Are you tired of relying on traditional password-based authentication for accessing your Linux server remotely? In an era where data security is of paramount importance, it is crucial to explore advanced methods for safeguarding your sensitive information.
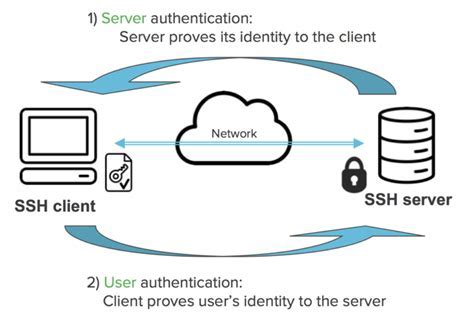
In this tutorial, we will delve into the world of Secure Shell (SSH) and its ability to establish secure connections between different devices over an unsecured network. By utilizing cryptographic techniques, SSH ensures that your data remains confidential and protected from unauthorized access. Moreover, with SSH, you can bid farewell to the hassle of constantly remembering and updating passwords.
This step-by-step article aims to guide you through the process of setting up an SSH server on your Linux system, providing you with an alternative method for authentication using cryptographic keys. By seamlessly integrating public and private key pairs, you can enhance the security of your Linux environment and streamline your remote access experience.
Disclaimer: Prior knowledge of Linux systems and basic command-line usage is assumed. It is also recommended to backup critical data and exercise caution while performing any administrative tasks.
Streamlining Access: A Comprehensive Walkthrough to Establishing Secure Shell Connectivity on a Linux Environment with Key-based Authentication

In order to establish a secure and efficient means of remote access to a Linux system, it is crucial to set up an SSH server. By implementing key-based authentication, administrators can enhance the security of their server while simplifying the login process. This guide will take you through the step-by-step process of configuring an SSH server on a Linux system, emphasizing the use of cryptographic keys for authentication.
Generating and Managing SSH Key Pairs
In this section, we will explore the creation and management of SSH key pairs, which consist of a public key (which is stored on the server) and a private key (which is securely kept by the user). We will delve into the mechanisms behind key generation, discuss best practices for key management, and provide detailed instructions on how to implement these practices for enhanced security.
Configuring the SSH Server
Once the SSH key pairs have been generated, it is essential to configure the SSH server to accept key-based authentication. In this section, we will guide you through the process of modifying the SSH server configuration file, explaining the necessary parameters and options to enable key-based authentication. Additionally, we will discuss advanced server configuration options to further personalize the SSH environment to meet your specific needs.
Transferring Public Keys to the SSH Server
After generating and configuring the SSH keys, the public key must be transferred to the SSH server to enable key-based authentication. In this section, we will demonstrate various methods to securely copy the public key from the local machine to the SSH server. We will explore traditional file transfer methods, such as using the SSH protocol itself, as well as alternative approaches, including utilizing web-based file transfer protocols.
Enabling Key-based Authentication on the Client
To complete the setup process, the client machine must be configured to use key-based authentication when connecting to the SSH server. In this section, we will provide instructions on how to enable key-based authentication on popular SSH client applications. We will cover the necessary configuration options and settings for both command-line clients and graphical user interface (GUI) tools, ensuring a smooth and secure connection to the SSH server.
Testing and Troubleshooting
Once the setup is complete, it is crucial to test the SSH connection using key-based authentication to ensure its functionality. In this section, we will guide you through the process of testing the SSH connection and provide troubleshooting tips for common issues that may arise during the setup. By following these steps, you will be able to verify that the key-based authentication is working properly and address any potential problems effectively.
Enhancing Security and Best Practices
To further enhance the security of your SSH server, this section will cover additional best practices and security measures that can be implemented. We will discuss topics such as disabling password authentication, configuring firewall rules, and implementing two-factor authentication. By following these recommendations, you can ensure that your SSH server is robustly secured against potential threats.
Conclusion
In conclusion, this step-by-step guide has provided a comprehensive walkthrough on setting up an SSH server in a Linux environment using key-based authentication. By following these instructions and applying the recommended security practices, you can establish a secure and streamlined remote access solution for your Linux system. By utilizing the power of cryptographic keys, you can significantly improve the security of your SSH server while simplifying the authentication process for authorized users.
Advantages of Using SSH Keys Instead of Passwords
When it comes to securing your Linux server, there is an alternative to relying solely on passwords for authentication. SSH keys provide a more secure and convenient way to access your server remotely. In this section, we will explore the reasons why using SSH keys is a recommended practice.
| Enhanced Security | Using SSH keys significantly strengthens the security of your server. Passwords can be vulnerable to brute-force attacks or dictionary-based hacking attempts. However, SSH keys use asymmetric encryption, providing a higher level of protection. |
| Simplified Authentication | With SSH keys, you can simplify the authentication process. Once you have set up ssh keys on your server and client, you won't have to remember or enter passwords every time you want to connect. This can save time and minimize the risk of password-related security issues. |
| No Password Sharing | Sharing passwords among multiple users can be a security concern. By using SSH keys, each user can have their own key pair, eliminating the need to share passwords. This helps maintain individual accountability and confidentiality. |
| Stronger Authentication Methods | SSH keys provide stronger authentication methods compared to passwords. You can further increase security by using passphrase-protected keys. Passphrases add an extra layer of security, making it harder for unauthorized individuals to gain access to your server. |
In conclusion, SSH keys offer improved security, simplified authentication, and stronger authentication methods compared to using passwords for accessing a Linux server. By utilizing SSH keys, you can better protect your server and enhance the overall security of your system.
Generating Unique Identification for Secure Shell Connections on Local Machine
In the initial phase of setting up a secure shell (SSH) connection on your local machine, it is essential to generate a distinctive form of identification that ensures the security and authenticity of the connection. This unique identification, known as SSH keys, serves as a secure alternative to passwords and allows for secure remote access to the server.
In this step, we will explore the process of generating SSH keys on your local machine. This involves creating a pair of keys: a public key and a private key. The public key, as the name suggests, can be freely shared with remote servers, while the private key must be kept secret and securely stored on your local machine.
To generate SSH keys, you can use various tools such as the OpenSSH suite, PuTTY, or Git Bash, depending on your operating system. These tools provide command-line interfaces that facilitate the key generation process.
Once the keys are generated, they can be used to establish secure connections with SSH servers by exchanging and verifying the keys between the local machine and the server. This method eliminates the need for passwords and provides a more secure and efficient way to establish remote connections.
| Key Generation Steps: |
|
By following the instructions in this step, you will successfully generate SSH keys on your local machine, establishing a crucial aspect of the SSH connection setup process. Once the keys are generated, they are ready to be utilized in the subsequent steps of configuring the SSH server and enabling secure remote access.
Step 2: Transferring the public key to the remote server
Once you have generated your unique authentication key, the next step is to securely transfer the public key to the remote server. This key will serve as your identification when connecting to the server, ensuring a secure and encrypted connection.
Before transferring the public key, it is important to ensure that you have established a secure connection to the remote server. This can be done using various methods such as secure file transfer protocols or secure shell protocols.
Once a secure connection is established, you can proceed with transferring the public key. This involves copying the content of the public key file and pasting it into the appropriate file on the remote server.
It is crucial to properly place the public key content in the correct file on the remote server. Typically, the public key file is located in the ".ssh" directory on the remote server, under the authorized_keys file.
After pasting the public key content into the authorized_keys file, make sure to save the changes and exit the file. It is also important to set the correct permissions for the authorized_keys file to maintain security.
With the public key successfully transferred and the necessary configurations completed, you are now ready to proceed to the next step in setting up your SSH server in Linux. This will allow you to securely connect to the remote server using your private key for authentication.
[MOVIES] [/MOVIES] [/MOVIES_ENABLED]FAQ
What is SSH server and why do I need to set it up in Linux?
SSH server stands for Secure Shell server, which allows secure remote access to a Linux system. Setting up an SSH server in Linux is important for various purposes, such as remote administration, secure file transfer, and tunneling network connections.
Can I use passwords instead of keys for SSH authentication?
Yes, you can use passwords for SSH authentication. However, using SSH keys provides a higher level of security compared to passwords as they are longer and more complex. Additionally, keys eliminate the risk of password brute-force attacks.
How do I generate SSH keys?
You can generate SSH keys using the ssh-keygen command in Linux. Simply open a terminal and type "ssh-keygen" followed by pressing the Enter key. This will generate a public and private key pair, which can be used for SSH authentication.
What is the purpose of authorized_keys file?
The authorized_keys file is located in the ~/.ssh directory and contains a list of public keys that are allowed to connect to the SSH server. When a client tries to authenticate, the server checks whether the corresponding public key is present in the authorized_keys file to grant access.
How can I disable password authentication and only allow SSH key authentication?
To disable password authentication and only allow SSH key authentication, you need to modify the SSH server configuration file (/etc/ssh/sshd_config). Look for the "PasswordAuthentication" option and set it to "no". Save the file and restart the SSH service for the changes to take effect.




