In today's interconnected world, where data security is paramount, having a robust and efficient user management system is crucial for any organization. The ability to authenticate and manage users effectively not only ensures the privacy and integrity of the system but also enhances the overall productivity and user experience. This article explores the process of setting up and configuring the highly versatile and powerful sssd service on your Linux environment.
Integrating your Identity Provider seamlessly with Linux
The sssd service, short for System Security Services Daemon, acts as a bridge between your Linux environment and various identity providers such as Active Directory, LDAP, and Kerberos. This versatile tool allows you to streamline the authentication and user management process, offering enhanced security and convenience for your users. With sssd, you can centralize user information, control access to resources, and ensure the scalability and flexibility of your Linux systems.
Simplify User Authentication with Single Sign-On
One of the key features of sssd is its ability to integrate with Single Sign-On (SSO) systems, providing users with a seamless and unified authentication experience. By leveraging the power of SSO, users can log in once and gain access to multiple services and applications without the need for repetitive authentication. This not only improves user experience but also minimizes the risk of password fatigue and strengthens overall security.
Effortlessly Manage User Identities with Centralized Control
Gone are the days of manually managing individual user accounts and permissions on each Linux system. With sssd, you can centralize user identity and access control, simplifying the administration process and saving valuable time and effort. Whether you have a small network or a large-scale enterprise environment, sssd provides a comprehensive framework for managing user identities and seamlessly integrating them into your Linux infrastructure. By consolidating user information, you can ensure consistency, streamline operations, and efficiently enforce organizational policies.
Understanding the Functionality of sssd and Its Role in Linux System Authentication

One of the crucial components in a Linux system's authentication process is a tool called sssd, which plays a vital role in user management and authentication. By comprehending the inner workings of sssd, administrators can effectively control user access, ensure system security, and simplify their administration tasks.
sssd, which stands for System Security Services Daemon, acts as a bridge between user identity and various authentication sources such as local user accounts, LDAP directories, and Active Directory domains. It provides a unified interface for systems to authenticate and authorize users against multiple sources seamlessly.
A key advantage of utilizing sssd is the consolidation of user management across various authentication sources. With sssd, administrators can centralize user accounts and passwords, allowing for easier user management and reducing the need for separate credentials across different systems. This centralization also enhances security by enabling consistent password policies and access controls.
Furthermore, sssd incorporates caching mechanisms, which improve system performance and reliability. By caching user credentials locally, sssd reduces the number of remote authentication requests, enhancing response times and minimizing network dependencies. This caching feature is particularly useful in scenarios where the connection to an authentication source may be intermittent or slow.
sssd also offers a range of configuration options, which permit fine-tuning of authentication methods, user mapping, and integration with various services. Administrators can define rules and settings to adapt sssd to the specific requirements of their environment, ensuring seamless integration with existing infrastructure.
In summary, sssd plays a fundamental role in Linux system authentication by providing a unified interface for user management and authentication against multiple sources. Its consolidation capabilities, caching mechanisms, and customizable configuration options make it a powerful tool for simplifying administration tasks, enhancing security, and improving system performance.
Step 1: Installing sssd on a Linux Distribution
One of the initial steps in setting up the sssd service on a Linux distribution is to install it on the system. This involves downloading and installing the necessary packages to enable sssd functionality.
Here are the general steps to install sssd on your Linux system:
- Update the package manager to ensure you have the latest available software packages.
- Use the package manager to search for and install the sssd package.
- Verify the successful installation of sssd by checking its version and related packages.
Updating the package manager is an important step to ensure that you have access to the latest versions of software packages. By searching for and installing the sssd package using the package manager, you can easily manage dependencies and ensure that the installation process goes smoothly.
Once sssd is installed, it is crucial to verify its successful installation by checking the version and related packages. This will help confirm that sssd is properly installed and ready to be configured for the desired authentication and identity management functionality.
Using package manager to install sssd
Introduction: In this section, we will explore the process of installing sssd using the package manager on a Linux-based operating system. By leveraging the package manager, users can easily obtain and install sssd without the need for manual configuration, ensuring a streamlined and efficient setup.
Identifying the appropriate package manager: Depending on the Linux distribution being used, there are various package managers available, such as apt, yum, zypper, or dnf. Before proceeding with the installation, it is crucial to determine the specific package manager utilized by your system.
Updating the package lists: Prior to installing any software, it is recommended to update the package lists to ensure that you will be obtaining the latest version of sssd. This can be achieved by executing the appropriate command, such as "apt update" or "yum update." This step ensures a more secure and up-to-date installation.
Installing sssd: Once the package lists are updated, the next step involves using the package manager to install sssd. This can be accomplished by running the command that corresponds to your package manager, such as "apt install sssd" or "yum install sssd." The package manager will then handle the retrieval and installation of all necessary dependencies.
Verifying the installation: After the installation process is complete, it is crucial to verify that sssd has been successfully installed. This can be done by checking the version of sssd, as well as the availability of its associated tools and configuration files. Such verification ensures that the installation was completed accurately.
Conclusion: Using the package manager to install sssd on a Linux system enables users to easily obtain and deploy sssd without the need for manual intervention. By following the steps outlined in this section, users can ensure a swift and efficient installation process, bringing them one step closer to successfully utilizing the features and benefits of sssd.
Step 2: Setting up sssd to Enhance User Authentication and Authorization
Once you have completed the initial setup of your Linux system, it is time to delve into the process of configuring sssd. This step is crucial in order to enhance the overall user authentication and authorization capabilities of your system. By configuring sssd, you will be able to streamline and centralize user management, enabling seamless integration with various authentication providers.
- Configure sssd: Begin by accessing the sssd configuration file, typically located in the /etc/sssd/ directory. Here, you can customize the various settings and options to align with your specific requirements. This includes specifying which authentication providers to utilize, such as LDAP or Active Directory, as well as defining the desired user access controls.
- Integrate with PAM: The next step is to integrate sssd with the Pluggable Authentication Modules (PAM) framework. This allows sssd to seamlessly interact with PAM and handle user authentication requests. By modifying the appropriate PAM configuration files, you can specify the desired behavior for different authentication stages, such as password validation and session management.
- Customize Identity Mapping: One of the key advantages of sssd is its ability to facilitate identity mapping, which ensures consistent user identification across different authentication providers. By configuring identity mapping, you can unify user accounts from various sources and map them to a single, coherent identity. This step involves defining the appropriate mapping rules and attributes, such as UID and GID mappings.
- Enable Cached Credentials: To enhance performance and ensure uninterrupted access to user accounts, it is recommended to enable cached credentials in sssd. By enabling caching, sssd can store user credentials locally, allowing for offline authentication and reducing the dependency on external authentication providers. This feature can be particularly useful in scenarios where network connectivity is limited or unreliable.
By following these steps and effectively configuring sssd, you can greatly enhance the user authentication and authorization capabilities of your Linux system. Additionally, sssd provides a seamless and unified approach to user management, simplifying the overall administration and maintenance of user accounts. Stay tuned for the next steps to complete the configuration process.
Understanding and Editing the sssd Configuration File
In this section, we will explore the intricacies of the configuration file used by sssd, a powerful tool that facilitates centralized user authentication and identity management on Linux-based systems. By gaining a deeper understanding of this configuration file, you will be able to customize and fine-tune the behavior of sssd to suit the specific needs of your environment.
The sssd configuration file acts as a roadmap for the sssd daemon, guiding it in its interactions with identity providers, such as Active Directory or LDAP servers, as well as defining the desired caching and authentication behavior. By carefully editing this configuration file, you can control how sssd interacts with these providers, specify the desired authentication methods, and optimize performance and security settings.
The configuration file is written using a simple, yet powerful syntax that allows you to define a hierarchy of sections, each containing specific options and values. Understanding the different sections and their respective options will enable you to tailor the behavior of sssd to meet your specific requirements.
Key concepts that you should grasp when editing the sssd configuration file include:
| Section | Description |
| [sssd] | The global section that contains general options applicable to the entire configuration file. |
| [domain] | Defines the configuration options for a specific domain or provider, such as an Active Directory or LDAP server. |
| [nss] | Specifies the options related to user and group name resolution. |
| [pam] | Controls the behavior of sssd when interacting with the Pluggable Authentication Modules (PAM). |
| [sudo] | Enables integration with the sudo command, allowing you to define rules and access controls for privileged user actions. |
By understanding the purpose and possible options within each section of the sssd configuration file, you will gain the ability to fine-tune the behavior of sssd based on your specific needs. This will not only enhance the performance and security of your Linux-based systems but also allow for seamless integration with your chosen identity providers.
Step 3: Setting up sssd to enable LDAP authentication
In this step, we will explore the configuration process of sssd to enable LDAP authentication on your Linux system. The integration of sssd with LDAP allows users to authenticate their credentials against the LDAP server, enhancing access control and security. This section will guide you through the necessary steps to configure and customize sssd for LDAP authentication.
To begin, we will discuss the key configuration files involved in setting up sssd for LDAP authentication. These files include /etc/sssd/sssd.conf for sssd configuration and /etc/nsswitch.conf for name service switch configuration. It is important to understand the structure and syntax of these files before proceeding with the configuration process.
Next, we will provide step-by-step instructions on how to modify the sssd.conf file to enable LDAP authentication. This involves specifying the LDAP server details, configuring the authentication domain, and defining the search base and filters for user and group authentication. Additionally, we will explain how to enable encryption for secure communication between the sssd client and the LDAP server.
After configuring the sssd.conf file, we need to update the nsswitch.conf file to prioritize sssd for user and group lookup. By setting the proper order in the nsswitch.conf file, we ensure that sssd is consulted first for user and group information, before falling back to other sources like local files or other network services.
Finally, we will cover some common troubleshooting techniques to help you debug and resolve any issues that may arise during the configuration process. These techniques include checking logs, verifying network connectivity, and using command-line tools to test the LDAP authentication. By following these troubleshooting steps, you can ensure a smooth integration of sssd with LDAP authentication on your Linux system.
Configuring sssd for LDAP Authentication
In this section, we will explore the steps involved in setting up the System Security Services Daemon (sssd) to enable authentication against an LDAP server. By implementing this configuration, you can enhance the security of your Linux environment and avoid the need for separate credentials for each user.
To begin, we must ensure that the sssd package is installed on your Linux system. This package provides the necessary components to connect to an LDAP server and authenticate users. If you haven't already installed it, you can do so by using your system's package manager.
Once the sssd package is installed, the next step is to configure the sssd daemon to connect to your LDAP server. This involves providing the necessary information such as the LDAP server's address, port, and credentials for accessing the LDAP directory. You can specify these settings in the sssd configuration file, which is typically located at "/etc/sssd/sssd.conf".
In addition to the basic server connection settings, you also need to define the LDAP search base, which represents the starting point for searching for user and group information in the LDAP directory. This information is crucial for the sssd daemon to successfully locate and authenticate users.
Furthermore, it is important to define the mapping rules that determine how the LDAP attributes should be mapped to the corresponding sssd attributes. These mappings ensure that the user and group information retrieved from the LDAP directory can be properly utilized by the sssd daemon.
Once the sssd configuration is complete, the next step is to start the sssd service and enable it to run at system startup. This can be achieved by using the systemctl command, which is a common system management utility on modern Linux distributions.
After configuring and starting the sssd service, you can then test the LDAP authentication by attempting to log in with an LDAP user account. If the configuration is correct, the sssd daemon will authenticate the user against the LDAP server and grant access to the Linux system.
In conclusion, setting up sssd to authenticate against an LDAP server is a crucial step in enhancing the security and efficiency of your Linux environment. By following the steps outlined in this section, you can ensure seamless integration between your Linux system and an LDAP directory for user authentication.
Step 4: Setting up sssd for authentication with Active Directory
In this section, we will explore the process of configuring the sssd service on your Linux system to enable authentication with Active Directory. By integrating sssd with Active Directory, you can provide seamless access to resources for users within your organization.
Before diving into the configuration steps, it's important to understand that sssd, or System Security Services Daemon, is a software suite that enables Linux systems to authenticate against remote directories, such as Active Directory. By using sssd, you can centralize user management and authentication, simplifying the administration process.
The first step in configuring sssd for Active Directory authentication is to install the necessary packages. You will need to install the sssd package, as well as the necessary dependencies, such as krb5-workstation for Kerberos authentication. This can be done through your Linux distribution's package manager.
| Component | Description |
|---|---|
| sssd | The main package that provides the System Security Services Daemon. |
| krb5-workstation | A package that provides the necessary tools for Kerberos authentication. |
Once the packages are installed, you will need to configure the sssd service to connect to Active Directory. This involves editing the sssd configuration file, typically located at '/etc/sssd/sssd.conf'. You will need to specify the domain information, such as the domain name and server address, as well as any additional required settings.
After configuring sssd, you will need to start and enable the sssd service. This can be done using your distribution's init system, such as systemd or init.d.
Once the sssd service is running, you can test the Active Directory authentication by attempting to log in with an AD user account on the Linux system. If everything is configured correctly, the system should authenticate the user and provide access to the resources associated with their AD account.
In conclusion, setting up sssd for Active Directory authentication on your Linux system involves installing the necessary packages, configuring the sssd service, and testing the authentication process. By integrating sssd with Active Directory, you can streamline user management and enhance security within your organization.
Integration of sssd with Active Directory for authentication
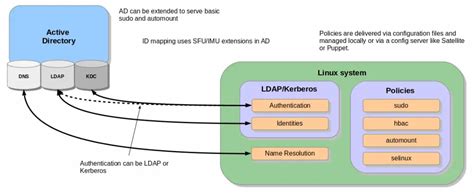
In this section, we will explore the seamless integration of sssd with Active Directory for authentication purposes on your Linux system. By leveraging the power of sssd and the centralized user management of Active Directory, you can enhance the security and efficiency of your authentication process.
One of the key advantages of integrating sssd with Active Directory is the ability to authenticate users against their Active Directory credentials without having to create separate user accounts on the Linux system. This eliminates the need for duplicate user management and ensures that users can seamlessly log in to the Linux system using their existing Active Directory credentials.
- Configuration: The first step in integrating sssd with Active Directory is to configure sssd to establish a connection with the Active Directory server. This involves specifying the domain name, server address, and authentication protocol to be used. The configuration file for sssd allows you to define these settings in a structured manner.
- Secure authentication: The integration of sssd with Active Directory ensures secure authentication by leveraging Kerberos, a network authentication protocol. When a user attempts to log in, sssd interacts with the Active Directory server and the Kerberos infrastructure to verify the user's credentials and grant access to the Linux system.
- User mapping: Mapping Active Directory users to their corresponding Linux system accounts is a crucial aspect of the integration process. Sssd provides various methods for user mapping, including user attributes, group membership, or direct mapping. This mapping allows Linux system resources and permissions to be managed based on Active Directory user accounts.
- Access control: With sssd integrated with Active Directory, you can enforce access control policies based on Active Directory groups and attributes. This provides a centralized approach to managing user access to various resources on the Linux system, enhancing security and simplifying administration tasks.
- Single sign-on: The integration of sssd with Active Directory enables single sign-on functionality, allowing users to authenticate once and access multiple resources seamlessly. This eliminates the need for users to provide their credentials repeatedly, enhancing user experience and productivity.
By following the steps outlined in this section, you can successfully integrate sssd with Active Directory for authentication on your Linux system. This integration not only simplifies user management but also enhances security and provides a seamless experience for your users.
Step 5: Enabling caching in sssd
In this section, we will explore the process of enabling the caching feature in the sssd service on your Linux machine. By enabling caching, you can enhance the performance and availability of user authentication and authorization, as well as improve the overall user experience within your system.
Caching is the process of storing frequently accessed data in a local cache for faster retrieval. This can be particularly useful in environments with a high volume of user authentication requests, as it reduces the need to constantly reach out to the remote identity provider for user information.
Enabling caching within sssd involves configuring the appropriate parameters in the sssd configuration file. By specifying the cache credentials, timeout values, and the cache file location, you can tailor the caching behavior to meet your specific requirements.
Cache credentials refer to the storage of user credentials in the cache. By caching user credentials, subsequent authentication requests can be processed without the need for revalidation, resulting in faster authentication times.
Timeout values determine how long the cached information remains valid. By configuring appropriate timeout values, you can balance security and performance considerations based on the specific needs of your system.
The cache file location specifies the path where the caching data is stored. It is essential to choose a secure location to ensure the integrity of the cached data.
By following the steps outlined in this section, you will be able to enable caching in the sssd service, resulting in improved performance and user experience within your Linux system.
Linux authentication on Microsoft Active Directory using sssd
Linux authentication on Microsoft Active Directory using sssd by Roel Van de Paar 298 views 3 years ago 2 minutes, 12 seconds
FAQ
What is sssd and why is it important to configure it on a Linux system?
SSSD stands for System Security Services Daemon. It is an open-source service that provides a set of daemons to manage and authenticate user accounts on Linux systems. It is important to configure sssd on a Linux system to facilitate centralized authentication, allow users to log in using various identity providers, and enhance system security and performance.
What are the prerequisites for configuring sssd on a Linux system?
The prerequisites for configuring sssd on a Linux system include installing the sssd package, enabling the required authentication providers (such as LDAP, Kerberos, or Active Directory), configuring the system's DNS resolution to correctly resolve authentication servers, and ensuring proper connectivity to the authentication server.
How can I configure sssd to authenticate users against an LDAP server?
To configure sssd for LDAP authentication, you need to modify the sssd.conf file. Specify the LDAP server's address, port, and search base in the configuration file. Additionally, you will need to provide the LDAP bind distinguished name (DN) and password to allow sssd to bind to the LDAP server. Once the configuration is applied and sssd is restarted, users should be able to authenticate against the LDAP server.
Is it possible to configure sssd to authenticate users using Active Directory?
Yes, it is possible to configure sssd to authenticate users using Active Directory. In the sssd.conf file, you need to specify the Active Directory server's address, domain name, and the user and group base DN. Additionally, you will need to provide the user account and password that has permission to join the Linux system to the Active Directory domain. After configuring sssd and restarting it, users will be able to authenticate against the Active Directory server.
How can I troubleshoot common issues when configuring sssd on a Linux system?
If you encounter issues when configuring sssd, there are several steps you can take to troubleshoot. Firstly, check the sssd logs for any error messages or warnings that could indicate the problem. Ensure that the authentication server is accessible and the necessary ports are open. Verify the correctness of the sssd.conf file and any related configuration files. Also, make sure that the Linux system's DNS resolution is correctly configured to resolve the authentication server's address. If needed, consult the documentation or seek assistance from the sssd community or forums to resolve any specific issues.




