As the digital world continues to evolve, so do the threats that lurk in the shadows. With the increasing need to connect remotely and access sensitive information, safeguarding your online presence is now more crucial than ever. In this article, we will delve into the intricacies of optimizing your device's settings to establish a secure and seamless virtual private network (VPN) connection.
By implementing the right configuration settings, you can shield your valuable data from prying eyes and cyberspace intruders. Discover the tried and tested techniques to strengthen your online security, ensuring a seamless and uninterrupted browsing experience.
In this comprehensive guide, we will explore strategies to tighten your device's defenses, protect your private information, and maintain your online anonymity. Through a step-by-step walkthrough, we will uncover the nuances of customizing your device to seamlessly connect to a VPN, unlocking a whole new level of online protection.
Join us as we navigate the intricate world of VPN connectivity. Gain insight into the critical components that make up a secure VPN connection and learn how to configure your devices effortlessly. Regardless of your technical prowess, this guide will provide you with the necessary knowledge and resources to embark on a secure online journey.
Crucial Considerations for Establishing a Secure VPN Connection on Your Windows System
Creating a secure Virtual Private Network (VPN) connection on your Windows device requires careful planning and attention to several important factors. When configuring your VPN connectivity, it is vital to consider various aspects that can greatly impact the performance, reliability, and security of your connection.
In order to ensure a successful VPN setup, it is essential to determine the appropriate VPN protocol that suits your specific requirements. Different protocols offer varying levels of encryption, speed, and compatibility, so analyzing your needs and selecting the most suitable option is key.
- Network Compatibility and Firewall Considerations:
- Authentication and Encryption Methods:
- Bandwidth and Performance Optimization:
- Logging and Privacy Concerns:
- Compatibility with Other Network Services:
Before establishing a VPN connection, it is crucial to assess the compatibility of your network infrastructure and any potential conflicts with firewalls. Some network configurations may restrict VPN access or hinder its functionality, so thoroughly evaluating these aspects beforehand is essential.
Choosing an appropriate authentication and encryption method is vital to ensure the confidentiality and integrity of your data. Strong encryption protocols, such as AES-256, combined with secure authentication mechanisms like certificate-based authentication or two-factor authentication, provide an enhanced level of security for your VPN connections.
Optimizing your network's bandwidth utilization and performance is crucial when setting up a VPN connection. Network congestion and bandwidth limitations can negatively affect the speed and reliability of your VPN, so implementing techniques such as Quality of Service (QoS) or prioritization of VPN traffic can help mitigate these issues.
Privacy is a significant consideration when configuring a VPN connection. Reviewing the logging policies of your chosen VPN service provider is essential to ensure they align with your privacy requirements. Understanding what data is being logged and for how long can help you make informed decisions regarding your online privacy.
Consider the compatibility of your chosen VPN solution with other network services and applications. Ensuring that your VPN works seamlessly with other critical services such as remote desktop, VoIP, or file sharing applications is essential to maintain uninterrupted workflow and efficiency.
By taking these essential considerations into account when configuring your VPN connection on Windows, you can establish a secure and reliable network connection that meets your specific needs.
Determining Your VPN Requirements
In this section, we will explore the factors to consider when determining your specific requirements for setting up a VPN connection. By understanding your needs and goals, you can ensure that the configuration meets your unique needs for secure and reliable connectivity.
Defining Security Priorities: One of the first steps in determining your VPN requirements is identifying your security priorities. Consider the importance of confidentiality, integrity, and availability of your data. Evaluate the level of protection required for sensitive information and the potential risks associated with unauthorized access.
Assessing Network Infrastructure: Analyze your existing network infrastructure to determine the compatibility and capacity for VPN connectivity. Assess the availability of resources such as routers, firewalls, and servers that are necessary for establishing a VPN connection. Consider the bandwidth limitations and potential performance impacts to ensure a smooth and efficient connection.
Evaluating User Accessibility: Determine the number of users who will require access to the VPN, as well as their locations and devices. Consider whether remote access is required for employees working from home or traveling, or if access is limited to specific locations. This assessment will help determine the scalability and flexibility required for your VPN configuration.
Identifying Protocols and Encryption: Evaluate the protocols and encryption methods supported by your VPN client and server. Consider the compatibility with your existing systems and the level of encryption required to ensure secure data transmission. This step will help determine the appropriate VPN protocol and encryption algorithms to be used.
Defining Authentication Mechanisms: Determine the authentication mechanisms that align with your security requirements. Assess whether username and password combinations are sufficient or if multi-factor authentication is necessary. Consider the availability of authentication servers such as RADIUS or Active Directory, or the need for certificate-based authentication.
Considering Business Continuity: Evaluate the impact of VPN connectivity on your business continuity plans. Assess whether redundant connections, failover mechanisms, or backup servers are necessary to ensure uninterrupted access to critical resources. Consider the potential disruptions and downtime that may be associated with VPN configuration changes or maintenance.
Reviewing Legal and Compliance Requirements: Lastly, consider any legal and compliance requirements that pertain to your industry or organization. Determine if there are specific regulations or standards that dictate the use of VPNs, such as HIPAA or GDPR. Ensure that your VPN configuration aligns with these requirements to avoid any violations or breaches.
By thoroughly assessing these factors, you can determine your specific VPN requirements and proceed with configuring your Windows environment for secure and efficient connectivity.
Choosing the Right VPN Protocol

Exploring the various options available when it comes to selecting the correct VPN protocol is a crucial step in achieving optimal connectivity and security. Each protocol offers unique advantages and considerations, and understanding these differences will help determine the best fit for your specific needs.
- OpenVPN: This open-source protocol is highly versatile and widely used due to its strong security features and compatibility across platforms.
- L2TP/IPsec: Offering excellent security through the combination of the Layer 2 Tunneling Protocol (L2TP) and Internet Protocol Security (IPsec), this protocol is often used for mobile devices.
- PPTP: Despite being the least secure option, Point-to-Point Tunneling Protocol (PPTP) is often chosen for its simplicity and compatibility with older devices.
- SSTP: Developed by Microsoft, Secure Socket Tunneling Protocol (SSTP) is a reliable choice for Windows users, as it leverages the built-in security features of the operating system.
- WireGuard: Known for its exceptional speed and simplicity, WireGuard is gaining popularity for its modern cryptographic protocols and efficient implementation.
Considerations such as security, speed, device compatibility, and ease of use should guide your decision-making process. Evaluating the unique features of each protocol will ensure the establishment of a VPN connection that meets your specific requirements.
Enhancing Security Measures for Seamless VPN Integration
Implementing robust security settings is vital to ensure a secure and uninterrupted VPN connection. This section focuses on optimizing your system's security measures to achieve a seamless integration with your VPN service.
1. Strengthening Authentication: Authentication plays a crucial role in keeping unauthorized users at bay while maintaining the integrity of your VPN connection. Explore various authentication methods, including username/password, certificates, or multifactor authentication, to choose the most suitable one for your needs.
2. Encryption for Unbreachable Privacy: Encrypting the data transmitted through your VPN connection is essential to safeguard the confidentiality of your information. Investigate different encryption protocols, such as OpenVPN, IPSec, or SSL/TLS, to determine the best encryption method that meets your security requirements.
3. Firewall Configuration: Configuring your firewall is instrumental in blocking malicious network traffic and protecting your system from unauthorized access. Employ a reliable firewall solution and ensure that it is correctly set up to permit VPN traffic while still enforcing stringent security rules.
4. Intrusion Detection and Prevention: Deploying an intrusion detection and prevention system reinforces your defense against potential attacks. Consider implementing an IDS/IPS solution to monitor network traffic, detect suspicious activities, and proactively respond to any security threats.
5. Regular Security Updates: Staying up to date with the latest security patches and updates is paramount in maintaining a secure VPN connection. Regularly check for system updates, including security patches for the operating system, VPN client, and any relevant third-party software, to ensure that your system is protected against known vulnerabilities.
6. Auditing and Logging: Enabling auditing and logging features helps you track and analyze VPN activity for any anomalies or potential security breaches. Configure appropriate logging levels to capture relevant information, which can assist in forensic analysis and incident response in case of any security incidents.
Note: Properly configuring security settings for VPN connectivity is a crucial aspect of ensuring the confidentiality, integrity, and availability of your network resources. The specific steps for configuring these settings may vary depending on your operating system and VPN client software.
Setting up VPN Client Software on your Windows Device
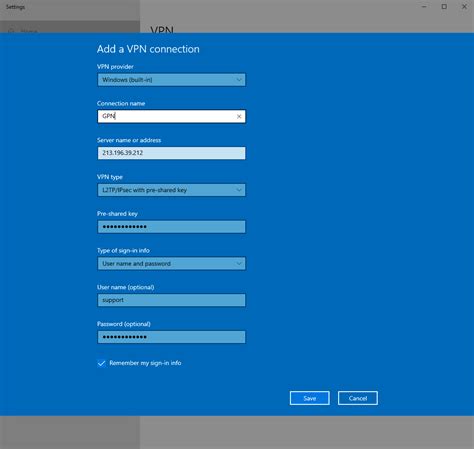
In this section, we will explain the process of setting up VPN client software on your Windows device, allowing you to securely connect to your desired virtual private network. By following these steps, you will be able to establish a VPN connection on your Windows device in a few simple and straightforward steps.
To begin, you will need to navigate to the official website of your chosen VPN provider. Once there, you can download the appropriate VPN client software for your Windows device. It is important to ensure that you are downloading the correct version that is compatible with your device's operating system.
- Step 1: Locate the download button on the website and click on it to start the download process.
- Step 2: Once the download is complete, locate the downloaded file and double-click on it to initiate the installation process.
- Step 3: Follow the on-screen instructions provided by the installation wizard to install the VPN client software. You may need to agree to the terms and conditions, choose an installation directory, and select any additional components you wish to install.
- Step 4: After the installation is complete, launch the VPN client software from your Windows device.
Upon launching the software, you will typically be greeted with a login screen. Here, you will need to enter your VPN provider's credentials, which typically include a username and password. Make sure to enter these details correctly to authenticate your access to the VPN network.
Once you have logged in, you will be presented with a user-friendly interface that allows you to select your desired VPN server location. This is an important step, as it determines the virtual location your device will be connected to, providing you with various benefits such as enhanced privacy, security, and access to geographically restricted content.
After selecting the server location, you can click on the "Connect" or "Start" button to establish a connection to the VPN network. The VPN client software will then initiate the connection process, securely tunneling your internet traffic through the VPN server.
Once the connection is established, you will be able to browse the internet, access online resources, and utilize network-dependent applications with the added security and privacy offered by the VPN.
Remember, if you encounter any issues during the setup or connection process, you can refer to your VPN provider's support documentation or contact their customer support for assistance.
Creating Firewall Exceptions for VPN Traffic
Enhancing your network security while ensuring seamless VPN connection requires the establishment of appropriate firewall exceptions. In this section, we will discuss the essential steps to create necessary firewall exceptions to allow secure VPN traffic.
To enable VPN connectivity without compromising your network's protection against potential threats, it is crucial to configure your firewall settings effectively. Firewall exceptions play a vital role in permitting VPN traffic to pass through your network's security measures. These exceptions need to be meticulously planned and implemented to strike the right balance between network accessibility and safeguarding against unauthorized access.
Setting up firewall exceptions primarily entails identifying the specific protocols, ports, and IP addresses associated with your VPN connection. This involves determining which network resources VPN traffic needs to access and ensuring that the necessary firewall rules are defined to permit this communication. By strategically creating exceptions within your firewall configuration, you can segregate VPN traffic from other non-essential network communication, limiting potential vulnerabilities.
When creating firewall exceptions, it is essential to consider the specific VPN technologies and protocols in use. Whether you employ PPTP, L2TP/IPsec, OpenVPN, or another VPN technology, each has its unique requirements for allowing traffic through firewalls. By understanding these requirements, you can tailor your firewall exceptions to suit your specific VPN deployment and improve overall network security.
Additionally, firewall exceptions should not only focus on outbound traffic but also consider inbound traffic requirements. By allowing incoming VPN traffic through carefully defined firewall rules, you can enable remote access to your network while maintaining security. However, it is crucial to restrict access to only authorized VPN users and implement robust authentication methods to prevent unauthorized access attempts.
In conclusion, creating firewall exceptions for VPN traffic is a critical aspect of ensuring secure connectivity. Understanding the specific needs and requirements of your VPN technology, identifying the appropriate protocols, ports, and IP addresses, and implementing well-defined firewall rules are key steps to strike the right balance between accessibility and network protection. By following these guidelines, you can establish a robust firewall configuration that enhances your network security while facilitating seamless VPN connectivity.
Troubleshooting Common VPN Connection Issues

In this section, we will address the frequent challenges encountered when establishing a VPN connection on various devices. We will provide practical tips and techniques to overcome these issues, ensuring a seamless and secure connection for your browsing needs.
1. Connection Timeout
Oftentimes, users may experience a connection timeout when attempting to connect to a VPN server. This can be caused by various factors such as server overload, network congestion, or incorrect server settings. To resolve this issue, try connecting to a different server location, check your network settings, or contact your VPN service provider for assistance.
2. Authentication Problems
Authentication problems can occur if the entered username, password, or public key is incorrect or expired. Ensure that you have entered the correct credentials and check for any leading or trailing spaces. Additionally, verify that your VPN service subscription is active and up-to-date. If the issue persists, consider resetting your password or contacting your VPN provider for further guidance.
3. Limited Internet Connectivity
In some cases, after establishing a VPN connection, users may experience limited internet connectivity or restricted access to certain websites or services. This can be due to firewall settings, network restrictions, or IP address conflicts. To resolve this, try disabling any firewalls temporarily, ensure that your VPN is configured to allow internet access, or contact your network administrator for assistance.
4. Slow Connection Speeds
Slow connection speeds can be a common complaint when using a VPN. This can be caused by network congestion, server load, or a slow internet connection. To improve speeds, try connecting to a different server location, switch to a protocol optimized for speed, or upgrade your internet service plan. Additionally, it may be helpful to close any unnecessary applications or downloads that could be utilizing bandwidth.
5. DNS Resolution Issues
DNS resolution issues can prevent a VPN connection from establishing properly. This can result in websites not loading, DNS leaks, or misrouted traffic. To resolve this, ensure that your DNS settings are configured correctly, consider using a VPN client with built-in DNS leak protection, or try manually specifying DNS servers provided by your VPN service.
| Problem | Solution |
|---|---|
| Connection Timeout | Try connecting to a different server location or check network settings. |
| Authentication Problems | Verify credentials and ensure VPN subscription is active. |
| Limited Internet Connectivity | Temporarily disable firewalls and ensure VPN allows internet access. |
| Slow Connection Speeds | Connect to a different server, switch protocols, or upgrade internet plan. |
| DNS Resolution Issues | Check DNS settings, use VPN client with DNS leak protection, or specify DNS servers. |
Securing Your VPN Connection on Windows
Ensuring the utmost security for your virtual private network (VPN) connection is essential in today's cyber landscape. In this section, we will explore key strategies and best practices to safeguard your VPN access on the Windows operating system.
- Choose a Strong and Unique Password:
- Enable Two-Factor Authentication:
- Regularly Update Your VPN Software:
- Utilize a Firewall:
- Encrypt Your Data:
- Use Trusted and Secure Networks:
Start by creating a strong and unique password for your VPN connection. Avoid using common words or predictable combinations and consider incorporating a mix of uppercase and lowercase letters, numbers, and special characters. It is also crucial that you do not reuse passwords across different platforms.
Adding an extra layer of security to your VPN connection is achievable by enabling two-factor authentication (2FA). This feature requires users to provide a second form of verification, such as a unique code sent to their mobile device or generated by an authenticator app, in addition to their password.
To stay protected against potential vulnerabilities, it is vital to keep your VPN software up to date. Manufacturers often release updates and patches to address security flaws and enhance overall stability. Make it a habit to regularly check for updates and promptly install them.
Incorporating a firewall into your VPN setup can provide an extra layer of protection by monitoring and controlling incoming and outgoing network traffic. Windows operating system offers a built-in firewall that can be configured to filter traffic and protect your connection from malicious activities.
Encrypting your data is an essential step in securing your VPN connection. Ensure that your VPN software supports strong encryption protocols such as OpenVPN or IKEv2. Encryption will scramble your data, making it unreadable to unauthorized individuals attempting to intercept your connection.
When connecting to your VPN, it is important to choose trusted and secure networks. Avoid using public Wi-Fi networks or unsecured connections, as these can be susceptible to eavesdropping and hacking attempts. Opt for secure networks you trust, such as your home or office network.
Install and Configure OpenVPN Server in Windows PC
Install and Configure OpenVPN Server in Windows PC by Techy Druid 37,186 views 4 months ago 17 minutes
How To Add and Enable FREE VPN On Windows 11
How To Add and Enable FREE VPN On Windows 11 by Murugan S 303,433 views 2 years ago 3 minutes, 11 seconds
FAQ
What is VPN connectivity?
VPN connectivity refers to the ability to establish a secure and private connection between a device and a remote network using a Virtual Private Network (VPN). This allows users to access resources on the remote network as if they were directly connected to it.
Why do I need to configure Windows for VPN connectivity?
Configuring Windows for VPN connectivity is necessary to ensure a secure and reliable connection. By configuring Windows, you can set up the necessary protocols, security settings, and authentication methods to establish a VPN connection and protect your data from unauthorized access.
Can I configure multiple VPN connections on Windows?
Yes, you can configure multiple VPN connections on Windows. Each VPN connection will have its own settings, including the VPN provider, connection name, server address, and authentication method. This allows you to easily switch between different VPN services or connect to different remote networks.
Why is it necessary to configure Windows for VPN connectivity?
Configuring Windows for VPN connectivity is necessary in order to establish a secure connection to a remote network or server. VPN (Virtual Private Network) allows users to access resources securely over the internet, protecting their data and ensuring privacy.
What steps are involved in configuring Windows for VPN connectivity?
Configuring Windows for VPN connectivity requires a few key steps. Firstly, you need to set up a VPN connection on your Windows device by going to the Network & Internet settings and adding a new VPN connection. Then, you will need to enter the necessary details such as the server address, authentication method, and credentials. After that, you can connect to the VPN by clicking on the network icon in the system tray and selecting the VPN connection. Finally, you may need to configure additional settings such as split tunneling or DNS resolution depending on your specific requirements.




