In today's increasingly interconnected world, the ability to connect and manage your systems remotely has become essential. Whether you're a system administrator responsible for maintaining multiple servers or a tech-savvy enthusiast with a passion for tinkering, the need to access your Linux system from anywhere cannot be understated.
This article will explore strategies and approaches to establish seamless connectivity to your Linux environment without physically being present. By leveraging the power of remote connections, you can easily administer your system, troubleshoot issues, and perform various tasks remotely, all while enhancing overall productivity and convenience.
Throughout this comprehensive guide, we will delve into various techniques and tools that will empower you to gain remote control over your Linux system effortlessly. We will explore methods that allow you to securely access your system from across the globe, using remote login protocols and robust encryption. Additionally, we will discuss how to set up and configure remote access with diverse alternatives, such as Secure Shell (SSH) and Virtual Network Computing (VNC), to tailor the solution to your specific requirements and preferences.
By the end of this article, you will have a profound understanding of the different options available for establishing remote access, enabling you to choose the most suitable approach for your Linux system. Whether you're looking to connect to a personal Linux server or manage a network of enterprise-grade machines, this guide will equip you with the knowledge and skills necessary to effortlessly establish and maintain remote access.
Understanding the Significance of Distal Connectivity
The ability to connect to a remote system and work on it from a distinct location has become increasingly vital in today's digital era. The convenience and flexibility offered by remote access cannot be understated, as it allows users to manage and manipulate essential data and resources without being physically present at the same location as the server. This section aims to explore the importance of establishing a secure and efficient channel that enables remote control and administration of systems, thereby enhancing productivity and facilitating collaboration.
Enhanced Productivity:
Remote access empowers users with the ability to perform various tasks and carry out important operations regardless of their geographical location. This freedom allows for increased productivity as it eliminates the need for physical presence at the server's location, saving time and costs associated with travel. Moreover, it enables swift troubleshooting, maintenance, and updates, minimizing downtime and ensuring seamless operations.
Flexibility and Mobility:
The flexibility offered by remote access allows users to work from different devices, including desktops, laptops, tablets, or even smartphones. This mobility provides convenience and enables professionals to access critical data and perform necessary tasks, regardless of their location, ensuring efficient workflow continuity.
Facilitates Collaboration:
Remote access fosters collaboration among team members, regardless of where they are located. It allows multiple users to connect to the same server simultaneously, enabling real-time collaboration, efficient sharing of resources, and seamless communication. This not only improves efficiency but also promotes teamwork and enables remote teams to work together effectively.
Security and Control:
Establishing a secure remote access connection is crucial to safeguard sensitive information and prevent unauthorized access. By implementing robust authentication and encryption measures, organizations can maintain control over who can access their systems remotely, ensuring data confidentiality, integrity, and compliance with security regulations.
In conclusion, understanding the significance of remote connectivity emphasizes the need for a secure and efficient remote access setup. By leveraging the benefits of enhanced productivity, flexibility, collaboration, and security, individuals and organizations can unlock the full potential of distal connectivity.
Choosing the ideal protocol for remote connectivity
When establishing a secure connection to a distant operating system, it is essential to select the most suitable protocol that meets your specific requirements. By opting for the appropriate remote access protocol, you can guarantee efficient and reliable communication with your target system, enhancing productivity and ensuring a seamless user experience.
| Protocol | Description | Advantages | Disadvantages |
|---|---|---|---|
| RDP (Remote Desktop Protocol) | RDP, developed by Microsoft, is designed for Windows-based systems, offering a graphical interface for remote access. | - Provides a native Windows environment for remote administration. - Supports multimedia and audio redirection. - Allows remote printing and file sharing. | - Restricted compatibility with non-Windows operating systems. - Vulnerable to security threats if not properly configured. |
| SSH (Secure Shell) | SSH is a cryptographic network protocol that offers secure and encrypted communication between two systems, allowing command-line access. | - Provides strong encryption and authentication mechanisms. - Granular control over access permissions. - Supports tunneling for secure data transfer. | - Limited graphical capabilities compared to other protocols. - May require additional setup for file transfers. |
| VNC (Virtual Network Computing) | VNC enables remote access to the desktop environment of a system, allowing users to view and control the graphical interface remotely. | - Cross-platform compatibility. - Suitable for accessing Linux, Windows, and macOS systems. - Allows collaboration and screen sharing. | - May experience latency or performance issues over slow network connections. - Lacks built-in encryption, requiring additional security measures. |
| HTTPS (Hypertext Transfer Protocol Secure) | HTTPS, commonly used for web browsing, can also serve as a remote access protocol by providing secure and encrypted communication through a web browser interface. | - Utilizes standard web technologies. - Firewall-friendly communication. - Supports remote access from any device with a web browser. | - Requires a web server setup for remote access. - Limited interactivity compared to other protocols. |
Choosing the appropriate remote access protocol relies on understanding the unique aspects and requirements of your environment. Evaluating factors such as compatibility, security, graphical capabilities, and ease of implementation will help you make an informed decision and establish a reliable remote connection to your Linux server or any other operating system.
Configuring Secure Shell (SSH) for Remote Administration

The purpose of this section is to guide you through the process of installing and setting up the Secure Shell (SSH) protocol on your Linux server. SSH provides a secure and encrypted method for remote access and administration of your server, allowing you to securely connect and manage your system from any location.
Before we dive into the installation process, it is important to understand the benefits of using SSH for remote administration. With SSH, you can establish a secure connection between your local machine and the server, ensuring that your data transmission is protected from unauthorized access. This ensures the confidentiality and integrity of your administrative tasks, as well as helps prevent any malicious attacks or data breaches.
To install and configure SSH on your Linux server, follow the steps outlined below:
Step 1: Check if SSH is already installed on your server by running the command "which ssh". If the command returns a path, it means SSH is already installed. If not, proceed to the next step. |
Step 2: Install SSH by using the package manager of your Linux distribution. For example, if you are using Ubuntu, run the command "sudo apt-get install openssh-server". |
Step 3: Configure SSH by modifying the main configuration file located at "/etc/ssh/sshd_config". This file contains various settings that control the behavior of the SSH server. Some important settings include port number, authentication methods, and allowed user groups. |
Step 4: Restart the SSH service to apply the changes made in the configuration file. This can be done by running the command "sudo service sshd restart" or "sudo systemctl restart sshd", depending on your Linux distribution. |
Step 5: Verify that SSH is running and accessible by attempting to connect to your server using an SSH client. Use the command "ssh username@server_ip_address" and enter the password when prompted. If you are able to successfully connect, SSH is now properly installed and configured on your Linux server. |
By following these steps, you will have successfully installed and configured SSH on your Linux server, allowing secure remote access and administration. Make sure to keep your SSH configuration updated and regularly monitor your logs for any suspicious activity to ensure the ongoing security of your server.
Generating and managing SSH keys for secure connectivity
In this section, we will explore the process of creating and handling SSH keys to ensure secure and encrypted communication between systems. By utilizing SSH keys, users can authenticate themselves and establish a secure connection with a Linux-based server without relying on traditional password-based authentication methods.
SSH keys play a pivotal role in enhancing security by providing a more secure alternative to passwords. This method involves generating a pair of cryptographic keys – a public key and a private key. The public key is shared with the server, while the private key remains securely stored on the user's local system.
Using these keys, the server can verify the authenticity of the user attempting to establish a connection. The private key, protected with a strong passphrase, adds an extra layer of security, preventing unauthorized access even if the public key is compromised.
Managing SSH keys involves generating the key pair, securely storing the private key, and distributing the public key to the Linux server. This can be accomplished using various tools and utilities, including the widely used OpenSSH package.
| Advantages of SSH Keys | Best Practices for Managing SSH Keys |
|---|---|
| Enhanced security through public-key cryptography | Regularly rotate and update SSH keys |
| No need to remember or transmit passwords | Restrict SSH access to authorized users only |
| Protection against brute-force attacks | Securely store and backup private keys |
By following the best practices for managing SSH keys, system administrators can significantly mitigate the risks associated with unauthorized access and protect the confidentiality and integrity of their Linux servers.
Securing Remote Connection: Setting up Firewall Rules
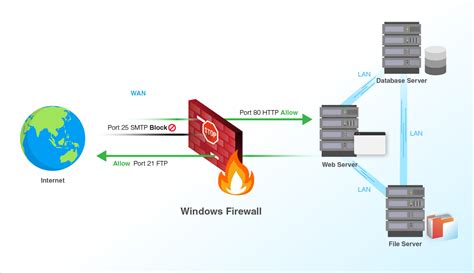
Ensuring a secure and reliable means of accessing a remote Linux-based system is an essential aspect of server administration. One crucial step in this process is configuring firewall rules to protect the system from unauthorized access or malicious activities. In this section, we will explore the necessary measures and considerations to establish a robust firewall configuration for remote connectivity.
Understanding Firewall Rules:
Firewall rules act as a virtual barrier, determining what traffic is allowed to enter or leave a networked device. By carefully designing and implementing firewall rules, administrators can define the specific protocols, ports, and IP addresses that are permitted access to the system.
Creating an Access Policy:
Before configuring firewall rules, it is crucial to establish an access policy that aligns with the organization's security requirements. This policy should define the scope of remote access, including the individuals or systems that are authorized to connect, the types of services or applications accessible, and any restrictions or limitations imposed.
Identifying Allowed Services:
After establishing an access policy, the next step is to identify the services that will be made available remotely. This may include SSH (Secure Shell) for terminal access, FTP (File Transfer Protocol) for file management, or HTTP(S) (Hypertext Transfer Protocol) for web-based applications. Each service will require appropriate firewall rules to allow incoming connections while maintaining security.
Defining Source IP Addresses:
In order to restrict remote access to authorized individuals or systems, it is essential to define the source IP addresses that are allowed to establish a connection. This can be achieved by specifying the IP ranges, individual IP addresses, or using subnet masks for more flexibility.
Configuring Port Forwarding:
In some cases, remote access may require the use of non-standard ports, especially when multiple services are hosted on the same system. Configuring port forwarding rules within the firewall will enable traffic to be directed to the appropriate service or application based on the port number.
Enabling Logging and Monitoring:
To maintain visibility and detect any suspicious or unauthorized activities, it is essential to enable firewall logging and monitoring. By reviewing firewall logs, administrators can identify potential security breaches, unusual traffic patterns, or unauthorized connection attempts, allowing for timely and effective response measures.
By carefully configuring firewall rules specific to remote access requirements, administrators can significantly enhance the security and control of Linux servers, minimizing the risk of unauthorized access or potential threats.
Enabling remote connectivity through port forwarding
In the realm of establishing a connection from afar to a Linux-based system, a crucial measure to undertake involves the activation of remote accessibility via port forwarding. By implementing this approach, one can facilitate the ability to connect and interact with a distant system using alternative ports and routes, thus circumventing the necessity to directly access the primary server. This article delves into the concept of enabling remote connectivity through port forwarding and provides an overview of the steps involved in the process.
Understanding the concept of port forwarding
Port forwarding, also known as port mapping, entails the redirection of network traffic from one port to another, enabling data to flow through alternate communication channels. This technique allows for the creation of a seamless pathway between the remote device and the Linux server by diverting incoming requests to access specific services or applications. By configuring port forwarding, users can establish a secure and reliable means of remote access to their Linux-based system.
Examining the benefits of port forwarding
The utilization of port forwarding bestows numerous advantages upon users seeking remote connectivity. Firstly, this method enhances security by shielding the primary server from direct external access, thereby reducing the risk of unauthorized breaches. Port forwarding also enables users to access services and applications on their Linux server without modifying any existing network settings, simplifying the process and minimizing disruption to other devices and connections. Furthermore, by leveraging alternate ports and routes, port forwarding ensures greater flexibility and versatility in establishing remote access to the Linux server.
Implementing port forwarding for remote access
The process of enabling remote connectivity through port forwarding generally involves several distinct steps. These steps encompass identifying the specific service or application that necessitates remote access, configuring the router or gateway settings to allow port forwarding, mapping and defining the rules for incoming traffic, and testing the connectivity to ensure successful remote access. By meticulously following these steps, users can effectively enable and utilize port forwarding to establish seamless remote access to their Linux server.
Conclusion
In conclusion, enabling remote access through port forwarding presents an efficient and secure method of establishing connectivity to a Linux server from a remote location. This article has explored the concept of port forwarding, examining its benefits and providing an overview of the implementation process. By familiarizing oneself with this technique and carefully following the necessary steps, users can navigate the realm of remote connectivity and leverage the capabilities of their Linux-based system with ease and convenience.
Securing Remote Connectivity with VPN
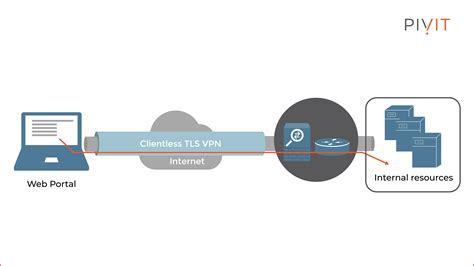
Ensuring secure and reliable remote connectivity to a Linux-based system is of utmost importance for businesses and individuals. One effective approach to achieve this is through the use of a Virtual Private Network (VPN). By implementing a VPN, users can establish an encrypted connection over the internet, enhancing privacy, data integrity, and protecting sensitive information from unauthorized access.
| Benefits of VPN for Remote Access |
|---|
| Enhanced Security |
| Increased Privacy |
| Data Encryption |
| Access Control |
| Network Anonymity |
By utilizing a VPN, remote users can securely connect to their Linux systems from anywhere in the world, ensuring that sensitive data transmitted between the user's device and the server remains secure. VPNs provide a secure tunnel that protects information from potential eavesdropping, thereby minimizing the risk of unauthorized access to confidential data.
Furthermore, VPNs offer increased privacy by masking the actual IP address of the connected device. This prevents websites, online services, and attackers from tracking and identifying the user's real location, adding an extra layer of anonymity and protection to the remote access process.
In addition to security and privacy benefits, VPNs utilize data encryption techniques to safeguard transmitted data from interceptions or tampering. Encryption ensures that even if the data were to be intercepted, it remains unreadable and unintelligible to unauthorized individuals, mitigating the risk of data breaches and theft.
Another advantage of using VPNs for remote access is the ability to implement access control measures. VPNs allow administrators to define and enforce strict access policies, ensuring that only authorized users can connect to the Linux server. By implementing access control mechanisms such as user authentication and device certification, VPNs add an extra layer of protection against unauthorized access attempts.
In conclusion, the use of a VPN for secure remote access to a Linux server is a robust solution that protects sensitive data, enhances privacy, and provides a secure connection for remote users. By leveraging the benefits of VPN technology, businesses and individuals can establish a secure and encrypted communication channel, establishing remote access capabilities without compromising security.
Enhancing Security with Two-Factor Authentication
In today's digital landscape, securing access to sensitive data is of paramount importance. One effective method to fortify your system's security is through the implementation of two-factor authentication. By requiring users to provide two separate forms of identification before granting access, two-factor authentication adds an extra layer of protection against unauthorized access.
An increasing number of security breaches and cyber attacks have highlighted the vulnerabilities of traditional username and password authentication systems. These can be compromised through various means, such as phishing attacks, brute force attacks, or stolen credentials. However, by integrating two-factor authentication, even if one factor (such as a password) is compromised, the second factor (typically a unique code sent to a mobile device) serves as an additional barrier, greatly reducing the risk of unauthorized access.
Implementing two-factor authentication on your Linux server provides an added level of security for remote users seeking access. This method requires users to provide not only a username and password, but also a separate verification code generated by a trusted authentication app or received via SMS. By utilizing this additional authentication factor, even if an attacker gains access to valid login credentials, they would still be unable to access the server without the secondary verification code.
- Step 1: Choose a reliable two-factor authentication method
- Step 2: Install and configure the necessary software or plugin
- Step 3: Generate and link the initial set of verification codes
- Step 4: Communicate the setup process to remote users
- Step 5: Test the two-factor authentication system thoroughly
While two-factor authentication undoubtedly enhances security, it is important to select a method that strikes the right balance between usability and robustness. Consider factors such as ease of setup, compatibility with your existing systems, and the reliability of the authentication app or service. By following the provided steps, you can successfully set up two-factor authentication on your Linux server and significantly fortify the security of remote access.
Monitoring remote connections and managing user permissions
In this section, we will discuss the important aspects of keeping track of and controlling the connections to your Linux-based system from remote locations. Additionally, we will explore the strategies and techniques for managing user privileges and permissions effectively.
Tracking and monitoring remote connections
It is crucial to have a reliable system in place to monitor and track the remote connections to your Linux server. By implementing robust monitoring solutions, you can ensure the integrity and security of your system. These solutions provide real-time visibility into incoming and outgoing connections, allowing you to identify any unauthorized access attempts or suspicious activities.
Utilizing advanced logging mechanisms enables comprehensive tracking capabilities, generating detailed logs of connection attempts, successful logins, and failed authentication attempts. By regularly reviewing these logs, you can promptly detect and respond to any potential security threats.
Managing user privileges and permissions
Effectively managing user privileges and permissions is essential for maintaining the security and integrity of your Linux server. By granting appropriate access rights to users, you can ensure that they have the necessary permissions to perform their tasks while preventing unauthorized access or unintended modifications.
Implementing the principle of least privilege ensures that users only have access to the resources and actions required for their specific roles or responsibilities. By granting minimal privileges, you minimize the potential for accidental or deliberate misuse of system resources.
Regularly reviewing and auditing user permissions is crucial to maintaining a secure environment. By periodically assessing user privileges and removing unnecessary access rights, you can reduce the risk of unauthorized actions or data breaches.
By implementing robust monitoring practices and effectively managing user permissions, you can enhance the security and control of your Linux server, ensuring it remains accessible only to authorized individuals and minimizing the potential risks associated with remote access.
Troubleshooting common issues with remote connectivity to Linux host machines
In this section, we will explore the common challenges that arise when attempting to establish a remote connection with Linux-based servers. We will identify potential obstacles that users may encounter and provide practical solutions for addressing these issues.
Network connectivity problems:
One of the most prevalent issues that can impede remote access to a Linux server is related to network connectivity. Users may encounter difficulties establishing a connection due to firewall restrictions, misconfigured networking settings, or inadequate network bandwidth. To overcome these challenges, it is crucial to verify firewall rules, ensure proper network configuration, and optimize network resources if necessary.
Authentication failures:
Another common stumbling block when attempting remote access to a Linux server involves authentication failures. This can manifest as incorrect login credentials, faulty SSH key configurations, or disabled user accounts. Troubleshooting authentication issues involves verifying the accuracy of login details, checking SSH key configurations, and ensuring that the user account is active and not locked.
Port forwarding concerns:
Port forwarding is often required to establish a remote connection to a Linux server. However, issues may arise if the necessary ports are not properly forwarded in routers or firewalls. Troubleshooting port forwarding problems involves checking router and firewall settings, ensuring the correct ports are open and forwarded, and validating that the Linux server's network interface is correctly configured.
Software compatibility issues:
Certain software applications utilized for remote access may exhibit compatibility issues with Linux servers. This can result in connection failures, erratic behavior, or limited functionality. Troubleshooting software compatibility problems involves verifying software versions, checking for known compatibility issues, and exploring alternative remote access applications if necessary.
Performance degradation:
Remote access to a Linux server may suffer from performance degradation, leading to slow response times or laggy connections. This can be caused by insufficient system resources, network congestion, or high server load. To enhance performance, troubleshooting measures may include optimizing system resources, conducting network analysis, and load balancing if applicable.
Security considerations:
When setting up remote access to a Linux server, it is paramount to prioritize security. Common issues may involve weak passwords, inadequate encryption protocols, or compromised network security. Troubleshooting security-related problems includes enforcing secure password policies, implementing strong encryption methods, and regularly auditing system security measures.
Conclusion:
By proactively addressing the above-mentioned troubleshootings, users will be able to overcome common issues encountered during remote access to Linux servers. Understanding and troubleshooting these challenges effectively will facilitate a seamless and secure remote connectivity experience.
[MOVIES] [/MOVIES] [/MOVIES_ENABLED]FAQ
What is remote access to a Linux server?
Remote access to a Linux server refers to the ability to connect to and manage the server from a remote location, using a computer or device connected to the internet.
Why would I need remote access to a Linux server?
Remote access allows you to manage your Linux server from any location. It is especially useful if you need to make changes, troubleshoot issues, or perform administrative tasks without physically being present at the server's location.
What are the different ways to set up remote access to a Linux server?
There are several methods to set up remote access to a Linux server, including SSH (Secure Shell) protocol, VNC (Virtual Network Computing), and web-based control panels like cPanel or Plesk.
How do I enable SSH for remote access to my Linux server?
To enable SSH, you need to install the OpenSSH server on your Linux server. You can do this by running the command 'sudo apt-get install openssh-server' (for Ubuntu/Debian) or 'sudo yum install openssh-server' (for CentOS/RHEL). Once installed, SSH will allow you to remotely connect to your server via a secure command-line interface.
Are there any security considerations when setting up remote access to a Linux server?
Yes, security is a crucial aspect when setting up remote access to a Linux server. It is recommended to use strong passwords or SSH key pairs for authentication, disable SSH root login, and regularly update your server's software to patch any vulnerabilities.
What is the purpose of installing an OpenSSH server to set up remote access?
The purpose of installing an OpenSSH server on the Linux server is to enable secure remote access. OpenSSH provides a secure way to communicate and transfer data between the client and the server over an encrypted connection. It is the most common and widely used method for remote access to Linux servers as it utilizes strong cryptographic algorithms to protect the data transmission. By installing and configuring the OpenSSH server, you can securely connect to the Linux server from a remote location using an SSH client.




