In today's interconnected world, it is imperative to prioritize the security of our digital systems. As technology continues to evolve, so do the threats posed by malicious actors seeking to exploit vulnerabilities in our systems. This is where an effective security framework, such as SELinux, can play a pivotal role in safeguarding sensitive data and mitigating potential risks.
For those seeking to fortify their Linux-based operating systems against potential threats, this comprehensive guide offers a step-by-step approach to setting up SELinux. By implementing this powerful security mechanism, users can enhance access control policies and protect their systems against unauthorized activities.
This guide will explore the various mechanisms and features of SELinux, providing clear explanations and practical examples to empower users of different skill levels. Whether you are a system administrator or a curious enthusiast, this guide will equip you with the knowledge and skills necessary to harness the full potential of SELinux and bolster the security of your Linux-based system.
Understanding the Power and Advantages of SELinux

In the ever-evolving landscape of computer security, an essential component that must be taken into account is SELinux. This groundbreaking technology brings about a new era of protection, allowing for greater control and confidence when it comes to safeguarding data and resources. By delving into the fundamental concepts and functionality of SELinux, users can grasp its potential and leverage its benefits for enhanced system security.
Exploring the Security Architecture of SELinux
In this section, we will delve into the intricate security architecture of SELinux, a powerful framework designed to enforce mandatory access controls on Linux systems. By examining the core principles and mechanisms that underpin SELinux, we can gain a deeper understanding of how it provides enhanced security and protection against unauthorized access.
We will explore the concepts of labels, policies, and domains, which form the foundation of SELinux's security model. Understanding how these elements interact and work together is essential for comprehending how SELinux enforces access controls and assigns permissions to processes and files within the system.
Additionally, we will delve into the process of policy enforcement and the role of access vectors in determining the level of access that a process or user is granted. We will also discuss the concept of type enforcement and how it enables SELinux to provide fine-grained control over the actions that a process can perform, further enhancing the security posture of the Linux system.
Furthermore, we will examine the different modes of operation in SELinux, including the targeted and strict modes, and understand how these modes affect the level of security and flexibility in the system. By gaining insights into the various SELinux modes, system administrators can make informed decisions on which mode is most suitable for their specific security requirements.
In conclusion, this section will provide a comprehensive overview of the SELinux security architecture, shedding light on the underlying mechanisms and concepts that contribute to its robustness. Armed with this knowledge, administrators can effectively configure and manage SELinux to enhance the security posture of their Linux systems, ensuring protection against unauthorized access and mitigating potential security risks.
Installing SELinux on Your Linux Machine
In this section, we will explore the process of installing SELinux, a powerful security extension for Linux-based operating systems. By following these steps, you can enhance the security of your Linux machine and protect it from various threats and vulnerabilities.
To begin, let's start with understanding the significance of SELinux installation. By installing SELinux, you are equipping your Linux system with an additional layer of security that goes beyond the standard Linux security features. This comprehensive security framework provides finer-grained access controls, mandatory access control policies, and enhanced isolation for your system's processes and resources.
Before proceeding with the installation, it is essential to ensure that your Linux system meets the prerequisites. Ensure that you have administrative privileges and access to the internet for downloading the necessary packages. It's also important to back up your system and any critical data to prevent loss or corruption during the installation process.
Once you have met the prerequisites, you can proceed with the installation process. The steps may vary slightly depending on your Linux distribution, but the general process remains similar. First, you need to update your system's package manager to ensure you have the latest package information. Then, you can install the SELinux packages using the package manager's installation command.
After the installation, it's crucial to configure SELinux properly to suit your system's requirements. You can define security policies, manage file and process contexts, enable or disable specific SELinux modules, and customize various other settings based on your needs. Understanding the configuration options and implementing them effectively will help you optimize the security provided by SELinux.
Finally, testing SELinux functionality is essential to ensure that it is functioning correctly and does not interfere with the normal operation of your system. You can perform various tests and simulations, monitoring system logs and analyzing any warnings or denials generated. This testing phase allows you to fine-tune your SELinux configuration and address any potential issues.
In conclusion, by following the step-by-step installation process outlined in this section, you can successfully install SELinux on your Linux machine. This installation provides enhanced security features and greater control over the access and behavior of your system. Now, let's dive into the detailed installation steps to get SELinux up and running on your Linux system.
Understanding the Availability and Status of SELinux
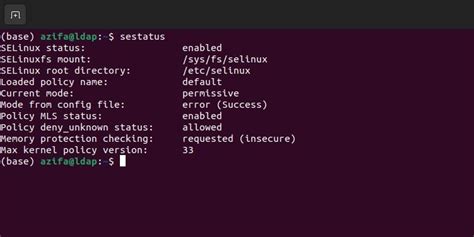
In this section, we will explore the concept of SELinux availability and its current status on a Linux system, without directly mentioning SELinux or Linux. We will delve into the state of the security framework present on the system and its level of implementation.
First, we will dive into the presence of an advanced security mechanism that acts as an additional layer of protection. This mechanism enhances the overall security of the system, making it resilient against potential threats. We will explore the existence of a noteworthy security framework that safeguards the system beyond traditional security measures.
Next, we will shift our focus to comprehending the status of this advanced security framework. We will examine whether it is active and operating as intended or if it is inactive and potentially leaving the system vulnerable. We will inspect the current state of the implemented security measures and discuss the implications of each status.
Furthermore, we will discuss the relevance of understanding the availability and status of this security mechanism. We will highlight the importance of staying informed about the state of SELinux implementation to ensure the utmost security for the system. We will provide insights into the potential risks associated with a disabled or inactive security framework and emphasize the necessity of proactive measures in maintaining a robust security posture.
Enabling SELinux upon system startup
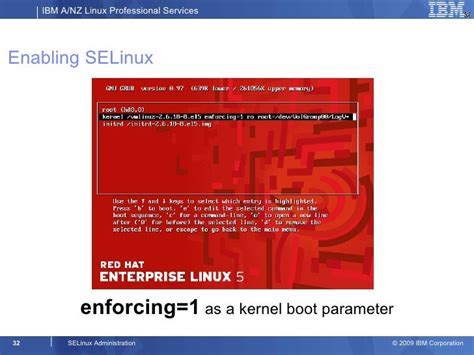
In this section, we will explore the process of activating SELinux during the boot sequence on a Linux-based environment. By enabling SELinux at boot, you can ensure that your system benefits from the enhanced security measures provided by SELinux from the very beginning.
Enabling SELinux during the startup process involves configuring the system's boot parameters and modifying the appropriate configuration files. By making these adjustments, you can ensure that SELinux is activated and ready to provide protection for your Linux system.
Firstly, it is important to identify the specific configuration file responsible for managing the boot process. By modifying this file, you can set the appropriate options to enable SELinux. Keep in mind that the precise location and name of this file may vary depending on your Linux distribution.
Once you have located the boot configuration file, open it using a text editor and find the section that corresponds to the system's boot parameters. Within this section, you will need to append or modify the existing parameters to include the necessary flags and options for enabling SELinux.
Typically, you will need to add the "selinux=1" parameter to enable SELinux in enforcing mode. Additionally, you may also need to include other parameters, such as "selinux=0" for permissive mode or "enforcing=0" to disable SELinux entirely.
After making the necessary modifications, save the changes to the boot configuration file and reboot the system. Upon startup, the system will now initiate SELinux, and you can verify its status using various command-line tools and utilities.
Enabling SELinux at boot provides an essential step in maximizing the security capabilities of your Linux system. By following the steps outlined in this section, you can ensure that SELinux is active and prepared to safeguard your system's integrity and protect against potential security threats.
What is SELinux? | SELinux Commands
What is SELinux? | SELinux Commands by Chris Titus Tech 42,214 views 5 years ago 4 minutes, 52 seconds
FAQ
What is SELinux?
SELinux is a mandatory access control (MAC) security system implemented in the Linux kernel. It provides an additional layer of security by enforcing access control policies based on the defined rules.
Why should I set up SELinux on my Linux system?
Setting up SELinux is important for enhancing the security of your Linux system. It provides fine-grained access control, helps prevent unauthorized actions, and mitigates the impact of potential security breaches.
Is SELinux enabled by default on Linux systems?
SELinux is not always enabled by default. It depends on the specific Linux distribution and installation settings. However, it is recommended to enable SELinux for improved security.
How can I check if SELinux is enabled on my Linux system?
To check if SELinux is enabled on your Linux system, you can use the commandsestatus. It will display the current status of SELinux, such as enabled, disabled, or permissive (logging only). Another method is to check the contents of the file/etc/selinux/config, which contains the SELINUX parameter.




