As the adoption of containerization continues to increase, issues related to the security of container images have garnered significant attention. In the context of Rocky Linux 8.6, one aspect that demands careful consideration is the presence of potentially hazardous image repositories. These repositories, while serving as a valuable resource for developers and system administrators, could also pose a considerable risk if not cautiously managed.
Within the realm of containerization, image repositories play a pivotal role in facilitating the distribution and sharing of container images. However, not all image repositories are created equal when it comes to security. Some repositories may harbor malicious or vulnerable images that, if utilized without proper scrutiny, can lead to devastating consequences, such as unauthorized access, data breaches, or even compromising the integrity of the entire system.
This article aims to shed light on the challenges related to unsafe image repositories in Rocky Linux 8.6 and explore the potential vulnerabilities they could introduce to containerized environments. By understanding these risks, administrators and developers can make more informed decisions when choosing and managing image repositories, ultimately bolstering the overall security of their deployments.
Potential Risks of Utilizing Insecure Container Repositories

Within the realm of containerization, there exist certain repositories which, if not suitably secured, can pose substantial hazards to system integrity. Such repositories, while initially appearing to offer convenience and expedience, may inadvertently expose systems to a plethora of vulnerabilities.
By deploying containers sourced from unsafe registries, organizations expose themselves to potential risks that could compromise the confidentiality, integrity, and availability of their systems. These risks encompass the possibility of malicious actors leveraging insecure containers to execute unauthorized actions, exploit weaknesses in software, or gain unauthorized access to sensitive data.
The utilization of insecure container repositories may further lead to the inadvertent installation of compromised or tampered images. This could result in the execution of malicious code or unauthorized modifications to critical system components. Additionally, the lack of security controls within these repositories may allow for the distribution of containers containing outdated or vulnerable software, which increases the likelihood of successful attacks.
Moreover, untrusted container registries may lack sufficient monitoring and vulnerability patching practices. This increases the likelihood of undetected or unaddressed security flaws within the containers, creating potential opportunities for cybercriminals to exploit known vulnerabilities and gain unauthorized access to sensitive information.
Ultimately, it is crucial for organizations to exercise caution when sourcing containers from insecure registries, as the potential risks associated with such practices can undermine the security posture of their systems and expose them to a wide range of vulnerabilities.
Exploiting the Weaknesses: Potential Risks and Exploitation Techniques
In this section, we will explore the various ways in which the vulnerabilities present in the compromised registries can be exploited, thereby posing significant risks to the security and integrity of a system. By taking advantage of these weaknesses, malicious actors can gain unauthorized access, execute arbitrary code, and compromise the overall functionality of the environment.
One of the key aspects to consider when discussing the exploitation of these vulnerabilities is the potential for unauthorized access. By exploiting weaknesses in the compromised registries, attackers can bypass authentication mechanisms, gaining illicit entry into a system. Once inside, they can launch further attacks, gaining control over critical resources and sensitive data.
Furthermore, the exploitation of these vulnerabilities can involve the execution of arbitrary code. By injecting malicious scripts or manipulating the registry content, attackers can take advantage of security gaps to execute their own code within the targeted environment. This allows them to carry out a range of malicious activities, such as privilege escalation, data exfiltration, or even complete system takeover.
Another significant risk associated with the exploitation of these weaknesses is the potential for compromising the overall functionality of the system. By tampering with the registry, attackers can manipulate the integrity of the environment, resulting in instability, crashes, or system-wide failures. This can lead to disruptions in services, loss of data, and financial ramifications for affected organizations.
It is crucial to highlight that the exploitation techniques utilized by attackers can vary greatly, making it challenging to detect and mitigate these risks effectively. Therefore, it is imperative for system administrators and security professionals to stay vigilant, implement robust security measures, and regularly update and patch vulnerable components to safeguard against these potential exploitation scenarios.
Overall, understanding the risks posed by the vulnerabilities present in the compromised registries is essential in order to mitigate their impact effectively. By recognizing the potential exploitation techniques utilized by attackers, organizations can take proactive measures to enhance their security posture and protect their systems from malicious activities.
Malware Distribution
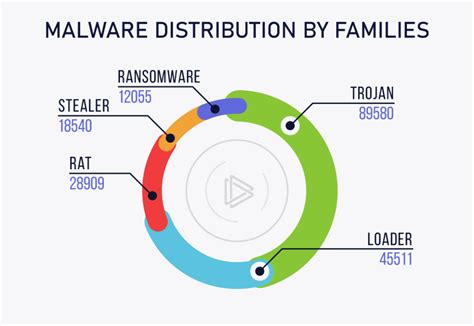
The distribution of malicious software poses a significant threat to the security and stability of computer systems. In the context of the aforementioned topic, we will explore the potential risks associated with the dissemination of harmful code through Docker container repositories. By examining the mechanisms by which malware can be distributed and the vulnerabilities it exploits, we aim to shed light on the importance of securing container ecosystems.
Malware distribution involves the intentional spread of harmful software designed to compromise or exploit computer systems. This illicit activity can occur through various means, including the unauthorized use of software repositories. Within the realm of Docker containers, which provide a lightweight and portable environment for deploying applications, the potential exists for malware to be introduced through insecure or compromised registries. These repositories serve as centralized locations where container images are stored and can be accessed by users. However, if not adequately protected, they can become breeding grounds for malware distribution.
The repercussions of malware distribution can be severe, ranging from data theft and unauthorized access to system corruption and disruption. For instance, malicious code can be embedded within container images, masking its true intent and purpose. Once these infected images are pulled from a compromised registry and executed on a host system, the malware can propagate, compromise other containers or even the host itself. This can lead to a domino effect, with the malware rapidly spreading across the entire container ecosystem, causing widespread damage and compromising the integrity of applications and data.
To mitigate the risks associated with malware distribution, it is crucial to implement robust security measures throughout the entire container lifecycle. This includes ensuring the integrity and authenticity of container images, regularly scanning for vulnerabilities and malware, and strictly controlling access to container registries. By adopting these practices, system administrators can significantly reduce the likelihood of malware infiltration and protect the overall security of their containerized environments.
Data Breaches
In the context of the topic discussing the identified risks in the Rocky Linux 8.6 operating system, it is imperative to turn our attention to the potential occurrence of data breaches. With the presence of insecure repositories and servers, there is a heightened possibility of unauthorized access and exposure of sensitive information. This section delves into the consequences and implications of data breaches, exploring the various ways in which such incidents may occur and the subsequent threats they pose to individuals and organizations alike.
Denial-of-Service (DoS) Attacks

In the realm of cybersecurity, there exists a relentless form of attack known as Denial-of-Service (DoS). This malevolent technique aims to disrupt the availability and functionality of targeted systems, rendering them temporarily or permanently inaccessible to legitimate users. Although the subject of this discussion lies outside the realms of unsafe Docker registries in Rocky Linux 8.6 and potential vulnerabilities, understanding the various facets of DoS attacks is fundamental in comprehending the wider landscape of security threats.
DoS attacks can take many forms, ranging from simple and rudimentary methods to more sophisticated and complex techniques. One of the most prevalent tactics leveraged by attackers is flooding the targeted system with an overwhelming number of requests, thereby depleting crucial resources such as bandwidth, memory, or processing power. Another common approach involves exploiting vulnerabilities in network protocols or software, causing target systems to crash or become unresponsive.
There are two primary types of DoS attacks: volumetric attacks and application layer attacks. Volumetric attacks aim to overwhelm a network or system by flooding it with a colossal volume of traffic or data. This flood of data can lead to network congestion, bottlenecks, and ultimately exhaust the target's resources. On the other hand, application layer attacks are more targeted and focus on exploiting weaknesses in specific applications or services running on the target system, often with the intent to exploit vulnerabilities and drain resources.
- Syn Flooding: This attack exploits the TCP three-way handshake process by sending a large number of SYN requests to the target, occupying its resources and preventing legitimate connections.
- UDP Flood: In a UDP flood attack, the attacker sends a flood of User Datagram Protocol (UDP) packets to the target, overwhelming its network capacity and potentially disrupting communication.
- HTTP Flood: This attack involves flooding a web server with a massive number of HTTP requests, rendering it unable to handle legitimate traffic and causing a denial of service for genuine users.
- Slowloris: Slowloris is a stealthy DoS technique that attempts to consume all available connections on the targeted web server. By sending incomplete HTTP requests and maintaining multiple connections, the attacker effectively prevents the server from accepting additional legitimate connections.
Preventing and mitigating the impact of DoS attacks require a multi-layered approach, involving network monitoring, traffic analysis, and the implementation of robust security measures. Organizations must be proactive in adopting solutions such as firewalls, intrusion detection systems (IDS), and rate-limiting mechanisms to help safeguard against DoS attacks.
Identifying Insecure Container Repositories
When it comes to ensuring the security of containerized applications, one of the key aspects to consider is the integrity and safety of the repositories from which these containers are pulled. In this section, we will explore the process of identifying potentially unsafe container repositories without compromising the security of the overall system.
It is crucial to be able to distinguish between trustworthy and potentially hazardous container repositories in order to protect against vulnerabilities and potential exploits. By implementing effective identification techniques, users can mitigate the risk of exposing their systems to malicious or compromised containers.
Identifying insecure container repositories involves analyzing various factors that indicate potential vulnerabilities. Some key indicators to consider include the reputation and history of the repository provider, the frequency and regularity of security updates, and the level of community support and engagement. Additionally, scanning tools and vulnerability assessment techniques can be used to detect any known vulnerabilities or suspicious activities within the repositories.
Furthermore, attention should be given to the authentication and encryption mechanisms employed by the repository providers. Secure containers rely on strong authentication protocols and encryption algorithms to ensure the confidentiality and integrity of the container images. Therefore, it is important to verify that the repository in question implements these security measures effectively.
In conclusion, the process of identifying unsafe container repositories is a critical step in ensuring the overall security and stability of containerized applications. By being aware of the indicators mentioned above and employing robust authentication and encryption measures, users can make informed decisions and safeguard their systems against potential vulnerabilities.
Lack of Secure Connection (HTTPS)
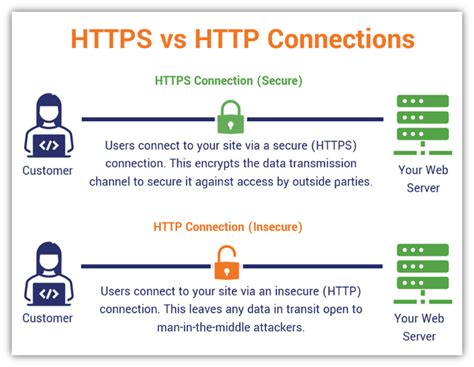
In the scope of examining the unsafe aspects surrounding the repositories in the Rocky Linux 8.6 distribution, it is essential to address the issue of the absence of a secure connection, specifically the lack of HTTPS protocol implementation. This section will delve into the potential risks and consequences that arise when Docker registries and other software repositories operate without a secure connection.
Without the implementation of a secure connection, the integrity and confidentiality of the data exchanged between the clients and the repositories are undermined. The absence of HTTPS leaves the communication channel vulnerable to eavesdropping, data interception, and unauthorized access. This poses a significant threat, especially when handling sensitive or confidential data within software environments.
As HTTPS protocols provide encryption and secure authentication mechanisms, their absence exposes Docker registries and their contents to potential tampering, man-in-the-middle attacks, and malicious modifications. When software repositories lack a secure connection, there is an increased risk of compromising the authenticity and integrity of the packages, leading to the installation of compromised or malicious software components.
Failing to implement HTTPS also hinders the ability to ensure the trustworthiness and genuineness of the repositories. Lack of secure connection opens avenues for attackers to create malicious imitations of legitimate repositories, potentially tricking users into unknowingly downloading and executing harmful software.
Addressing the lack of secure connection is crucial in securing software distribution and protecting the overall integrity of the Rocky Linux 8.6 distribution. By enforcing HTTPS protocols and ensuring trusted certificates are used, the risk of unauthorized access, data interception, and tampering can be mitigated. Adopting secure connection practices in Docker registries and other software repositories is vital in maintaining a secure software ecosystem and safeguarding users' systems and data.
Unverified Content and Unsigned Images
In the context of the discussed issue surrounding certain repositories in the Rocky Linux 8.6 distribution, it is essential to address the potential risks associated with unverified content and unsigned images. This section aims to shed light on the importance of ensuring the authenticity and integrity of the software packages and container images utilized within the Docker environment.
When working with Docker, it is crucial to exercise caution when utilizing content from unverified sources. Unverified content refers to software packages or container images that have not undergone a thorough validation process to ensure their reliability and trustworthiness. By using unverified content, organizations expose themselves to various risks, including the possibility of deploying compromised or malicious software within their Docker containers.
Furthermore, the usage of unsigned images poses additional security concerns. Unsigned images lack the cryptographic signature that verifies their origin and confirms their authenticity. Without these digital signatures, it becomes challenging to establish the integrity and trustworthiness of the images, leaving them susceptible to tampering or unauthorized modifications.
Deploying unverified content and unsigned images increases the likelihood of introducing vulnerabilities into the Docker environment. Malicious actors may exploit these vulnerabilities to gain unauthorized access to sensitive data, compromise the integrity of the system, or execute arbitrary code within the containers.
To mitigate the risks associated with unverified content and unsigned images, it is crucial to implement best practices. This includes utilizing trusted and well-established repositories, verifying the cryptographic signatures of software packages and container images before deployment, and regularly monitoring for any signs of unauthorized or malicious activity within the Docker environment. By following these measures, organizations can enhance the security and integrity of their Docker infrastructure, reducing the potential for exploitation and safeguarding their systems from potential threats.
Enterprise Linux Security Episode 68 - Barracuda's Vulnerability
Enterprise Linux Security Episode 68 - Barracuda's Vulnerability Learn Linux TV দ্বারা 2,708টি ভিউ 10 মাস আগে এ স্ট্রীম হয়েছে 43 মিনিট
How To Save And Load Docker Container On Rocky Linux 8.6
How To Save And Load Docker Container On Rocky Linux 8.6 LinuxHelp দ্বারা 94টি ভিউ 11 মাস আগে 6 মিনিট, 3 সেকেন্ড
FAQ
What are the potential vulnerabilities in Rocky Linux 8.6 due to unsafe Docker registries?
Unsafe Docker registries in Rocky Linux 8.6 can expose the system to various vulnerabilities, such as the risk of deploying malicious or compromised container images. These images may contain backdoors, malware, or vulnerable components that can be exploited by attackers.
How can unsafe Docker registries lead to security breaches in Rocky Linux 8.6?
By using unsafe Docker registries, there is a higher chance of downloading container images that have been tampered with by malicious actors. This can ultimately lead to security breaches, as the compromised images can run arbitrary code on the host system, potentially compromising confidential data or causing other damage.
Are there any recommended practices to secure Docker registries in Rocky Linux 8.6?
Absolutely! To secure Docker registries in Rocky Linux 8.6, it is recommended to enforce authentication and access controls for registry access. Additionally, regular vulnerability scanning of container images and ensuring the use of only trusted and verified images can significantly reduce the risk of potential vulnerabilities.
How can users identify unsafe Docker registries in Rocky Linux 8.6?
Users can identify potentially unsafe Docker registries by checking for warning signs such as unauthenticated access, lack of access controls, or the presence of known malicious images. It is crucial to research and review the registry's reputation and security practices before utilizing it to minimize the risk of vulnerabilities.
What steps should be taken if unsafe Docker images have been deployed in Rocky Linux 8.6?
If unsafe Docker images have been deployed in Rocky Linux 8.6, immediate action should be taken to mitigate the potential risk. This includes removing the compromised images, conducting a thorough security assessment, and patching any vulnerabilities that may have been exploited. It is also important to inform relevant authorities and keep a record of the incident for further investigation.
What are the potential vulnerabilities in Rocky Linux 8.6 due to unsafe Docker registries?
The potential vulnerabilities in Rocky Linux 8.6 due to unsafe Docker registries include the risk of downloading malicious or tampered container images, which can result in compromised systems, data breaches, and unauthorized access.
How can unsafe Docker registries in Rocky Linux 8.6 be exploited by attackers?
Attackers can exploit unsafe Docker registries in Rocky Linux 8.6 by uploading malicious or compromised container images, impersonating legitimate images, injecting malware or backdoors, and potentially gaining unauthorized access, compromising the security and integrity of the system.




