In the modern digital landscape, ensuring the security and integrity of your network is of paramount importance. One tool that holds incredible value in this regard is Snort, a powerful intrusion detection and prevention system. If you're a Linux enthusiast seeking to fortify your system against potential threats, then this step-by-step tutorial is tailor-made for you. Dive into the world of unparalleled network protection as we guide you through the process of setting up Snort on a Linux machine.
Embark on an enlightening journey where we demystify the intricacies of establishing an impenetrable shield for your network. This tutorial caters to both novices and experienced Linux users who are eager to explore the universe of network security. With our expert guidance, you'll gain a firm understanding of the essential steps required to install and configure Snort, empowering you to safeguard your digital assets with confidence.
As we navigate through this comprehensive walkthrough, we'll equip you with the knowledge needed to detect and mitigate potential threats swiftly. Through the clever utilization of various techniques and methodologies, we'll transform your Linux machine into an impregnable fortress against intrusion attempts, ensuring that your network remains secure in an increasingly interconnected world.
Introduction to Snort: A Comprehensive Overview
Understanding the fundamentals of Intrusion Detection Systems (IDS) is crucial in maintaining the security and integrity of a network. In this section, we will delve into the world of Snort, a powerful and widely-used open-source IDS solution that offers advanced threat detection capabilities. Through this comprehensive overview, you will gain insights into the purpose, features, and benefits of Snort, empowering you to make informed decisions regarding its implementation in your Linux environment.
The Advantages of Using Snort on a Linux Environment
When it comes to securing your network, utilizing an intrusion detection system (IDS) is crucial. Snort, a powerful open-source IDS, offers numerous benefits when deployed on a Linux operating system. This section explores the advantages of incorporating Snort in your network security strategy, highlighting its effectiveness, flexibility, and community support.
Enhanced Threat Detection: Snort's advanced detection capabilities enable it to identify and alert you about a wide range of threats, including network-based attacks, malicious traffic, and suspicious activities. Powered by a comprehensive set of rules, Snort can intelligently analyze network traffic and provide early warning signs of potential security breaches, allowing you to take proactive measures.
Customizability and Flexibility: One of the key strengths of Snort lies in its flexibility. With its extensive rule sets and plugins, Snort allows you to tailor the detection parameters according to your specific network requirements. Whether it's fine-tuning the detection thresholds, adjusting protocols, or customizing response actions, Snort on Linux empowers you to adapt the system to suit your unique security needs.
Active Community Support: Snort has a vibrant and active community of developers and security experts who continuously contribute to its improvement. This dedicated community regularly updates Snort with new rules, plugins, and patches, ensuring that the system remains up-to-date with the latest threats and vulnerabilities. The availability of community support also means that you can seek assistance, share experiences, and collaborate with like-minded professionals in optimizing Snort's performance on a Linux platform.
Cost-Effective Solution: Choosing a Linux operating system as the foundation for Snort adds another layer of cost-effectiveness to your network security strategy. Linux is an open-source platform that is free to use, reducing the overall investment required for deploying and maintaining the system. Furthermore, Snort itself is an open-source tool, eliminating the need for expensive commercial IDS solutions while still providing robust network security capabilities.
Integration with Existing Infrastructure: Snort seamlessly integrates with various network devices and systems, making it an ideal choice for organizations with diverse environments. Whether you have a complex network architecture, a mix of different operating systems, or a variety of network appliances, Snort on Linux can be easily integrated into your existing infrastructure, augmenting your overall security posture without causing disruption.
In conclusion, leveraging Snort on a Linux system offers a multitude of benefits for network security. From its advanced threat detection capabilities and flexibility in customization to its active community support and cost-effectiveness, Snort on Linux is a valuable tool to enhance your organization's security defenses and protect against emerging threats.
Installation Process
In this section, we will explore the process of installing Snort, an intrusion detection system, on a Linux-based operating system. By following the steps outlined here, you will be able to set up Snort and enhance your system's security by detecting and preventing potentially malicious activities.
Firstly, we will cover the initial setup requirements to ensure a smooth installation. Then, we will proceed with the installation process itself, including the necessary dependencies and configuration options. Finally, we will verify the successful installation and discuss any additional steps that may be required for optimal functionality.
Throughout this guide, we will provide clear and concise instructions, accompanied by relevant examples, to assist you in each step of the installation process. It is important to follow these instructions carefully to ensure a successful deployment of Snort on your Linux system.
By the end of this installation section, you will have a fully operational Snort setup on your Linux system, equipped to monitor and analyze network traffic for potential security threats. Let's begin the installation process and take a step towards fortifying your system's defenses against intruders.
Checking Linux System Requirements
In order to successfully set up and utilize Snort on your Linux system, it is crucial to ensure that your system meets the necessary requirements. By checking the Linux system requirements, you can ensure a smooth and efficient installation process, allowing Snort to function optimally on your system.
Firstly, it is important to verify that your Linux operating system is compatible with Snort. Ensure that you are using a supported distribution and version. Additionally, check for any specific dependencies or libraries that Snort may require and make sure they are installed on your system.
Next, assess the hardware specifications of your Linux system. Determine if your system meets the necessary CPU and memory requirements for Snort to operate effectively. Additionally, consider the storage capacity available on your system to accommodate extensive log files and other data generated by Snort.
Furthermore, it is important to evaluate the network capabilities of your Linux system. Check if your system has multiple network interfaces to allow Snort to monitor and analyze network traffic effectively. Additionally, ensure that your system has the necessary network connectivity and access to the internet for downloading Snort rules and updates.
Lastly, it is recommended to review the security configurations of your Linux system. Ensure that any firewalls or security software on your system do not interfere with Snort's functionality. Adjust any necessary network configurations or permissions to allow Snort the required access to the network traffic.
By thoroughly checking these Linux system requirements, you can ensure a successful setup and implementation of Snort on your system. This will help you in effectively monitoring and protecting your network against potential threats and attacks.
Obtaining and Compiling Snort: A Comprehensive Process
In this section, we will explore the detailed process of obtaining and compiling Snort on a Linux system. By following these steps, you will be able to download, configure, and compile Snort to ensure its successful installation and usage.
To begin, the initial step involves obtaining the necessary files and dependencies required for Snort's compilation. This process entails retrieving the latest version of Snort from the official website or a trusted repository. Additionally, you must gather other essential components such as the PCRE (Perl Compatible Regular Expressions) library and DAQ (Data Acquisition) module.
Component | Purpose |
Snort | The main intrusion detection and prevention system that analyzes network traffic and raises alerts for potential threats. |
PCRE Library | Provides support for regular expressions, enabling Snort to efficiently analyze patterns within network packets. |
DAQ Module | Offers a common interface for packet I/O, allowing Snort to interact with various network interfaces and capture traffic. |
Once you have acquired these prerequisites, it is crucial to verify their integrity by checking their cryptographic hash values or performing digital signature verification. These verification methods ensure the authenticity and integrity of the downloaded files.
After confirming the integrity of the obtained files, you can proceed with the compilation process. This involves configuring and building Snort on your Linux system. The configuration step allows you to customize Snort according to your specific requirements, such as specifying the network interfaces to monitor and the ruleset to use for intrusion detection. Following the configuration, you can commence the compilation, which transforms the source code into executable binaries that can be executed on your system.
As part of the compilation process, you may encounter certain challenges or errors. It is essential to address these issues promptly to ensure a successful compilation. Troubleshooting techniques, such as installing missing dependencies, resolving library conflicts, or modifying the build script, can be employed to overcome these obstacles.
Once the compilation is complete without any errors, you can proceed to the next steps in the Snort setup process, which involve configuring and tuning Snort's detection rules and configuring the necessary network monitoring interfaces. These subsequent steps will be covered in detail in the following sections.
Configuring Snort: Securing Your Network with Customized Settings
In this section, we will delve into the vital aspects of configuring Snort to enhance your network security. By fine-tuning Snort's settings, you can tailor its functionality to fit your specific requirements and effectively safeguard your system against potential threats.
To begin, it is crucial to understand the various configuration options and parameters that Snort offers. These parameters allow you to specify how Snort should analyze and respond to network traffic, thereby enabling you to customize its behavior according to your network environment.
- Rule Management: Here, we will explore the process of managing Snort's rules, which dictate the specific actions the system takes when it detects suspicious or malicious network activity. We will discuss techniques such as rule classification, rule suppression, and rule customization to ensure that Snort operates optimally for your network.
- Logging and Alerting: Snort provides extensive logging and alerting capabilities that allow you to monitor network events and take appropriate action. In this section, we will guide you through configuring logging options, selecting appropriate log formats, and setting up alert mechanisms to stay informed about potential security incidents.
- Network Traffic Analysis: Snort's ability to analyze network traffic in real-time is a vital aspect of its functionality. We will delve into the available options for traffic analysis, including protocol analysis, payload analysis, and flow analysis. You will learn how to configure these settings to maximize the effectiveness of Snort's analysis capabilities.
- Performance Optimization: Configuring Snort optimally can significantly enhance its performance and reduce false positive or false negative detections. We will discuss techniques such as rule optimization, preprocessor configuration, and hardware acceleration to ensure that Snort operates efficiently for your network traffic load.
- Integration with Additional Tools: Snort integrates seamlessly with other security tools to provide a comprehensive security framework. We will explore how to configure Snort to work alongside tools such as Barnyard2, which facilitates enhanced log management and analysis.
By following this step-by-step guide for configuring Snort, you will not only strengthen your network security but also gain a deeper understanding of the inner workings of this powerful intrusion detection and prevention system.
Creating the Heart of Snort: Fundamental Rules for Optimal Performance
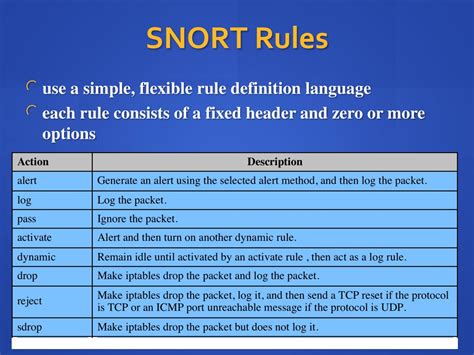
In this section, we will delve into the creation of the core rules that form the backbone of Snort's functionality. These rules are crucial for maximizing the performance and effectiveness of Snort in detecting and mitigating various network threats. By crafting well-defined and comprehensive rules, you can enhance your network security posture and ensure that Snort operates at its full potential.
Firstly, it is essential to understand the significance of rule syntax and structure. We will walk you through the steps of constructing rules using Snort's rule language, including defining rule options, conditions, and actions. You will learn how to use various rule modifiers, such as content, depth, and pcre, to specify the characteristics of packets that should be matched by Snort.
Additionally, we will explore the utilization of variables and flow control mechanisms within the rule creation process. These features allow for dynamic rule development, enabling Snort to adapt to changes in network traffic and effectively respond to emerging threats. We will provide examples and explain how to define variables, implement logical operators, and incorporate flow control directives to create robust and adaptable rules.
- Choosing appropriate rule options and thresholds is another critical aspect of rule creation that we will cover extensively. Configuring these parameters correctly ensures accurate detection with minimal false positives or negatives. We will guide you through the available preprocessor options, such as stream4, frag3, and stream5, and explain how to configure them optimally for your network environment.
- Furthermore, we will discuss best practices for organizing and managing rule sets. Categorizing rules into logical groups and efficiently structuring them can streamline maintenance, improve performance, and simplify troubleshooting. We will provide recommendations on creating rule categories, understanding rule order, and leveraging rule management tools to enhance the efficiency of rule management.
- Lastly, we will explore the concept of rule performance optimization. Sometimes, less is more when it comes to rule creation. By employing various techniques, such as rule compression, negation, and blacklist/whitelist tuning, you can significantly improve Snort's detection capabilities without sacrificing system resources. We will delve into these optimization techniques and discuss their impact on Snort's performance and resource consumption.
By mastering the art of creating Snort's core rules, you will empower yourself to build a robust and adaptive intrusion detection system tailored to your network's specific requirements and threat landscape.
Configuring Snort to Monitor Network Traffic
As you embark on the journey of setting up Snort on your Linux system, it is crucial to understand the importance of configuring Snort to effectively monitor network traffic. This section focuses on the essential steps to tailor Snort's settings and parameters to suit your specific network environment.
Identifying Target Network: Before diving into the configuration process, it is crucial to identify the target network that Snort will monitor. This includes determining the IP address range and subnet that Snort will analyze for potential threats.
Tuning Rule Sets: Snort utilizes rule sets to detect and classify various types of network traffic. To optimize Snort's performance, it is necessary to tune the rule sets by enabling or disabling specific rules, adjusting thresholds, or customizing rule actions.
Defining Preprocessors: Snort's preprocessor modules enhance its network traffic analysis capabilities by detecting and normalizing specific protocols, performing session reconstruction, or conducting anomaly detection. It is important to configure and enable the appropriate preprocessors based on your network's requirements.
Setting Output Plugins: Snort provides various output plugins to store or deliver alerts generated during network traffic analysis. Deciding on the appropriate output plugin based on your operational needs and tailoring its settings, such as defining a log directory or configuring alert notification mechanisms, is vital.
Establishing Logging and Alerting: Configuring Snort's logging options is essential to ensure comprehensive record-keeping and to facilitate incident investigation. This section focuses on setting up appropriate logging mechanisms, including logging to files, databases, or Security Information and Event Management (SIEM) systems. Additionally, alerting mechanisms for real-time notification of potential threats can be customized based on your network's requirements.
Implementing Performance Optimization Techniques: Snort's performance can be further enhanced by utilizing various techniques, such as implementing inline mode, load balancing, or distributed configurations. Understanding these optimization techniques and their impact on Snort's performance will help you fine-tune your configuration accordingly.
Verifying Configuration: Once you have completed the configuration process, it is crucial to validate that Snort is functioning correctly. This includes verifying that rules are being loaded, preprocessors are working as expected, and alerts are being generated and logged appropriately.
By following these steps and configuring Snort to monitor network traffic effectively, you can ensure a vigilant and proactive approach to network security, detecting and responding to potential threats in a timely manner.
Exploring the Functionality of Snort: A Hands-On Approach

Having successfully configured Snort on your Linux system, the next crucial step is to thoroughly test its functionality to ensure that it is correctly detecting and responding to potential threats. By conducting comprehensive tests, you can gain confidence in the effectiveness of Snort as an intrusion detection and prevention system.
To begin testing Snort, one of the initial steps involves generating test traffic on your network. This can be achieved by either using specialized tools or simulating realistic attack scenarios. By generating various types of network traffic, such as malicious packets, malformed protocols, or known patterns of attacks, you can assess the ability of Snort to identify and alert you about potential security breaches.
One of the primary test scenarios involves launching known attacks, commonly referred to as "signature-based testing." In this approach, intentionally crafted attack packets are sent to the monitored network, mimicking real-world threats. By examining Snort's response, including its detection, logging, and alerting capabilities, you can gauge its accuracy in identifying and combating such attacks.
- Test the effectiveness of Snort's rule-based detection system by creating custom rules targeted at specific attack patterns or behaviors. By carefully crafting and deploying these rules, you can assess Snort's ability to identify attacks that exhibit specific characteristics.
- Conduct ongoing testing and fine-tuning of Snort's configuration to ensure optimal performance. By analyzing the collected logs and alerts, you can identify any false positives or false negatives and make necessary adjustments to the rule sets and configurations.
- Perform a comprehensive system test by simulating a variety of attack scenarios, such as network-wide scans, denial-of-service attacks, or attempts to exploit common vulnerabilities. Analyze how Snort responds to each scenario and assess its overall ability to protect your network against these threats.
It is important to note that testing Snort is an iterative process that should be conducted regularly to ensure its ongoing effectiveness. By continuously refining and updating its rule sets, configurations, and testing scenarios, you can enhance your network's security posture and stay ahead of evolving threat landscapes.
Verifying Snort Installation
In this section, we will discuss how to confirm the successful installation of Snort on your Linux system. Verifying the installation ensures that the necessary components are set up correctly and ready to be used for network intrusion detection.
First, we will check if Snort executable is available in the system. Open the terminal and type snort -V. This command displays the Snort version and the build information. If the command is not recognized, it indicates that Snort may not be installed properly or its location is not included in the system's PATH.
Next, we need to verify the configuration files. Snort relies on various configuration files to define its behavior and rulesets. By default, the main configuration file is located at /etc/snort/snort.conf. Use the command ls -l /etc/snort/snort.conf to verify the existence of the file and ensure that it has the necessary read permissions.
Once the configuration file is confirmed, we can check if Snort rules are correctly set up. These rules define the signatures used by Snort to detect network intrusions. To list the available rules, use the command ls -l /etc/snort/rules/. Ensure that the directory contains the necessary rule files and that they can be accessed by Snort.
Finally, we will test the Snort installation by running a test capture. This captures network traffic and displays the output on the screen. Use the command sudo snort -dev -i eth0, replacing eth0 with the appropriate interface name for your system. If Snort is running correctly, you should see the captured network packets scrolling on the terminal.
By performing these verification steps, you can ensure that Snort is properly installed and ready to be used for network intrusion detection on your Linux system.
Generating Sample Network Traffic
In this section, we will explore methods to create simulated network traffic for the purpose of testing and fine-tuning your Snort installation. By generating sample network traffic, you can evaluate the effectiveness of Snort's intrusion detection capabilities without relying solely on real-world events. This allows you to proactively identify and rectify any weaknesses or false positives in your system.
One approach to generating sample network traffic is through the use of packet crafting tools. These tools enable you to create custom packets with specific characteristics and payloads, mimicking various types of network traffic. By sending these crafted packets to your Snort installation, you can observe how the system behaves and whether it accurately detects and alerts on any suspicious or malicious activity.
Another method for generating sample network traffic is to use network traffic generators. These tools generate a stream of network traffic with predefined parameters, such as packet size, protocol, and traffic rate. By configuring the traffic generator to mimic different types of network activity, you can simulate various scenarios and evaluate Snort's ability to detect and respond to different types of threats.
Additionally, network capture files, also known as packet captures, can be utilized to generate sample network traffic. These files contain recorded network traffic from past events or real-world scenarios. By replaying these capture files through Snort, you can recreate the original network traffic and assess how well the system identifies any potential security incidents.
It is important to note that while generating sample network traffic can be a useful tool for testing the functionality of Snort, it should not be the sole method of evaluating its effectiveness. Real-world network traffic and continuous monitoring are crucial for accurate and comprehensive intrusion detection.
| Advantages | Disadvantages |
|---|---|
| Provides controlled testing environment | May not accurately represent live network conditions |
| Able to simulate a wide range of network traffic scenarios | Does not account for evolving threats and attack techniques |
| Allows proactive identification and mitigation of system weaknesses | Cannot replicate the complexity and variability of real-world traffic |
Monitoring Snort Alerts
In this section, we will explore the crucial aspect of monitoring alerts generated by Snort, a powerful intrusion detection and prevention system. As Snort diligently analyzes network traffic for potential security threats, it generates alerts to notify system administrators of suspicious activities. Monitoring these alerts is essential for proactive incident response and safeguarding the network.
Understanding Alert Analysis:
Effective monitoring of Snort alerts requires a comprehensive understanding of the analysis process. System administrators need to develop the ability to discern between false positives and genuine threats. By scrutinizing the alert data and correlating it with other network events, they can better evaluate the severity and significance of each alert.
Centralized Alert Management:
An efficient way to monitor Snort alerts is by implementing a centralized alert management system. This approach enables system administrators to collect, correlate, and analyze alerts from multiple Snort sensors deployed across the network. Through a unified dashboard, they can quickly identify patterns, trends, and prioritize alerts based on their potential impact.
Real-time Alert Notifications:
Real-time alert notifications are crucial for immediate incident response. By configuring Snort to send notifications to designated personnel through various channels, such as email or SMS, system administrators can promptly address any potential security breaches. Timely alerts allow for swift action, reducing the risk of further compromise and minimizing the impact on the network.
Automating Alert Analysis:
To enhance efficiency, system administrators can leverage automation in alert analysis. Implementing custom scripts or utilizing specialized tools, they can automatically process the alerts and perform pre-defined actions based on certain criteria. Automation not only saves valuable time but also enables faster response and remediation, improving the overall security posture.
Ongoing Monitoring and Maintenance:
Monitoring Snort alerts is an ongoing process that requires regular attention and maintenance. System administrators should conduct periodic reviews of the alert logs, adjusting the detection rules based on the changing threat landscape and network environment. Additionally, they should stay updated with the latest Snort releases and security patches to ensure their system remains resilient against emerging threats.
By dedicating sufficient resources and expertise to monitoring Snort alerts, system administrators can effectively identify and respond to potential security incidents, fortifying their network's defenses and mitigating risks.
FAQ
What is Snort?
Snort is an open-source intrusion detection and prevention system that monitors network traffic for potential security threats.
Why should I set up Snort on my Linux system?
Setting up Snort on a Linux system can help enhance the security of your network by detecting and preventing potential security breaches, such as unauthorized access or attacks.
Is Snort difficult to install and configure?
No, Snort is relatively easy to install and configure on a Linux system. The step-by-step guide provides detailed instructions to help you through the process.
What are the system requirements for running Snort?
The system requirements for running Snort include a Linux operating system, a minimum of 1GB RAM, a 2GHz CPU, and sufficient storage space for log files.
Can I customize the rules in Snort?
Yes, Snort allows you to customize the rules according to your specific security needs. The step-by-step guide provides instructions on how to modify and add rules.
What is Snort and why would I want to set it up on my Linux system?
Snort is a free and open-source network intrusion detection system that can help protect your network from unauthorized access and attacks. By setting up Snort on your Linux system, you can monitor network traffic, detect suspicious activity, and take necessary actions to mitigate risks.




