In today's hyperconnected world, safeguarding sensitive data and securing critical systems is of paramount importance. With the growing concerns surrounding unauthorized access and data breaches, organizations are seeking robust solutions to bolster their security measures. One effective way to achieve this is by leveraging the power of an efficient operating system to establish comprehensive access control mechanisms.
Enhancing the protection of your IT infrastructure
Access control refers to the practice of granting or revoking permissions to users, ensuring that only authorized individuals have the ability to perform specific actions within a system. By utilizing Linux, a versatile and open-source operating system, organizations can implement a wide array of access control mechanisms to fortify the security of their infrastructure.
Achieving granular access permissions
Linux offers a multitude of powerful tools and features that enable administrators to tailor access permissions according to their specific requirements. From using access control lists (ACLs) to specify fine-grained permissions on individual files or directories, to utilizing role-based access control (RBAC) frameworks to assign privileges based on user roles, Linux empowers organizations to establish granular control over their system resources.
Why Linux is an Ideal Platform for Establishing Security Measures

When it comes to implementing robust security solutions for safeguarding sensitive data and restricting unauthorized access, Linux stands out as an exceptional platform. With its robust architecture and versatile capabilities, Linux provides a solid foundation for establishing effective system access control measures.
Linux, renowned for its stability, compatibility, and scalability, offers an array of features that make it an ideal choice for enforcing security in various environments. Its open-source nature allows for continuous improvement and frequent security updates, ensuring that vulnerabilities are promptly addressed. Furthermore, Linux's flexibility enables customization, making it adaptable to diverse security needs.
In addition to its technical advantages, Linux has a vibrant community of developers and system administrators who actively contribute to the enhancement of its security features. This collaborative effort results in constant improvements, advanced tools, and comprehensive documentation, creating a supportive environment for implementing effective system access control measures.
Moreover, Linux's implementation of access control mechanisms, such as Mandatory Access Control (MAC) and Discretionary Access Control (DAC), allows for granular control over user privileges and system resources. Through these mechanisms, administrators can define and enforce strict access policies, ensuring that only authorized individuals can access critical data and perform privileged operations.
Linux also boasts a wide selection of reliable and efficient security tools, such as firewall solutions, intrusion detection systems, and file integrity checkers. These tools, coupled with Linux's robust security features, provide comprehensive protection against external threats and unauthorized system access.
Overall, Linux's inherent security features, extensive community support, and customizable nature make it an ideal platform for implementing rigorous system access control measures. Its versatility and ongoing development efforts ensure that Linux remains at the forefront of secure computing environments, protecting critical assets and maintaining data integrity.
Enhanced Security
In the realm of safeguarding digital assets, an advanced approach to ensuring the integrity, confidentiality, and availability of sensitive information is paramount. This section delves into elevating the security measures beyond the standard levels by exploring alternative strategies and techniques.
Strengthening Defenses:
To fortify the shield against potential threats, it is imperative to employ robust security mechanisms that go beyond the conventional methodologies. By implementing advanced protocols and practices, it becomes possible to minimize vulnerabilities and maximize the resilience of the system.
Multi-layered protection:
Enhancing security involves erecting a multi-layered defense architecture. This approach combines various security components, such as firewalls, intrusion detection systems, encryption algorithms, and access control mechanisms, to create a comprehensive security framework that safeguards the system from internal and external risks.
Continuous monitoring and detection:
Ongoing surveillance is one of the key pillars in achieving enhanced security. By implementing effective monitoring tools and procedures, any unauthorized activities or abnormal behaviors can be swiftly identified and mitigated, ensuring that the system remains protected from potential threats at all times.
Secure remote access:
Enabling secure remote access capabilities allows authorized personnel to access critical resources from remote locations without compromising the system's security. By utilizing encrypted communication protocols, strong authentication methods, and secure virtual private networks (VPNs), the risks associated with remote access can be minimized.
Regular security audits and updates:
Maintaining a proactive approach to security involves conducting regular security audits to identify and fix any existing vulnerabilities. Additionally, staying up-to-date with the latest security patches and updates ensures that potential security flaws are promptly addressed and mitigated, providing an added layer of security to the system.
In summary, the section on enhanced security explores advanced strategies and techniques to strengthen the overall security posture. By employing multi-layered defense mechanisms, continuous monitoring, secure remote access, and regular security audits, it becomes possible to enhance the security of the system and mitigate potential risks.
Flexibility in Access Control Policies
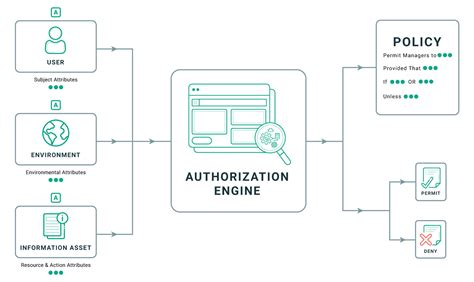
In the realm of managing permissions and regulating user activities, Linux offers a wide range of options, allowing for flexibility in defining access control policies. This versatility empowers administrators to tailor access rights and restrictions based on the specific needs of their systems and organizations, ultimately ensuring a secure and efficient environment.
Customization: Linux provides a multitude of methods for customizing access control policies, enabling administrators to create finely-grained rules that align with the unique requirements of their systems. By utilizing various tools and techniques, such as role-based access control (RBAC), mandatory access control (MAC), or user and group permissions, administrators can dynamically manage the access privileges of individual users or groups within the system.
Scalability: The flexibility offered by Linux in terms of access control policies extends beyond individual systems. With Linux-based solutions, administrators can effortlessly define and apply access rules across multiple machines or distributed networks. This scalability is particularly beneficial for large organizations and enterprises, as it simplifies the centralized management of access control and ensures consistent policy enforcement across all interconnected systems.
Adaptability: In a constantly evolving technological landscape, Linux's flexibility in access control policies allows for smooth adaptation to new security challenges and requirements. Whether it involves integrating with external authentication systems, incorporating advanced access control mechanisms, or accommodating changes in user roles and responsibilities, Linux ensures that access control policies can be updated and reconfigured with minimal disruption to the overall system.
Enhanced Security: By leveraging the flexible access control capabilities of Linux, system administrators can enhance the security posture of their systems. The ability to finely define permissions and restrictions helps mitigate potential risks and unauthorized access, reducing the potential impact of security breaches. This promotes a secure computing environment and protects sensitive data and resources from unauthorized access or malicious activities.
In summary, Linux's flexibility in access control policies offers administrators the ability to create highly customized and scalable access rules, adapt to changing security requirements, and enhance the overall security of their systems.
Comprehensive User Management
In this section, we will explore the crucial aspect of user management in the context of Linux administration. Efficient user administration is a fundamental part of maintaining a secure and organized system environment.
Ensuring user accountability
User management involves creating, modifying, and deleting user accounts, as well as assigning specific access privileges and roles to each user. By implementing a comprehensive user management system, administrators can ensure accountability and minimize security risks.
Managing user permissions
One key aspect of user management is controlling user permissions and access rights. This allows administrators to grant or deny specific privileges to users, restricting their ability to perform certain actions or access sensitive information. Effective permission management is critical for maintaining data integrity and preventing unauthorized access.
Implementing user groups
Creating user groups is an efficient way to manage user accounts with similar characteristics or permissions. Group membership simplifies the process of assigning privileges to multiple users simultaneously, streamlining administrative tasks and reducing complexity.
Authentication and password management
Implementing robust authentication mechanisms and enforcing password policies are essential for ensuring system security. User management includes setting up strong password policies, regular password expiration, and enforcing two-factor authentication where necessary. These measures enhance system protection against unauthorized access and malicious activities.
Auditing user activity
An integral part of user management is auditing user activity to monitor system logs and track user actions. By implementing proper auditing practices, administrators can identify potential security breaches, detect any unauthorized activities, and take necessary actions promptly.
Effective user management plays a vital role in maintaining the integrity, security, and efficient operation of a Linux-based system. By implementing comprehensive user administration practices and utilizing various tools and techniques, administrators can establish a robust system access control environment.
Fine-tuning Privileges with Granular Control
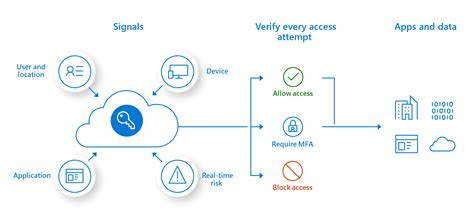
In this section, we explore the concept of carefully tailoring and refining access privileges within a Linux environment. Through a meticulous approach, we can achieve an elevated level of control over the specific permissions granted to different users or groups, enhancing security and optimizing system performance.
By delving into the intricacies of access controls, we unlock the ability to finely adjust the capabilities and limitations for various entities within the system. This granular control empowers administrators to allocate privileges on a more detailed level, ensuring that each user or group is granted only the necessary authority required to perform their respective tasks.
Through the utilization of powerful mechanisms, such as user-based permissions, role-based access control, and mandatory access control, we can establish a robust framework for managing privileges. By carefully defining and assigning roles, administrators gain the ability to allocate permissions based on a user's specific responsibilities, enhancing overall system security and maintaining the principle of least privilege.
Furthermore, in order to provide a comprehensive solution, we also explore the concept of access control lists (ACLs). By leveraging ACLs, administrators can extend and customize the standard Linux permissions model, granting or denying specific permissions to individual users or groups on a per-file or per-directory basis. This level of control enables targeted fine-tuning of access privileges, promoting a more secure and efficient system environment.
In summary, this section delves into the concept of granular control over privileges within the Linux ecosystem. By carefully tailoring access controls and utilizing mechanisms such as user-based permissions, role-based access control, mandatory access control, and access control lists, administrators can achieve a heightened level of control, enhancing security and optimizing system performance.
Integration with existing Authentication Systems
Incorporating existing authentication systems into a Linux-based access control setup enables enhanced security and streamlined user management. By seamlessly integrating with external authentication systems, organizations can leverage their existing user databases and access control policies, minimizing the need to manually manage user accounts and access privileges.
Advantages of Integration:
Enhanced Security: Integrating with existing authentication systems allows organizations to leverage advanced security features already in place, such as multi-factor authentication and password complexity requirements. This ensures that access to critical systems and resources remains secure.
Streamlined User Management: By integrating with existing authentication systems, organizations can centralize user management processes, eliminating the need for separate user accounts and access control mechanisms. This simplifies user provisioning, deprovisioning, and role-based access assignment.
Reduced Administrative Overhead: Incorporating existing authentication systems into the Linux-based access control setup reduces administrative overhead by eliminating the need to duplicate user accounts, passwords, and access control policies. This saves time and effort for system administrators.
Integration Methods:
LDAP Integration: Linux provides support for integrating with Lightweight Directory Access Protocol (LDAP) servers, allowing organizations to authenticate and authorize users against their LDAP directory. This enables seamless integration with existing directory services, such as Microsoft Active Directory or OpenLDAP.
Single Sign-On (SSO) Integration: Linux supports the integration of existing Single Sign-On solutions, enabling users to authenticate once and gain access to multiple systems or applications. SSO integration simplifies the user experience and reduces the need for multiple sets of credentials.
Authentication Proxy Integration: Organizations can utilize authentication proxies, such as SAML or OAuth, to integrate Linux-based access control systems with existing authentication infrastructure. This enables secure and standardized authentication across multiple platforms.
By integrating Linux-based access control systems with existing authentication systems, organizations can maximize security, streamline user management processes, and minimize administrative overhead. This facilitates efficient and secure access to critical systems and resources, while leveraging the advantages of existing authentication infrastructure.
Simplified Auditing and Compliance Monitoring

In this section, we will explore a simplified approach to auditing and compliance monitoring in the context of utilizing the powerful capabilities of Linux for system access control. By implementing efficient auditing practices and robust compliance monitoring measures, organizations can ensure that their systems adhere to the established security policies and regulations without compromising performance or overwhelming system administrators.
One key aspect of simplified auditing is the utilization of comprehensive logging mechanisms to track and record relevant system activities. By leveraging Linux's log files and command-line tools, administrators can gain valuable insights into user activities, network connections, and system events. This detailed information allows for precise monitoring and analysis, aiding in identifying potential security breaches, detecting unauthorized access attempts, and mitigating the impact of malicious activities.
Furthermore, by implementing automated audit log analysis tools, organizations can simplify the process of monitoring and reviewing system logs. These tools can intelligently analyze log files, identify patterns, and generate concise reports, reducing the manual effort required and streamlining the auditing process. By adopting such tools, administrators can efficiently identify and address any deviations from the defined security policies, ensuring compliance with regulatory standards and organizational guidelines.
Another aspect of simplified auditing is the implementation of proactive alerting mechanisms. By configuring Linux systems to generate real-time alerts based on predetermined criteria, administrators can promptly identify critical security events and take immediate action. These alerts can be triggered by events such as failed login attempts, changes to system configurations, or suspicious user activities, enabling administrators to respond swiftly and effectively to potential security threats.
In addition to auditing, compliance monitoring plays a vital role in maintaining system security. By utilizing Linux's capabilities for monitoring file integrity, network traffic, and system configurations, organizations can effectively ensure compliance with industry regulations and internal policies. Automated integrity checkers, network monitoring tools, and configuration management systems allow for continuous monitoring, enabling administrators to identify any unauthorized changes or deviations and promptly initiate corrective actions.
In conclusion, simplified auditing and compliance monitoring are critical components of a robust system access control strategy. By leveraging Linux's features and tools in logging, analysis, alerting, and monitoring, organizations can streamline auditing processes, mitigate security risks, and demonstrate adherence to regulatory standards. The implementation of efficient auditing and compliance monitoring measures strengthens overall system security and contributes to the establishment of a secure and compliant environment.
Access your PCs from ANYWHERE with REMOTE DESKTOPS (Linux, Mac, and Windows)
Access your PCs from ANYWHERE with REMOTE DESKTOPS (Linux, Mac, and Windows) by The Linux Experiment 132,896 views 9 months ago 15 minutes
FAQ
What is system access control?
System access control refers to the methods and mechanisms used to manage and restrict access to computer systems and resources. It involves implementing policies and settings to ensure that only authorized users can access certain files, applications, or system functions.
Why is system access control important?
System access control is important for several reasons. It helps protect sensitive data and resources from unauthorized access or misuse. It also helps prevent malicious activities such as hacking, data breaches, or unauthorized changes to the system. Additionally, access control enhances user accountability and allows for better auditing and compliance with security regulations.
How can Linux be used to set up system access control?
Linux offers various tools and features to set up system access control. One of the most commonly used tools is the Linux permissions system, which assigns different read, write, and execute permissions to files and directories for different users or user groups. Linux also provides the ability to create user accounts with specific privileges, implement firewall rules, and utilize access control lists (ACLs) for fine-grained control over permissions.
What are some best practices for implementing system access control on Linux?
There are several best practices for implementing system access control on Linux. Firstly, it is important to regularly update the system and keep all software and packages up to date to prevent security vulnerabilities. Additionally, enforcing the principle of least privilege is crucial, meaning that users should only have the minimum level of access necessary to perform their tasks. Implementing strong password policies, enabling two-factor authentication, and regularly reviewing and monitoring access logs are also important practices for robust system access control.




