As technology advances and our dependency on the internet grows, ensuring the security of our online activities has become more important than ever. While browsing the web or accessing sensitive information, it is crucial to protect your data from potential threats and unauthorized access. One effective way to safeguard your online connection is by employing a Virtual Private Network (VPN).
A VPN, also known as a virtual private network, creates a secure and encrypted connection between your device and the internet. By routing your internet traffic through an encrypted tunnel, a VPN protects your data from being intercepted or accessed by third parties. Moreover, it assigns a different IP address to your device, making it appear as if you are accessing the internet from a different location.
Setting up a VPN on your Linux device allows you to take advantage of these benefits while maintaining your privacy and security. Whether you are using Linux on your personal computer, smartphone, or tablet, implementing a VPN further enhances your online security posture. In this article, we will guide you through the process of configuring a VPN on your Linux system, providing you with the tools and knowledge to establish a protected connection within a few simple steps.
Understanding the Fundamentals of Virtual Private Networks and Their Significance for Linux Users
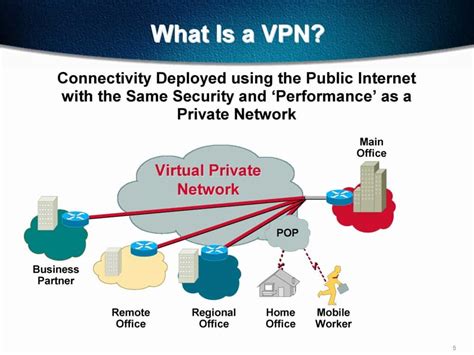
In today's interconnected world, where online privacy and security are paramount, virtual private networks (VPNs) have become essential tools for individuals using Linux operating systems. VPNs serve as a safeguard, protecting sensitive data, enhancing anonymity, and enabling secure connections over the internet. By grasping the basics of VPN technology and its importance for Linux users, individuals can ensure a safer and more private online experience.
Choosing the Optimal VPN Protocol for Your Linux-Based Environment
When it comes to securing your online activities and enhancing your privacy on a Linux-based operating system, selecting the most appropriate VPN protocol plays a crucial role. A VPN protocol acts as the underlying technology that establishes a secure connection between your device and the VPN server, ensuring encrypted communication and safeguarding your data from prying eyes. With a plethora of VPN protocols available, it is essential to make an informed decision based on your specific needs and the features offered by each protocol.
| Protocol | Advantages | Disadvantages |
|---|---|---|
| OpenVPN | OpenVPN, known for its open-source nature, combines strong security with optimal performance. It is widely supported and offers excellent configurability, making it an ideal choice for advanced users. | Requires the installation of additional software and can be more complex to set up compared to other protocols. |
| IPSec/IKEv2 | IPSec, in combination with IKEv2, provides robust security and seamless operation. Its ability to quickly reconnect to the VPN server after a network interruption makes it suitable for users who frequently switch between networks. | May not be as easily configurable as OpenVPN and might require additional third-party software. |
| WireGuard | WireGuard, gaining popularity due to its simplicity and efficiency, offers faster speeds and lower latency. It is designed to be lightweight, making it an excellent choice for resource-constrained devices. | Being a relatively new protocol, it may not be as widely supported as other options and may have limited documentation available. |
Each VPN protocol has its unique advantages and disadvantages, and the right choice depends on factors such as the desired level of security, ease of configuration, and compatibility with your Linux-based setup. It is recommended to thoroughly research and experiment with different protocols to determine which one aligns best with your specific requirements.
Comparing various VPN protocols and selecting the optimal one according to your requirements

When it comes to securing your online privacy and establishing a secure connection over the internet, using a Virtual Private Network (VPN) is highly recommended. However, there are numerous VPN protocols available, each with its own set of features, advantages, and disadvantages. In this section, we will explore the different VPN protocols and provide insights on selecting the most suitable one to meet your specific needs.
Step-by-step guide to installing a secure network client on an open-source operating system
In this section, we will walk you through the process of setting up a virtual private network (VPN) client on a widely used open-source operating system. By following these step-by-step instructions, you will be able to establish a secure connection to a remote network, protecting your data and ensuring anonymity while browsing the internet on your Linux system.
Step 1: Preparing for installation
Before installing the VPN client on your Linux system, it is essential to ensure that you have administrative privileges and a stable internet connection. Additionally, make sure to have the necessary credentials provided by your VPN service provider, including the server address, username, and password.
Step 2: Choosing the right VPN client
There are several VPN client options available for Linux systems, each with its own set of features and compatibility. Research and select the client that best suits your requirements and download the installation package.
Step 3: Installing the VPN client
Once you have downloaded the VPN client installation package, navigate to the directory where it is saved and open a terminal window. Execute the installation command provided by the client's documentation, ensuring that you follow any specified prerequisites or dependencies.
Step 4: Configuring the VPN client
After the installation is complete, you will need to configure the VPN client by entering the server address, username, and password provided by your VPN service provider. Follow the instructions provided by the client's documentation to set up these connection details correctly.
Step 5: Establishing the VPN connection
Once you have successfully configured the VPN client, you can establish a connection to the VPN server through the client's interface. This will initiate the secure tunnel and route all your network traffic through the VPN, ensuring privacy and security.
Step 6: Verifying the VPN connection
To ensure that your VPN connection is active and functioning correctly, you can verify your new IP address, check for any DNS leaks, and test your connection speed. This step will help you confirm that your Linux system is securely connected to the VPN server.
Step 7: Disconnecting from the VPN
When you no longer need the VPN connection, it is essential to disconnect from the VPN server to restore your regular internet access. This action can typically be done through the VPN client's interface with the click of a button, saving system resources and returning your network configuration to its default state.
By following these step-by-step instructions, you can successfully install a VPN client on your Linux system, ensuring privacy, security, and anonymity while browsing the internet. Remember to refer to the VPN client's documentation for any specific installation or configuration details that may vary from these general guidelines.
Installation Process for Various VPN Clients on Linux
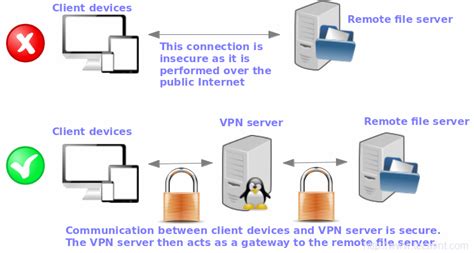
In this section, we will guide you through the step-by-step process of setting up different VPN clients on your Linux system. We will explore the installation procedures and configuration steps required to establish secure connections and protect your online privacy. Throughout this walkthrough, we will cover a range of client options available for Linux, addressing their individual features, advantages, and installation requirements.
OpenVPN: One of the most widely used VPN clients for Linux, OpenVPN provides a robust and versatile solution for establishing secure connections. We will delve into the installation instructions for OpenVPN, covering its flexible configuration options and integration with various Linux distributions.
WireGuard: Growing in popularity due to its simplicity and efficiency, WireGuard offers a modern approach to VPN connections on Linux. We will walk you through the installation process of WireGuard, discussing its unique encryption protocol, ease of use, and compatibility with different Linux kernels.
StrongSwan: Suitable for advanced users and enterprise environments, StrongSwan is a powerful VPN client that supports various protocols for secure communications. We will provide detailed instructions on installing and configuring StrongSwan, including its advanced features, such as certificate-based authentication and network bridging.
IPsec/L2TP: For those seeking compatibility with legacy systems, IPsec/L2TP remains a viable option. We will guide you through the installation procedure of setting up IPsec/L2TP VPN connections on your Linux system, exploring its reliability, cross-platform capabilities, and network traversal enhancements.
Note that the installation process for each VPN client may differ slightly depending on your Linux distribution. We will aim to provide general guidelines that can be adapted to various system setups, but it's always recommended to refer to the specific documentation and guides provided by the respective client developers for detailed instructions.
Configuring Network Privacy Settings on Your Open-Source Operating Environment
In the realm of digital security, it is paramount to safeguard your online activities, protecting your privacy and data from potential threats and surveillance. As an open-source aficionado, you have chosen to embrace the Linux ecosystem, harnessing its powerful features and flexibility. To further enhance your digital defenses, it is crucial to configure your network privacy settings, utilizing a Virtual Private Network (VPN) solution.
A VPN encrypts your internet traffic, providing a secure and private pathway, shielding your sensitive information from prying eyes. With Linux's versatility, you have a plethora of options to configure your VPN settings, tailoring them to your specific requirements, while ensuring optimal performance and anonymity.
Here's a step-by-step guide to configuring your VPN settings on your Linux system:
- Identify and select a reputable VPN service provider: It is imperative to choose a trusted VPN service that aligns with your privacy needs. Research various providers, comparing their features, jurisdiction, logging policies, and encryption standards to make an informed decision.
- Install the necessary VPN software: Depending on the VPN provider you choose, follow their instructions for installing the appropriate software on your Linux distribution. This may involve using package managers such as apt, yum, or dnf, or downloading the software directly from the provider's website.
- Configure VPN settings: Once the software is installed, launch the VPN client and navigate to the settings menu. Here, you will find options to input your VPN credentials, including the server address, protocol, authentication type, and port. Consult your VPN provider's documentation for the specific details required for configuration.
- Choose your VPN protocol: Linux supports various VPN protocols, such as OpenVPN, WireGuard, and IKEv2. Depending on your security and speed priorities, choose the protocol that best suits your needs. Consider factors like encryption strength, stability, and compatibility.
- Select your desired VPN server location: Most VPN providers offer a wide selection of server locations globally. Choose a server location that aligns with your browsing needs, whether you seek access to geo-restricted content or require enhanced privacy in a specific jurisdiction.
- Configure advanced VPN settings (optional): For those with more advanced requirements, explore the additional options available in the VPN client settings. These may include features like split tunneling, kill switch, or DNS leak protection. Consult your VPN provider's documentation to understand the purpose and functionality of each configuration option.
- Connect to the VPN server: Once you have completed the configuration, click the connect button in the VPN client to establish a secure connection to the chosen server. Verify that your IP address has changed, indicating a successful connection.
- Test your VPN connection: To ensure your VPN is functioning correctly, perform various online tests to confirm your privacy and security levels. These may include DNS leak tests, IP address checks, or speed tests to assess the performance impact of the VPN connection.
By following these steps, you can successfully configure your VPN settings on your Linux system, enhancing your privacy and security while navigating the vast digital landscape.
Customizing and Optimizing VPN Settings for Enhanced Security and Performance

Enhancing the security and performance of your VPN on a Linux system involves customizing and optimizing various settings. By making these adjustments, you can ensure that your VPN connection is secure and efficient, providing you with a seamless browsing experience while protecting your data.
- Tweak encryption protocols: One way to enhance VPN security is by adjusting the encryption protocols used. Consider using stronger encryption algorithms such as AES-256, which provide a higher level of security compared to weaker options like DES or RC4.
- Optimize VPN server selection: Choosing the right VPN server location can significantly impact performance. Selecting a server that is geographically closer to your physical location can reduce latency and improve overall connection speed.
- Enable secure DNS: Enabling secure DNS resolution can add an extra layer of security to your VPN connection. Configure your system to use a trusted DNS resolver or consider using DNS-over-HTTPS (DoH) or DNS-over-TLS (DoT) protocols for secure DNS resolution.
- Disable IPv6: In some cases, IPv6 traffic might bypass the VPN connection, potentially exposing your IP address and compromising your privacy. Disable IPv6 on your Linux system to ensure that all internet traffic goes through the VPN tunnel.
- Implement kill switch: A kill switch is a crucial feature that cuts off internet access if the VPN connection drops unexpectedly. By enabling a kill switch, you can prevent any data leakage and ensure that your online activities remain private.
- Regularly update VPN software: Keep your VPN software up to date to take advantage of the latest security patches and improvements. Regular updates help address any vulnerabilities or issues that could potentially compromise the security and performance of your VPN connection.
By customizing and optimizing various VPN settings on your Linux system, you can create a more secure and efficient VPN experience. These adjustments, such as tweaking encryption protocols, optimizing server selection, enabling secure DNS resolution, disabling IPv6, implementing a kill switch, and ensuring regular software updates, play a vital role in enhancing both the security and performance of your VPN connection.
Troubleshooting common VPN issues on Linux
In this section, we will explore various common challenges that users may encounter while configuring and using a virtual private network (VPN) on a Linux system. By understanding and troubleshooting these issues, you can ensure a smoother and more reliable VPN connection.
1. Connectivity problems: One common issue users face is difficulty establishing a connection to the VPN server. This could be due to factors such as incorrect network settings, firewall restrictions, or compatibility issues with VPN protocols. Troubleshooting connectivity problems involves checking network configurations, ensuring appropriate firewall rules, and verifying the VPN protocol compatibility with your Linux system.
2. Slow connection speeds: Poor performance or slow connection speeds are other common problems that may arise while using a VPN on Linux. This could be attributed to factors like a high server load, distance from the VPN server, or bandwidth limitations imposed by your internet service provider. Troubleshooting slow connection speeds involves testing different VPN servers, optimizing network settings, or considering an upgrade to a higher-speed internet connection.
3. DNS leaks: DNS leaks refer to instances where DNS requests bypass the VPN tunnel, potentially exposing your network activities to prying eyes. Linux users may encounter DNS leak issues due to misconfigurations or vulnerabilities in the VPN client or operating system. Troubleshooting DNS leaks involves checking DNS settings, configuring the VPN client to prevent DNS leaks, or utilizing third-party tools to test and validate DNS privacy.
4. Authentication errors: Authentication errors are another common hurdle that users may encounter when setting up a VPN on Linux. This could be due to incorrect login credentials, expired certificates, or mismatched authentication protocols between the client and server. Troubleshooting authentication errors involves verifying login information, updating certificates if necessary, and ensuring consistent authentication configuration across the VPN infrastructure.
5. Software conflicts: In some cases, conflicts between the VPN software and other applications installed on your Linux system can cause issues. These conflicts may lead to connectivity problems, system crashes, or performance degradation. Troubleshooting software conflicts includes identifying conflicting applications, updating or reinstalling the VPN software, or adjusting system settings to mitigate compatibility issues.
By addressing these common VPN issues on Linux, you can enhance your overall VPN experience and establish a secure and reliable connection for your online activities.
[MOVIES] [/MOVIES] [/MOVIES_ENABLED]FAQ
What is a VPN and why should I set it up on my Linux system?
A VPN (Virtual Private Network) is a secure network connection that allows you to access the internet privately and securely. Setting up a VPN on your Linux system can provide you with enhanced security, privacy, and the ability to bypass geo-restrictions.
Is it difficult to set up a VPN on a Linux system?
No, setting up a VPN on a Linux system is not difficult. In fact, Linux has built-in support for various VPN protocols, making the setup process relatively straightforward. By following a few steps, you can have a VPN up and running on your Linux system in no time.
What VPN protocols are supported on Linux?
Linux supports various VPN protocols such as OpenVPN, IKEv2, L2TP/IPsec, and PPTP. Each protocol has its own advantages and disadvantages, so you can choose the one that best suits your needs.
Are there any VPN clients specifically designed for Linux?
Yes, there are several VPN clients specifically designed for Linux systems. Some popular options include OpenVPN, NetworkManager, and strongSwan. These clients provide a user-friendly interface and make it easier to set up and manage VPN connections on Linux.
Can I use a free VPN service on my Linux system?
Yes, there are free VPN services available for Linux systems. However, it's important to note that free VPNs often have limitations such as limited data usage, slower speeds, and a smaller number of available servers. If you require higher speeds, unlimited data, and a wider range of server locations, you may need to consider a paid VPN service.
What is a VPN?
A VPN (Virtual Private Network) is a network technology that provides a secure and encrypted connection over a public network, such as the internet. It allows users to access private networks remotely and securely, protecting their data and online activities from prying eyes.




