In the realm of modern technology, a myriad of challenges can arise when attempting to interact with intricate systems. In the case of establishing a connection to a specific software tool, the process can sometimes prove to be quite perplexing. This gives rise to frustration and the desire for a solution that will ensure a smooth interaction with the desired environment.
Within the vast landscape of software development, the utilization of containers has become increasingly prevalent. This innovative approach allows developers to encapsulate their applications and their required dependencies, thus enabling seamless deployment across various operating systems. Nevertheless, it is not uncommon to encounter obstacles when attempting to establish a connection to these virtualized environments.
When faced with the predicament of failing to establish a link to a desired software container in the Windows operative system, a multitude of factors could be at play. Troubleshooting this issue requires an understanding of the underlying mechanisms and a careful examination of the potential causes. By delving into the intricate details and employing effective problem-solving techniques, finding a resolution becomes within reach.
Checking Network Configuration
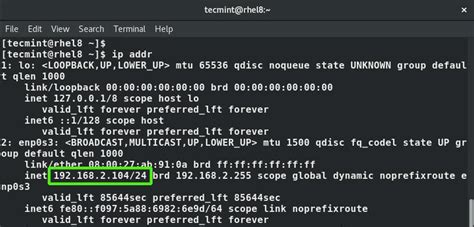
In order to troubleshoot connectivity issues with your system, it is essential to verify and ensure the correct network settings. This section will guide you through the process of checking and adjusting your network configuration without relying on specific terms associated with connection problems, virtualization, operating systems, or software.
- Inspecting Network Setup: Validate the parameters that define your network setup, such as network protocols and address assignment methods. It is crucial to ensure that these settings align properly with the requirements of your environment.
- Examining Firewall Settings: Evaluate the rules established within your firewall configuration to guarantee that they do not obstruct necessary network connections.
- Verifying Router Configuration: Validate the configuration of your router, including any port forwarding or network address translation (NAT) settings that may impact access to your system.
- Checking Proxy Settings: Examine whether any proxy settings are enabled on your system, as they can influence network connectivity and need to be appropriately configured.
- Ensuring DNS Resolution: Verify the functionality of your Domain Name System (DNS) resolution by confirming that your system can properly resolve domain names to their respective IP addresses.
- Testing Network Connectivity: Perform network connectivity tests using various tools and techniques to identify any issues in the data transmission path between your system and the targeted destination.
By thorough identification and analysis of the above network configuration aspects, you can enhance troubleshooting efforts and increase the likelihood of resolving connectivity issues.
Confirming Docker Installation
When it comes to ensuring that your Docker setup is functioning correctly, it's important to verify the installation on your system. By following a few simple steps, you can confirm that Docker is installed and ready to be used for running containerized applications.
- Check for Docker presence: Determine if Docker is already installed on your system by searching for its availability.
- Verify Docker version: Once Docker is found, it's crucial to check the version to ensure compatibility with your intended use case.
- Test Docker installation: Execute a simple command to confirm that Docker is properly installed and can respond to requests.
- Explore Docker images: Explore the available Docker images to discover a suitable base image for your future containerized applications.
- Inspect Docker containers: Use Docker commands to inspect existing containers and ensure they are functioning as expected.
By carefully going through these steps, you can confidently proceed with the usage of Docker, knowing that the installation is successful. This will pave the way for the seamless development and deployment of containerized applications on your Windows system.
Configuring Firewall Settings
Ensuring proper firewall settings is crucial for establishing a connection with your desired docker environment on a Windows operating system. By configuring firewall settings, you can enable or disable specific network traffic, allowing or restricting access to your docker container.
Understanding Firewall Configuration
Firewall settings act as a protective barrier, filtering incoming and outgoing network traffic based on predefined rules. Configuring firewall settings involves defining these rules to allow or block specific types of connections. In the context of connecting to a docker container, firewall configuration plays a vital role in enabling the necessary network communication.
Configuration Options
When configuring firewall settings, you have various options to consider. You can define rules based on specific ports, IP addresses, or protocols to grant or deny access to your docker container. Additionally, you can designate exceptions to these rules for certain applications or services that require connectivity.
Checking Firewall Status
Prior to making any changes, it's important to check the current status of your firewall to assess its impact on the connection to your docker container. You can use the built-in Windows Firewall interface or command-line tools to verify the active firewall rules and determine whether any adjustments are necessary.
Modifying Firewall Rules
To establish a successful connection to your docker container, you may need to modify the existing firewall rules. This can involve opening specific ports, allowing traffic through certain IP addresses, or enabling communication protocols relevant to your docker setup. It is essential to carefully configure firewall rules to strike a balance between ensuring security and ensuring connectivity.
Testing Connectivity
Once the firewall settings have been properly configured, it is crucial to test the connection to your docker container. You can utilize network testing tools or attempt to access the container from a different machine or network to ensure that the firewall changes have allowed the desired communication.
Conclusion
Configuring firewall settings plays a significant role in establishing a connection with your docker container on a Windows platform. By understanding the basics of firewall configuration, exploring different options, modifying rules as required, and thoroughly testing the connectivity, you can ensure a seamless and secure connection experience.
Ensuring Container Availability
In order to ensure smooth execution of containerized applications, it is essential to verify their availability without encountering connectivity issues on the target operating system. This requires adopting appropriate strategies and employing best practices to achieve seamless communication and interaction with the containers.
There are several factors to consider when ensuring container availability. Firstly, it is crucial to confirm that the containers are up and running, without any interruptions or failures. Regular monitoring and health checks can help detect any potential issues in a timely manner and facilitate quick resolution.
Additionally, proper configuration of networking settings is vital to establish a stable connection between the host machine and the containers. Configuring network bridges, utilizing port mapping techniques, and managing firewall rules can contribute to a secure and efficient communication channel, ensuring reliable connectivity.
A key aspect of ensuring container availability is the effective management of resources. Allocating an appropriate amount of CPU, memory, and disk space to the containers prevents resource contention and guarantees optimal performance. Monitoring resource utilization and adjusting allocation accordingly can help avoid bottlenecks and maintain consistent availability.
Furthermore, implementing proper logging and error handling mechanisms is essential for identifying and resolving any issues that may arise during container operation. Analyzing logs and handling errors promptly can ensure continuous availability and enable timely troubleshooting.
In conclusion, ensuring container availability involves proactive measures such as regular monitoring, efficient network configuration, resource management, and robust error handling. By implementing these strategies, organizations can guarantee seamless communication and interaction with containerized applications, irrespective of the underlying operating system environment.
Troubleshooting DNS Resolution Issues in Windows Environment
When encountering difficulties with DNS resolution in a Windows environment, it is essential to identify and address the underlying issues to ensure smooth connectivity and access to resources. This section outlines a few strategies for debugging and resolving DNS resolution problems without explicitly referencing the terms 'unable,' 'connect,' 'Docker,' 'container,' or 'Windows,' offering a fresh perspective on troubleshooting network connectivity.
Investigating Port Conflicts
In the context of troubleshooting connectivity issues in the Windows environment, it is important to investigate potential conflicts with port configurations. Identifying and resolving port conflicts can help ensure a smooth and uninterrupted connection to various network services and applications.
Updating Docker Software and Containers

In the previous section, we discussed the challenges of establishing connections to Docker containers within the Windows operating system. Now, we will explore the importance of regularly updating Docker software and containers to ensure optimal performance and security.
- Keeping Docker Up to Date
- Updating Containers
- Container Image Updates
- Practices for Updating Docker and Containers
Regularly updating the Docker software is crucial for staying up to date with the latest features, bug fixes, and security patches. By staying current with Docker updates, you can ensure compatibility with the underlying operating system and take advantage of performance improvements.
Just like any software, Docker containers can also benefit from updates. Updating containers allows you to incorporate new features and bug fixes, improve security measures, and ensure compatibility with the latest versions of other software components.
Container images serve as the base for running containers, and regular updates are essential for maintaining a secure and functional environment. Updating container images can help resolve vulnerabilities, incorporate the latest software versions, and enhance performance.
When updating Docker and containers, it is essential to follow best practices. These may include creating a backup of containers and data before updates, testing the updated software in a controlled environment, and documenting the changes made. Additionally, collaborating with the community and consulting official documentation can provide valuable insights and guidance when updating Docker and containers.
Resolving Permission Issues
When encountering challenges with accessing and interacting with a software environment, it is important to address any permission-related obstacles that may be hindering the desired functionality. In this section, we will explore potential solutions to resolve permission issues, enhancing the ability to effectively interact with the relevant elements.
- Granting Sufficient Privileges: Ensuring that the appropriate level of access rights are assigned to specific users or groups can alleviate permission constraints. Reviewing and adjusting permissions can provide the necessary authorizations for a seamless experience.
- Refining User Roles: Assigning specific roles to different users can help clarify responsibilities and streamline permission management. By defining clear roles, it becomes easier to assign and revoke permissions, reducing the potential for complications.
- Implementing Secure Credentials: Utilizing secure authentication and authorization mechanisms can play a significant role in resolving permission issues. By confirming the validity and accuracy of the provided credentials, access can be granted or denied accordingly.
- Reviewing Firewall Settings: Configuring firewall settings to allow necessary network traffic can sometimes resolve permission-related challenges. Ensuring that the required ports and protocols are open and accessible can enhance connectivity between components.
- Monitoring Audit Logs: Examining audit logs can provide insights into permission-related events and actions. Identifying any discrepancies or anomalies in the logs can assist in pinpointing and rectifying permission issues effectively.
By incorporating these strategies and methodologies, individuals can troubleshoot and resolve permission issues, fostering a smoother interaction with the software environment. It is important to regularly review and enhance permission management practices to maintain a secure and efficient system.
Dealing with Resource Constraints
In the realm of software development and system administration, managing and troubleshooting issues related to limited resources is an essential task. When faced with resource constraints, it is crucial to understand the impact they can have on overall system performance and functionality.
Resource constraints, often referred to as limitations or scarcities, can manifest in various forms and affect different aspects of a system. These constraints may result in sluggish performance, intermittent connectivity, or even complete system failure.
One common resource constraint is insufficient memory, which can lead to slow response times, frequent crashes, and inability to handle concurrent tasks. Another constraint could be limited processing power, causing delays in data processing and execution of complex operations.
Resource constraints can also arise from network bottlenecks, where limited bandwidth or high network traffic impedes communication and connectivity between different components of a system. In such cases, it becomes crucial to optimize network configurations and prioritize the allocation of resources.
The key to dealing with resource constraints lies in identifying and analyzing the specific limitations that impact a system. Implementing efficient resource management techniques, such as prioritizing critical tasks, optimizing resource allocation, and employing caching mechanisms, can alleviate the effects of these constraints.
Moreover, adopting proactive measures like monitoring system performance, implementing automated alerts and notifications, and conducting regular capacity planning can help identify potential resource constraints before they severely impact the system.
Addressing resource constraints requires a combination of technical expertise, analytical skills, and an understanding of the system's architecture. By effectively managing and mitigating these constraints, organizations can ensure optimal system performance and enhance user experience.
FAQ
Why am I unable to connect to a Docker container in Windows?
There can be several reasons why you might be unable to connect to a Docker container in Windows. It could be due to misconfiguration of the network settings in Docker, firewall restrictions, or issues with the container itself. Additionally, make sure that the container is running and accessible on the correct IP address and port.
How can I troubleshoot the "Unable to Connect to Docker Container" issue in Windows?
If you are facing issues connecting to a Docker container in Windows, there are several steps you can take to troubleshoot the problem. Firstly, ensure that the container is running and accessible. Then, check the network settings in Docker to ensure they are properly configured. You can also check for firewall restrictions that might be blocking the connection. Lastly, make sure that the container is listening on the correct IP address and port.
Are there any specific Docker network configurations that could cause connection issues in Windows?
Yes, there are certain Docker network configurations that can lead to connection issues in Windows. One common problem is when a container is not attached to the correct network or there is a mismatch in network settings between the container and the host. Ensure that the container is connected to the appropriate network and that the network settings are consistent between the container and the host.
What should I do if I encounter a "Connection refused" error when trying to connect to a Docker container in Windows?
If you receive a "Connection refused" error while attempting to connect to a Docker container in Windows, there are a few possible causes. Firstly, check if the container is running and accessible. Then, verify that the container is listening on the correct IP address and port. Additionally, ensure that there are no firewall restrictions blocking the connection. If all else fails, try restarting Docker or the host machine.
Is there a way to connect to a Docker container running on Windows from another machine?
Yes, it is possible to connect to a Docker container running on Windows from another machine. To achieve this, you need to ensure that the container is running in a mode that allows external access, such as bridged or host mode. You also need to know the IP address of the machine running the Docker container and the port on which the container is listening. With this information, you can connect to the container from another machine using the IP address and port.
Why am I getting an "Unable to Connect to Docker Container in Windows" error?
If you are getting an "Unable to Connect to Docker Container in Windows" error, it could be due to various reasons. One common reason is that the container may not be running or may have crashed. Another possible reason is that there might be a network configuration issue, such as a firewall blocking the connection. It could also be caused by incorrect port mappings or container configurations. To troubleshoot the issue, you can check the container status, inspect the network settings, and review the container logs for any error messages.




