The Windows Certificate Store is a centralized repository that securely stores digital certificates and cryptographic keys to provide authentication and encryption services to various applications and services.
In this section, we will explore the process of adding certificates to Windows Certificate Store, ensuring the integrity and security of your system. We will cover the steps involved, from obtaining the certificate files to importing them into the appropriate store within the Windows operating system.
Firstly, you will need to acquire the digital certificate file or files that you wish to add to the Windows Certificate Store. This can be obtained from a trusted certificate authority or through a self-signed certificate generated by your organization.
Next, we will discuss the different methods available for importing certificates into the Windows Certificate Store. This includes using the Certificate Import Wizard provided by Microsoft Management Console (MMC) or utilizing Windows PowerShell commands for automated processes.
Furthermore, we will explore the options for selecting the appropriate store within the Windows Certificate Store to add your certificates, such as the Trusted Root Certification Authorities store or the Personal store. Understanding the purpose and usage of each store will allow for the correct placement of certificates for different scenarios.
In addition to adding certificates to the Windows Certificate Store, we will also discuss the management and maintenance of certificates within the store. This involves tasks such as renewing certificates, revoking certificates, and removing obsolete or unused certificates to ensure the trust and security of your system.
By following the guidelines and procedures outlined in this section, you will gain the necessary knowledge and skills to confidently add certificates to the Windows Certificate Store, enhancing the security and reliability of your system.
Exporting Certificates for Integration with Other Applications
In this section, we will explore the process of exporting certificates from the Windows operating system in order to integrate them seamlessly with other applications. By exporting certificates, you can ensure secure and reliable communication between various software systems without compromising on data integrity or confidentiality.
- Step 1: Accessing the Certificate Store
Firstly, you need to navigate to the Certificate Store, which contains all the certificates installed on your Windows system. This store acts as a centralized repository for managing digital certificates and cryptographic keys. To access the Certificate Store, follow these steps:
- Open the Windows menu and search for "Certificate Manager."
- Select the "Manage computer certificates" option from the search results.
- Once the Certificate Manager dialog box opens, navigate to the appropriate certificate store.
After accessing the Certificate Store, you need to locate and select the specific certificate that you want to export. This could be a self-signed certificate, a public key certificate issued by a trusted Certificate Authority, or any other type of certificate required by the target application. Follow these steps to select the desired certificate:
- Navigate to the respective certificate store within the Certificate Manager.
- Browse through the list of installed certificates and identify the one you need.
- Right-click on the selected certificate and choose the "Export" option.
Once you have selected the desired certificate, you need to export it in a format that can be easily imported by other applications. Follow these steps to export the certificate:
- In the Certificate Export Wizard, select the appropriate export format, such as Personal Information Exchange (*.pfx) or Base-64 encoded X.509 (*.cer).
- Choose the destination folder where you want to save the exported certificate.
- Provide a meaningful name for the exported certificate file.
- Enter a strong password to protect the exported certificate and confirm the password.
- Review the summary of the export settings and click on the "Finish" button to complete the process.
Now that you have successfully exported the certificate, you can import it into the target application or system where it is required. Follow these steps to import the exported certificate:
- Open the target application or system that needs to use the exported certificate.
- Locate the import function or option within the application or system.
- Select the exported certificate file from the destination folder where you saved it.
- Enter the password you set during the export process to unlock and import the certificate.
- Review any additional settings or configurations related to the imported certificate, if applicable.
- Click on the "Import" or "Finish" button to complete the import process.
By following these steps, you can easily export certificates from Windows and utilize them in other applications or systems, enabling secure communication and seamless integration across various software environments.
Saving Certificates as Files in Various Formats
In the context of configuring certificates on your operating system, it is important to understand how to save these certificates as files in different formats. This section will guide you through the process of exporting certificates and provide an overview of the various formats available.
When managing certificates, it is often necessary to save them as files for various purposes such as sharing, backup, or importing into other systems. Windows provides several file formats that can be used to save certificates.
One commonly used format is the PEM format, which stands for Privacy Enhanced Mail. This format uses Base64 encoding to represent the certificate data, making it readable in text format. PEM files typically have extensions like .pem, .crt, or .cer.
Another format commonly used is the PFX format, also known as PKCS #12. PFX files are password-protected containers that can store one or more certificates along with their corresponding private keys. These files have extensions like .pfx or .p12.
Additionally, the DER format is widely used, especially for certificates that need to be imported into devices or systems with limited storage or processing capabilities. DER files store the certificate data in binary format and have extensions like .der or .cer.
Windows also supports the CER format, which is a variant of the DER format. CER files contain only the public key portion of a certificate and are often used for sharing public keys between systems.
When saving certificates as files, it is essential to understand the specific requirements of the target system or application where the certificates will be used. By choosing the appropriate file format, you can ensure compatibility and successful certificate configuration.
In conclusion, knowing how to save certificates as files in different formats is a crucial skill when configuring certificates. Understanding the characteristics and intended uses of formats like PEM, PFX, DER, and CER can help you effectively manage and share certificates in your Windows environment.
Managing Certificate Revocation Lists (CRLs)
In the realm of ensuring the security and trustworthiness of digital certificates, managing Certificate Revocation Lists (CRLs) plays a vital role. Understanding how to effectively work with CRLs is essential for maintaining a robust certificate configuration.
When it comes to certificate validation, CRLs serve as a critical tool for verifying the status of certificates issued by a certification authority (CA). They provide a list of revoked or invalidated certificates, preventing their usage in secure communications and transactions. By keeping track of revoked certificates, organizations can mitigate potential security risks and protect sensitive information.
- Importance of CRL Distribution Points
- Methods of Obtaining CRLs
- Verifying CRL Signatures
- Strategies for CRL Update Management
- Implementing CRL Auto-Update Mechanisms
- Alternative Approaches to Check Certificate Revocation
Understanding the importance of CRL distribution points is crucial for effective certificate management. This section explores different methods of obtaining CRLs and provides insights on verifying the authenticity of CRL signatures, ensuring their trustworthiness.
To simplify the process of managing CRLs, implementing strategies for CRL update management is essential. This involves establishing suitable schedules and procedures for regularly updating and refreshing CRLs, minimizing potential discrepancies and ensuring the most up-to-date information is used for certificate validation.
Additionally, exploring alternative approaches to check certificate revocation can provide insights into technologies like Online Certificate Status Protocol (OCSP), which offers an alternative to CRLs for real-time certificate status verification.
By effectively managing CRLs, organizations can establish a robust system for ensuring the validity and security of digital certificates, thereby strengthening their overall certificate configuration.
Configuring and Updating CRLs in Windows
In this section, we will explore the process of configuring and updating Certificate Revocation Lists (CRLs) in a Windows operating system. CRLs play a crucial role in ensuring the security and validity of digital certificates by providing information about revoked certificates. By effectively managing and updating CRLs, Windows users can maintain a reliable and trustworthy certificate infrastructure.
To begin, we will discuss the importance of staying up-to-date with CRLs and the potential risks associated with outdated or incorrect information. We will then delve into the various methods available in Windows for configuring CRLs, including both manual and automated options. We will explore how to locate and retrieve CRLs from trusted sources, validate their authenticity, and update them regularly to ensure accurate certificate revocation information.
| Topics Covered: |
|---|
| 1. Understanding the significance of CRLs |
| 2. Configuring CRL distribution points |
| 3. Setting up automatic CRL updates |
| 4. Verifying the authenticity of CRLs |
| 5. Troubleshooting common CRL issues |
In the subsequent sections, we will provide step-by-step instructions and detailed explanations for each configuration method mentioned above. We will explore the Windows Certificate Manager, Group Policy settings, and other relevant tools and utilities to effectively manage CRLs in a Windows environment.
By following the guidance and best practices outlined in this section, Windows users will be equipped with the knowledge and tools to ensure the accuracy and integrity of their certificate revocation information, ultimately enhancing digital security and protecting against potential threats.
Configuring Certificate Trust Chains
In order to establish secure connections and ensure the authenticity of websites, applications, or services, it is crucial to configure the trust chains for certificates in Windows. Certificate trust chains serve as a hierarchical structure that establishes the trustworthiness of a digital certificate within a specific network or system.
When configuring certificate trust chains, it is essential to understand the concept of certificate authorities (CAs) and their role in issuing and verifying certificates. CAs act as trusted third parties that validate the identity and authenticity of individuals, organizations, or devices by digitally signing their certificates.
The configuration process involves several key steps, starting with the installation and management of root certificates, which are the highest level of authority in the trust chain. Root certificates are pre-installed in Windows and are used to verify the authenticity of intermediate certificates, which in turn validate end-entity certificates.
Intermediate certificates are typically issued by trusted root CAs and play a crucial role in establishing the trust chain. They serve as a bridge between the root and end-entity certificates, ensuring the integrity and legitimacy of the entire certificate chain.
Once the root and intermediate certificates are configured and validated, the next step is to configure the trust settings within Windows. This involves adding trusted root certificates to the appropriate trust stores, such as the Trusted Root Certification Authorities store or Intermediate Certification Authorities store.
| Key Steps for Configuring Certificate Trust Chains |
|---|
| 1. Install and manage root certificates |
| 2. Validate and configure intermediate certificates |
| 3. Configure trust settings in Windows |
By properly configuring the certificate trust chains, Windows can establish a secure and trusted environment for various digital transactions, ensuring the integrity and confidentiality of sensitive information.
[MOVIES] [/MOVIES] [/MOVIES_ENABLED]FAQ
How do I configure certificates in Windows?
To configure certificates in Windows, you need to access the Certificate Manager tool. You can do this by searching for "certmgr.msc" in the start menu or the Run dialog box. Once the tool is open, you can manage certificates for various purposes, such as HTTPS, digital signatures, and more.
What are the different types of certificates available in Windows?
Windows supports several types of certificates, including Personal Certificates used for authentication, Secure Email Certificates for email encryption, Code Signing Certificates for software developers, and Trusted Root Certificates used to validate the authenticity of other certificates.
Can I import certificates in Windows?
Yes, you can import certificates in Windows. To do this, open the Certificate Manager tool, navigate to the certificate store where you want to import the certificate (e.g., Personal, Trusted Root Certification Authorities), right-click, and select "All Tasks" > "Import". Follow the instructions in the Certificate Import Wizard to import the certificate.
How do I export certificates in Windows?
To export a certificate in Windows, open the Certificate Manager tool, locate the certificate you want to export in the appropriate certificate store, right-click on it, and select "All Tasks" > "Export". Follow the instructions in the Certificate Export Wizard to export the certificate in a desired format, such as .pfx or .cer.
What is the purpose of certificate revocation in Windows?
The purpose of certificate revocation in Windows is to invalidate a previously trusted certificate. This could be due to various reasons, such as expiration, compromise, or the certificate holder's request. Revocation ensures that applications or processes relying on certificates do not trust any revoked certificate and can take appropriate action.




