In the realm of containerization, where the isolation of applications and system resources is paramount, the management of administrative privileges can pose unique challenges. Specifically, when it comes to Windows Docker containers, ensuring that they run with elevated privileges or as an administrator can be a complex task. This article delves into the intricacies of this issue, exploring the limitations and potential workarounds.
When working with Windows Docker containers, the need may arise to execute tasks that require administrative privileges. These tasks can include modifying system components, accessing restricted resources, or performing critical system operations. However, by default, Docker containers are designed to run with limited privileges, isolating them from the host system.
To run a Windows Docker container as an administrator, it is necessary to bypass the default security measures. This process can involve modifying policies, granting special permissions, or adjusting container configurations. However, these workarounds may introduce potential security risks, compromising the isolation and security guarantees offered by containerization technology.
The topic explored in this article delves into the delicate balance between achieving elevated privileges within a Windows Docker container and maintaining the security and isolation benefits of containerization. By understanding the limitations and potential trade-offs, administrators and developers can make informed decisions when it comes to implementing solutions that require elevated privileges."
Understanding the Operation of Windows Docker Containers
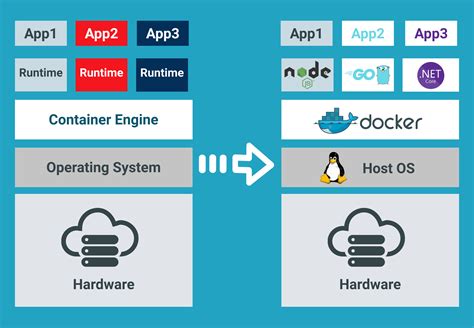
Windows Docker containers are a powerful technology for isolating and running applications in a consistent and portable manner. This section aims to provide a comprehensive understanding of how Windows Docker containers work, without delving into the specific issue of running containers as administrators.
- Isolation and Efficiency:
- Container Images:
- Container Runtimes:
- Layered File System:
- Container Networking:
Windows Docker containers leverage the built-in containerization features of the Windows operating system. By isolating applications using lightweight, process-based containers, they ensure that each application runs independently of its host environment. This enables efficient resource utilization and allows multiple containers to run concurrently on the same system.
Container images form the foundation of Windows Docker containers. These images are highly portable and contain all the necessary files, libraries, and configurations required to run an application. They are created from a base operating system image and can be customized to include additional software components or dependencies as needed.
At the core of Windows Docker containers lies the container runtime, which is responsible for launching and managing containers. The runtime interacts with the underlying operating system and orchestrates the creation, execution, and termination of containers. It provides the necessary environment for applications to run, including filesystem isolation, network connectivity, and resource allocation.
Windows Docker containers utilize a layered file system, where each container has its own read-write layer on top of a shared read-only system image. This layered approach allows for efficient storage usage and quick container startup times. Additionally, changes made within a container are isolated to its private layer, ensuring clean and reproducible deployments.
Windows Docker containers can be connected to various networking interfaces to facilitate communication with other containers or the host system. Through network namespaces and virtual bridges, containers can be assigned individual network settings, enabling them to interact securely and efficiently with external resources.
By understanding the fundamental principles and components that underpin Windows Docker containers, developers and system administrators can harness the full potential of this technology and address specific challenges such as running containers as administrators. Through proper configuration and optimization, containers can deliver enhanced performance, scalability, and security for a wide range of applications.
Challenges with Running Containers as Administrator
In the context of the topic "Challenges with Running Containers as Administrator," this section discusses the difficulties encountered when attempting to give containers elevated privileges. These challenges involve limitations in granting administrative rights to containers and the potential risks associated with running containers with elevated permissions.
Elevated Privileges Limitations: Running containers with administrative rights can be challenging due to the inherent security restrictions and limitations imposed by the operating system. Containers are designed to provide isolated environments, ensuring that each container operates independently of the host system. Granting containers full administrative access can undermine the isolation and security mechanism, which is a crucial aspect of containerization.
Security Risks: Allowing containers to run as administrators introduces potential security risks. Containers are susceptible to exploitation, and granting administrative privileges increases the attack surface, making it easier for malicious actors to compromise the container and potentially gain control over the host system. Running containers with elevated permissions should be done judiciously to mitigate these security risks.
Compatibility Challenges: In certain scenarios, running containers as administrators may pose compatibility challenges. Some applications or services may not function correctly within an elevated container environment due to dependency on specific user privileges or access control restrictions. Such compatibility issues can lead to unexpected behavior or application failures, necessitating careful consideration before running containers with administrative privileges.
Alternative Approaches: To address the challenges associated with running containers as administrators, alternative approaches can be considered. One option is to use least-privileged accounts within containers, striking a balance between container isolation and necessary access rights. Another approach involves employing additional security measures such as implementing a robust network segmentation strategy or utilizing containerization platforms with built-in security features to enhance the overall security posture while still enabling essential administrative tasks within containers.
In summary, despite the challenges faced when trying to run containers as administrators, understanding the limitations, security risks, and alternative approaches can help navigate the complexities and ensure a more secure and efficient containerized environment.
Methods to Overcome the Limitations

In this section, we will explore various strategies and techniques to overcome the constraints encountered when trying to run a Windows Docker container as an administrator.
Enhancing Privileges: One possible approach to tackle this issue is by enhancing the privileges of the container. By elevating the container's permissions, it can perform tasks that require administrator access. This can be achieved through configuring security policies or modifying the container's access control settings.
Using Alternative Solutions: If running the container as an administrator proves to be challenging, one can explore alternative solutions. For instance, instead of running the container as an administrator, segregate the tasks that require administrative access into separate processes or services, while keeping the container itself running under standard user permissions.
Exploring Compatibility Options: It might be worth investigating compatibility options provided by Docker or Windows to overcome the limitation of running a Windows Docker container as an administrator. These options could include using special flags or parameters during container creation or exploring specific Docker versions that offer improved compatibility.
Collaborating with the Docker Community: Another way to find a workaround for this limitation is by seeking help and collaborating with the larger Docker community. Engaging in forums, discussions, or reaching out to experienced Docker users can provide valuable insights, tips, and potential solutions to overcome the challenge.
Optimizing Container Configuration: It is crucial to thoroughly review and optimize the container configuration to minimize the need for running it as an administrator. This can involve fine-tuning the permissions and access control settings, leveraging proper user and group management practices, and ensuring that the container's functionality aligns with these configurations.
Implementing Security Best Practices: While working around the limitation of running a Windows Docker container as an administrator, it is essential to prioritize security. Implementing security best practices such as utilizing user and group management, employing strong passwords, and regularly updating the container's software can help mitigate the risks associated with running containers under standard user permissions.
By employing these methods and carefully considering the implications, it is possible to overcome the limitations encountered when attempting to run a Windows Docker container as an administrator. Each approach comes with its considerations and trade-offs, so it is important to tailor the chosen solution to the specific requirements and constraints of the given scenario.
Using PowerShells's 'RunWithElevatedPrivileges' Command
In this section, we will explore the functionality and benefits of PowerShells's 'RunWithElevatedPrivileges' command, which allows executing commands with elevated privileges in a secure and controlled manner.
With 'RunWithElevatedPrivileges', users gain the ability to perform tasks that require administrative access without needing to run the entire Windows Docker container as an administrator. This command provides a more granular approach, ensuring only specific commands or portions of the script have elevated privileges.
- Enhanced Security: 'RunWithElevatedPrivileges' helps maintain security by limiting the execution of privileged commands to only the necessary sections of the code.
- Controlled Access: Instead of running the entire container as an administrator, the command allows administrators to define and control which commands require elevated privileges.
- Reduced Risk: By executing specific tasks with elevated privileges, administrators can minimize the risk of unintentional or unauthorized access to critical system resources.
To utilize the 'RunWithElevatedPrivileges' command effectively, it is important to understand its syntax and how to integrate it into PowerShell scripts. The command should be used selectively and only when necessary to ensure a secure and efficient workflow.
By leveraging the 'RunWithElevatedPrivileges' command, administrators can strike a balance between running commands with elevated privileges and maintaining the overall integrity and security of the Windows Docker container.
Modifying the Dockerfile to Enable Elevated Privileges
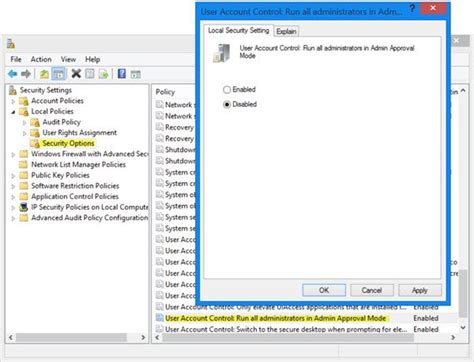
In this section, we will discuss how to modify the Dockerfile in order to grant elevated privileges for running a Windows container. By making necessary adjustments to the Dockerfile, you can ensure that the container has the necessary permissions to execute actions that require administrative privileges.
To enable elevated privileges in the Docker container, you can utilize various approaches such as modifying the user, adjusting permissions, or enabling specific capabilities. These modifications will allow the container to perform tasks that require administrative access, enhancing its capabilities and flexibility.
One of the methods involves modifying the user within the Dockerfile. By creating a new user or updating the existing user, you can set the appropriate permissions and privileges required for running the container as an administrator. This approach ensures that all actions executed within the container will have the necessary elevated privileges.
Another technique involves adjusting the permissions within the Dockerfile. By configuring file system permissions or granting specific access rights to critical directories, you can enable the container to perform administrative tasks without encountering permission denied errors. This approach guarantees that the container has the necessary access to important system resources.
In addition, you can enable specific capabilities within the Dockerfile to grant elevated privileges to the container. By explicitly granting certain capabilities like SYS_ADMIN or NET_ADMIN, the container will be able to perform advanced administrative operations, such as manipulating networking settings or managing system-level resources.
| Benefits of Modifying the Dockerfile for Elevated Privileges: |
|---|
| 1. Enhanced flexibility and capability of the Windows container |
| 2. Ability to execute administrative tasks without encountering permission issues |
| 3. Increased control and access to critical system resources |
| 4. Improved performance and efficiency in container operations |
By modifying the Dockerfile to allow elevated privileges, you can ensure that your Windows container has the necessary permissions and capabilities to run as an administrator. This enables you to leverage the full potential of the containerized environment and perform advanced tasks that require administrative access.
Best Practices for Managing Elevated Privileges
Elevated privileges are an essential aspect of system administration, granting users or processes higher levels of access to perform certain tasks. However, it is crucial to handle these privileges with utmost care to ensure the security and stability of the system. In this section, we will discuss the best practices for managing elevated privileges, focusing on effective strategies that minimize potential risks and improve overall system management.
One of the key practices is to implement the principle of least privilege. This means granting users or processes only the privileges necessary for them to perform their designated tasks, avoiding unnecessary elevation of privileges. By adopting this approach, the potential damage or misuse of elevated privileges can be significantly reduced.
Another important aspect is the proper auditing and monitoring of privileges. Administrators should regularly review and analyze the usage of elevated privileges, tracking any deviations from normal operations. This helps identify potential security breaches, unusual activities, or unauthorized access attempts, allowing for prompt actions to mitigate risks and maintain control over privileged accounts.
Implementing strong security measures, such as multi-factor authentication and password policies, is also crucial in handling elevated privileges. This ensures that only authorized individuals can utilize these privileges, reducing the chances of unauthorized access or compromise of privileged accounts.
| Best Practices for Handling Elevated Privileges: |
|---|
| Implement the principle of least privilege |
| Regularly audit and monitor the usage of privileges |
| Utilize strong security measures |
Furthermore, employing a privilege escalation mechanism can be beneficial for efficiently managing elevated privileges. This allows for temporary elevation of privileges when necessary, minimizes the risk of prolonged access, and provides accountability for privilege usage.
Additionally, it is important to keep privileges well-documented and regularly update privilege assignments to reflect any changes in roles or responsibilities. This helps ensure that individuals have the appropriate level of access required for their current tasks, preventing potential security gaps or unnecessary elevation of privileges.
Lastly, implementing regular training and awareness programs for users and administrators regarding the proper handling of elevated privileges is essential. This fosters a security-conscious culture, helps individuals understand the risks associated with privilege abuse, and encourages responsible usage of elevated privileges.
By following these best practices, organizations can effectively manage and control elevated privileges, minimizing potential vulnerabilities and enhancing the overall security and stability of their systems.
Limiting the Use of Administrator Privileges
Controlling and restricting the use of elevated privileges is crucial for a secure and well-managed system. In this section, we will explore the concept of limiting the use of administrator privileges, emphasizing the importance of keeping privilege levels under control and outlining best practices for effective privilege management.
By implementing a robust privilege management strategy, organizations can minimize the risk of unauthorized access, system vulnerabilities, and potential misuse of administrator privileges. This approach ensures that only authorized users have access to elevated privileges, reducing the attack surface and enhancing overall system security.
The first step towards limiting the use of administrator privileges is to define clear roles and responsibilities within the organization. By identifying individuals who require administrative access for legitimate purposes, organizations can create policies and procedures that restrict privilege escalation to only those who truly need it. This not only enhances security but also improves accountability and reduces the potential for accidental damages caused by unrestricted administrative access.
Implementing a least privilege principle is another important aspect of limiting administrator privileges. This principle involves granting users the minimum level of privileges necessary to perform their tasks effectively. By applying the principle of least privilege, organizations can prevent unnecessary access to sensitive resources, reducing the likelihood of privilege abuse and increasing overall system resilience.
Regular auditing and monitoring are critical components of a comprehensive privilege management strategy. By continuously monitoring administrative activities and reviewing privilege assignments, organizations can quickly identify any unauthorized access attempts or suspicious behavior. This proactive approach allows for timely response and remediation, mitigating potential security incidents and ensuring compliance with regulatory requirements.
In conclusion, limiting the use of administrator privileges is key to maintaining a secure and well-functioning system. By implementing clear roles, embracing the principle of least privilege, and maintaining robust monitoring practices, organizations can effectively control access to elevated privileges and protect against potential threats.
Implementing Proper Access Control and Permissions
In the context of the topic, "Inadequate Privileges for Windows Docker Container Execution," this section discusses the importance of establishing comprehensive access control and permissions. By implementing effective access control mechanisms, organizations can ensure the appropriate levels of permissions are assigned to users, applications, and system components, enabling them to perform their intended tasks securely and efficiently.
Establishing Role-Based Access Control (RBAC)
One of the fundamental principles in implementing proper access control is the utilization of Role-Based Access Control (RBAC). RBAC allows organizations to define roles based on specific tasks, job functions, or responsibilities within the system. Each role is then assigned a set of permissions that determine what actions and resources an individual with that role can access. By implementing RBAC, organizations can ensure that the principle of least privilege is applied, granting users only the permissions necessary to perform their duties, minimizing the risk of unauthorized access or privilege abuse.
Implementing Privilege Separation
Privilege separation is another critical aspect of proper access control. It involves segregating functionalities and components into separate processes or containers, allowing each entity to operate with the least privileges required for its specific function. By implementing privilege separation, organizations can limit the impact of potential security breaches, as compromising one component or process does not automatically grant access to other sensitive resources or functionalities.
Applying Least Privilege Principle
The least privilege principle states that users and entities should be granted the minimum level of privileges necessary to perform their tasks effectively. This principle reduces the attack surface by limiting the potential impact of a compromised entity. Organizations should regularly review and fine-tune permissions to ensure they remain aligned with the principle of least privilege, minimizing the risk of unauthorized access or malicious activities.
Implementing Access Control Lists (ACLs)
Access Control Lists (ACLs) provide a granular level of control by enabling organizations to define specific access permissions for individual users or groups. ACLs can be applied to various resources, such as files, directories, devices, or network services. By utilizing ACLs, organizations can tailor permissions to reflect the unique requirements of different user groups or individuals, ensuring that access is granted or denied based on predefined criteria.
Regular Auditing and Monitoring
Auditing and monitoring play a crucial role in maintaining effective access control and permissions. Regular audits help identify any inconsistencies or deviations from the established access policies, allowing organizations to rectify any issues promptly. Additionally, continuous monitoring enables real-time detection of unauthorized access attempts or suspicious activities, ensuring immediate response and mitigation.
Conclusion
Implementing proper access control and permissions is essential for ensuring the security and integrity of Windows Docker containers. By adhering to principles such as Role-Based Access Control, privilege separation, least privilege, and utilizing mechanisms such as Access Control Lists and regular auditing, organizations can establish a robust and secure environment where authorized entities can function effectively while mitigating the risk of unauthorized access or misuse of privileges.
How to Fix Run As Administrator Not Working in Windows 10
How to Fix Run As Administrator Not Working in Windows 10 by MJ Tube 795,613 views 5 years ago 2 minutes, 58 seconds
FAQ
Why am I unable to make my Windows Docker container run as an administrator?
There could be several reasons for this issue. One possible reason is that you do not have the necessary permissions to run the container as an administrator. Another reason could be that the container does not have the required configuration or dependencies to run with administrator privileges.
Is there a workaround to make a Windows Docker container run as an administrator?
Yes, there are a few workarounds that you can try. One option is to modify the container's image to include the necessary configuration and dependencies for running as an administrator. Another option is to use a base image that already has administrator privileges configured. Additionally, you can try running the container with elevated privileges or using the "runas" command to execute commands within the container as an administrator.
Can I run a specific command as an administrator within a Windows Docker container?
Yes, you can run a specific command as an administrator within a Windows Docker container. You can use the "runas" command followed by the "Administrator" account and the desired command to execute it with administrator privileges. For example, you can run "runas /user:Administrator command" to run the "command" as an administrator within the container.
Are there any security implications of running a Windows Docker container as an administrator?
Yes, there are security implications when running a Windows Docker container as an administrator. Running as an administrator gives the container higher privileges, which could potentially be exploited by malicious code or attackers. It is important to carefully consider the risks and only run the container as an administrator if it is absolutely necessary, and to ensure that proper security measures are in place.
Is it recommended to run a Windows Docker container as an administrator?
Running a Windows Docker container as an administrator is not generally recommended unless it is absolutely necessary. Running as an administrator increases the attack surface and potential vulnerabilities of the container. It is recommended to follow the principle of least privilege and only grant administrator privileges when it is needed for specific tasks or applications within the container.
Why am I unable to make a Windows Docker container run as administrator?
There could be several reasons why you are unable to make a Windows Docker container run as administrator. One possible reason is that the base image you are using for the container does not have administrative privileges. Another reason could be that the container is running in a restricted environment that does not allow administrative access. Additionally, it is possible that the Docker daemon itself is not configured to allow containers to run as administrator. To troubleshoot this issue, you can check the base image documentation, review the container environment restrictions, and examine the Docker daemon configuration.




