A Comprehensive Introduction to Efficient Management of Linux Servers Remotely
In the world of technology, effective management of Linux servers requires the utilization of various tools and protocols. One such protocol that proves to be indispensable for remote server management is SSH, which stands for Secure Shell. SSH is a secure method of connecting to a remote Linux server and executing commands, transferring files, and performing other administrative tasks. This reliable and encrypted protocol provides a secure channel over an unsecured network, ensuring the confidentiality and integrity of data exchanged between the client and the server.
With the exponential growth of remote server management, understanding and implementing SSH has become a crucial skill for system administrators and developers. By utilizing SSH, one can securely access remote servers, perform administrative tasks, and manage the server's configuration without physically being present at the server's location.
SSH offers a range of capabilities that simplify server management, including the ability to execute commands, transfer files, and establish secure tunnels. Through the use of cryptographic keys, SSH ensures secure and authenticated connections, minimizing the risk of unauthorized access and data breach. This protocol also supports features like port forwarding, X11 forwarding, and agent forwarding, granting users the flexibility to access remote resources and services seamlessly.
Whether you are new to the world of Linux server administration or seeking to enhance your existing skills, this article will serve as a beginner-friendly and comprehensive guide to effectively leveraging SSH for remote server management. By exploring the fundamental concepts, practical usage scenarios, and best practices, you will gain the knowledge and confidence to take full advantage of SSH, optimizing your efficiency and productivity in managing Linux servers remotely.
Understanding SSH: Exploring the Basics of Linux Server Administration Remotely
Introduction: This section provides an in-depth examination of SSH, a widely-used protocol for secure remote administration of Linux servers. By delving into the fundamentals of SSH, beginners can gain a comprehensive understanding of its role in managing Linux servers remotely without compromising security.
An Overview of SSH: Before we dive into the technical aspects, it's important to grasp the essence of SSH and its significance in administering Linux servers from a remote location. SSH acts as a secure channel that enables a user to connect to a remote server, execute commands, transfer files, and manage various aspects of the server's configuration.
Key Features and Capabilities: This part explores the essential features and capabilities of SSH that make it an invaluable tool for remote server management. From secure encrypted communication to support for various authentication methods, SSH ensures confidentiality, integrity, and authenticity of data exchanged between the client and the server.
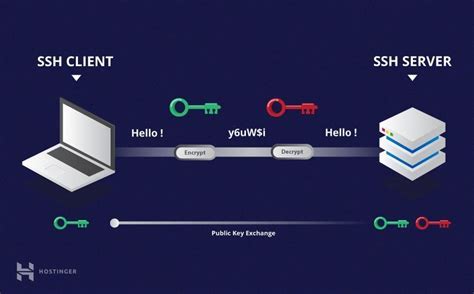
The SSH Architecture: Understanding how SSH operates at a technical level is crucial for effective server management. This section delves into the inner workings of SSH, its client-server architecture, relevant components, and the process flow of establishing a secure connection between the two entities.
Configuring SSH: To use SSH effectively, proper configuration is essential. This part provides step-by-step guidance on configuring SSH in Linux environments, covering key aspects such as generating secure key pairs, modifying configuration files, and implementing server-side security measures.
Conquering Common Challenges: As beginners embark on their journey with SSH, it's vital to be aware of common hurdles and pitfalls. This section discusses common challenges faced during SSH usage and offers troubleshooting tips to overcome issues related to connection failures, access control, and authentication problems.
Best Practices and Security Considerations: Security should be of paramount importance when managing Linux servers remotely. This segment offers best practices for securely using SSH, including guidelines for choosing strong passwords, disabling unnecessary authentication methods, utilizing firewall rules, and implementing multi-factor authentication.
Expanding Your SSH Knowledge: As users gain more experience with SSH, they may want to explore advanced features and additional tools available for optimizing server management. This part introduces various resources, tutorials, and open-source projects that can further enhance SSH usage and provide extended functionality.
Conclusion: By mastering SSH, beginners can unlock the potential of remotely managing Linux servers securely and efficiently. This section provides a recap of the key concepts covered in the article and emphasizes the importance of continuous learning and practice to improve skills in remote server administration.
Understanding SSH: Unveiling the Inner Workings of Secure Shell
Have you ever wondered how you can securely access, manage, and control your remote Linux server from anywhere in the world? The answer lies in the powerful technology called SSH. In this section, we will delve into the fundamental concepts of SSH and explore how it functions to provide a secure and encrypted channel for remote server management.
What is SSH?
SSH, short for Secure Shell, is a network protocol that enables secure communication and data transfer between two networked devices. It offers a secure alternative to traditional protocols like Telnet, FTP, and rlogin, which transmit data in plain text, making them highly susceptible to eavesdropping and unauthorized access.
How Does SSH Work?
At its core, SSH utilizes a client-server model to establish a secure connection between a local computer (client) and a remote server. When a client initiates an SSH connection to a remote server, a series of cryptographic techniques are employed to authenticate both parties and establish a secure connection. This process involves the exchange of public and private keys, encryption algorithms, and challenge-response mechanisms.
Key Components of SSH
SSH consists of three main components: the SSH client, SSH server, and SSH keys. The SSH client is the program running on the local computer that allows users to connect to remote servers. The SSH server, installed on the remote server, handles incoming SSH connections and facilitates secure communication. SSH keys, a pair of public and private keys, play a crucial role in the authentication process and encryption of data.
Benefits of SSH
By leveraging SSH for remote Linux server management, you can enjoy a plethora of benefits. Firstly, SSH ensures the confidentiality of your data by encrypting it during transmission, protecting sensitive information from prying eyes. Secondly, SSH provides strong authentication mechanisms, reducing the risk of unauthorized access and mitigating the chances of security breaches. Lastly, SSH allows for secure file transfers, command execution, and other remote management tasks with ease and convenience.
Setting Up SSH: Step-by-Step Tutorial for Beginners

In this section, we will discuss the process of setting up SSH on your Linux server in a step-by-step manner. By following these instructions, you will be able to establish a secure and convenient connection to your server.
| Step | Description |
|---|---|
| Step 1 | Install OpenSSH Package |
| Step 2 | Generate SSH Key Pair |
| Step 3 | Configuring SSH Server |
| Step 4 | Testing SSH Connection |
| Step 5 | Disabling Password Authentication |
In the first step, we will cover the installation process of the OpenSSH package, which is the most common SSH implementation for Linux systems. This package provides the necessary software for both the SSH client and server.
Next, we will move on to generating an SSH key pair. This involves creating a public and private key that will be used for authentication purposes. The key pair ensures a secure and encrypted connection between the client and server.
After generating the keys, we will proceed with configuring the SSH server. This step involves modifying the server's configuration file to enable specific settings, such as listening on a specific port or restricting specific users from accessing the server.
The fourth step involves testing the SSH connection. We will demonstrate how to use the SSH client to verify that you can connect to the server successfully. This step is crucial to ensure that the SSH setup has been completed correctly.
Finally, we will discuss the importance of disabling password authentication and how to implement this additional security measure. By disabling password authentication, you can rely solely on SSH key-based authentication, which is more secure and less prone to unauthorized access.
Best Practices for Secure SSH Connection and Server Management
In this section, we will explore essential techniques and strategies to ensure a secure and efficient SSH connection and server management. By following these best practices, you can enhance the security of your remote Linux server and effectively manage it.
- 1. Utilize strong authentication protocols:
- 2. Regularly update SSH software:
- 3. Configure SSHd settings:
- 4. Implement firewall rules:
- 5. Monitor SSH logs:
- 6. Regularly change SSH passwords and keys:
- 7. Limit SSH access to specific user accounts:
- 8. Enable two-factor authentication:
Implementing strong authentication methods such as public-key authentication or multi-factor authentication can significantly enhance the security of your SSH connection. These methods provide an extra layer of protection by requiring more than just a password for access.
Keeping your SSH software up to date ensures that you have the latest security patches and bug fixes. Regularly checking for updates and applying them promptly is crucial in mitigating potential vulnerabilities.
Optimize your SSH server settings to restrict access, limit authentication attempts, and enforce strong encryption standards. Adjusting parameters such as MaxAuthTries, PermitRootLogin, and Ciphers can enhance the overall security of your SSH connection.
Utilize a firewall to control incoming and outgoing SSH traffic. By allowing SSH connections only from trusted IPs and blocking suspicious or unauthorized access attempts, you can prevent potential security breaches.
Regularly review SSH logs to identify any suspicious activity, such as failed login attempts or unauthorized access attempts. Monitoring these logs can help you detect and respond to potential security incidents promptly.
To minimize the risk of unauthorized access, it is essential to periodically change your SSH passwords and keys. This practice ensures that even if credentials are compromised, they will become obsolete after a certain period.
Restrict SSH access to only the necessary user accounts. By limiting access privileges to trusted individuals, you minimize the chances of unauthorized access and potential security breaches.
Implementing two-factor authentication adds an extra layer of security by requiring a secondary authentication method, such as a unique code generated on a smartphone app. This additional step provides an added level of protection against unauthorized access.
By following these best practices, you can ensure a secure SSH connection and effectively manage your remote Linux server, protecting it from potential security threats.
[MOVIES] [/MOVIES] [/MOVIES_ENABLED]FAQ
What is SSH and why should I use it for remote Linux server management?
SSH stands for Secure Shell and it is a cryptographic network protocol used for secure remote access to servers. It provides a secure way to manage your Linux server remotely, allowing you to execute commands, transfer files, and administer the server without physically being there.
How can I install SSH on my Linux server?
SSH is usually installed by default on most Linux distributions. However, if it is not installed, you can easily install it by running the following command: 'sudo apt-get install openssh-server' for Ubuntu/Debian or 'sudo yum install openssh-server' for CentOS/RHEL.
How do I connect to a remote Linux server using SSH?
To connect to a remote Linux server using SSH, you need to open a terminal on your local machine and use the following command: 'ssh username@ip_address'. Replace 'username' with your username on the remote server and 'ip_address' with the IP address of the server. You will then be prompted to enter your password for authentication.
Is it possible to use SSH without entering a password everytime?
Yes, it is possible to use SSH without entering a password every time by setting up SSH key authentication. This involves generating a public and private key pair on your local machine and adding the public key to the remote server. Once set up, you can log in to the remote server without entering a password by using your private key.
Can I transfer files between my local machine and a remote Linux server using SSH?
Yes, you can transfer files between your local machine and a remote Linux server using SSH. One way to do this is by using the 'scp' command, which stands for secure copy. It allows you to securely copy files between your local machine and a remote server using SSH encryption.




