Are you a fervent advocate of streamlining your organization's workflow and increasing operational efficiency? Look no further! In this comprehensive article, we will delve into the world of an innovative configuration management tool that is designed to revolutionize the way you manage your Linux-based systems. With its plethora of features and remarkable flexibility, this tool has proven to be an indispensable asset for countless tech-savvy professionals.
Swiftly guiding you through the installation process, we will equip you with the necessary skills and knowledge to effortlessly set up this remarkable tool. Brace yourself for an exhilarating journey where we navigate the intricate landscapes of effective system administration. So, prepare yourselves to discover newfound avenues to automate your workflows, save precious time, and enhance the overall reliability of your systems.
Through this comprehensive step-by-step guidance, you will gain a deep understanding of the inner workings of this configuration management tool and how it can be harnessed to orchestrate your infrastructure with stunning precision. By the time you reach the end of this article, you will have acquired the expertise needed to confidently wield this powerful tool, empowering you to seamlessly manage your Linux environment and optimizing your organization's performance.
A comprehensive overview of Puppet and the benefits it brings to IT infrastructure management
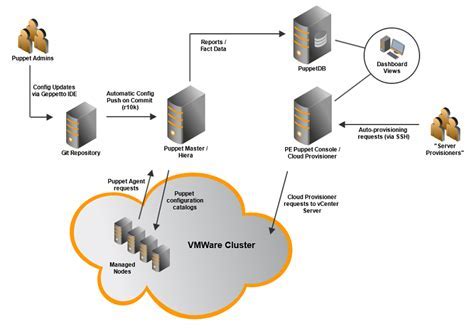
In today's ever-evolving technological landscape, effective management of IT infrastructure is paramount for businesses to stay competitive. Puppet, a powerful configuration management tool, offers a comprehensive solution for automating and orchestrating various aspects of IT infrastructure management. With Puppet, organizations can streamline the deployment, configuration, and maintenance of their systems, resulting in improved efficiency, scalability, and reliability.
One of the key advantages of using Puppet is its ability to manage infrastructure as code. By treating infrastructure configurations as code, organizations can leverage version control, testing, and continuous integration practices, ensuring consistent and predictable deployments. Puppet's declarative language allows administrators to define the desired state of systems, enabling automated enforcement and continuous monitoring to maintain that state.
Puppet's architecture is also highly scalable, making it suitable for managing both small-scale and large-scale infrastructures. With Puppet's master-agent model, administrators can centrally manage and control a fleet of systems, ensuring consistent configurations across multiple servers. This centralized approach allows for efficient updates and changes, reducing the risk of human error and minimizing disruptions.
Furthermore, Puppet offers a rich ecosystem of modules and plugins that extend its functionality and facilitate the management of diverse systems, applications, and cloud environments. These pre-built modules provide ready-to-use configurations and best practices, saving time and effort in setting up and managing complex systems.
Another notable advantage of Puppet is its support for cross-platform management. Whether you have a mixed environment of Linux, Windows, or other operating systems, Puppet enables you to manage and automate configurations across different platforms from a single control point. This cross-platform compatibility simplifies the management process and ensures consistency across heterogeneous environments.
In conclusion, Puppet is a powerful configuration management tool that offers numerous advantages in managing IT infrastructure. By adopting Puppet, organizations can automate and orchestrate their infrastructure, improve efficiency and reliability, and ensure consistency across diverse platforms. With its comprehensive features and robust ecosystem, Puppet empowers businesses to confidently manage and scale their IT environments in today's dynamic landscape.
Understanding the prerequisites for configuring Puppet
In order to successfully set up the Puppet configuration management tool, there are certain requirements that must be met. This section provides an overview of the necessary components and considerations to ensure a smooth installation and deployment process.
Operating System Compatibility: Before setting up Puppet, it is important to ensure that your Linux distribution is compatible with the tool. Puppet supports a wide range of Linux distributions, including but not limited to Ubuntu, CentOS, Debian, and Red Hat Enterprise Linux.
System Requirements: To optimize performance and stability, it is recommended to meet the minimum system requirements for Puppet. This includes having sufficient CPU, memory, and disk space to support the installation and operation of Puppet on your Linux environment.
Network Connectivity: Puppet relies on network connectivity to communicate between the Puppet master and Puppet agent nodes. Therefore, it is crucial to have a stable network connection in order for the Puppet infrastructure to function properly.
Package Dependencies: Puppet has certain dependencies that need to be installed before the tool can be set up. These dependencies may include software packages such as Ruby, SSL libraries, and additional Puppet modules, which are necessary for Puppet to operate seamlessly.
Authentication and Access: To set up Puppet, it is important to have the necessary authentication credentials and access to the Linux system. This includes having administrative privileges or sudo access to install and configure Puppet components.
Security Considerations: As Puppet involves managing configurations and sensitive information, it is essential to consider security measures during the setup process. This may involve configuring SSL certificates, setting up firewall rules, and implementing access controls to protect the integrity and confidentiality of Puppet deployments.
By understanding and fulfilling these requirements, you can ensure a successful setup and deployment of the Puppet configuration management tool on your Linux system.
Understanding the System and Software Requirements for Deploying and Utilizing Puppet on Linux

In order to successfully implement and utilize the powerful automation capabilities of Puppet on Linux systems, it is essential to meet certain system and software prerequisites. This section explores and explains the necessary components and configurations required before proceeding with the installation and usage of Puppet.
- A compatible Linux distribution: Puppet supports a wide range of Linux distributions, including but not limited to Ubuntu, CentOS, and Red Hat Enterprise Linux. It is crucial to ensure that the chosen distribution is supported by Puppet to ensure smooth operation.
- Supported versions of Linux kernel and package management: Different versions of the Linux kernel and package management tools, such as Dpkg and RPM, have specific requirements for Puppet compatibility. It is essential to refer to the Puppet documentation or official website to determine the exact kernel and package management versions that are supported.
- Adequate hardware resources: Puppet requires a certain level of hardware resources to function efficiently. This includes CPU, RAM, and disk space requirements. The specific hardware specifications may vary depending on factors such as the size of the infrastructure and the complexity of the Puppet manifests and modules being used.
- Network connectivity: Puppet relies on network connectivity to communicate between the Puppet server and the managed Puppet agents. It is crucial to ensure that the network infrastructure is properly configured to allow seamless communication and data transfer.
- Secure shell access: Secure shell (SSH) access is required for managing the Puppet infrastructure. It is necessary to have SSH properly configured with the appropriate authentication mechanisms, including key-based authentication or password-based authentication, depending on the security requirements of the environment.
- Additional software packages: Depending on the specific requirements of the Puppet implementation, certain additional software packages may be needed. This can include components such as a database backend (e.g., PostgreSQL or MySQL) for PuppetDB, a web server (e.g., Apache or Nginx) for hosting the Puppet Forge, or other tools and utilities that enhance the functionality of Puppet.
By ensuring that these system and software prerequisites are met, you can lay a solid foundation for setting up and using Puppet on Linux effectively. This comprehensive understanding of the requirements allows for a smooth and successful deployment, minimizing any potential issues or complications along the way.
Setting up the Puppet server on a Linux platform
In this section, we will explore the process of installing and configuring the Puppet server on a Linux system, bringing the power of automation to your infrastructure management framework. By following these steps, you will be able to effortlessly establish a reliable and efficient Puppet server environment.
Step 1: Preparation
Before installing the Puppet server, it is essential to ensure that your Linux system meets the necessary prerequisites. This involves verifying the compatibility of the operating system version, allocating sufficient resources, and enabling the required services and dependencies. Taking these initial preparations will set the foundation for a smooth Puppet server installation.
Step 2: Installation
Once the system is adequately prepared, it's time to proceed with the installation of the Puppet server. This step involves downloading the appropriate Puppet package, importing the Puppet repository key, and updating the package manager. By carefully following these installation instructions, you will have the Puppet server up and running in no time.
Step 3: Configuration
With the Puppet server installed, the next crucial step is configuring its settings to align with your specific requirements. This includes defining the server's hostname, specifying the certificate authority (CA) details, configuring access control, and setting up environments. By customizing these configuration parameters, you can tailor the Puppet server to suit your infrastructure management needs.
Step 4: Testing and Validation
After the installation and configuration steps are completed, it is crucial to validate the functionality of the Puppet server. This involves performing tests to ensure proper communication with Puppet agents, checking for error-free operation, and verifying the successful deployment of Puppet manifests and modules. By conducting thorough testing, you can guarantee the reliability and accuracy of the Puppet server environment.
Step 5: Maintenance and Updates
Successfully setting up the Puppet server is not the end of the journey; it marks the beginning of a continuous maintenance and update process. This step involves regularly monitoring the server's performance, managing security aspects, applying patches and updates, and staying up-to-date with the latest Puppet releases. By maintaining an active and well-maintained Puppet server, you can ensure long-term efficiency and effectiveness.
By following this step-by-step guide, you will be able to install and configure the Puppet server on a Linux platform, establishing a robust and automated infrastructure management solution for your organization.
Setting Up the Puppet Server: A Comprehensive Installation and Configuration Guide for Linux

In this section, we will explore the detailed process of installing and configuring the Puppet server on a Linux system. By following the step-by-step instructions provided in this guide, you will be able to successfully set up and manage a Puppet server to automate the deployment and configuration of your infrastructure.
Before diving into the installation and configuration process, it is important to understand the role of the Puppet server and its significance in a Linux environment. The Puppet server acts as the central hub for managing and orchestrating the configuration of multiple systems within your infrastructure. It enables administrators to define desired system states, enforce consistency across various nodes, and streamline the management of configuration changes.
Now, let's begin the installation process by ensuring that your Linux system meets the necessary prerequisites. Check the compatibility of your operating system, verify the availability of system resources, and gather the required software packages. Once these prerequisites are met, proceed with the installation of the Puppet server.
Next, we will guide you through the process of configuring the Puppet server to suit your specific needs. This includes setting up the server hostname, defining certificates for secure communication, configuring access control, and establishing a connection with Puppet agents on the nodes you intend to manage.
An integral part of the configuration process involves creating and managing Puppet modules. These modules serve as the building blocks for defining the desired state and behavior of the systems in your infrastructure. We will explain how to structure and organize modules effectively, as well as how to leverage pre-existing modules from the Puppet Forge.
In addition to module configuration, we will also cover the essential aspects of managing Puppet environments. Environments allow you to create separate sandboxed spaces for testing changes, ensuring proper version control, and promoting configurations to production. We will provide step-by-step instructions on how to create, configure, and switch between different Puppet environments.
By the end of this guide, you will have gained a comprehensive understanding of how to install and configure the Puppet server on a Linux system. You will be equipped with the knowledge and skills necessary to leverage Puppet's power and flexibility in automating the management of your infrastructure. Let's get started!
| Contents |
|---|
| 1. Introduction |
| 2. Preparing the Linux System |
| 3. Installing the Puppet Server |
| 4. Configuring the Puppet Server |
| 5. Managing Puppet Modules |
| 6. Working with Puppet Environments |
| 7. Conclusion |
Setting up Configuration Management Agents on Linux
In the realm of managing system configurations, it is crucial to have effective configuration management agents in place on your Linux clients. These agents act as intermediaries, facilitating the communication between the central configuration management server and the individual Linux machines.
There are multiple configuration management agents available for Linux, each with its own set of features and capabilities. It is important to choose the right agent for your specific environment and requirements. Here are some popular options:
- AgentX:
- Systemd Puppet Wrapper:
- Chef:
- Ansible:
- SaltStack:
Once you have decided on the configuration management agent that best suits your needs, the next step is to install and configure it on your Linux clients. The installation process may vary slightly depending on the agent chosen, but generally involves the following steps:
- Downloading the agent package:
- Installing the agent package:
- Configuring the agent:
- Connecting the agent to the configuration management server:
After completing these steps, your Linux clients will be ready to receive and apply configuration changes pushed by the central configuration management server. This enables centralized administration and ensures consistency across your infrastructure.
Installing the Puppet Agent and Establishing Communication with the Server
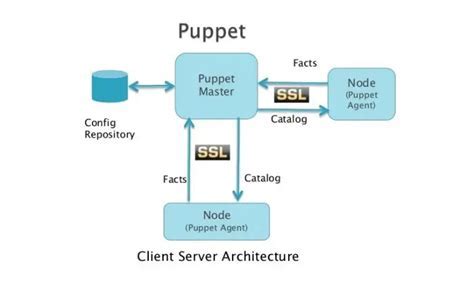
This section focuses on the process of installing the Puppet agent on client machines and establishing a secure communication channel with the Puppet server. By following these steps, you can enable effective management and automation of your Linux infrastructure using Puppet.
- Ensure that the client machines meet the necessary system requirements for Puppet installation.
- Download and install the Puppet agent package on each client machine, leveraging the appropriate package manager for your Linux distribution.
- Configure the Puppet agent by specifying the Puppet server's hostname or IP address as well as any necessary certificate details.
- Generate a Certificate Signing Request (CSR) on the Puppet agent and submit it to the Puppet server for signing.
- Accept and sign the Puppet agent's certificate on the Puppet server to establish trust between the server and the client.
- Configure the Puppet agent's communication settings to ensure it can connect and interact with the Puppet server.
- Start the Puppet agent service on each client machine, enabling it to retrieve configuration instructions and apply them.
- Verify the successful connection and communication between the Puppet agent and the Puppet server.
By diligently following these steps, you will create a reliable and secure setup where the Puppet agent can seamlessly communicate with the Puppet server, enabling efficient management and automation of your Linux environment.
Configuring Puppet Manifests and Modules
In this section, we will explore the process of configuring manifests and modules in Puppet installation on a Linux system. By customizing the manifests and modules, you can define the desired state of your infrastructure and manage it effectively.
To configure the Puppet manifests, you will create or modify the Puppet code files that define how resources should be managed on the target systems. You can use various types of resources, such as packages, services, files, and users, to define the desired configuration.
Within the manifests, you can specify dependencies between resources, define conditions for resource application, and set parameters for resource configuration. This allows you to create a comprehensive and flexible configuration model for your infrastructure.
Modules, on the other hand, are used to organize and package Puppet code. You can think of modules as self-contained units of Puppet code that encapsulate related resources and their configurations. By properly structuring and organizing your modules, you can ensure reusability, maintainability, and modularity in your Puppet codebase.
In this section, we will discuss best practices for configuring and organizing Puppet manifests and modules. We will cover topics such as creating and managing manifests, structuring modules, using variables and templates, and leveraging community modules and templates to accelerate your configuration process.
An introduction to Puppet manifest files and modules, and effective strategies for writing and organizing them
Within the realm of configuration management, Puppet provides a powerful and efficient solution for automating administrative tasks. Central to the functionality of Puppet are its manifest files and modules, which serve as blueprints for defining and managing the desired state of systems. This section will provide an overview of these crucial components and delve into practical strategies for writing and organizing them effectively.
Manifest files, written in Puppet's declarative language, serve as the building blocks of configuration management. They describe the desired configuration state of a specific aspect of a system, such as packages, services, or user accounts. By specifying the intended state rather than the steps to achieve it, manifest files enable idempotent configuration management, ensuring that systems are brought to and maintained in the desired state regardless of their initial condition.
Puppet modules, on the other hand, provide a logical framework for grouping related manifest files and associated resources. They encapsulate a specific functionality or piece of configuration logic, promoting modularity and reusability. Modules not only enhance the organization and maintainability of Puppet code but also facilitate collaboration among system administrators by allowing the sharing of code and best practices. By following established conventions for module layout and naming, teams can maintain consistency and improve efficiency across their Puppet infrastructure.
When it comes to writing effective Puppet manifest files, it is crucial to adopt a structured approach. This involves using resources, such as packages and services, to define the desired state of a system and managing dependencies between different resources. By understanding and utilizing Puppet's resource dependency graph effectively, administrators can ensure that changes are applied in the correct order and dependencies are satisfied, thereby avoiding configuration inconsistencies and errors.
Furthermore, organizing manifest files within modules helps to maintain clarity and simplifies collaboration. By grouping related resources within a module, administrators can easily locate and manage configuration logic specific to a particular aspect of the system. Modules can also be organized hierarchically, allowing for the creation of reusable parent modules that encapsulate common configuration patterns while child modules focus on specific system requirements.
| Manifest file | Module |
|---|---|
| system.pp | base |
| packages.pp | webserver |
| services.pp | database |
| users.pp | network |
In summary, understanding the role of manifest files and modules is essential for effective Puppet configuration management. By adopting a structured approach to writing manifest files and organizing them within modules, administrators can ensure consistency, modularity, and maintainability across their Puppet infrastructure.
Puppet Language Syntax and Best Practices
In this section, we will explore the syntax and best practices of the Puppet language, a powerful configuration management tool used for automating IT infrastructure. Understanding the syntax and following best practices is crucial for effective Puppet code development and maintenance.
Firstly, let's delve into the fundamental elements of Puppet's syntax. Puppet code is written in a declarative style and consists of resources, attributes, and values. Resources represent the objects to be managed, such as files, packages, or services. Attributes define the properties of resources, and values specify the desired state of those properties.
Proper indentation and formatting are essential for writing clean and readable Puppet code. It is recommended to use two spaces for indentation and to align attributes and values for better clarity. Consistent and clear naming conventions enhance code maintainability and understanding.
Using comments strategically in your Puppet code is another best practice. Comments allow you to provide explanations, documentations, and notes for yourself and other team members. They can also be used to temporarily disable or test specific sections of code.
Reusability is a key aspect of writing efficient Puppet code. Puppet provides the concept of modules, which encapsulate and organize code logic for specific purposes. By creating reusable modules, you can save time, improve code maintainability, and foster collaboration within teams.
In summary, this section will provide a comprehensive overview of Puppet language syntax, including resource declaration, attribute assignment, indentation, naming conventions, and the importance of comments and reusability. Mastering these language elements and adhering to best practices will greatly contribute to the effectiveness and efficiency of your Puppet deployments.
Tips and guidelines for crafting clean and efficient code in Puppet, encompassing syntax guidelines and best practices

In this section, we will delve into the fundamental principles and recommendations for constructing meticulous and high-performing Puppet code. Adhering to a well-defined syntax not only enhances code readability but also fosters maintainability and scalability.
A well-structured Puppet codebase is a cornerstone for effectively managing infrastructure configurations. By following syntax rules and employing recommended practices, you can streamline your Puppet manifests, modules, and classes, resulting in more manageable codebases and efficient execution.
Here, we will explore helpful guidelines to facilitate clean and elegant code writing in Puppet, encompassing proper indentation, consistent naming conventions, efficient resource management, and effective use of variables and functions. Moreover, we will emphasize the significance of documentation, code modularization, and code reusability to promote collaboration and code maintainability.
To establish comprehensive code quality, we will discuss common pitfalls and anti-patterns to avoid, such as code duplication, excessive resource ordering, and neglecting proper testing methodologies. Incorporating automated testing frameworks, like rspec-puppet and Beaker, can mitigate risks and ensure the correctness of your Puppet code.
Additionally, we will introduce version control best practices, enabling seamless collaboration, code versioning, and rollback capabilities. Employing tools like Git and utilizing branching and code review workflows will enhance team productivity and code traceability.
| Key Topics: |
|---|
| 1. Syntax rules and conventions |
| 2. Proper indentation and formatting |
| 3. Consistent naming conventions |
| 4. Effective resource management |
| 5. Utilizing variables and functions efficiently |
| 6. Importance of documentation |
| 7. Modularization and code reuse |
| 8. Identifying and avoiding common code pitfalls |
| 9. Testing methodologies and tools |
| 10. Version control best practices |
Managing Environments in Puppet: An Essential Aspect of Configuration Management
When it comes to configuration management, the ability to manage environments efficiently plays a pivotal role. In this section, we will explore the significance of managing environments in Puppet and how it contributes to streamlining and automating system configurations without explicitly mentioning the "setting up" process, the target platform, or the specific guide format.
Environment Definition: Before diving into the details, it is crucial to understand the concept of environments in Puppet. An environment is a segregated space or a domain within Puppet where different sets of configurations are applied, enabling administrators to handle distinctive infrastructure needs. By creating and managing environments, you gain flexibility and control over the configuration changes deployed across various stages of your system's lifecycle.
Managing Environment-Specific Configurations: The ability to define and maintain environment-specific configurations is a fundamental capability of Puppet. In this section, we will explore the tooling and best practices required to effectively create, organize, and apply environment-specific configurations. This includes techniques for managing environment-specific variables, configurations for development, testing, and production environments, and strategies to ensure consistency and reproducibility throughout the system's evolution.
Environment Isolation: One of the key advantages of managing environments in Puppet is the ability to isolate configuration changes. Puppet provides mechanisms to keep environments separate, allowing modifications in one environment without affecting others. We will delve into the importance of environment isolation, its impact on system stability, and strategies to ensure that changes made in a specific environment do not inadvertently affect the overall infrastructure.
Environment Promotion: In complex environments, seamless transitioning of configurations from one environment to another is often necessary. This section will focus on the best practices and methodologies involved in promoting configurations across different environments. We will explore techniques for verifying compatibility, conducting staging tests, and automating the promotion process to ensure smooth and reliable promotion of configurations.
Environment Versioning and Rollbacks: Managing version control and enabling rollbacks is critical in any configuration management system. In Puppet, the ability to track changes made to environment-specific configurations and to rollback undesired modifications plays a crucial role in maintaining system integrity. In this part, we will discuss strategies for versioning environments, tracking changes, and reverting configurations to previous states when needed.
In conclusion, managing environments in Puppet is an essential aspect of configuration management. By understanding and embracing the capabilities it offers, administrators gain the ability to efficiently tailor system configurations to different needs, ensure stability through environment isolation, and simplify the process of promoting and controlling versions of configurations. These aspects collectively contribute to an organized and automated approach to configuration management.
[MOVIES] [/MOVIES] [/MOVIES_ENABLED]FAQ
What is Puppet?
Puppet is an open-source configuration management tool that allows system administrators to automate the process of deploying, managing, and configuring software on multiple servers.
Why should I use Puppet?
Puppet provides a reliable and scalable solution for managing server configurations. It helps to ensure consistency across a large number of servers and reduces the time and effort required for manual configuration.
How do I install Puppet on Linux?
To install Puppet on Linux, you first need to add the Puppet repository to the package manager, and then run the installation command. Detailed step-by-step instructions can be found in the article.
Can I use Puppet to manage both physical and virtual servers?
Yes, Puppet can be used to manage both physical and virtual servers. It supports a wide range of platforms and can be used to automate configuration management on any type of server infrastructure.
Are there any alternatives to Puppet?
Yes, there are several alternative configuration management tools available, such as Ansible, Chef, and SaltStack. Each tool has its own strengths and weaknesses, so it's important to evaluate your specific requirements before choosing one.




