Data management is an essential aspect of running any business or organization in today's digital age. It involves countless tasks that revolve around organizing, storing, and retrieving information. However, to ensure smooth and effective data management, it is crucial to set up your Windows environment correctly. By configuring your operating system to optimize database operations, you can enhance performance, improve security, and streamline workflows.
When it comes to database management, Windows offers a wealth of features and tools that can significantly aid in maintaining and securing your data. Leveraging these resources to their maximum potential can empower your team to work with efficiency and accuracy. From customizing system settings to utilizing the built-in security measures, every step you take towards optimizing your Windows environment is a step closer to streamlined database management.
One of the primary aspects to consider when fine-tuning your Windows for data management is optimizing system performance. An efficiently run operating system can handle large datasets, complex queries, and heavy workloads without experiencing lag or crashes. By configuring hardware resources, memory allocation, and prioritizing background processes, you ensure that your database operations run smoothly, providing reliable and timely results.
Moreover, it is vital to pay attention to the security of your data. With the increasing number of cybersecurity threats in today's interconnected world, database management requires stringent measures to protect sensitive information. Windows offers various security features, such as user access controls, encrypted connections, and firewalls, which can be configured to safeguard your database from unauthorized access and potential breaches.
Securing Access: Firewall Configuration for Efficient Database Administration
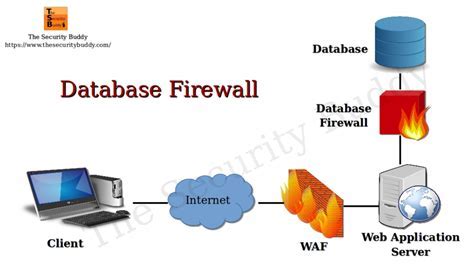
In today's digital landscape, safeguarding sensitive data is of utmost importance for any business or organization. To ensure the smooth and secure functioning of a database management system, it is imperative to configure firewall settings in a meticulous manner.
Firewall Settings:
1. Establishing Firewall Rules: Creating a robust set of rules that dictate which network traffic is allowed to access the database environment. This involves defining and configuring ports, protocols, and IP addresses that are necessary for the database management system's operation.
2. Implementing Access Control: Setting up firewall policies that filter incoming and outgoing traffic, allowing only authorized connections to the database. Configuring rules for individual users or user groups based on specific roles, privileges, or organizational requirements.
3. Enabling Intrusion Detection: Activating firewall features that monitor network traffic for any suspicious or unauthorized activities. This includes detecting and blocking potential threats such as SQL injection attacks or unauthorized access attempts.
4. Continuous Monitoring and Updates: Regularly reviewing firewall logs and updating firewall rules as necessary to adapt to evolving security threats and changing business needs. Ensuring that firewall software and firmware are updated with the latest patches and security fixes.
By diligently configuring firewall settings, organizations can fortify their database management system against potential cyber threats, unauthorized access, and data breaches. It is crucial to strike a balance between data security and accessibility while tailoring the firewall configuration to meet the specific needs of the database environment.
Boosting Windows Efficiency for Database Supervision
In this section, we will explore techniques to enhance the performance of your operating system specifically tailored for overseeing and organizing data repositories. By implementing these optimizations, you can significantly improve the overall efficacy of your Windows-based environment, allowing for smoother and more efficient management of databases.
1. Exploit Resource Allocation Utilize resource allocation strategies intelligently to allocate system resources effectively. By optimizing the allocation of CPU, memory, and disk usage, you can ensure that your database management operations receive the necessary computational power and storage capacity for optimal performance. |
2. Streamline Start-up Processes Analyze and streamline start-up processes to eliminate unnecessary applications and services that may consume system resources and lead to sluggish system performance. Identifying and disabling irrelevant startup programs can reduce unnecessary load on your system, resulting in improved responsiveness when managing databases. |
3. Fine-tune System Parameters Improve the performance of your Windows system by adjusting and fine-tuning various parameters such as I/O settings, disk cache size, and memory management. Optimizing these settings can enhance database operations by reducing disk I/O bottlenecks and improving data retrieval and storage efficiency. |
4. Utilize Disk Partitioning Efficiently manage database storage by using disk partitioning techniques. By separating data, log files, and operating system files into different partitions or drives, you can isolate and optimize the dedicated space for your databases, minimize disk fragmentation, and enhance overall system performance. |
5. Monitor System Health Implement comprehensive system monitoring tools to regularly assess the health and performance of your Windows environment. By closely monitoring system metrics, disk usage, and network activity, you can identify and address potential bottlenecks or issues that may impact your database management tasks. |
Choosing the Right Windows Version for Efficient Database Operations

Introduction: In order to ensure optimal performance and security for your database management system, it is crucial to select the most suitable version of the Windows operating system. This section will guide you through the process of determining the appropriate Windows edition, highlighting key factors to consider and providing recommendations for effective database management.
Evaluating System Requirements: Before embarking on the installation of a Windows version, it is necessary to evaluate your hardware and software requirements. Look for compatibility with your system's processor architecture, memory capacity, and disk space. Additionally, consider the compatibility of your database management system with specific Windows editions, as certain versions may offer enhanced features and compatibility.
Understanding Licensing Options: To make an informed decision, it is essential to understand the different licensing options available for Windows versions. Evaluate the benefits and limitations of each licensing model, such as volume licensing or subscription-based licenses, to ensure compliance and cost-effectiveness for your specific database management needs.
Exploring Specialized Windows Editions: Microsoft offers a variety of specialized Windows editions tailored to meet specific business requirements. Explore specialized editions, such as Windows Server, which are designed to maximize performance, security, and scalability for database management operations. Consider whether features like clustered databases, high availability, or data analytics capabilities are necessary for your organization's database infrastructure.
Considering Security Features: Security is a critical aspect of database management. When selecting a Windows version, evaluate the built-in security features, such as Windows Defender Firewall, Windows Hello, and BitLocker encryption. These features play a vital role in safeguarding your database infrastructure against potential threats and unauthorized access.
Finalizing the Decision: After carefully assessing your system requirements, licensing options, specialized editions, and security features, it is time to finalize your decision. Choose the Windows version that aligns with your organization's needs, budget, and long-term growth plans for efficient and reliable database management.
Enhancing Security Measures for Windows User Accounts in Database Administration
In the realm of overseeing and safeguarding data within a database, one significant aspect crucial to consider is the reinforcement of security protocols involving user accounts in a Windows environment. This article aims to explore various strategies and guidelines for fortifying user account security, without compromising system accessibility or impeding administrative functionality.
1. Implementing Strong Password Policies
One fundamental step in securing Windows user accounts for database management is the implementation of robust password policies. This entails creating rules that enforce the use of complex passwords, incorporating a combination of alphanumeric characters, symbols, and varying case sensitivity. Additionally, regular password updates and the prohibition of commonly-used or easily guessable passwords contribute to enhancing the overall security of user accounts.
2. Enabling Two-Factor Authentication
Adding an extra layer of protection to user accounts, the implementation of two-factor authentication can significantly minimize the risk of unauthorized access. By requiring users to provide a second form of verification, such as a unique code generated through a mobile app or received via SMS, the system adds an additional barrier against potential security breaches.
3. Restricting User Privileges
In a database management setting, it is essential to assign user privileges according to specific roles and responsibilities. By granting only the necessary access rights to individual user accounts, the risk of unauthorized access or accidental data manipulation is reduced. Applying the principle of least privilege (PoLP) ensures that users can only access and modify the data required for their designated tasks.
4. Regularly Monitoring User Account Activity
Continuous monitoring of user account activity is a vital practice in maintaining robust security measures. By keeping a close eye on login attempts, system administrators can identify unusual patterns, potential brute-force attacks, or suspicious activities within the database. This allows for timely intervention and the implementation of additional security measures, if needed.
5. Conducting Regular Security Audits
To ensure the ongoing effectiveness of implemented security measures, regular security audits should be conducted. These audits involve comprehensive evaluations of user account settings, permissions, and access rights. By identifying potential vulnerabilities and weaknesses, administrators can make necessary adjustments and improvements to keep the database secure.
Implementing strong password policies, enabling two-factor authentication, restricting user privileges, monitoring account activity, and conducting regular security audits form the pillars of an effective user account security strategy in Windows-based database management. By combining these measures, organizations can proactively protect their valuable data assets while facilitating efficient and secure administrative operations.
Selecting the Perfect Antivirus Solution for Efficient Database Administration

Securing your computer system from malicious threats is crucial for smooth and effective database administration. As a database manager, it is essential to carefully choose the right antivirus software that aligns with your specific requirements.
When it comes to safeguarding your data and ensuring the reliability and integrity of your database, a robust antivirus solution is a necessity. It acts as a shield against various types of malware, such as viruses, Trojans, worms, and spyware that can compromise the security of your database.
Understanding the Factors:
While selecting antivirus software for database management, there are several factors to consider. Firstly, it is important to look for a solution that offers real-time protection, as it can detect and prevent malware from infecting your system immediately.
Additionally, compatibility with your operating system is vital. You need to ensure that the antivirus software supports the version of the OS you are using for database management.
Another crucial factor is the scanning speed and efficiency of the antivirus software. A slow scanning process can significantly impact the performance of your database management activities. Therefore, opt for a solution that offers fast and accurate scans without compromising the system's speed.
Furthermore, considering the reputation and credibility of the antivirus provider is essential. Look for established and well-known companies that have a track record of providing reliable antivirus software.
Conclusion:
Choosing the right antivirus software for database management is an essential step towards maintaining the security and integrity of your database. By carefully evaluating the various factors mentioned above, you can select a solution that best meets your needs and ensures a smooth, secure, and efficient database management experience.
Maximizing Database Performance with Efficient Windows Update Management
Ensuring optimal performance of your database requires a comprehensive approach that goes beyond regular database management tasks. One often overlooked aspect is the effective management of Windows updates, which can have a significant impact on the overall performance of your database system.
Properly managing Windows updates helps maintain a stable and secure environment for your database, as well as ensuring that the latest improvements and bug fixes are implemented. However, indiscriminate installation of updates without considering their potential impact on database performance can lead to unwanted disruptions and decreased efficiency.
To maximize database performance, it is important to establish a structured approach to Windows update management. This involves understanding the different types of updates available, evaluating their relevance to your database environment, and implementing a well-defined update schedule that minimizes disruptions to critical database operations.
A key aspect of efficient Windows update management is the ability to control when and how updates are installed. This can be achieved through the use of Windows Update Group Policies, which allow you to customize update settings and decide which updates are installed automatically and which require manual intervention.
In addition to controlling the installation process, it is vital to assess the potential impact of updates on database performance before implementing them. This can be done by setting up a separate test environment where updates can be evaluated prior to deployment in the production database system. Regular performance testing and monitoring can help identify any potential issues and ensure that updates do not adversely affect database performance.
Furthermore, creating a comprehensive backup and recovery strategy is essential when managing Windows updates for database performance. In the event of any issues or unexpected consequences resulting from an update, having a reliable backup allows you to quickly restore the database to its previous working state, minimizing downtime and potential data loss.
In conclusion, efficient Windows update management plays a crucial role in maximizing the performance of your database system. By carefully evaluating updates, controlling the installation process, and implementing a well-structured update schedule, you can maintain a stable and efficient environment that supports your database operations while minimizing disruptions and ensuring the security of your data.
| Benefits of Efficient Windows Update Management for Database Performance |
|---|
| - Improved stability and security of the database environment |
| - Access to the latest bug fixes and improvements |
| - Minimized disruptions to critical database operations |
| - Enhanced control over the installation process |
| - Potential performance optimization through testing and monitoring |
| - Reliable backup and recovery strategy for risk mitigation |
Configuring Services for Efficient Data Administration on Windows Systems
In this section, we will explore the crucial steps involved in setting up and customizing essential services on Windows operating systems to optimize database management functionality. By configuring these services, you can enhance the efficiency, security, and performance of your database infrastructure.
- Identifying and Optimizing Key Services
- Securing and Restricting Access to Database Services
- Tuning Services for Maximum Performance
- Enabling Monitoring and Alerting Mechanisms
- Implementing Backup and Recovery Services
In order to achieve seamless data administration and management, it is essential to ensure that the appropriate services are set up and configured according to your specific requirements. By following best practices and leveraging advanced service settings, you can establish a robust foundation for successful database management on Windows systems.
Optimizing Disk Configuration for Efficient Database Operations
In the realm of organizing your storage resources to maximize the performance and efficiency of database operations, selecting the most appropriate disk configuration is of paramount importance. The disk configuration you choose can significantly impact the overall speed, reliability, and scalability of your database management system.
When it comes to choosing the best disk configuration for effective database management, several factors should be taken into consideration. These factors include the type of database workload, the size of the database, and the specific performance requirements of your application. By carefully evaluating these factors, you can determine the most suitable disk configuration that aligns with your unique database management needs. To facilitate this evaluation process, refer to the table below which highlights various disk configurations and their respective advantages:
| Configuration | Advantages |
|---|---|
| RAID 0 (striping) | Improved read/write performance by distributing data across multiple disks |
| RAID 1 (mirroring) | Enhanced data redundancy and fault tolerance through data duplication |
| RAID 5 (striping with distributed parity) | Balanced performance and data protection through striping and distributed parity |
| RAID 10 (mirrored striping) | Combines benefits of RAID 0 and RAID 1 for optimal performance and redundancy |
| SSD (Solid State Drive) | Exceptional read/write speeds and improved response times for demanding workloads |
It is crucial to note that there is no one-size-fits-all solution when it comes to disk configuration for database management. The choice ultimately depends on your specific requirements and priorities. For example, if your application demands high read/write speeds, RAID 0 or SSD configurations might be more suitable. Conversely, if data redundancy and fault tolerance are of utmost importance, RAID 1 or RAID 10 configurations are preferable.
Furthermore, consider the scalability of your chosen disk configuration. As your database grows and workload intensifies, it is essential to ensure that your disk configuration can accommodate future expansion and maintain optimal performance levels.
In conclusion, selecting the best disk configuration for effective database management involves a thoughtful evaluation of your database workload, size, performance requirements, and growth potential. By considering these factors and leveraging the advantages of various disk configurations, you can optimize your database operations to achieve enhanced performance, reliability, and scalability.
Optimizing Network Configuration for Enhanced Database Performance

Introduction: This section focuses on the crucial steps involved in configuring network settings to improve database performance. Efficient network configuration plays a pivotal role in enhancing the speed, reliability, and overall performance of database systems. By carefully fine-tuning various network parameters and optimizing settings, database administrators can ensure seamless communication between servers and clients, minimizing latency and maximizing throughput.
Enhancing Memory Configuration for Efficient Database Operations
Ensuring optimal memory settings is crucial for effective management of databases, offering enhanced performance and productivity. Adjusting memory configurations allows for efficient utilization of system resources, resulting in improved response times, reduced latency, and increased throughput without compromising data integrity or security.
Allocate Sufficient Memory: Assign an appropriate amount of memory to the database management system to accommodate the size and complexity of the database. Adequate memory allocation enables faster data retrieval and processing, minimizing disk I/O operations and enhancing overall system performance.
Utilize Caching Mechanisms: Implementing efficient caching techniques, such as query result caching or data caching, can significantly reduce the load on the database server. Caching frequently accessed data or query results in memory speeds up retrieval operations, reduces latency, and improves response times for subsequent requests.
Consider Workload Patterns: Analyze the workload patterns and usage characteristics of the database. Understanding the type and frequency of queries, data manipulation operations, and concurrent connections helps determine the optimal memory settings for different scenarios. Prioritize memory allocation based on the criticality and frequency of specific operations to maximize efficiency.
Tune Memory Parameters: Fine-tune parameters related to memory management, such as buffer pools, shared memory, and query cache size. Optimizing these parameters ensures that memory resources are effectively utilized, minimizing overhead and maximizing available memory for essential database operations.
Monitor and Adjust: Regularly monitor memory utilization and performance metrics to identify any potential issues or bottlenecks. Adjust memory settings as necessary, based on performance analysis, workload changes, or system requirements. Continuously monitoring and optimizing memory allocation preserves system stability and ensures efficient database management.
Implement Intelligent Memory Management: Consider employing advanced memory management techniques, such as dynamic memory allocation, memory compression, or automatic memory tuning. These intelligent mechanisms adaptively adjust memory configurations based on system demands, providing efficient resource allocation and improved database performance.
Final Thoughts: Optimizing memory settings plays a vital role in achieving efficient database management. By allocating sufficient memory, leveraging caching mechanisms, considering workload patterns, tuning memory parameters, monitoring performance, and implementing intelligent memory management, organizations can unlock enhanced database performance and effectively manage their data-driven operations.
FAQ
What operating system is compatible with setting up Windows for database management?
Setting up Windows for database management is compatible with various operating systems such as Windows 10, Windows Server 2016, and Windows Server 2019.
What is the recommended hardware configuration for setting up Windows for database management?
The recommended hardware configuration for setting up Windows for database management typically includes a multi-core processor, at least 8GB of RAM (16GB or more is preferable), a solid-state drive for better performance, and enough storage space to accommodate the databases.
What software is needed to set up Windows for database management?
To set up Windows for database management, you will need to install a relational database management system (RDBMS) software such as Microsoft SQL Server or MySQL. Additionally, a development environment or an integrated development environment (IDE) for database management, such as Microsoft SQL Server Management Studio or phpMyAdmin, is recommended.
What are some security measures to consider when setting up Windows for database management?
When setting up Windows for database management, it is important to implement various security measures. This includes setting strong passwords for database accounts, encrypting database connections with SSL/TLS, regularly patching and updating the operating system and database software, implementing firewalls, and access control mechanisms to restrict unauthorized access to the databases.




