In this era of technological advancements, the need for seamless and secure access to files and resources on multiple devices has become an indispensable part of our daily lives. To achieve this, the establishment of remote connectivity emerges as a key solution, paving the way for effortless accessibility to networks and applications from any geographical location.
In today's digital landscape, the importance of safeguarding sensitive information cannot be overstated. As such, utilizing the power of encrypted communication proves essential in ensuring the privacy and integrity of the data being transmitted, thereby shielding it from nefarious actors seeking unauthorized access.
Within the realm of network administration, the process of configuring remote access via HTTPS emerges as a vital component, enabling users to securely connect to remote systems using a web browser. By engaging in this seamless interaction, individuals gain the ability to manage files, control systems, and administer applications remotely, without compromising the security of the network or the data it holds.
Throughout this comprehensive guide, we will delve into the intricacies of establishing remote access using HTTPS, exploring the fundamental principles, step-by-step instructions, and best practices. By navigating through this informative journey, you will acquire the necessary insights and skills to configure and harness a robust remote connection, bolstered by the impenetrable shield of encrypted communication.
Securing Remote Connectivity in Windows with Encrypted Web Protocol
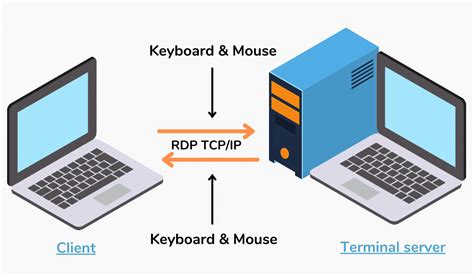
In today's digital age, ensuring secure and efficient remote connectivity to your Windows systems is of utmost importance. One effective way to achieve this is by setting up remote access using HTTPS, the encrypted web protocol. By utilizing HTTPS, you can establish a secure connection between remote users and your Windows environment, safeguarding sensitive data and minimizing the risk of unauthorized access.
Understanding the Significance of Remote Connectivity
In today's technologically advanced world, the ability to establish remote connections has become vital for efficient and convenient work and communication. This section aims to highlight the profound importance of remote access and the significant impact it has on modern work environments.
1. Enhanced Productivity: Remote access promotes increased productivity as it allows individuals to work from any location at any time. By eliminating the need for physical presence, employees gain the flexibility to optimize their work schedules, resulting in higher efficiency and output.
2. Efficient Collaboration: Remote connectivity fosters seamless collaboration among team members who may be physically located far apart. With remote access, individuals can securely share files, conduct online meetings, and collaborate on projects in real-time, promoting effective teamwork and knowledge exchange.
3. Expanded Business Reach: Remote access empowers businesses to expand their reach beyond geographical boundaries. By enabling employees or clients to connect remotely, companies can tap into a global talent pool, access new markets, and provide services to customers regardless of their location.
4. Cost and Time Savings: Implementing remote access solutions can result in significant cost savings for businesses. Companies can reduce expenses related to office spaces, commuting, and utilities. Additionally, with remote connectivity, individuals can save time by avoiding long commutes, resulting in a better work-life balance.
5. Increased Flexibility: Remote access provides individuals with the flexibility to manage their work-life balance effectively. It allows parents to spend more time with their families, offers individuals with disabilities or health concerns the opportunity to work comfortably from home, and enables professionals to pursue location-independent careers.
6. Disaster Recovery and Business Continuity: Remote access plays a vital role in ensuring business continuity during unforeseen circumstances such as natural disasters or emergencies. By enabling remote work, organizations can continue their operations even when physical office spaces are inaccessible or compromised.
Overall, understanding the significance of remote connectivity highlights its potential to revolutionize work environments, enhance productivity, and enable individuals and businesses to thrive in this digital era.
Configuring Your System for Remote Connectivity
To establish a secure and seamless connection from a remote location, it is essential to configure your Windows system appropriately. This section will delve into the necessary steps and settings that need to be implemented to enable efficient remote access, ensuring a smooth and reliable experience.
Step 1: Fine-tuning your Firewall Settings
To safeguard your system against unauthorized access, it is crucial to configure your firewall settings. By allowing specific incoming connections while blocking others, you can maintain a secure environment for remote access. Ensure that your firewall permits incoming connections through the designated ports required for remote connectivity.
Step 2: Enabling Remote Desktop
Enable the Remote Desktop feature on your Windows system to facilitate remote access. This feature allows you to control your system via a remote device, granting you access to your files, applications, and settings from a distance. Ensure that Remote Desktop is enabled and set up with the appropriate user permissions to establish a secure and controlled connection.
Step 3: Setting Up Network Address Translation (NAT)
Network Address Translation (NAT) allows for the translation of internal IP addresses to external ones, enabling communication between your local network and the internet. Configuring NAT on your router or gateway device is vital for remote access, as it ensures that requests from external devices reach your Windows system correctly.
Step 4: Establishing Secure Connections with VPN
Utilizing a Virtual Private Network (VPN) adds an extra layer of security to your remote access setup. By encrypting your internet traffic, VPNs provide a secure tunnel for information exchange between your remote device and the system you wish to connect to. Implementing a VPN on your Windows system enhances privacy and protects your data from potential threats.
Step 5: Consistent Monitoring and Updating
Regularly monitoring and updating your system is essential to ensure the ongoing security and stability of your remote access configuration. Stay vigilant with system updates, security patches, and firmware upgrades for your router or gateway device. Monitoring network activity and implementing appropriate security measures help maintain a reliable and protected remote access environment.
In conclusion, configuring your Windows system for remote access involves fine-tuning firewall settings, enabling Remote Desktop, setting up NAT, utilizing VPNs, and maintaining consistent monitoring and updating. By following these steps and implementing the necessary measures, you can establish a secure and reliable remote access setup tailored to your specific needs.
Securing Remote Connections with HTTPS
Ensuring the security of remote connections is of utmost importance when it comes to accessing your system or network from a remote location. One highly effective way to achieve this is by implementing HTTPS, which encrypts the data being transmitted between the client and the server.
HTTPS: HTTPS stands for Hypertext Transfer Protocol Secure and is the secure version of HTTP. By using HTTPS, the communication between the client and the server is protected through the use of SSL/TLS encryption. This encryption ensures that the data exchanged is secure and cannot be easily intercepted or tampered with.
Securing Remote Access: Implementing HTTPS for remote access helps to safeguard sensitive information, such as login credentials, personal data, and confidential documents. It prevents unauthorized access and protects against potential security threats, including eavesdropping, data breaches, and man-in-the-middle attacks.
Benefits of HTTPS for Remote Access: By establishing a secure connection using HTTPS, you gain the following advantages:
- Data Confidentiality: HTTPS encrypts the data transmitted, ensuring that it remains confidential and cannot be deciphered by unauthorized individuals.
- Data Integrity: The use of HTTPS guarantees that the data remains intact during transmission and cannot be tampered with or modified by attackers.
- Authentication: HTTPS verifies the identity of the server, ensuring that you are securely connecting to the intended remote system or network.
Enabling HTTPS: Setting up HTTPS for remote access typically involves obtaining a digital certificate, configuring your server to support HTTPS, and enforcing secure communication protocols such as TLS 1.2 or higher. Additionally, you may need to open the necessary ports on your firewall and regularly update your digital certificates to maintain security.
In conclusion, securing remote access with HTTPS is crucial for protecting your sensitive data and ensuring a secure connection between client and server. By implementing HTTPS, you can effectively mitigate security risks and maintain the confidentiality, integrity, and authentication of your remote connections.
REMOTE INTO ANY COMPUTER USING CHROME REMOTE DESKTOP 2022 | Updated | Google |
REMOTE INTO ANY COMPUTER USING CHROME REMOTE DESKTOP 2022 | Updated | Google | 来自ISAAC TECH 40,792次观看 2年前 9分钟2秒钟
How to EASILY Set Up Remote Desktop on Windows 10/11
How to EASILY Set Up Remote Desktop on Windows 10/11 来自Carson Cameron Clark 71,219次观看 10个月前 3分钟44秒钟
FAQ
What is remote access?
Remote access refers to the ability to access and control a computer or network remotely from a different location using a network connection.
Why is remote access important?
Remote access allows users to connect to their computers or networks from anywhere in the world, enabling access to files, applications, and resources that would otherwise be restricted to a local network.
What is HTTPS and why should I use it for remote access?
HTTPS stands for Hypertext Transfer Protocol Secure. It is a secure version of HTTP that uses encryption to protect the data being transmitted between a web browser and a server. Using HTTPS for remote access ensures that the connection between your computer and the remote device is encrypted, providing an additional layer of security.
Are there any additional steps required to set up remote access using HTTPS?
Yes, in order to set up remote access using HTTPS, you will need to configure your router or firewall to allow incoming HTTPS traffic to the computer you want to access remotely. This involves forwarding the appropriate ports and configuring any necessary security measures, such as setting up a secure certificate.




