Discover the art of seamlessly gaining entry into your Linux server without compromising security. In this guide, we will unveil a powerful tool that elevates your remote access experience to new heights, enabling you to effortlessly manage your server from anywhere in the world.
Unleash the potential of secure shell access and open up a world of possibilities. By harnessing the capabilities of a powerful protocol, you gain unparalleled control over your Linux machine, allowing you to execute commands, transfer files, and securely interact with your server's operating system.
Delve into the realm of remote administration, as we explore the intricacies of setting up a secure connection to your Linux system. Uncover the secrets of secure authentication methods, such as public key cryptography, that will safeguard your data and prevent unauthorized access.
Why is Secure Shell Connectivity Crucial for a Linux Device?

When considering the significance of reliable network connectivity to a Linux system, the integration of Secure Shell (SSH) becomes an indispensable component. The ability to establish secure, encrypted remote connections is paramount in ensuring the enhanced accessibility, management, and protection of sensitive information within a Linux environment.
Employing SSH access facilitates seamless remote administration, allowing authorized individuals to connect to a Linux device from a different location. This connectivity provides the flexibility and convenience of managing the system's operations, configuration settings, and troubleshooting without requiring physical presence.
Furthermore, SSH encrypts the communication channels, guaranteeing the confidentiality and integrity of data transmitted between the connected systems. Thus, unauthorized access or interception of sensitive information is significantly mitigated, contributing to the overall security of the Linux device and protecting it against potential threats and malicious activities.
In addition to secure remote administration, SSH access enables seamless file transfers between different systems, ensuring the secure exchange of data. This capability proves invaluable for system administrators, developers, and other users who need to efficiently and securely transfer files to and from a Linux device.
Moreover, by restricting access to SSH connections through proper authentication mechanisms, organizations and individuals can fortify the overall security posture of their Linux computer, effectively controlling who can establish connections and minimizing the risk of unauthorized access.
All in all, SSH access plays a fundamental role in reinforcing the reliability, accessibility, and security of a Linux computer, empowering users with the ability to remotely manage, transfer files, and protect sensitive information within a seamless and secure environment.
Installing OpenSSH on a Linux System
In this section, we will outline the process of installing OpenSSH on a Linux system, enabling secure remote access to the machine. By following these steps, you will be able to set up a secure and encrypted connection between the local and remote computers without having to physically be present at the machine.
To begin, you will need to access the terminal on your Linux system. Once you are in the terminal, you can proceed with the installation process. 1. Update the package manager by entering the following command: 'sudo apt update'. This will ensure that you have the latest package information. 2. Install OpenSSH by running the command: 'sudo apt install openssh-server'. This command will download and install the necessary files for OpenSSH. 3. During the installation process, you may be prompted to enter your password. This is necessary for administrative privileges to install the software. 4. Once the installation is complete, you can verify if the service is running by executing the command: 'sudo systemctl status ssh'. |
By following these simple steps, you can easily install OpenSSH on your Linux system, providing secure and encrypted access to your computer remotely. This will enable you to execute commands, transfer files, and perform various tasks on your Linux machine from any location.
Configuring Secure Shell (SSH) on a Linux System

Ensuring secure and reliable remote access to a Linux system is a crucial aspect of system administration. In this section, we will explore the process of configuring the Secure Shell (SSH) protocol on a Linux computer. By implementing SSH correctly, you can establish a secure and encrypted connection between remote machines, enabling you to securely manage your Linux system.
Generating SSH Keys
One of the first steps in configuring SSH is generating the necessary SSH keys. SSH keys consist of a public key that is placed on the remote server and a private key that is securely stored on your local machine. These keys are used for the authentication process when establishing a connection.
Synonyms: create, produce, construct, generate, forge
Customizing SSH Configuration
Once the SSH keys are generated, customizing the SSH configuration on your Linux computer is essential. The SSH configuration file allows you to define various options and parameters, including access restrictions, authentication methods, and log settings. By properly configuring these options, you can enhance the security and control of your SSH connections.
Synonyms: adjusting, adapting, tailoring, modifying, fine-tuning
Enabling Two-Factor Authentication
In order to add an extra layer of security to your SSH connections, enabling two-factor authentication (2FA) is highly recommended. Two-factor authentication requires an additional form of authentication, such as a physical token or a one-time password (OTP), to be provided along with the SSH key. This significantly increases the complexity for an unauthorized user to gain access to your Linux system.
Synonyms: activating, enabling, setting up, implementing, integrating
Configuring SSH Firewall Rules
To further enhance the security of your SSH setup, configuring appropriate firewall rules is crucial. By setting up firewall rules, you can restrict SSH access to specific IP addresses or networks, preventing unauthorized access attempts. Implementing robust firewall rules ensures that only trusted machines can establish SSH connections to your Linux computer.
Synonyms: defining, setting, establishing, arranging, shaping
Logging and Monitoring SSH Activity
Monitoring SSH activity is vital for detecting and addressing any suspicious or unauthorized access attempts to your Linux system. By enabling SSH logging and employing monitoring tools, you can effectively track user login attempts, connection errors, and other SSH-related events. This proactive approach allows you to promptly respond to potential security threats.
Synonyms: tracking, observing, overseeing, supervising, scrutinizing
Generating SSH Key Pair for Authentication
In this section, we will explore the process of creating a secure SSH key pair for authentication purposes. By using an SSH key pair, you can enhance the security of your Linux system by allowing secure remote access without relying on traditional password-based authentication.
Firstly, we will need to generate a unique public-private key pair. The private key will be stored securely on your local machine, while the public key will be shared with the remote Linux computer you wish to access. The keys are mathematically related but cannot be derived from each other, ensuring a secure authentication process.
- Open a command-line interface on your local machine and navigate to the directory where you want to store the key pair.
- Execute the command to generate the key pair, specifying a secure passphrase to protect your private key.
- Once the key pair is generated, you will have a private key file and a corresponding public key file.
- Next, securely transfer the public key to the remote Linux computer. This can be done by various methods, such as copying the key to a USB drive or using secure file transfer protocols like SCP or SFTP.
- Once the public key is on the remote computer, you need to add it to the authorized keys list for the user account you wish to authenticate with.
- Now that the key pair is set up, you can configure your SSH client on your local machine to use the private key for authentication when connecting to the remote Linux computer.
- Test the SSH connection to ensure that the key-based authentication is functioning correctly.
By following these steps, you will have successfully generated an SSH key pair and configured your Linux system for secure and convenient remote access. This method provides an additional layer of security compared to traditional password-based authentication.
Securing Remote Connectivity with Password Authentication
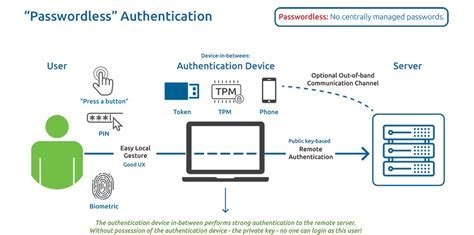
In this section, we will explore the process of enabling secure remote connectivity to your Linux system using password authentication for SSH access. By implementing password authentication, you can set up a secure login mechanism that verifies the identity of users accessing your system remotely.
Enhancing Security with Password Authentication:
Configuring password authentication for SSH access is a valuable step in securing remote connectivity to your Linux computer. This method allows users to authenticate themselves with a password rather than relying solely on cryptographic keys or certificates.
Advantages of Password Authentication:
Password authentication provides an additional layer of security by requiring users to enter a unique password during the authentication process. This method ensures that only authorized individuals with the correct credentials can gain access to your Linux system remotely.
Implementing Password Authentication:
To set up password authentication, you will need to modify the SSH configuration file on your Linux computer. By editing the configuration file, you can enable password authentication and specify the desired password requirements, such as length and complexity. It is important to choose a strong password policy and regularly enforce password changes to maintain the integrity of your system.
Best Practices for Password Authentication:
When implementing password authentication, it is essential to follow best practices to enhance the overall security of your Linux computer. These include:
- Using strong and unique passwords for each user account
- Enabling account lockouts after multiple failed login attempts
- Regularly updating passwords to prevent unauthorized access
- Disabling unused user accounts to minimize potential security risks
These practices will help strengthen your system's defenses against potential threats and ensure the confidentiality and integrity of your data.
Allowing Secure Remote Connections for a Designated User
In this section, we will explore the steps to grant secure remote access to a specific individual on your Linux system. By implementing this process, you can ensure that only authorized users can establish a connection to the system from a remote location.
Identification: Firstly, it is crucial to identify the user for whom you want to enable SSH access. Make sure you have the necessary details, such as the username or user ID, to proceed with the configuration.
Configuration: Once you have identified the user, you can proceed with configuring the SSH service to allow access. This involves modifying certain files, such as the SSH server configuration file, to specify the user's access permissions and authentication methods.
Key-based Authentication: One widely recommended authentication method is key-based authentication. This method uses cryptographic key pairs, consisting of a public and private key, to authenticate users. We'll guide you through the process of generating and configuring the necessary key pairs for the designated user.
Firewall Considerations: To ensure the security of your Linux system, it is essential to consider any firewall settings that may affect SSH access. We'll cover how to review and modify firewall rules to allow incoming SSH connections for the specific user without compromising overall system security.
Testing the Connection: After completing the configuration steps, it's important to verify that the designated user can successfully establish a secure SSH connection. We'll provide instructions on how to test the connection to ensure everything is functioning as expected.
Regular Maintenance: It's essential to regularly review and update SSH access permissions for your Linux system. We'll share best practices on periodically reviewing user access, disabling unused accounts, and revoking SSH access for individuals who no longer require it.
Security Considerations: Finally, we'll provide some additional security considerations to keep in mind when enabling SSH access for a specific user. These recommendations include using strong passwords, limiting user privileges, and monitoring SSH log files for any suspicious activities.
Using SSH Agent for Key-based Authentication
Enhance the security and convenience of accessing your Linux machine by utilizing the power of SSH agent for key-based authentication. This method offers a reliable and efficient way to authenticate your identity for secure remote login.
With SSH agent, you can securely store your private key and easily access it whenever you need to authenticate without repeatedly entering your passphrase. This simplifies the process and eliminates the need to remember a complex password or passphrase for each login attempt.
Setting up SSH agent involves a few simple steps. First, you will need to generate a key pair and add the public key to the authorized_keys file on the remote Linux machine. Once this is done, you can add your private key to the SSH agent using the ssh-add command.
- Generate a key pair using the ssh-keygen command
- Add the public key to the authorized_keys file on the remote Linux machine
- Start the SSH agent using the ssh-agent command
- Add your private key to the SSH agent using the ssh-add command
- Configure your SSH client to use the SSH agent for key-based authentication
By following these steps, you can ensure a secure and streamlined process for accessing your Linux machine remotely. With SSH agent and key-based authentication, you can enjoy the benefits of an enhanced level of security without the inconvenience of remembering complex passwords.
Establishing Remote Connection by Configuring Port Forwarding
In the realm of network communication, being able to configure port forwarding is essential for establishing a secure and efficient remote connection to a Linux device using the SSH protocol. This guide explores the process of setting up SSH access through port forwarding, presenting step-by-step instructions for configuring and managing port forwarding rules.
Understanding Port Forwarding
Port forwarding plays a crucial role in directing network traffic from one network interface to another, facilitating remote access to specific services or applications hosted on a Linux device. By configuring port forwarding, you can redirect incoming SSH requests from an external network to the correct port on the internal network, ensuring smooth and secure access to your Linux computer.
Configuring Port Forwarding Rules
Setting up SSH access via port forwarding involves establishing and managing port forwarding rules on both the router and the Linux machine. This section outlines the necessary steps to configure port forwarding, from accessing the router's configuration settings to defining the appropriate rules in the Linux firewall.
Accessing Router Configuration
To begin, access the router's administration interface by opening a web browser and entering the default gateway IP address. Login with the administrator credentials, navigate to the "Port Forwarding" or "Virtual Server" section, and proceed to create a new port forwarding rule.
Defining Port Forwarding Rules
Within the router's port forwarding settings, specify the following details for the SSH port forwarding rule:
| Option | Description |
|---|---|
| External Port | The port number on the external network to redirect SSH traffic. |
| Internal IP | The static IP address assigned to the Linux computer on the internal network. |
| Internal Port | The SSH port number on the Linux computer. |
| Protocol | The protocol type, usually TCP, to use for the SSH connection. |
Save the port forwarding rule and ensure it is enabled before proceeding to configure the Linux machine.
Adjusting Linux Firewall Settings
On the Linux computer, access the firewall settings and allow incoming SSH connections on the configured port. This typically involves modifying the rules of the firewall software, such as "iptables" or "ufw", to permit SSH traffic from the external network through the specified port.
Verifying and Testing SSH Access
After successfully configuring port forwarding on both the router and Linux machine, it is crucial to verify that SSH access is functioning as intended. Test the SSH connection by using a remote device on the external network to connect to the Linux computer via the configured port. Ensure that the connection is established securely and error-free, allowing you to remotely access and manage your Linux device.
By understanding and implementing port forwarding for SSH access, you can ensure secure and convenient remote management of your Linux computer from anywhere in the world.
Troubleshooting Connectivity Problems with Remote Server

In this section, we will explore common issues that may arise when attempting to establish a secure remote connection with a Linux server using SSH. We will discuss potential causes of connectivity problems and provide troubleshooting tips to help resolve them.
1. Incorrect SSH Configurations:
One of the most common reasons for SSH connection issues is incorrect configurations. Ensure that the SSH protocol is enabled on the server and the correct port is specified. Check that the firewall settings allow inbound SSH traffic, and verify that the server's SSH service is running properly.
2. Authentication Failures:
Authentication failures can occur if the client's public key is not properly added to the server's authorized keys or if the private key is not correctly configured on the client-side. Make sure that the correct public key is added to the authorized keys file and that the private key is correctly associated with the client.
3. Network Connectivity Issues:
Network connectivity problems can also prevent SSH access. Check the network settings, such as IP address and subnet mask, to ensure they are configured correctly. Verify that there are no network firewall rules blocking SSH traffic and that both the server and client have working network connections.
4. Public/Private Key Mismatch:
If the server's public key and the client's private key do not match, SSH access will be unsuccessful. Double-check that the public key used by the server matches the private key on the client-side. Regenerate keys if necessary and ensure they are correctly configured.
5. Software Compatibility Issues:
In some cases, SSH access problems may arise due to incompatible software versions. Verify that both the client and server are running compatible SSH software versions. Upgrade or downgrade the software if necessary to ensure compatibility.
Conclusion:
When facing SSH access issues, it is essential to diagnose and resolve the underlying problem. By addressing incorrect configurations, authentication failures, network connectivity issues, public/private key mismatches, and software compatibility problems, you can troubleshoot and resolve SSH connectivity problems effectively.
How to Enable SSH in Ubuntu 22.04 LTS Linux | Install openssh-server
How to Enable SSH in Ubuntu 22.04 LTS Linux | Install openssh-server by ProgrammingKnowledge 31,920 views 10 months ago 10 minutes, 42 seconds
access EVERYTHING from your web browser!! (Linux and Windows Desktop, SSH) // Guacamole Install
access EVERYTHING from your web browser!! (Linux and Windows Desktop, SSH) // Guacamole Install by NetworkChuck 1,628,760 views 2 years ago 29 minutes
FAQ
What is SSH and why is it necessary to set up SSH access to a Linux computer?
SSH stands for Secure Shell and it is a cryptographic network protocol used for secure remote login, command execution, and file transfer between computers. Setting up SSH access to a Linux computer allows you to securely connect to and manage the computer remotely, without physically being present.
How can I check if SSH is installed on my Linux computer?
To check if SSH is installed on your Linux computer, you can open a terminal and type the following command: "ssh -V". This will display the version of SSH installed on your machine. If SSH is not installed, you can install it by running the command: "sudo apt-get install openssh-server" (for Ubuntu and Debian based distributions) or "sudo yum install openssh-server" (for CentOS and Red Hat based distributions).




