Today, we embark on a captivating journey into the realm of software isolation and containment. Our quest is to unravel the intricacies that set apart two prominent techniques: the enigmatic Linux Jail and the revolutionary Docker Container. With an insatiable curiosity, we delve deep into the heart of these concepts, seeking to comprehend their profound dissimilarities.
As we embark on this expedition, we are ushered into a world where robust security measures and efficient resource management reign supreme. Our objective? To understand how Linux Jail and Docker Container harness the power of isolation to provide a secure and efficient environment for running applications. Brace yourself for an intellectual exploration that will challenge your perception of software architecture.
In this captivating exploration, we shall navigate through a labyrinth of technologically advanced principles and methods. By comparing and contrasting the unique attributes of both Linux Jail and Docker Container, we aim to paint a vivid picture of their distinctive roles in the intricate tapestry of virtualization. Prepare to be enchanted by a symphony of terminologies, techniques, and ideologies.
Linux Jail vs Docker Container: How They Differ
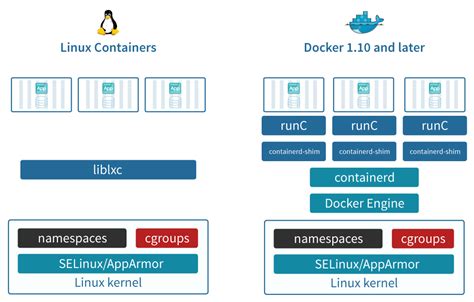
In the realm of software isolation and packaging, Linux Jail and Docker Container stand as two distinct approaches that serve similar purposes with unique characteristics. While both aim to provide efficient and secure environments for running applications, their underlying mechanisms and deployment methods differ significantly.
Differences in Isolation
When comparing Linux Jail and Docker Container technologies, it is essential to understand the differences in the level of isolation they provide.
While both Linux Jail and Docker Container offer mechanisms to encapsulate processes, files, and network resources, their approaches to isolation differ in significant ways.
A key distinction lies in the level of confinement each technology provides. Linux Jail, also known as FreeBSD Jail, utilizes operating system-level virtualization to separate processes and restrict their access to resources. On the other hand, Docker Container implements containerization using lightweight virtualization, which partitions the host operating system into isolated environments.
| Linux Jail | Docker Container |
|---|---|
| In Linux Jail, the isolation is achieved through the use of containers that share the same kernel as the host operating system. | Docker Container relies on containerization with the help of technologies like namespaces and cgroups, which offer enhanced isolation compared to Linux Jail. |
| Linux Jail primarily focuses on process-level isolation, ensuring that processes cannot interfere with each other or access restricted resources. | Docker Container extends the isolation to include file systems, network interfaces, and other resources, presenting a higher level of separation between containers. |
| Linux Jail is typically used for creating secure environments within a single host, limiting the potential impact of an exploited process. | Docker Container is built for deploying applications in a lightweight and portable manner, enabling consistent behavior across different hosts and environments. |
In summary, while Linux Jail and Docker Container share the goal of isolation, they employ distinct approaches that result in variations in the level and scope of isolation provided.
Differences in Resource Utilization
When comparing Linux jails and Docker containers, one important aspect to consider is the differences in resource usage. Both technologies provide mechanisms for isolating processes and their associated resources, but they do so in different ways.
In terms of resource allocation, Linux jails rely on the operating system's resource management capabilities, such as cgroups and namespaces. These mechanisms allow administrators to control the allocation of CPU, memory, disk space, and network bandwidth to individual jails. By carefully configuring resource limits, administrators can ensure that each jail gets its fair share of resources while preventing any single jail from monopolizing the system.
On the other hand, Docker containers utilize a layered approach to resource allocation. Each container is built using a base image, which contains the necessary dependencies and file system layers. This approach allows containers to share the underlying host operating system's resources more efficiently, resulting in reduced resource utilization. Docker also provides additional features like resource constraints and limits, allowing administrators to fine-tune resource allocation for individual containers.
Furthermore, Linux jails and Docker containers differ in terms of resource portability. Linux jails are tightly coupled to the underlying operating system and often require manual configuration to work on different systems. In contrast, Docker containers are designed to be highly portable, allowing them to run consistently across different environments. This portability simplifies the process of deploying and managing applications and facilitates a more flexible and scalable infrastructure.
- Linux jails rely on the operating system's resource management capabilities, such as cgroups and namespaces.
- Docker containers utilize a layered approach to resource allocation and can efficiently share the host operating system's resources.
- Linux jails often require manual configuration for portability, while Docker containers are designed to be highly portable.
Understanding these differences in resource utilization between Linux jails and Docker containers is crucial when considering which technology to use for your specific use case. It is essential to evaluate the trade-offs and choose the option that best suits your needs in terms of resource allocation, portability, and overall system performance.
Differences in Virtualization Technologies
In the realm of virtualization, various technologies have emerged, each offering distinct approaches to isolating and managing software applications. Understanding the differences between these virtualization technologies is crucial for choosing the most suitable solution for your needs.
While Linux Jail and Docker Container are two prominent virtualization technologies, they diverge in their fundamental principles and methodologies. Linux Jail, also known as FreeBSD Jail, employs an OS-level virtualization technique that isolates processes within a single operating system instance. On the other hand, Docker Container is based on containerization, a lightweight form of virtualization that allows for the creation of isolated environments to run applications.
One key distinction lies in the level of isolation provided by each technology. Linux Jail presents a more robust isolation by creating individual virtual environments for each process, which ensures that one process cannot interfere with another. In contrast, Docker Container operates within a shared kernel, enabling it to achieve higher efficiency and faster startup times for applications.
Another differentiating factor is the management and portability of these technologies. Docker Container offers a comprehensive management framework, allowing users to easily package applications and their dependencies into self-contained units called containers. These containers can be shared across different environments, ensuring consistent behavior and reducing software conflicts. Linux Jail, however, lacks these built-in management features, requiring more manual configuration and setup.
Ultimately, the choice between Linux Jail and Docker Container depends on the specific requirements of your project. If you prioritize strict isolation and security, Linux Jail may be the preferred option. Conversely, if scalability, portability, and efficient resource utilization are your main concerns, Docker Container offers a more flexible and user-friendly solution.
Comparison of Security Mechanisms
In this section, we will explore and compare the security mechanisms employed by Linux jails and Docker containers. Both of these technologies aim to provide isolation and protection for applications and processes, but they achieve this through different approaches and methods.
| Security Mechanism | Linux Jail | Docker Container |
|---|---|---|
| Process Isolation | Linux jails use operating system-level virtualization to isolate processes from the host and other jails. Each jail has its own file system, network stack, and user space, ensuring that processes within a jail are unable to interact with processes outside of it. | Docker containers utilize containerization technology to achieve process isolation. They leverage kernel namespaces and control groups to create a separate environment for each container. Each container has its own file system, network stack, and user space, ensuring that processes are isolated from one another. |
| Resource Control | Linux jails provide resource control features by allowing administrators to limit resource usage for each jail. This includes CPU utilization, memory allocation, and disk space usage. By setting resource limits, administrators can prevent a jail from impacting the performance and stability of the host system. | Docker containers offer similar resource control capabilities through the use of container-specific settings. Resource limits such as CPU shares, memory limits, and I/O throttling can be defined for each container, ensuring fair resource allocation and preventing containers from overwhelming the host system. |
| Security Profiles | Linux jails support the use of security profiles to further enhance security. These profiles define restrictions and permissions for different aspects of the jail, such as network access, file system access, and system calls. By carefully defining security profiles, administrators can strengthen the isolation and protect against potential vulnerabilities. | Docker containers employ a similar concept known as security policies. Security policies allow administrators to define and enforce restrictions on container behavior, such as network access, file system access, and capabilities. By enforcing strict security policies, Docker containers can mitigate potential security risks. |
| Image Integrity | Linux jails rely on system-level tools and mechanisms to ensure the integrity of the jail's image. This includes measures such as file system integrity checks, cryptographic verification, and image signing. | Docker containers place a strong emphasis on image integrity. Container images are typically built from a set of instructions defined in a Dockerfile, which allows for reproducibility and version control. Docker also provides mechanisms for verifying the integrity of pulled images and signing them for added security. |
By comparing the security mechanisms of Linux jails and Docker containers, we can better understand the different approaches and features that contribute to the overall security of these technologies. Both Linux jails and Docker containers have their own strengths and considerations, and the choice between them will depend on the specific use case and security requirements.
Differences in Portability
In the context of Linux Jail and Docker Container, a key aspect to consider is their level of portability. Portability refers to the ease with which a system or application can be moved and run across different environments.
When comparing the portability of Linux Jails and Docker Containers, it becomes apparent that there are notable distinctions. These variances have an impact on the flexibility and adaptability of each technology.
- Containerization: Docker Containers are designed with the objective of achieving maximum portability. By encapsulating the application and its dependencies into a container, they can be easily deployed and run on any system with Docker installed, regardless of the underlying operating system. This enables seamless movement of applications between different environments, such as development, testing, and production.
- Isolation: Linux Jails, on the other hand, provide a level of isolation within the same operating system environment. This means that they are limited to specific Unix-like operating systems, such as FreeBSD, and cannot be easily transported to other platforms. While this reduces portability, it also provides a higher level of security and resource utilization within the isolated environment.
- Dependencies: Docker Containers offer a significant advantage when it comes to managing dependencies. With Docker, the container image includes all the necessary libraries, frameworks, and dependencies required to run the application. This eliminates the need for manual installation and configuration of dependencies on different systems, ensuring consistent behavior across various environments. In contrast, Linux Jails rely on the host system's libraries and dependencies, which can cause compatibility issues when moving between different environments.
In summary, the portability of Docker Containers exceeds that of Linux Jails due to their ability to run on different operating systems, encapsulate dependencies, and facilitate easy deployment across various environments. However, Linux Jails offer a higher level of isolation and security within the same operating system environment. The choice between the two technologies should be based on the specific requirements and trade-offs that align with the desired use case.
Management and Administration
In the realm of Linux system environments, the role of management and administration plays a crucial part in optimizing performance and ensuring the smooth operation of both jails and docker containers. This section delves into the various aspects of managing and administering these two technologies, exploring the similarities and differences between them.
Handling Permissions: When it comes to managing permissions, both jails and docker containers employ distinct approaches. Jails utilize the concept of secure isolation to create an environment that separates processes and restricts interactions with the host system. In contrast, docker containers leverage the principle of containerization, enabling the encapsulation of applications and their dependencies into portable units.
Resource Allocation: Efficiently allocating system resources is another essential aspect of managing jails and docker containers. In jails, resource allocation is typically handled through various configuration parameters that control memory, CPU usage, and disk space limitations. Docker containers, on the other hand, utilize resource control groups (cgroups) to manage resource allocation and ensure fair distribution among running containers.
Networking: Networking is a vital component of management and administration for both jails and docker containers. Jails provide network isolation through the use of virtual network stacks and IP addresses, enabling secure communication within the jail environment. In the case of docker containers, network management is facilitated through the creation of virtual networks that enable seamless communication between containers or between containers and the host system.
Monitoring and Logging: Monitoring and logging are essential for managing jails and docker containers, as they provide insights into their performance and behavior. Jails offer monitoring through tools like iocage and resource monitoring utilities, enabling administrators to track resource usage and identify potential issues. Docker containers, on the other hand, utilize monitoring tools such as Docker Stats and Prometheus, which provide detailed metrics on resource utilization and container health.
Security: Security is of paramount concern when it comes to managing and administering jails and docker containers. Jails provide a robust level of security through the use of isolation mechanisms, file system restrictions, and privilege separation. Docker containers, too, prioritize security by implementing various features such as namespace isolation, user namespaces, and image verification to prevent unauthorized access and mitigate potential vulnerabilities.
Backup and Restore: Proper backup and restore procedures are essential for ensuring data integrity and recoverability in both jails and docker containers. Jails offer backup and restore capabilities through tools like iocage, allowing administrators to create snapshots and restore jails to previous states. Docker containers provide similar functionality through the use of Docker Compose files and docker commit commands, enabling the replication and restoration of containerized applications.
Updates and Patch Management: Keeping the system up to date and secure is a critical aspect of management and administration. Jails offer update mechanisms through FreeBSD's package management system, ensuring that the system and its dependencies remain current. Docker containers, on the other hand, utilize container image repositories and orchestration tools like Kubernetes to streamline the process of updating and patching containers.
Effective management and administration are instrumental in harnessing the full potential of both jails and docker containers. Understanding the nuances and specificities of these technologies allows system administrators to optimize performance, enhance security, and facilitate seamless operations within their respective environments.
Differences in Networking
When comparing the networking capabilities of Linux Jail and Docker Container, several distinctions become apparent. Let's delve into the unique networking features offered by each.
- Isolation: Both Linux Jail and Docker Container provide network isolation, ensuring that processes running within them have restricted network access. This segregation prevents interference from external sources and enhances security.
- Network Stack: Linux Jail employs its own network stack, which ensures complete virtualization of the network interface and facilitates the independent routing of network traffic. Docker Container, on the other hand, leverages the host system's network stack, utilizing its resources and eliminating the need for redundant implementations.
- Network Configuration: In terms of network configuration, Linux Jail allows for fine-grained control over network settings. IP addresses, routing tables, firewall rules, and other network parameters can be explicitly defined for each jail. Meanwhile, Docker Container provides a simplified approach to network configuration, abstracting away many of the complexities and enabling rapid deployment.
- Network Interfaces: Linux Jail offers the ability to create virtual network interfaces within the jail, enabling separate network namespaces and facilitating the segregation of network traffic. Docker Container, on the other hand, relies on Docker networking solutions, such as Docker Bridge or Overlay networks, to provide connectivity between containers and the external network.
- Inter-Container Communication: Docker Container excels in facilitating inter-container communication through the use of Docker networks. Containers can be connected to specific networks, allowing them to communicate seamlessly with other containers within the same network. Linux Jail, however, requires additional configurations and network bridges to achieve similar inter-jail communication.
These distinctions highlight the contrasting networking approaches of Linux Jail and Docker Container. While Linux Jail provides more extensive control and customization options, Docker Container simplifies network configuration and inter-container communication, streamlining the deployment and management process.
Comparison of Filesystem Isolation
In this section, we will explore the similarities and differences between the ways filesystem isolation is implemented in Linux jails and Docker containers. Both Linux jails and Docker containers provide a level of isolation for applications, allowing them to run securely and independently from each other. However, they utilize different mechanisms to achieve this isolation.
Filesystem Isolation in Linux Jails: In Linux jails, filesystem isolation is achieved through the use of chroot, a mechanism that changes the root directory for a process and its children. This creates a "jail" environment where the process operates within a restricted filesystem, unable to access files outside of its designated directory. This isolation ensures that the process is contained and cannot modify critical system files or interfere with other processes.
Filesystem Isolation in Docker Containers: Docker takes a different approach to filesystem isolation. It uses overlay filesystems, which allow multiple layers of filesystems to be stacked on top of each other. Each container in Docker has its own isolated filesystem, consisting of a read-write layer and a series of read-only layers. This allows each container to have its own separate filesystem, while still sharing common files and libraries from the underlying host system. Docker also provides additional features such as volumes, which allow data to be easily shared between containers or persisted outside of the container's lifespan.
Comparison: While both Linux jails and Docker containers provide filesystem isolation, there are some important differences to consider. Linux jails focus on limiting access to the filesystem by changing the root directory, providing a high level of isolation. However, this approach requires manual setup and configuration for each jail. On the other hand, Docker containers leverage the power of overlay filesystems, which offer a more flexible and dynamic filesystem isolation mechanism. Docker's approach simplifies management and deployment of isolated environments, making it easier to create and share containerized applications.
In conclusion, understanding the differences in filesystem isolation between Linux jails and Docker containers is crucial for choosing the appropriate solution for your specific use case. Whether you prioritize high-level isolation or ease of management, both options offer valuable ways to secure and compartmentalize applications.
Differences in Application Packaging
In the realm of isolating applications, Linux Jail and Docker Container each provide unique approaches to application packaging and management. These approaches differ in various aspects, including their underlying technology, levels of isolation, and resource utilization.
One key distinction lies in the way applications are packaged. In Linux Jail, applications are typically packaged using FreeBSD's Jail mechanism, which creates a lightweight virtual environment to isolate processes and their dependencies. This allows for applications to be encapsulated within their own file system, ensuring that they remain isolated from the host system and other applications. In contrast, Docker Containers adopt a different approach to packaging called containerization, which uses container images to package applications and their dependencies into portable and self-contained units. These images include all the necessary libraries, binaries, and configurations required to run the application, making it easier to replicate and deploy across different environments.
Another important distinction is the level of isolation provided by each technology. Linux Jail focuses on process-level isolation, ensuring that applications within a jail do not interfere with each other or the host system. This is achieved through effective resource isolation, including network, file system, and process isolation. On the other hand, Docker Containers extend this isolation further by providing an additional layer of virtualization at the operating system level. This means that each container operates as a separate instance from the host system, allowing for better isolation and security for applications.
Resource utilization also differs between Linux Jail and Docker Containers. Linux Jail relies on the host system's kernel and resources, meaning that the resources allocated to a jail are ultimately shared with the host and other jails. This can result in potential resource contention if not properly managed. In contrast, Docker Containers leverage containerization technology to provide resource isolation and control. Each container has its own isolated set of resources, including CPU, memory, and network, ensuring that applications running within the container have dedicated resources and are not impacted by other containers or the host system.
| Linux Jail | Docker Container |
|---|---|
| Uses FreeBSD's Jail mechanism | Utilizes containerization |
| Process-level isolation | Operating system-level isolation |
| Resource sharing with host and other jails | Resource isolation and control |
Performance Comparison: Linux Jail vs Docker Container
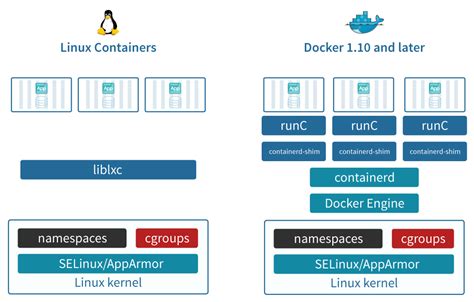
In this section, we will explore the performance differences between Linux Jails and Docker Containers, two popular techniques used for isolation and virtualization. By comparing their performance metrics, we can gain insights into their efficiency and potential trade-offs.
FAQ
What is the difference between Linux Jail and Docker container?
The main difference between Linux Jail and Docker container is in their level of isolation. Linux Jail, also known as chroot jail, provides a limited level of isolation by restricting processes to a specific directory. On the other hand, Docker container offers a higher level of isolation by creating an isolated environment with its own filesystem, networking, and processes.
Can Linux Jail and Docker container be used interchangeably?
No, Linux Jail and Docker container cannot be used interchangeably. Although they both provide some level of isolation, they have different purposes and mechanisms. Linux Jail is primarily used for restricting processes to a specific directory, while Docker container is used for creating isolated, lightweight environments for running applications.
Which is more secure, Linux Jail or Docker container?
Both Linux Jail and Docker container offer security benefits, but Docker container is generally considered more secure. Docker container provides better isolation between processes, prevents privilege escalation, and allows for fine-grained control over resource usage. However, it's important to note that the security of both Linux Jail and Docker container heavily depends on proper configuration and adherence to security best practices.
Are there any performance differences between Linux Jail and Docker container?
There can be performance differences between Linux Jail and Docker container. Docker container introduces a small overhead due to its additional layers and networking components, but it also provides optimizations such as resource sharing and efficient resource allocation. Linux Jail, being a simpler mechanism, typically has lower overhead but may not offer the same level of resource management and optimization as Docker container.
Can Docker containers be used inside a Linux Jail?
Technically, Docker containers can be used inside a Linux Jail, but it is not a recommended practice. Docker containers already provide their own isolation mechanisms and running them inside a Linux Jail can lead to unnecessary complexity and potential conflicts. It is generally more efficient and straightforward to utilize Docker's native isolation capabilities without relying on Linux Jail.




