At times, when safeguarding your computer is paramount, ensuring that your digital fortress remains impervious to threats becomes an essential priority. In this digital age, protecting your personal and sensitive information is of utmost significance, demanding a vigilant stance against potential cyber hazards.
Within the ever-evolving landscape of cybersecurity, the conundrum lies not only in identifying the right security software but also in optimizing its functions to enable a robust defense system, fostering an environment where your personal data can flourish in a secure cocoon. Delving into the intricacies of enhancing your security, this article delves into the lesser-known realms of empowering your Windows operating system with an extra layer of protection.
Today, we explore the realm of fine-tuning a quintessential guardian - the Windows Defender. While the term 'configuration' conjures up images of labyrinthine menus and complex settings, we present a comprehensive guide on manipulating the prowess of your computer's guardian without shedding a single tear of technological distress.
Overview of Windows Defender
Windows Defender is a vital component of the Microsoft operating system, providing robust protection against various forms of malicious software and potentially harmful online threats. In this section, we will explore the fundamental aspects of Windows Defender, delving into its key features, functionalities, and benefits without specifically focusing on the process of configuring it.
Comprehensive Defense: Windows Defender acts as a shield, safeguarding your computer from malware, spyware, viruses, and other harmful software elements that may compromise your system's security. It offers a multi-layered defense mechanism, combining real-time protection, cloud-based scanning, and efficient threat identification algorithms.
Real-Time Protection: Windows Defender continuously monitors your system, actively detecting and blocking any suspicious activities or files that may attempt to infiltrate your computer. It operates silently in the background, providing constant protection without interrupting your workflow.
Automatic Updates: Windows Defender regularly updates its vast database of known threats, ensuring that your computer is well-equipped to combat emerging malware and exploits. These automatic updates help in keeping your system secure against the latest vulnerabilities and attacks.
User-Friendly Interface: Windows Defender offers a user-friendly interface, allowing users to easily navigate and access its various settings, options, and reports. The interface provides clear and concise information about the security status of your computer, making it convenient to monitor and manage potential threats.
Customizable Settings: Users can customize the settings of Windows Defender according to their specific needs and preferences. From scheduled scans to exclusion lists, Windows Defender provides flexibility in configuring its functionalities to optimize performance and ensure compatibility with other software applications.
Safe Browsing: Windows Defender integrates with Microsoft Edge, the default web browser for Windows, offering enhanced protection during online activities. It actively scans websites and downloads for potential threats, providing a safe browsing experience by blocking malicious content before it reaches your system.
In conclusion, Windows Defender embodies the essence of reliable and comprehensive security software, protecting your computer and personal information from a myriad of threats. By understanding the overview of Windows Defender, you can leverage its powerful features and functionalities to safeguard your Windows operating system effectively.
Importance of Configuring Your Computer's Built-In Security
Configuring your computer's built-in security is an essential step in ensuring the safety and security of your system and personal data. By customizing the settings of your system's default security software, you can optimize its protection capabilities and enhance your overall cybersecurity.
Understanding the significance of configuring your computer's native security solution is crucial in today's digital landscape, where cyber threats continue to evolve and become more sophisticated. In this section, we will explore the reasons why customizing the settings of your system's built-in security is indispensable in safeguarding your computer and maintaining a secure online presence.
Firstly, by tailoring the settings of your computer's default security software, you can adapt it to your specific needs and preferences. This customization empowers you to define the level of protection that best suits your usage patterns and digital environment, ensuring a balance between maximum security and user convenience.
Furthermore, configuring your system's built-in security allows you to stay up to date with the latest threat intelligence and security patches. By enabling automatic updates, you ensure that your computer is equipped with the most current security measures to combat new and emerging threats.
In addition, proper configuration of your computer's native security solution provides you with a higher level of control and visibility over the security processes and actions. This increased control allows you to monitor and manage potential security breaches, quarantine suspicious files, and adjust security parameters according to evolving risks.
Lastly, configuring your computer's built-in security is an essential aspect of a layered defense strategy. By complementing your system's default security with additional security tools and practices, you create multiple barriers for potential threats, making it significantly more difficult for cybercriminals to gain unauthorized access to your system or compromise your sensitive information.
In conclusion, understanding the importance of configuring your computer's built-in security is fundamental in maintaining a robust and resilient cybersecurity posture. By customizing the settings of your system's native security solution, you maximize its protection capabilities and ensure the safety of your computer and personal data.
Unlock the Power of Windows Security: A Comprehensive Guide to Accessing Defender Settings
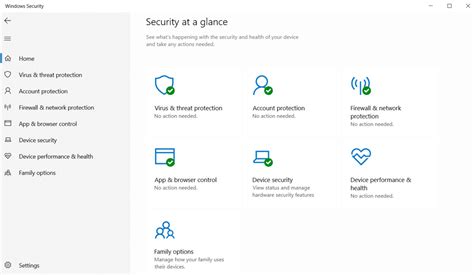
In this step-by-step guide, we will delve into the intricacies of fine-tuning the robust security capabilities in the widely acclaimed operating system from Microsoft. Discover how to effortlessly navigate through the intuitive interface and access the wealth of settings offered by Windows Defender.
Understanding the Core Principles
Before diving into the nitty-gritty details, it is crucial to grasp the fundamental concepts surrounding Windows Defender. Learn how this cutting-edge solution shields your system from potential threats, adapting to ever-evolving digital landscapes. Be confident in your understanding of the essential principles that underpin its functionality.
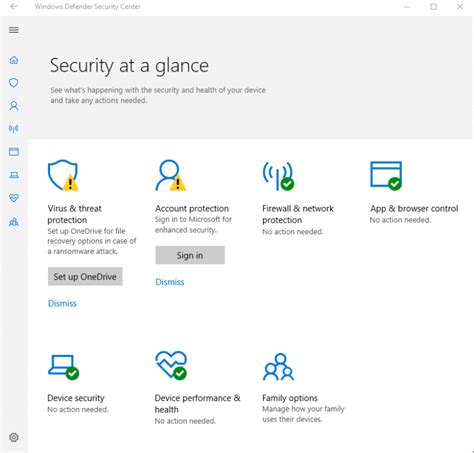
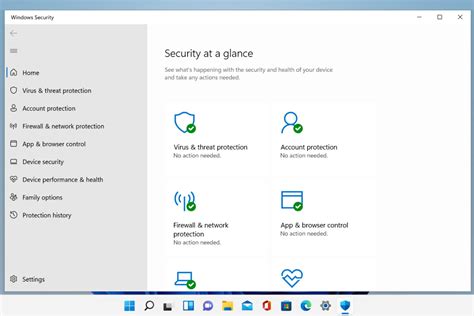
Exploring the Centralized Dashboard
Unleash your ability to customize Windows Defender by accessing the centralized dashboard. Discover the range of powerful features that provide you with a holistic view of your system's security status. Navigate through various sections, each offering a unique set of customizable options to meet your specific requirements.
Configuring Real-time Protection
Improve your defenses with real-time protection settings. Delve into the intricacies of configuring customized scans, blocking malicious files and applications, and maximizing the efficiency of threat detection. Unlock the potential to proactively combat emerging hazards and ensure your system remains secure.
Adding Exclusions for Enhanced Efficiency
Windows Defender allows you to fine-tune its behavior by adding exclusions tailored to your specific needs. Learn how to effectively exclude files, folders, or even entire drives from routine scans, optimizing system performance while maintaining a secure environment. Discover the art of balancing efficiency and security.
Configuring Advanced Settings
Take your control to the next level by exploring the advanced settings of Windows Defender. Learn how to adjust notification preferences, modify scanning options, and configure the firewall to safeguard your system more effectively. Master the art of customization and adapt Defender to match your unique security posture.
Staying Up to Date
Discover the importance of keeping your Windows Defender updated with the latest definitions and enhancements. Learn how to leverage automatic update settings effectively while ensuring your system remains protected against emerging threats. Stay ahead of potential vulnerabilities with ease.
With this comprehensive guide at your disposal, you'll unlock a whole new level of control and security on your Windows device. Follow these step-by-step instructions to access and configure the wide array of settings offered by Windows Defender, ensuring your digital experience remains worry-free.
Customizing real-time protection settings in Windows Defender
When it comes to enhancing the security of your system, Windows Defender offers a variety of customizable options that allow you to tailor its real-time protection settings according to your specific requirements. By tweaking these settings, you can optimize the effectiveness of Windows Defender in detecting and responding to potential threats.
In this section, we will explore the different ways you can customize the real-time protection settings in Windows Defender, without necessarily modifying the core functionality of the program. By understanding and utilizing these options, you can enhance your system's overall security without compromising its performance or usability.
| Setting | Description |
|---|---|
| Cloud-delivered protection | Enable or disable the option to use the power of the cloud to analyze and respond to emerging threats in real-time. |
| Automatic sample submission | Choose whether to allow Windows Defender to automatically submit unknown files to Microsoft for analysis, improving threat detection. |
| Potentially unwanted app blocking | Decide whether Windows Defender should proactively block potentially unwanted applications from being downloaded or executed on your system. |
| Exclusions | Add specific files, folders, or processes to the exclusions list, ensuring they are not scanned by Windows Defender's real-time protection. |
| Enhanced notifications | Enable or disable enhanced notifications to receive detailed alerts about the actions taken by Windows Defender in response to threats. |
| Tamper protection | Activate tamper protection to prevent malicious or unauthorized programs from modifying Windows Defender's settings without your knowledge. |
By customizing these real-time protection settings, you can strike the right balance between security and system performance, ensuring that Windows Defender provides optimal protection against potential threats while minimizing any potential impact on your daily activities.
Customizing Scan Options in Windows Security
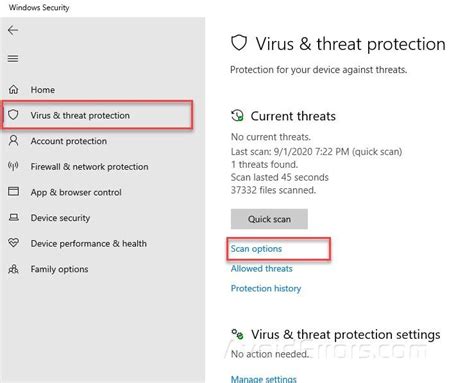
The ability to personalize your scanning preferences is an essential aspect of configuring your security settings within the Windows operating system. By tailoring the scan options in Windows Security, you can ensure a comprehensive analysis of your system while optimizing resource usage. This section delves into the various ways to customize scan options to suit your specific requirements.
Managing exclusions in Windows Defender
Optimizing the security settings of your operating system involves configuring various aspects to meet your specific requirements. One important aspect to consider is managing exclusions in your Windows Defender software. This section will provide insights on how to effectively handle exclusions within the Windows environment, allowing you to tailor your antivirus protection to target specific files, folders, or processes.
By properly managing exclusions, you can enhance the performance of your system as Windows Defender won't waste resources scanning trusted files or folders repeatedly. Additionally, you can minimize false positives, ensuring that legitimate files or applications are not mistakenly flagged as threats by the antivirus software.
- Adding file exclusions: Exclude specific files or file types from being scanned by Windows Defender, such as system backups, health monitoring software, or development tools.
- Excluding folders: Exclude entire folders from being scanned by Windows Defender, which can be useful when dealing with large directories or specific folders that contain known safe files.
- Managing process exclusions: Exclude certain processes from being monitored by Windows Defender, which can be helpful for applications that may conflict with the antivirus software or whose activities are considered safe.
- Setting up exclusion rules: Learn how to configure exclusion rules to automatically handle future file or folder exclusions, ensuring that new files or folders meeting specified criteria are automatically excluded from scans.
It's crucial to strike a balance between having effective antivirus protection and optimizing system performance. By mastering the art of managing exclusions in Windows Defender, you can customize your security settings to align with your specific needs and enhance the overall performance of your Windows operating system.
Exploring Advanced Options in Windows Guardian
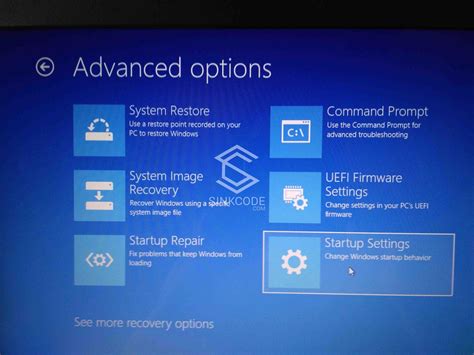
In order to enhance the protection provided by the security software on your system, it is essential to explore the advanced settings available in Windows Guardian. These features allow users to customize and optimize the level of security provided, ensuring a more tailored and robust defense against potential threats. By delving into these advanced options, users can take advantage of a range of powerful functionalities that will significantly enhance the effectiveness of Windows Guardian.
- Fine-tuning Real-time Protection:
- Customizing Scan Options:
- Managing Quarantine and Allowed Items:
- Configuring Exclusions:
- Customizing Notifications and Actions:
The ability to adjust the real-time protection settings is a crucial feature in Windows Guardian. By customizing the actions taken when potential threats are detected, users can strike the right balance between prompt action and minimizing system disruptions. Options such as specifying the level of cloud-based protection and configuring the behavior of the system when a threat is detected can be explored to ensure an optimal real-time protection experience.
Windows Guardian offers various scanning options, allowing users to perform tailored scans based on their preferences and requirements. By utilizing advanced scan settings, users can specify the inclusion or exclusion of specific folders or file types, as well as schedule automatic scans at convenient times. Exploring these options not only provides flexibility but also ensures comprehensive system scans, covering all potential sources of threats.
The Quarantine functionality in Windows Guardian keeps potentially harmful files isolated, preventing them from causing harm to the system. By understanding and utilizing the advanced settings related to Quarantine, users can manage and review quarantined items effectively. Additionally, the ability to manage and modify the list of allowed items allows users to whitelist trusted files and applications, ensuring they are not mistakenly identified as threats in future scans.
Exclusions are a useful feature that enables users to specify files, folders, or processes that Windows Guardian should omit during scans. By carefully configuring exclusions, users can ensure the security software focuses on potential threats without unnecessary interruptions caused by non-malicious files or applications. This advanced setting provides the flexibility and control needed to optimize security scans and maximize system performance.
Windows Guardian offers various notification and action settings that can be customized to suit individual preferences. By exploring these advanced options, users can determine the frequency and level of detail provided in notifications, as well as configure automated responses to specific threat detections. This level of customization ensures that users stay informed about the security status of their system while maintaining a seamless and unobtrusive user experience.
Tips for optimizing Windows Defender performance
Enhancing the efficiency and effectiveness of your system's built-in security solution can lead to a smoother overall experience. By following these tips, you can ensure that Windows Defender operates at its optimal level while safeguarding your device without compromising performance.
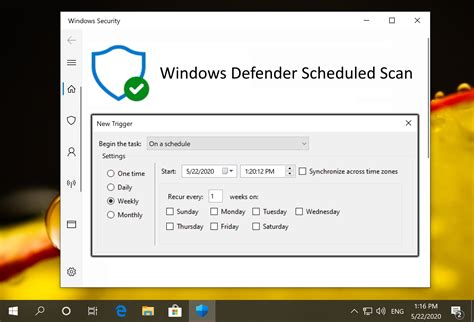
- Customize your scanning preferences: Adjusting the scanning schedule and configuring specific folders or file types to be excluded from scans can help reduce unnecessary strain on system resources.
- Keep your definitions up to date: Regularly updating your virus and threat definitions ensures that Windows Defender can recognize and protect against the latest threats effectively.
- Enable the Cloud-delivered protection feature: This feature allows Windows Defender to gather information from the cloud, providing real-time protection and enhancing detection capabilities.
- Utilize the Windows Security app: The Windows Security app provides a centralized location to manage and monitor Windows Defender settings and activity, allowing for simplified troubleshooting and increased efficiency.
- Consider Windows Defender exclusions: If certain applications or files are incorrectly flagged as potential threats by Windows Defender, you can add them to the exclusions list to prevent unnecessary warnings or removals.
- Opt for periodic full scans: Performing regular full system scans can help identify and remove hidden threats that may be missed during quick or custom scans.
By implementing these optimization techniques for Windows Defender, you can strike a balance between robust security and optimal system performance.
Make Windows 11 Security Better
Make Windows 11 Security Better by Britec09 9,905 views 2 months ago 12 minutes, 8 seconds
FAQ
What is Windows Defender?
Windows Defender is an anti-malware software that comes pre-installed on Windows operating systems. It provides real-time protection against viruses, spyware, and other types of malicious software.
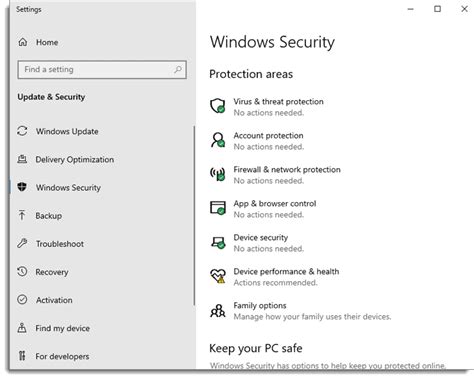
How can I access Windows Defender in Windows?
You can access Windows Defender by clicking on the Start menu, selecting Settings, and then clicking on Updates & Security. From there, you can click on Windows Security and access Windows Defender.
Can I customize the settings of Windows Defender?
Yes, you can customize the settings of Windows Defender. You can adjust the level of protection, schedule scans, exclude certain files or folders from being scanned, and more.
Is it necessary to have Windows Defender if I already have an antivirus software installed?
While having an antivirus software is important, having Windows Defender in addition to it can provide an extra layer of protection. Windows Defender is designed to work seamlessly with other antivirus software to enhance overall security.