In today's ever-evolving digital landscape, ensuring the utmost security of our technological environments has become an indispensable priority. As the complexity and sophistication of cyber threats continue to rise, it is imperative for individuals and organizations alike to implement robust security measures to safeguard their systems, protect sensitive information, and preserve the integrity of their operational frameworks.
One such powerful tool that plays a vital role in fortifying the security posture of Linux-based platforms is the highly esteemed Security-Enhanced Linux or SELinux. Through its intelligent and dynamic enforcement of access policies, SELinux equips administrators with the means to exercise fine-grained control over processes, resources, and overall system behavior. By leveraging the versatility and command-line prowess of the Bash interface, users can navigate the intricate nuances of SELinux and bolster their Linux environments with an added layer of protection.
Within this comprehensive guide, we delve into the fundamental concepts and practical techniques required to embark on a successful journey of setting up SELinux using the Bash shell. From understanding the core principles of mandatory access controls and process labeling, to effectively configuring policies and ensuring seamless integration with existing system components, this article serves as a definitive resource for both seasoned administrators and Linux enthusiasts who are eager to elevate their security practices to unprecedented heights.
Join us as we navigate the intricacies of SELinux, and unlock the full potential of the Bash shell, empowering ourselves to establish impenetrable fortresses in our Linux ecosystems. Together, let us embrace the art of fortifying our digital landscapes through the seamless combination of cutting-edge security technologies and the limitless possibilities of command-line prowess.
Understanding the Purpose and Advantages of SELinux

When it comes to securing your Linux-based operating system, it is essential to have a comprehensive understanding of SELinux and its significance. By implementing SELinux, you can enhance the overall security and protect your system from potential threats and unauthorized access.
One of the primary objectives of SELinux is to enforce mandatory access controls, ensuring that only authorized entities can access sensitive resources within the system. This robust security mechanism goes beyond traditional discretionary access controls, providing an additional layer of protection.
SELinux employs a set of policies and rules that are tailored to meet the specific requirements of your system. These security policies define the access privileges, restrictions, and permissions for different components and processes, enabling fine-grained control over system resources.
By integrating SELinux into your Linux system, you can mitigate the risks of both known and unknown vulnerabilities. It offers a proactive approach to security, limiting the potential damage caused by any malicious or compromised applications. SELinux effectively isolates processes, preventing unauthorized actions and reducing the impact of any potential security breaches.
Furthermore, SELinux allows for better auditing capabilities, providing detailed logs and reports of system activities. This enables administrators to monitor and analyze potential security incidents, making it easier to identify and address any potential vulnerabilities or suspicious activities.
In summary, understanding the purpose and advantages of SELinux is crucial in establishing a highly secure Linux environment. By implementing SELinux, you can enforce granular access controls, mitigate security risks, and enhance the overall integrity of your system.
Introduction to Linux Fundamentals
In this section, we will explore the fundamental concepts and principles of working with Linux operating systems. Understanding these basics will provide a solid foundation for setting up and configuring SELinux using the Bash shell.
First, we will delve into the core components and architecture of Linux, gaining an understanding of its modular design and the interaction between the kernel, shell, and user space. We will also explore the various distributions of Linux and their unique features.
Next, we will discuss the file system hierarchy in Linux, including the organization of files and directories, and how permissions and ownership are managed. Understanding these concepts is crucial for effectively managing SELinux security policies.
We will also cover the essential command-line tools and utilities in Linux, such as the package manager, text editors, network configuration, and process management. These tools play a crucial role in setting up and maintaining SELinux in a Linux system.
Additionally, we will touch upon the role of users and groups in Linux, including user account management, group permissions, and authentication mechanisms. This knowledge will be essential for configuring SELinux access controls.
Lastly, we will discuss the importance of regular system maintenance and security practices, including software updates, backup strategies, and network security measures. These practices ensure the overall stability and security of a Linux system, including SELinux configurations.
Exploring Operating Systems and Distributions in the Linux Environment

Delving into the realm of computer operating systems is a fascinating journey that allows users to discover a diverse array of Linux distributions and operating systems. These unique variations provide a multitude of options for users, each imbued with its own set of features, functionalities, and strengths. Analyzing the various distributions and operating systems within the Linux ecosystem helps users gain a deeper understanding of the vast possibilities available, enabling them to make informed decisions based on their specific needs and preferences.
Distribution Diversity:
Linux distributions, the different flavors of Linux operating systems, are characterized by their varied packaging of software, range of supported hardware, and distinctive graphical user interfaces. These distributions, often referred to as distros, cater to different user requirements, such as general-purpose computing, multimedia production, server administration, or security-focused applications. From Ubuntu and Debian to Fedora and Arch Linux, each distribution offers a unique user experience and embraces a specific philosophy, ultimately shaping the computing environment.
Operating System Exploration:
Expanding beyond Linux distributions, the world of Linux operating systems encompasses a broader scope that includes UNIX-based systems such as FreeBSD and OpenBSD. UNIX-like operating systems share similar principles and foundational concepts with Linux but possess their own distinct characteristics. These alternative operating systems provide users with a deeper understanding of the core principles and architecture upon which Linux is built, enhancing their grasp of the broader ecosystem and widening their knowledge base.
Customization and Adaptability:
A key advantage of exploring the vast array of Linux distributions and operating systems lies in their inherent flexibility and customizable nature. Users have the opportunity to tailor their computing environments to suit their specific desires, preferences, and workflows, ultimately creating a highly personalized user experience. Whether it is selecting a lightweight distribution for resource-constrained systems or opting for a robust distribution with extensive security features, the ability to adapt and customize provides Linux users with unparalleled control over their operating systems.
Evaluation and Selection:
Engaging in the exploration and evaluation of various Linux distributions and operating systems allows users to discern their strengths and weaknesses, aiding in the selection of the most appropriate system for their individual needs. By thoroughly researching and testing different options, users can identify the distribution or operating system that aligns with their goals and requirements. This exploration not only enhances knowledge but also empowers users to make informed decisions and maximize their computing experience within the vast Linux ecosystem.
In conclusion, delving into the world of Linux distributions and operating systems provides users with a captivating opportunity to explore the diversity, customization options, and strengths within the Linux ecosystem. Through thorough evaluation and selection, users can discover operating systems that align with their specific needs, enhancing their overall computing experience.
Introduction to Installing SELinux on a Linux System
When it comes to enhancing security on your Linux system, one powerful tool that you can consider is SELinux. This article will guide you through the process of installing SELinux on your Linux system, allowing you to bolster the protection of your valuable data and resources.
- Benefits of SELinux installation
- Understanding the role of SELinux in Linux security
- Prerequisites for installing SELinux
- Step-by-step guide to installing SELinux
- Verifying the successful installation of SELinux
By the end of this article, you will have a clear understanding of the importance of SELinux installation and the necessary steps to take in order to install SELinux on your Linux system effectively.
Step-by-Step Tutorial for Implementation
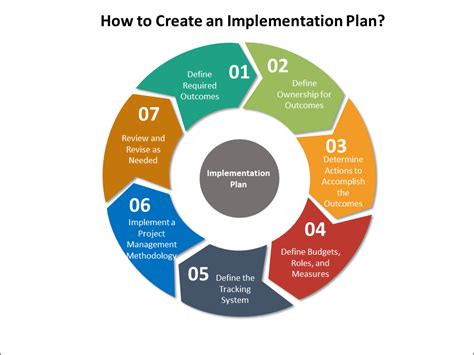
Building a comprehensive security setup for your Linux environment involves a range of steps. This guide will take you through each stage of the installation process, ensuring that you have a clear understanding of the steps involved in setting up SELinux using the Bash shell. By following this step-by-step tutorial, you will be able to successfully implement SELinux in your Linux system, providing enhanced security and protection for your applications and data.
- 1. Preparing the Environment
- 2. Configuring SELinux Policies
- 3. Modifying File Contexts
- 4. Troubleshooting Common Issues
- 5. Verifying SELinux Status
- 6. Enabling or Disabling SELinux
Throughout this guide, you will learn how to effectively execute each step using the Bash shell, making the setup process easier to understand and implement. By the end of this tutorial, you will have successfully installed SELinux in your Linux system, empowering you to confidently enhance the security mechanisms of your environment.
Configuring Security Policies for Enhanced System Protection
When it comes to fortifying the security of your Linux environment, the careful configuration of security policies is of utmost importance. In this section, we will delve into the intricacies of customizing and adapting SELinux policies, ensuring the highest level of protection against potential threats.
Customizing SELinux for Tailored Security Needs
When it comes to enhancing the security of your Linux environment, a one-size-fits-all approach may not always be sufficient. This section explores how to customize SELinux to effectively meet specific security requirements, without compromising the overall integrity and functionality of the system.
- Understanding the Role-Based Access Control (RBAC) Model
- Defining Your Security Objectives
- Identifying and Managing the Mandatory Access Control Policies
- Configuring SELinux Rules and Constraints
- Implementing Custom Security Contexts
- Creating and Modifying SELinux Modules
- Integration with Other Security Mechanisms
- Monitoring and Auditing Customized SELinux Settings
By diving into the intricacies of SELinux customization, administrators can tailor their security measures to tackle specific threats and vulnerabilities. This empowers organizations to build a robust and adaptive security framework, aligning SELinux policies with their unique security requirements.
Managing Access Control in a Secure Environment
In this section, we will explore the various aspects of managing access control in a secure environment. By carefully defining users and roles within the system, we can ensure that only authorized individuals have access to sensitive resources and information.
We will discuss how to create and manage users, define roles and their associated permissions, and assign these roles to specific users. By effectively managing SELinux access control, we can enhance the security of our Linux system, protect important data, and prevent unauthorized access or modifications.
Additionally, we will explore the concept of least privilege, which involves granting users only the permissions necessary for their specific tasks. This approach minimizes the risk of accidental or intentional misuse of privileges and helps to mitigate potential security vulnerabilities.
Furthermore, we will cover the importance of regularly reviewing and updating access controls to adapt to changing system requirements, user roles, and security policies. By periodically assessing and adjusting access permissions, we can maintain the integrity and confidentiality of our system and ensure it remains resistant to potential security breaches.
Managing Access Levels and Permissions
In this section, we will explore the process of assigning access levels and permissions within the environment. By implementing proper access controls, individuals can define the specific actions and operations permitted for different users, files, and processes. Through the establishment of access levels and permissions, organizations can ensure the security and integrity of their systems and data.
- Understanding Access Levels
- Defining User Permissions
- Managing File and Directory Access
- Implementing Process Restrictions
- Granting Special Privileges
Access levels refer to the different levels of access that can be granted to users, processes, and resources within the system. By defining access levels based on the principle of least privilege, organizations can limit the potential damage that can be caused by individual users or processes.
Once access levels are established, it is crucial to define user permissions accurately. User permissions determine the specific actions that a user can perform on files, directories, and other resources. By granting appropriate permissions, organizations can ensure that users have the necessary access to perform their tasks without compromising security.
In addition to user permissions, it is essential to manage file and directory access. By carefully controlling the read, write, and execute permissions on files and directories, organizations can mitigate the risk of unauthorized access or modification. Implementing proper access controls can help safeguard sensitive data and prevent unintended data breaches.
Furthermore, it is necessary to implement process restrictions within the system. By applying restrictions on the actions that individual processes can perform, organizations can prevent malicious processes from causing harm or compromising system integrity. These restrictions ensure that processes only have access to the necessary resources and actions required for their intended purpose.
Lastly, special privileges such as administrative access or specific user capabilities may need to be granted in some cases. Organizations should carefully evaluate and limit the granting of such privileges to only trusted individuals or processes. Special privileges should be granted and managed with caution to avoid potential security risks.
By effectively managing access levels and permissions within the system, organizations can maintain a secure and controlled environment, reducing the risk of unauthorized access, data breaches, and system vulnerabilities.
Troubleshooting Issues with SELinux: Overcoming Common Obstacles
In the pursuit of establishing a secure environment for your Linux-based operating system, the implementation of SELinux undoubtedly plays a crucial role. However, just like any other configuration, it is not immune to challenges that may arise during the setup process. This section aims to guide you through the troubleshooting steps to overcome the obstacles encountered while working with SELinux.
When delving into the realm of SELinux, it becomes imperative to address the potential roadblocks that might impede the smooth functioning of the system. Whether it be permission denials, conflicting policies, or misconfigurations, having a comprehensive understanding of troubleshooting techniques is vital in order to ensure a robust SELinux deployment.
One of the foremost sources of SELinux-related issues is inadequate access permissions. Sometimes, applications or services may encounter permission errors due to the tight security controls enforced by SELinux. In these cases, it is crucial to identify the specific access requirements and configure SELinux policies accordingly to grant the necessary permissions without compromising the overall system security.
Conflicting SELinux policies can also impede the normal operation of the system. When multiple policies clash or overlap, it can result in error messages, permission denials, or even system instability. To address this, it is essential to carefully review and modify the existing policies, ensuring that they align with your specific system requirements and do not conflict with one another.
Additionally, misconfigurations within the SELinux configuration files can lead to unexpected behavior or outright failures. In such cases, examining the configuration files, identifying any errors or inconsistencies, and making the necessary adjustments can help resolve the issue and restore the proper functioning of SELinux.
Remember that SELinux is a powerful security mechanism designed to provide granular access controls to enhance the security of your Linux system. However, it requires meticulous attention to detail and a proactive approach to resolve any issues that may arise during its setup. By following the troubleshooting techniques outlined here, you can effectively overcome SELinux hurdles and ensure the robustness of your system's security.
Addressing Common Issues and Resolving Them

When implementing SELinux in a Linux environment using the Bash shell, there may be certain challenges that arise. This section will discuss some common problems that users might encounter and provide effective solutions to overcome them.
| Problem | Solution |
|---|---|
| Access denied errors when accessing certain files or directories | Review the SELinux security context for the file or directory and modify it if necessary using the chcon command. Ensure that the appropriate SELinux boolean or policy is also enabled. |
| Applications or services failing to start due to SELinux restrictions | Investigate the denial messages in the SELinux logs (/var/log/audit/audit.log) and use tools like audit2allow to generate custom SELinux policies to allow the necessary actions. Apply the generated policy using semodule. |
| SELinux blocking network connection or access to specific ports | Check the SELinux labels for network-related files, such as configuration files or binaries. Adjust the labels using chcon or create SELinux modules using semodule to allow the desired network connectivity. |
| Difficulties in transitioning between SELinux modes | Understand the differences between SELinux modes (enforcing, permissive, and disabled) and the implications for system security. Use appropriate commands like setenforce, semanage, or getsebool to transition between modes and manage SELinux policies. |
By being aware of these common problems and utilizing the suggested solutions, users can effectively troubleshoot and overcome SELinux-related challenges, ensuring the security and integrity of their Linux systems.
[MOVIES] [/MOVIES] [/MOVIES_ENABLED]FAQ
What is SELinux?
SELinux (Security-Enhanced Linux) is a security mechanism implemented in Linux operating systems that provides a highly flexible and customizable access control framework.
How can I set up SELinux in a Linux system?
You can set up SELinux in a Linux system using the Bash shell by installing the necessary packages, configuring SELinux policies, and enabling it in the system's configuration.
Why should I consider setting up SELinux in my Linux system?
Setting up SELinux can greatly enhance the security of your Linux system by adding an additional layer of access control and protecting against various exploits and vulnerabilities.
Is it difficult to set up SELinux using the Bash shell?
Setting up SELinux using the Bash shell can be a bit complex for beginners, but with proper documentation and understanding of the configurations, it is feasible for most users.
Are there any potential drawbacks or limitations of using SELinux?
While SELinux provides enhanced security, it may also introduce additional complexity, making certain system configurations more challenging. Additionally, misconfigurations may lead to unintended consequences and restricted access to certain resources.
What is SELinux and why is it important in Linux systems?
SELinux (Security-Enhanced Linux) is a security mechanism built into the Linux kernel. It provides access control policies and mandatory access controls, which helps prevent unauthorized access to sensitive resources and reduces the potential damage caused by malicious software. SELinux is important in Linux systems because it adds an extra layer of security and helps protect against various cyber threats.




