In the fast-paced world of technology, it's crucial to prioritize the security of your systems and data. One effective way to achieve this is by implementing Secure Shell (SSH) access. This powerful protocol allows you to establish secure communication channels over unsecured networks, preventing unauthorized access and ensuring the safety of your Linux environment.
By enabling SSH access, you can securely connect to your Linux machine remotely, even from a different geographical location. Whether you're a system administrator, a developer, or a security-conscious individual, understanding how to set up SSH access on your Linux system is an essential skill.
Throughout this article, we will explore the process of enabling SSH access on your Linux machine, without directly revealing the specific distribution we will be using. We will guide you through the steps and provide invaluable insights into the best practices for configuring SSH, guaranteeing the highest level of security.
Ensuring Secure Remote Connections: The Vitality of SSH
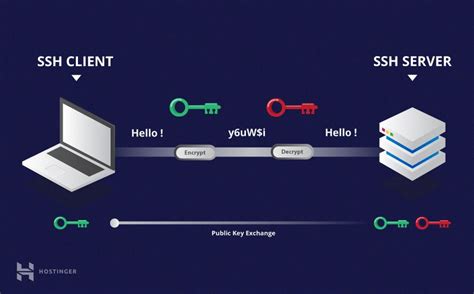
Secure remote access is a critical aspect of today's interconnected world, allowing individuals and organizations to connect to their systems from anywhere and at any time. This is particularly important for Linux Mint users, who value the security and reliability of their operating system. In this context, SSH stands out as a fundamental technology that ensures a secure and encrypted connection for remote access.
SSH, or Secure Shell, plays a pivotal role in establishing secure connections between two devices over an unsecured network, such as the internet. Its significance lies in the fact that it provides a secure channel for data communication, preventing unauthorized access and potential data breaches.
By utilizing strong encryption algorithms and authenticating both the client and the server, SSH guarantees the confidentiality, integrity, and authenticity of information transmitted between devices. Through the use of public-key cryptography, SSH offers a robust security framework that safeguards sensitive data from interception or manipulation.
Moreover, SSH is not limited to secure file transfers or remote logins. It encompasses a wide range of functionalities, including secure remote administration, secure tunneling, and secure command execution. This versatility provides users with comprehensive control and administration of their systems while maintaining a high level of security.
In conclusion, SSH is an indispensable tool for establishing secure remote connections on Linux Mint and other operating systems. Its robust encryption, authentication mechanisms, and versatile features make it a vital component for ensuring secure and reliable remote access, protecting against unauthorized access and maintaining data integrity.
Installing OpenSSH on Linux Mint
In this section, we will guide you through the process of setting up a secure and reliable remote connection on your Linux Mint system. By installing OpenSSH, a robust and widely-used remote login software, you will be able to access your Linux Mint machine from any remote location with ease and confidence.
Firstly, we recommend installing OpenSSH, which will enable secure access to your Linux Mint system over a network. OpenSSH is a popular open-source software suite that provides a secure channel for remote login sessions, file transfer, and other network services. It utilizes strong encryption algorithms and authentication protocols to ensure the confidentiality and integrity of your data.
To begin the installation process, open the terminal on your Linux Mint system. You can do this by pressing Ctrl + Alt + T or by searching for "terminal" in the application menu. Once the terminal is open, enter the following command to install the OpenSSH package:
sudo apt-get install openssh-server
After entering the command, you will be prompted to enter your administrator password. Once you provide the password and press Enter, the package manager will download and install the necessary files to set up OpenSSH on your system.
Once the installation is complete, OpenSSH will be up and running on your Linux Mint machine. You can verify the installation by checking the status of the OpenSSH service. In the terminal, type the following command:
sudo service ssh status
If the service is active and running, you will see a message indicating its status. Congratulations! You have successfully installed OpenSSH on your Linux Mint system, enabling secure remote access.
Now that OpenSSH is installed, you can configure the necessary firewall rules and access settings to enhance the security of your remote connection. Stay tuned for our next section on configuring SSH access on Linux Mint.
A Step-by-Step Guide to Installing OpenSSH: Enhancing Secure Remote Connectivity
Secure remote connectivity is vital for various computing systems to ensure efficient network administration and data transfer. In this comprehensive guide, we will walk you through the installation process of OpenSSH – a robust and widely-used SSH protocol – which facilitates secure communication between different devices and allows remote login and execution of commands.
- Check the Compatibility: Ensure that your operating system supports OpenSSH installation by referring to the official documentation or community forums.
- Install OpenSSH Package: First, update the package index of your system by running the following command:
sudo apt-get update. Next, install the OpenSSH package using the command:sudo apt-get install openssh-server. - Configure Firewall: Adjust your firewall settings to grant access to OpenSSH. Typically, you need to allow incoming connections on port 22, which is the default port for SSH.
- Customize OpenSSH Configuration (Optional): Navigate to the configuration file located at
/etc/ssh/sshd_configand make any necessary modifications according to your requirements. This file allows you to define specific settings, such as changing SSH port, limiting user access, or enabling key-based authentication. - Restart OpenSSH Service: Apply the changes made to the configuration file by restarting the OpenSSH service. Execute the command:
sudo service ssh restart. - Verify OpenSSH Installation: To confirm that OpenSSH is successfully installed, launch a separate terminal window and run the command:
ssh localhost. If the connection is established without any errors, OpenSSH is up and running. - Connect to Remote Host: To establish a secure SSH connection with a remote host, use the command:
ssh username@remote_ip_address. Replace "username" with your username and "remote_ip_address" with the IP address or hostname of the target system.
Congratulations! You have now completed the installation of OpenSSH and can securely access and administer remote systems. Remember to regularly update OpenSSH to benefit from the latest security enhancements and patches.
Setting up Secure Shell (SSH) Configurations on the Linux Mint Operating System
In this section, we will explore the process of configuring and customizing the Secure Shell (SSH) settings on a Linux Mint operating system. By adjusting the SSH configurations, you can enhance the security and optimize the remote access capabilities of your system.
- Reviewing the SSH Configuration Files
- Customizing SSH Port for Enhanced Security
- Enabling SSH Key Authentication
- Restricting SSH Access to Specific IP Addresses
- Managing SSH User Accounts and Permissions
Understanding the SSH configuration files is the first step towards configuring SSH on Linux Mint. By reviewing these files, you can gain insights into the default settings and make necessary adjustments. Additionally, customizing the SSH port can further fortify your system's security by preventing unauthorized access.
Enabling SSH key authentication offers a more secure alternative to password-based authentication. By generating and managing SSH key pairs, you can streamline the authentication process and eliminate the risk of password-related vulnerabilities.
Restricting SSH access to specific IP addresses or networks provides an added layer of security. By allowing access only from trusted sources, you can minimize the risk of unauthorized access and potential attacks.
The management of SSH user accounts and permissions is crucial for maintaining control and ensuring secure remote access. In this section, we will explore methods for creating and managing user accounts, as well as configuring their permissions and restrictions.
By implementing these various SSH configurations on your Linux Mint system, you can enhance its security and optimize remote access, providing a reliable and secure environment for your SSH connections.
Enhancing Security: Customizing SSH Configuration
In this section, we will explore various methods to improve the security of your remote connection by customizing the settings of your SSH environment. By fine-tuning your SSH configuration, you can effectively protect your system from potential unauthorized access and mitigate security risks.
1. Enforcing Strong Authentication: Strengthening the authentication process is crucial in ensuring secure remote access. We'll delve into techniques such as implementing public key authentication, enabling multifactor authentication, and using certificate-based authentication to enhance the overall security of your SSH connections.
2. Limiting Access and Privileges: Restricting access to your system is a fundamental security measure. We will discuss ways to limit SSH access to specific users or groups, including the use of firewall rules and the creation of custom user access policies. Additionally, we'll explore the concept of privilege separation and explain how to configure different levels of access privileges for different users.
3. Hardening Encryption and Algorithms: SSH encryption protocols play a crucial role in securing data transmission. We'll provide guidance on disabling weak algorithms, enabling stronger ciphers, and configuring key exchange algorithms to ensure robust encryption and protect against potential vulnerabilities.
4. Implementing Fail2Ban: To mitigate the risk of brute-force attacks and invalid login attempts, we'll introduce the concept of Fail2Ban. This powerful tool automatically detects and blocks suspicious IP addresses that exhibit malicious behavior, providing an additional layer of protection for your SSH server.
5. Monitoring and Logging: Monitoring SSH activity is essential for identifying potential security threats and suspicious activities. We'll explore different logging options and explain how to configure SSH to generate detailed logs, enabling you to analyze and respond to any security incidents effectively.
In this section, we will guide you through each step of customizing your SSH settings, equipping you with the knowledge and tools to enhance the security of your Linux system. By implementing these best practices, you can establish a secure and reliable SSH environment, ensuring the confidentiality and integrity of your remote connections.
Generating Key Pair for Secure Remote Connections
In this section, we will discuss the process of creating a unique set of cryptographic keys known as SSH key pair. These keys consist of a private key and a matching public key, which are used to authenticate and secure remote connections between systems.
To generate the SSH key pair, we will utilize a powerful cryptographic algorithm that ensures the confidentiality and integrity of the data being transmitted over the network.
By generating your own SSH key pair, you can enhance the security of your Linux Mint system by eliminating the need for passwords when establishing SSH connections. Instead, authentication is based on the possession of the private key, making it virtually impossible for unauthorized individuals to gain access to your system.
To create the SSH key pair, we will follow a step-by-step process that involves generating the private key, extracting the public key from it, and securely storing both keys on your Linux Mint system. We will also provide guidelines on how to properly protect and manage your SSH keys to maintain the highest level of security.
In addition, we will explain the concept of key fingerprinting and how it can be used to verify the authenticity of SSH key pairs. This ensures that you are connecting to the correct remote system and helps prevent man-in-the-middle attacks.
By the end of this section, you will have a comprehensive understanding of how to generate, manage, and utilize SSH key pairs, allowing you to establish secure and trustworthy remote connections on your Linux Mint system.
Steps to Generate and Utilize SSH Key Pair for Authentication
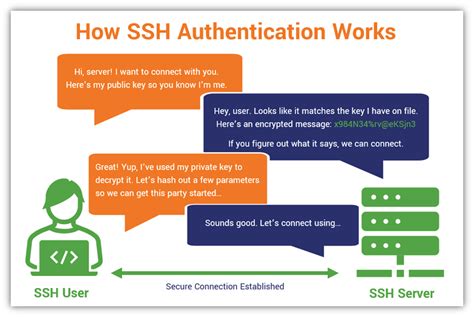
Creating and implementing an SSH key pair is an essential process for securely accessing remote servers. By generating an SSH key pair, you can establish a secure and encrypted connection between your local machine and the remote server. This method eliminates the need for traditional password-based authentication, providing an added layer of security.
Outlined below are the steps you need to follow to generate an SSH key pair and effectively utilize it for authentication:
- Generate the SSH key pair: Begin by generating a new SSH key pair using a secure algorithm. Various programs and utilities exist for this purpose, such as OpenSSH and PuTTYGen. These tools will create a public and private key pair.
- Choose a secure passphrase: A passphrase is an extra layer of security that protects your private key. It is akin to a password and should ideally be a combination of random words or phrases that are easy for you to remember but difficult for anyone else to guess. This passphrase will be required every time you use your SSH key.
- Store your private key securely: The private key is a sensitive file that should be kept in a secure location on your local machine. It is crucial to protect this file from unauthorized access to maintain the integrity of your SSH connection.
- Configure the remote server: To allow SSH key authentication, you need to configure the remote server to recognize your public key. This involves adding the public key content to the appropriate file on the server. The exact location and method may vary depending on the server's operating system and setup.
- Test the SSH key pair: Once the server is configured, you can test the SSH key pair by initiating an SSH connection to the remote server. If everything is configured correctly, the server will recognize your SSH key and grant you access without requiring a password.
- Optional: Disable password authentication: For enhanced security, you can further improve your SSH setup by disabling password authentication on the remote server. This ensures that only users with valid SSH keys can access the server, mitigating the risk of brute-force attacks.
By following these steps, you can create and utilize an SSH key pair to authenticate yourself when accessing remote servers. This method not only enhances security but also provides a more convenient and efficient way of managing remote connections.
Establishing Remote Connection to Your Linux Mint Machine
Ensuring secure and seamless remote access to your Linux Mint machine entails setting up a reliable and efficient communication channel between your computer and the Linux Mint operating system. This guide will walk you through the process of creating an SSH connection from another computer to your Linux Mint machine, allowing you to remotely manage and control your system.
Step 1: Enabling SSH Service
To enable remote access via SSH, you need to first activate the SSH service on your Linux Mint machine. This service acts as the gateway for incoming connections and facilitates secure communication between devices. By enabling SSH, you grant permission for external devices to establish a connection with your Linux Mint machine.
Note: Make sure to configure proper firewall settings to allow incoming SSH connections and enhance the security of your system.
Step 2: Configuring SSH Authentication
After enabling the SSH service, it is crucial to configure authentication settings to ensure that only authorized devices can establish a remote connection. By implementing strong authentication mechanisms, such as using SSH keys, you can significantly enhance the security of your Linux Mint machine.
Note: Avoid using weak or easily guessable passwords, as they can jeopardize the security of your remote connection.
Step 3: Establishing Remote Connection
Once the SSH service is enabled and authentication settings are in place, you can initiate a remote connection to your Linux Mint machine. Use an SSH client on the computer you wish to connect from to establish a secure and encrypted session with your Linux Mint operating system. This will enable you to execute commands, transfer files, and perform administrative tasks on your Linux Mint machine remotely.
Note: Ensure that both the client and the target Linux Mint machine are connected to the same network, or configure appropriate network settings to establish a connection over the internet.
By following these steps, you can successfully set up SSH access to your Linux Mint machine from another computer. This will enable you to manage your system remotely, enhancing flexibility and accessibility for your workflow.
Enabling Remote Connectivity to Linux Mint via Secure Shell
Discover how to establish a secure and remote connection to your Linux Mint operating system using the powerful Secure Shell (SSH) protocol. With SSH, you can securely access your Linux Mint system from any location, allowing you to manage your files, execute commands, and perform administrative tasks with ease.
By enabling remote connectivity through SSH, you can conveniently control your Linux Mint system remotely using a graphical user interface (GUI) or command-line interface (CLI) from any device. This capability enhances your flexibility and productivity, enabling you to efficiently manage your Linux Mint system without being physically present.
Learn the step-by-step process of configuring SSH access on your Linux Mint system, ensuring that your remote connection is secure and protected from unauthorized access. Understand the essential concepts of SSH key pairs, authentication methods, and encryption algorithms to establish a robust and foolproof connection.
Discover the various configuration options and settings available in Linux Mint to fine-tune your SSH access, such as managing multiple user accounts, restricting IP addresses, and implementing firewall rules. Implementing these security measures ensures that only trusted individuals can connect to your Linux Mint system remotely, maintaining the integrity of your data and privacy.
Follow our comprehensive guide to enable remote access to your Linux Mint system via SSH and unlock a whole new world of convenience and efficiency. Embrace the power of SSH and experience seamless remote management with your Linux Mint operating system.
Setting up Passwordless SSH Login
One of the key aspects of securing your Linux Mint system is setting up passwordless SSH login, which allows you to access your system remotely without entering a password. This not only enhances convenience but also strengthens the security of your system by eliminating the risk of password-based attacks. In this section, we will explore the steps to enable passwordless SSH login on your Linux Mint system.
- Generate SSH Key Pair
- Copy Public Key to Remote Server
- Configure SSH Settings
- Test Passwordless SSH Login
The first step in enabling passwordless SSH login is generating a key pair consisting of a public key and a private key. The public key will be stored on the remote server, while the private key will be securely stored on your local machine. This key pair ensures a secure and encrypted connection between your local machine and the remote server.
Once you have generated the SSH key pair, the next step is to copy the public key to the remote server. This involves adding the public key to the authorized_keys file on the remote server, which grants access to the corresponding private key. By doing so, you will be able to authenticate yourself on the remote server using the private key, without requiring a password.
After copying the public key to the remote server, you need to configure the SSH settings to allow passwordless authentication. This can be done by modifying the SSH server configuration file on the remote server. By specifying the appropriate settings, you can ensure that the server accepts key-based authentication and denies password-based authentication.
Once you have completed the above steps, it is important to test the passwordless SSH login to ensure everything is set up correctly. This involves attempting to log in to the remote server using the private key. If the login is successful without prompting for a password, then you have successfully enabled passwordless SSH login on your Linux Mint system.
Streamlining Secure Login: A Step-by-Step Guide to Passwordless SSH Access Setup
Ensuring hassle-free and secure login to your Linux distribution using SSH is a crucial aspect of system administration. This comprehensive guide aims to help you configure SSH login without the need to enter a password every time, enhancing convenience and efficiency.
| Step 1: | Generating SSH Key Pair |
| Step 2: | Transferring Public Key to the Remote Host |
| Step 3: | Securing the Private Key |
| Step 4: | Configuring SSH on the Remote Host |
| Step 5: | Testing Passwordless SSH Login |
| Step 6: | Maintaining and Revoking SSH Access |
In the initial step, we will generate a unique pair of cryptographic keys – a private key and a corresponding public key. These keys will serve as the means to authenticate your access without requiring a password. Next, we will transfer the public key to the remote host, enabling it to recognize and authorize your SSH connection.
Once the keys are in place, it is essential to secure the private key to prevent unauthorized use. This involves setting appropriate file permissions and optionally encrypting the private key with a passphrase.
Configuring SSH on the remote host entails modifying the SSH server's configuration file to allow passwordless login using public key authentication. This step ensures your system grants access solely based on the possession of the private key.
With everything set up, it is crucial to test the passwordless SSH login to confirm its successful implementation. This step will allow you to troubleshoot any potential issues and ensure a smooth login experience in the future.
Lastly, we discuss best practices for maintaining and revoking SSH access. These include regularly monitoring SSH access logs, implementing security measures to protect the private key, and promptly revoking access when necessary.
Managing Secure Shell Connections
When it comes to effectively managing your secure shell connections, there are several key aspects to consider. In this section, we will explore various techniques and approaches to optimize your SSH experience without compromising security.
One important aspect of managing SSH connections is understanding the concept of authentication methods. By utilizing different authentication methods, such as public key authentication or password authentication, you can enhance the security of your connections and control who has access to your system.
Another crucial aspect is managing SSH keys. SSH keys are cryptographic keys that allow you to authenticate securely without the need for a password. We will delve into the process of generating and managing SSH keys, including how to add and remove keys, as well as rotate them for added security.
Furthermore, we will discuss the configuration options available to customize your SSH connections. These options include setting up aliases for frequently used connections, specifying timeouts for inactive sessions, and configuring port forwarding for secure remote access to other services on your network.
In addition to configuration options, we will explore best practices for securing your SSH connections. This includes techniques like disabling root login, restricting SSH access to specific IP addresses or networks, and implementing two-factor authentication to provide an extra layer of security.
| Key Points: |
|---|
| Understanding authentication methods |
| Managing SSH keys |
| Customizing SSH connections |
| Securing SSH connections |
FAQ
How can I set up SSH access on Linux Mint?
To set up SSH access on Linux Mint, you need to install the OpenSSH server. You can do this by opening the terminal and running the command "sudo apt-get install openssh-server".
What are the benefits of setting up SSH access on Linux Mint?
Setting up SSH access allows you to remotely access your Linux Mint machine from another computer using a secure encrypted connection. This can be useful for managing your machine remotely or transferring files securely.
Do I need to have any prior knowledge to set up SSH access on Linux Mint?
While some basic knowledge of the Linux command line interface can be helpful, you don't need to be an expert to set up SSH access on Linux Mint. The process is fairly straightforward and there are plenty of tutorials available online to guide you through the process.
Can I use SSH access on Linux Mint to connect to other machines?
Yes, once you have set up SSH access on your Linux Mint machine, you can use it to connect to other machines running an SSH server. This allows you to remotely access and manage multiple machines from a single location.
Are there any security considerations when setting up SSH access on Linux Mint?
Yes, security is an important aspect to consider when setting up SSH access. It is recommended to use strong passwords or SSH keys for authentication, disable root login, and set up a firewall to restrict SSH access to trusted IP addresses only. These measures can help to enhance the security of your SSH connections.




