Integrating cutting-edge technology into the realm of electronic payments has become indispensable for businesses seeking a competitive edge in the modern marketplace. With the continual evolution and growth of digital transactions, companies are increasingly relying on robust, secure, and efficient systems to handle their financial operations. In this context, the adoption of open-source software emerges as a viable and strategic choice for configuring electronic payment systems.
By harnessing the power of open-source software, businesses can tap into a vast array of benefits that enhance their payment processing capabilities. Firstly, the flexibility and adaptability inherent in these software solutions empower companies to tailor their electronic payment systems according to their unique requirements. The customizable nature of open-source software enables enterprises to mold and shape their payment infrastructure to align seamlessly with their specific goals, whether it be streamlining processes, boosting security measures, or optimizing transaction speed.
Moreover, open-source software fosters an environment of innovation and collaboration. Thanks to the transparent nature of these platforms, businesses can gain insights and contributions from an extensive community of developers, experts, and enthusiasts worldwide. This collective brainpower ensures that open-source software continually evolves, improves, and remains at the forefront of technological advancements. Organizations can thus leverage the expertise and experience of this global community to refine their electronic payment systems and stay one step ahead in an ever-evolving digital landscape.
Additionally, the cost-efficiency of open-source software cannot be understated. Unlike proprietary software, which often comes with a hefty price tag, open-source solutions offer businesses an economical alternative without sacrificing quality or functionality. With open-source software, companies can avoid expensive licensing fees, reduce maintenance costs, and allocate their financial resources towards other critical business areas. This financial freedom allows enterprises to invest in cutting-edge hardware, robust security measures, or supplementary features that enhance their overall payment system performance.
In conclusion, embracing open-source software for electronic payment system configuration is a strategic move for any business aiming to unlock unparalleled advantages. The flexibility, collaborative environment, and cost-efficiency of open-source solutions position companies for success in an increasingly digital world. By harnessing the power of open-source software, organizations can build robust and secure payment systems that adapt to their unique needs while tapping into the collective knowledge and innovation of a global community.
Ensuring Security: Exploring the Advantages of Linux for Safeguarding Electronic Payment Systems
In the realm of electronic payment systems, selecting a reliable and secure platform for configuration is of utmost importance. This article discusses the reasons why Linux emerges as a robust choice for securing electronic payment systems, emphasizing its numerous advantages and features that contribute to enhanced security.
1. Open Source Advantage: Linux's open-source nature allows for constant scrutiny and peer review, greatly reducing the risks of vulnerabilities and ensuring the system remains up-to-date with the latest security patches. |
2. Stability and Reliability: Linux is renowned for its stability and reliability, offering a solid foundation for electronic payment system configurations. Its robust architecture minimizes the possibility of failures or crashes, ensuring uninterrupted operation and secure transactions. |
3. Customization and Flexibility: Linux provides extensive customization options, enabling system administrators to tailor the configuration to specific security requirements. This flexibility allows for the implementation of advanced security measures and the integration of additional security tools. |
4. Strong Community Support: The Linux community is vast and active, actively collaborating to enhance security and address any issues that may arise. This collective effort fosters a robust ecosystem centered around security, resulting in timely support and continuous improvement. |
5. Privilege Separation: Linux employs a strict privilege separation mechanism, ensuring that different processes and users operate in isolated environments. This approach significantly mitigates the risk of unauthorized access, protecting sensitive payment data from potential threats. |
Overall, Linux emerges as a highly secure choice for configuring electronic payment systems, offering a combination of open-source transparency, stability, flexibility, community support, and robust privilege separation mechanisms. By leveraging these advantages, businesses can ensure the utmost security of their electronic payment systems and protect sensitive customer information.
Enhancing Security: The Robust Features of Linux
In the realm of digital transactions and payment systems, the importance of high-level security measures cannot be overstated. To safeguard sensitive financial information, Linux offers a range of robust features that make it a preferred choice for configuring electronic payment systems. This section explores the key security aspects of Linux that contribute to its reputation as a secure operating system.
Customization Options in Linux for Enhanced Configuration
In the realm of electronic transactions, the versatility and adaptability of the Linux operating system opens up a world of customization possibilities for optimizing the configuration of payment systems. By leveraging the rich features and functionalities provided by Linux, businesses can tailor their payment systems according to their unique requirements, enhancing security, efficiency, and user experience.
Enhanced Security:
Linux provides a robust foundation for securing electronic payment systems through customization. By leveraging various security options, such as encryption algorithms, access controls, and firewalls, businesses can fortify their payment systems against potential vulnerabilities and safeguard sensitive customer data.
Efficiency Optimization:
With Linux, businesses have the flexibility to fine-tune their payment systems for optimal performance and efficiency. Through customization options like process optimization, resource allocation, and load balancing, organizations can ensure smooth and seamless payment transactions, even during peak periods of activity.
User Experience Enhancement:
Linux offers a wide array of customization options to enhance the user experience of electronic payment systems. By customizing the graphical user interface (GUI), businesses can create intuitive and user-friendly interfaces, simplifying the payment process for both customers and employees. Integration with external devices, such as card readers and biometric scanners, further enhances the user experience by providing convenient and secure authentication methods.
Adaptability to Business Needs:
Linux's open-source nature empowers businesses to customize their payment systems according to their specific needs. Whether it's integrating with existing infrastructure, implementing proprietary software, or adapting to evolving industry standards, Linux provides the flexibility and extensibility required to tailor electronic payment systems to meet the unique demands of different businesses.
In conclusion, Linux offers an abundance of customization options for optimizing the configuration of electronic payment systems. From enhancing security and efficiency to improving the user experience and adapting to diverse business needs, Linux's versatility makes it an ideal choice for businesses seeking to maximize the potential of their payment systems. By harnessing the power of Linux customization, organizations can create tailored solutions that meet their requirements while ensuring secure and convenient electronic transactions.
Key Considerations for Configuring Electronic Payment Systems on Linux
In this section, we will discuss important factors to consider when configuring electronic payment systems on the Linux operating system. Understanding these key considerations is essential for ensuring the security, stability, and efficiency of your payment system.
- Compatibility: Ensuring that your chosen electronic payment system is compatible with the Linux operating system is crucial. This includes verifying that the software, hardware, and network components work seamlessly together.
- Security: Implementing robust security measures is vital to protect sensitive payment data. This involves utilizing encryption techniques, implementing firewall configurations, and regularly updating security patches and software versions.
- Integration: Seamless integration with existing systems is another crucial aspect. Ensure that your electronic payment system is capable of integrating with other software and hardware components, such as ERP systems, point-of-sale terminals, and financial institutions' networks.
- Performance: Configuring your electronic payment system to achieve optimal performance is essential to ensure swift and reliable payment transactions. This can include optimizing hardware resources, network connectivity, and software configurations.
- Compliance: Adhering to industry standards and regulations is imperative in electronic payment system configurations. Make sure your system is compliant with Payment Card Industry Data Security Standard (PCI DSS) requirements and other applicable regulations to prevent breaches and legal complications.
- Maintainability: Regular monitoring, maintenance, and updates are necessary to keep your electronic payment system running smoothly. Implement proper backup and disaster recovery measures to minimize downtime and ensure business continuity.
By considering these key factors, you can confidently configure electronic payment systems on the Linux operating system, enabling secure, efficient, and reliable payment transactions.
Choosing the Right Linux Distribution for your Payment Solution

In order to ensure the secure and reliable operation of your payment solution, it is crucial to choose the most appropriate Linux distribution for your specific requirements. This article will guide you through the factors to consider and provide valuable insights on making the best choice.
Consider the Security: One of the primary concerns when selecting a Linux distribution for your payment system is the level of security it offers. Look for distributions that have a strong track record in terms of regular security updates and a vigilant community that actively identifies and patches vulnerabilities.
Assess the Stability: A stable Linux distribution is essential for an electronic payment system, as any downtime can cause financial losses and reputational damage. Opt for a distribution that has a long-term support release, ensuring that it will receive updates and fixes for an extended period of time.
Evaluate the Compatibility: Compatibility with your existing hardware and software is another crucial aspect to consider. Ensure that the Linux distribution you choose is compatible with the drivers, applications, and protocols required by your payment system.
Examine the Community Support: Linux distributions with vibrant and active communities can be immensely helpful, especially in troubleshooting and resolving issues. A strong community support system means you can seek assistance from experienced users and developers to enhance the performance and security of your payment solution.
Weigh the Customization Options: Depending on your specific needs and preferences, you may require a Linux distribution that allows for easy customization. Look for distributions that offer a wide range of customization options, allowing you to tailor the operating system to meet your unique requirements.
Consider the Resource Requirements: Evaluate the resource needs of your payment system and choose a Linux distribution accordingly. Consider factors such as system resources, memory usage, and hardware requirements to ensure that the chosen distribution can effectively support your payment solution.
Analyze the Licensing: Finally, take into account the licensing requirements and terms of the Linux distribution. Ensure that it aligns with your organizational policies and complies with any specific legal regulations related to your payment system.
By carefully considering these factors, you can select the right Linux distribution for your payment system and lay a solid foundation for a secure and efficient electronic payment solution.
Ensuring Compliance with Regulatory Standards
When implementing an electronic payment system, it is crucial to ensure compliance with regulatory standards to guarantee the integrity, security, and privacy of sensitive financial information. This section will discuss the importance of adhering to regulatory standards and provide an overview of key measures and best practices to maintain compliance.
- Familiarize yourself with relevant regulations: Understanding the regulatory landscape is essential for configuring an electronic payment system that meets the necessary standards. Stay informed about industry-specific regulations, such as the Payment Card Industry Data Security Standard (PCI DSS), General Data Protection Regulation (GDPR), and the Security Standards for the Protection of Electronic Financial Transactions (SEPA).
- Implement robust authentication mechanisms: Secure user authentication is a critical component of maintaining compliance. Implement multifactor authentication protocols, such as biometrics or token-based authentication, to enhance the security of access to the payment system.
- Adopt encryption and data protection methods: Encryption plays a vital role in protecting sensitive payment data from unauthorized access or interception. Employ strong encryption algorithms, such as Advanced Encryption Standard (AES), to safeguard data both in transit and at rest.
- Establish secure network infrastructure: Implementing a secure network infrastructure is paramount to compliant payment system configuration. Utilize firewalls, intrusion detection systems, and regularly updated security patches to safeguard against network vulnerabilities and potential attacks.
- Regularly perform vulnerability assessments and penetration testing: Conducting regular assessments and testing helps identify potential security vulnerabilities within the payment system. Regularly scan for vulnerabilities, perform penetration tests, and address any identified weaknesses promptly.
- Maintain thorough audit trails: Keeping comprehensive logs and audit trails is crucial for ensuring compliance and facilitating effective incident response. Implement logging mechanisms that capture critical events, such as user access, system changes, and transaction details, for traceability and compliance monitoring purposes.
- Provide regular training and awareness programs: Design and implement training programs to educate all personnel involved in payment system configuration about the importance of compliance. Foster a culture of security awareness to ensure that regulatory standards are upheld consistently.
By following these guidelines, organizations can establish a robust and compliant electronic payment system on Linux that meets all necessary regulatory standards. Adhering to these standards is critical not only for legal and regulatory compliance but also for maintaining customer trust and safeguarding sensitive financial data.
Securing Transactions: Implementing Encryption Protocols on Linux
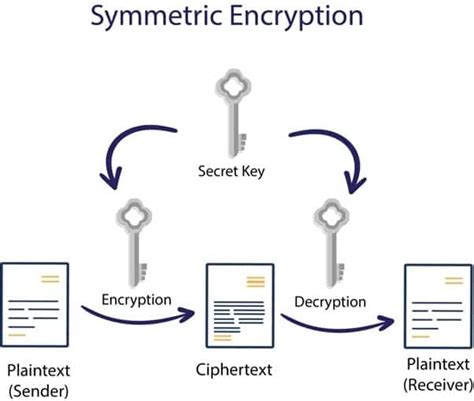
Ensuring the security of electronic payment systems is paramount in today's digital world. Implementing encryption protocols on Linux provides a reliable and effective solution to protect sensitive information during transactions.
Encryption protocols play a vital role in safeguarding data integrity, confidentiality, and authenticity. By employing robust encryption methods, such as symmetric and asymmetric algorithms, Linux offers a secure environment for electronic payment systems.
- Symmetric Encryption: This method involves using a single key to both encrypt and decrypt data. With Linux, various symmetric encryption algorithms, such as AES (Advanced Encryption Standard) and DES (Data Encryption Standard), can be easily implemented for securing transactions.
- Asymmetric Encryption: Unlike symmetric encryption, this approach uses a pair of keys - public and private keys. The public key encrypts the data, while the private key decrypts it. Linux supports popular asymmetric encryption algorithms like RSA and DSA, enabling secure communication channels for electronic payment systems.
- Digital Signatures: Linux provides mechanisms for generating digital signatures, which enhance the integrity and authenticity of electronic payments. By using cryptographic hashing algorithms, such as SHA-256, Linux ensures that transactions remain tamper-proof and verifiable.
Implementing encryption protocols on Linux requires careful consideration of key management, secure key storage, and secure communication channels. Proper configuration and regular updates of encryption software and libraries are essential to stay ahead of emerging security vulnerabilities.
In conclusion, harnessing the power of encryption protocols on Linux strengthens the security posture of electronic payment systems. By utilizing symmetric encryption, asymmetric encryption, and digital signatures, Linux offers a reliable and robust foundation for ensuring the confidentiality, integrity, and authenticity of transactions.
Efficient Strategies for Setting Up Electronic Payment Systems on Linux
This section focuses on implementing effective approaches to configure electronic payment systems on the Linux platform. It explores various techniques and recommended practices for optimizing the setup process while ensuring secure and reliable payment processing.
To ensure the successful configuration of electronic payment systems on Linux, it is vital to incorporate efficient strategies that streamline the setup process. By employing these strategies, businesses can ensure seamless integration with their existing infrastructure while enhancing the security and reliability of their payment processing systems.
One critical aspect of setting up electronic payment systems on Linux is maintaining strong security measures. It is essential to implement robust authentication mechanisms, encryption protocols, and secure network configurations to protect sensitive customer data and prevent unauthorized access to payment information.
Another key consideration when configuring electronic payment systems on Linux is implementing reliable monitoring and logging mechanisms. By closely monitoring and logging system activities, businesses can promptly detect any suspicious activities or potential security breaches. This allows for timely responses to mitigate risks and ensure the integrity of the payment system.
| Best Practices for Configuring Electronic Payment Systems on Linux |
| 1. Strengthening Security Measures |
| 2. Implementing Monitoring and Logging Mechanisms |
| 3. Ensuring High Availability and Redundancy |
| 4. Optimizing Performance and Scalability |
| 5. Conducting Regular Audits and Compliance Checks |
Additionally, ensuring high availability and redundancy is crucial for electronic payment systems to minimize downtime and maximize reliability. Implementing redundant systems, failover mechanisms, and regular backups guarantees uninterrupted payment processing, even in the event of hardware or software failures.
Lastly, optimizing the performance and scalability of electronic payment systems is essential to handle increasing transaction volumes efficiently. By utilizing efficient database management strategies, load balancing techniques, and hardware resource optimization, businesses can accommodate growing payment demands without compromising system performance and response times.
By following these best practices for configuring electronic payment systems on Linux, businesses can efficiently set up secure and reliable payment processing environments, safeguarding customer data and ensuring smooth transaction processing.
Enhancing Security with Two-Factor Authentication
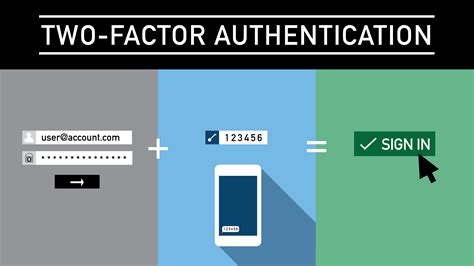
In this section, we will explore the implementation of a robust and advanced security measure known as two-factor authentication (2FA) for your electronic payment system. 2FA adds an extra layer of protection to ensure that only authorized users can access sensitive data or perform financial transactions.
Introducing an Additional Layer of Verification
Two-factor authentication involves the use of two independent factors to verify the identity of a user. Instead of relying solely on a password, which can be easily compromised, this method adds an extra layer of verification, making it significantly more difficult for unauthorized individuals to gain access.
The first factor typically involves something the user knows, such as a password or PIN, while the second factor requires something the user possesses, such as a physical token or a mobile device.
Enhanced Security Measures with Two-Factor Authentication
By implementing two-factor authentication, your electronic payment system will benefit from enhanced security measures. This additional layer of verification mitigates the risks associated with password theft, phishing attacks, and other common security threats.
Two-factor authentication significantly reduces the likelihood of unauthorized access to sensitive user data and prevents fraudulent transactions.
Choosing the Right Two-Factor Authentication Method
There are various methods available for implementing two-factor authentication, including hardware tokens, software-based solutions, SMS-based verification, and biometric authentication. It is essential to choose the method that best fits the needs of your electronic payment system and provides the optimal balance between security and convenience.
Each method offers its own advantages and considerations, and it is crucial to carefully assess which approach aligns with your system's requirements and user preferences.
Securing Your Electronic Payment System with Two-Factor Authentication
In this section, we will guide you through the step-by-step process of implementing two-factor authentication for your Linux-based electronic payment system. We will cover the necessary configuration settings, integration with existing security protocols, and best practices to ensure a seamless and highly secure user experience.
By following these guidelines, you will have the knowledge and tools to empower your electronic payment system with an extra layer of security, safeguarding sensitive information and keeping your users' financial transactions protected.
Ensuring the Security of Your Payment System with Regular Patching and Updates
Keeping your electronic payment system secure is crucial in today's digital landscape. Regular patching and updates play a vital role in maintaining the integrity and reliability of your system.
By regularly applying patches and updates to your payment system, you can stay ahead of potential vulnerabilities and security threats. These updates are designed to address any existing security flaws, enhance the system's functionality, and improve its overall performance.
Regular patching and updates offer several benefits to your payment system:
- Improved Security: Updates often include security patches that address known vulnerabilities, preventing unauthorized access and protecting sensitive customer data.
- Enhanced Performance: Updates can optimize the system's performance by fixing bugs, improving response times, and streamlining processes.
- Compatibility: With regular updates, you ensure that your payment system remains compatible with the latest hardware, software, and security standards.
- Compliance: Many regulatory standards require regular updates as part of maintaining a secure payment system. By staying up to date, you can ensure compliance with industry regulations.
To implement a successful patching and updating strategy, it is essential to follow a few best practices:
- Regular Assessment: Conduct regular assessments to identify vulnerabilities and security gaps within your payment system. This will help you determine which updates are necessary.
- Testing: Before applying any updates, thoroughly test them in a controlled environment to ensure they do not negatively impact your system's performance or functionality.
- Notification and Monitoring: Stay informed about the latest updates and security advisories from your payment system's provider. Establish a monitoring system to track and apply updates promptly.
- Backup and Recovery: Always back up your payment system's data before applying any patches or updates. This ensures you have a failsafe in case any issues arise during the update process.
In conclusion, regularly patching and updating your payment system is essential for maintaining its security, reliability, and compliance with industry standards. By adopting a proactive approach and following best practices, you can ensure the smooth functioning of your electronic payment system while safeguarding sensitive customer information.
Enhancing Security: Monitoring and Logging Techniques for Identifying Abnormalities

In this section, we will explore various monitoring and logging techniques that can be employed to detect anomalies within electronic payment systems. By implementing effective monitoring and logging practices, organizations can strengthen their security measures and proactively identify any suspicious activities or deviations from normal behavior.
One of the key monitoring techniques is through the use of intrusion detection systems (IDS), which constantly analyze network traffic and look for any signs of potential attacks or unauthorized access attempts. These systems employ a combination of signature-based and anomaly-based detection methods to identify known attack patterns as well as any abnormal behavior that deviates from the established norms.
Additionally, organizations can leverage log files generated by various system components, such as web servers, databases, and application servers, to gain insights into the activities taking place within the electronic payment system. By carefully analyzing these logs, administrators can identify any unusual patterns, error messages, or unauthorized access attempts that may indicate a potential security breach or system compromise.
Furthermore, real-time monitoring tools can be implemented to provide immediate notifications and alerts whenever certain predefined parameters or thresholds are breached. This allows administrators to take prompt action and mitigate potential security risks before they escalate into more significant issues.
In order to effectively detect anomalies, it is crucial for organizations to establish a baseline of normal system behavior. By carefully monitoring and logging various system metrics and user activities over a period of time, administrators can establish a benchmark against which any deviations can be identified. This baseline can then be continuously updated and refined to adapt to evolving threats and changes in system behavior.
- Intrusion detection systems (IDS)
- Analysis of log files
- Real-time monitoring tools
- Establishing a baseline of normal behavior
By implementing these monitoring and logging techniques, organizations can enhance the security of their electronic payment systems and swiftly detect any anomalies that may pose a threat to the integrity and confidentiality of sensitive payment information.
FAQ
Can Linux be used for electronic payment system configuration?
Yes, Linux can be used for electronic payment system configuration. It offers a secure and reliable platform for setting up and managing payment systems.
What are the advantages of using Linux for electronic payment system configuration?
There are several advantages of using Linux for electronic payment system configuration. Firstly, Linux is an open-source operating system, which means that it can be customized and tailored to meet specific requirements. Secondly, Linux is known for its stability and security, providing a robust platform for handling sensitive payment data. Lastly, Linux offers a wide range of tools and software that can be used to configure and manage electronic payment systems effectively.
Is Linux compatible with various payment processing protocols?
Yes, Linux is compatible with various payment processing protocols. It supports popular protocols like ISO 8583, NACHA, and EMV, which are widely used in the electronic payment industry.
How can Linux ensure the security of electronic payment systems?
Linux ensures the security of electronic payment systems through various measures. Firstly, it provides robust access controls and permissions management, allowing administrators to restrict access to sensitive payment data. Secondly, Linux has a strong built-in firewall and security features that protect against unauthorized access and potential cyber threats. Additionally, Linux receives regular security updates and patches, ensuring that any vulnerabilities are promptly addressed.
Are there any specific Linux distributions recommended for electronic payment system configuration?
While there are several Linux distributions available, some distributions are better suited for electronic payment system configuration. One popular choice is Red Hat Enterprise Linux, known for its reliability and support for enterprise-level deployments. Another option is Ubuntu, which offers a user-friendly interface and a wide range of software packages. Ultimately, the choice of distribution depends on specific requirements and preferences.




