In the rapidly evolving digital landscape, where security threats loom large, it is imperative for organizations to safeguard their systems against potential vulnerabilities. To achieve this, one needs to understand the fundamentals of vulnerability assessment, a critical aspect of fortifying the digital infrastructure. This article aims to shed light on the process of setting up a powerful vulnerability assessment tool, OpenVAS, on a Linux-based platform, equipping users with an effective solution to identify and mitigate security weaknesses.
With the relentless rise in cyberattacks, the need for a comprehensive vulnerability assessment tool has never been more pressing. OpenVAS emerges as a leading contender, offering a wide range of features and capabilities to identify, categorize, and analyze potential security flaws within an information system. By leveraging the power of OpenVAS, organizations can gain a deep understanding of their system's vulnerabilities, enabling them to take proactive measures to enhance their security posture.
One of the key advantages of OpenVAS is its seamless integration with Linux, a versatile and reliable operating system renowned for its stability and security. By harnessing the power of Linux, users have access to a myriad of tools and utilities that facilitate the smooth installation and configuration of OpenVAS. This guide will walk you through the necessary steps to set up OpenVAS on your Linux system, ensuring a hassle-free experience from start to finish.
Understanding the Significance of OpenVAS in Enhancing System Security
When discussing the realm of cybersecurity, it becomes crucial to delve into the world of OpenVAS and comprehend its relevance. OpenVAS serves as a powerful tool that plays a vital role in fortifying the security of Linux systems. It encompasses a plethora of features and functionalities that aid in the identification of potential vulnerabilities, enabling users to implement necessary safeguards effectively.
OpenVAS essentially acts as a guardian, performing comprehensive vulnerability assessments and identifying weaknesses within a system or network. By conducting thorough scans and audits, OpenVAS evaluates potential entry points for malicious entities, allowing users to take proactive measures to protect their systems from potential threats.
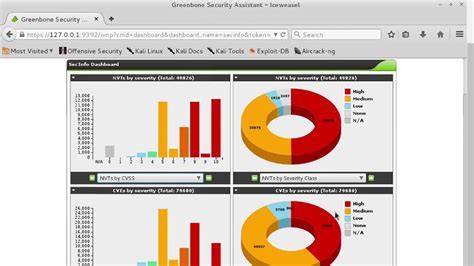
The importance of OpenVAS lies in its ability to provide detailed and accurate vulnerability reports. With the help of OpenVAS, users gain access to comprehensive insights into the potential risks and vulnerabilities present within their Linux systems. These reports not only highlight the weaknesses but also offer recommendations and remediation actions, empowering users to prioritize their security endeavors effectively.
Moreover, OpenVAS ensures continuous monitoring of systems, assisting users in maintaining an up-to-date security posture. By regularly scanning and assessing their networks, users can stay vigilant against emerging threats and promptly address any vulnerabilities that may arise.
By utilizing OpenVAS, users can establish a robust security framework that protects their Linux systems against various cyber threats, such as unauthorized access, data breaches, and system compromises. OpenVAS emerges as a critical component in the ever-evolving landscape of cybersecurity, enabling users to safeguard their systems and data with confidence.
Gathering and Preparing the Required Software Components
Before embarking on the OpenVAS setup process on your Linux system, it is essential to gather and prepare the necessary software components. This section will guide you through the steps of acquiring and organizing the software tools required for a successful OpenVAS installation.
Identifying Software Needs:
The first step in preparing for OpenVAS installation is to identify the specific software components you will need. This includes identifying the compatible versions of the operating system, libraries, and dependencies required by OpenVAS.
Checking System Resource Requirements:
Next, it is crucial to assess your Linux system's resource capabilities to ensure optimal performance of OpenVAS. Consider the system's CPU, RAM, and disk space to verify if they meet OpenVAS's minimum requirements. Additionally, ensure that your network connection is stable and suitable for handling vulnerability scanning tasks.
Acquiring the Software:
Once you have a clear understanding of the software needs and system resources, proceed to acquire the necessary components. This involves downloading the compatible versions of Linux distribution, relevant packages, and any additional dependencies required by OpenVAS.
Preparing the Environment:
Prior to installing OpenVAS, it is important to prepare the environment for seamless integration. This may involve creating user accounts with appropriate permissions, configuring network settings, and setting up any additional software tools required as prerequisites for OpenVAS.
Verifying Software Compatibility:
Finally, it is critical to verify the compatibility and integrity of the acquired software components for a smooth installation process. Perform a checksum verification or integrity check to ensure that the downloaded files are not corrupted or modified, as this could potentially impact the OpenVAS setup.
By meticulously gathering and preparing the necessary software components, you lay a solid foundation for setting up OpenVAS on your Linux system. This attention to detail ensures a smooth installation process and paves the way for effective vulnerability assessment and management.
Step 1: Installing OpenVAS on a Linux System

In this section, we will guide you through the process of installing OpenVAS on your Linux-based operating system. By following these steps, you will be able to set up a powerful vulnerability scanning tool that can enhance the security of your system.
Choosing a Suitable Distribution for OpenVAS
When it comes to selecting a Linux distribution for running OpenVAS, it is crucial to consider various factors that can impact the overall performance and security of your system. This section will provide an overview of the important considerations involved in choosing the right Linux distribution for OpenVAS without specifically mentioning the names of specific distributions.
One of the key factors to consider is the stability and reliability of the Linux distribution. It is essential to opt for a distribution that has a long history of reliable performance and a strong track record of regular security updates. By selecting a distribution with a solid reputation, you can ensure a stable and secure environment for running OpenVAS.
Another aspect to consider is the community support and documentation available for the Linux distribution you choose. It is beneficial to select a distribution that has an active and engaged community, as this will provide you with a wealth of resources, forums, and tutorials to assist you in setting up and maintaining OpenVAS effectively.
Furthermore, compatibility with OpenVAS is a crucial consideration. Not all Linux distributions are created equal when it comes to compatibility with OpenVAS dependencies and plugins. Before making a decision, it is important to research and ensure that the Linux distribution you choose seamlessly integrates with OpenVAS, enabling smooth and efficient scanning.
In addition to functionality, it is vital to take into account the system requirements of the Linux distribution. OpenVAS may have specific hardware or software requirements, and it is essential to choose a distribution that can meet these demands comfortably. This will ensure optimal performance and minimize any potential issues that could arise during installation or usage.
Finally, a consideration that should not be overlooked is personal preference and familiarity. It is essential to select a Linux distribution that you are comfortable and familiar with, as this will facilitate the setup and management of OpenVAS. Your expertise and knowledge of the distribution will contribute to a smoother implementation and ultimately enhance the effectiveness of your vulnerability management process.
By considering the factors outlined in this section, you will be equipped to make an informed decision when it comes to choosing the Linux distribution that best suits your needs for running OpenVAS, without mentioning specific names. The subsequent steps in this guide will assume that you have selected an appropriate distribution and will focus on the actual setup of OpenVAS on your chosen system.
Downloading and Installing OpenVAS

In this section, we will explore the process of acquiring and setting up OpenVAS on your Linux environment. The configuration steps outlined below will guide you through the preparation and installation of this advanced vulnerability scanning tool.
To begin the installation process, you need to obtain the necessary OpenVAS package. This can be done by downloading the latest version from the official OpenVAS website or by utilizing package managers available on your Linux distribution.
Once you have successfully obtained the OpenVAS package, you can proceed with the installation. The specific steps for installation may vary depending on your Linux distribution, but in general, you will need to access the terminal and execute the appropriate commands. This might include commands such as unpacking the downloaded package, running the installation script, and resolving any dependencies that may be required.
After the installation is complete, you will need to perform initial configuration to set up OpenVAS according to your specific requirements. This includes tasks such as creating an administrative user, configuring network settings, and setting up necessary databases.
A crucial step in the installation process is updating the OpenVAS vulnerability feed. This feed contains the latest information about known vulnerabilities and is essential for accurate scanning. You will need to download and update this feed regularly to ensure your OpenVAS installation remains up to date and effective.
| Downloading and Installing OpenVAS |
| 1. Obtain the OpenVAS package |
| 2. Install OpenVAS on your Linux distribution |
| 3. Perform initial configuration |
| 4. Update the OpenVAS vulnerability feed |
Configuration of OpenVAS for Initial Setup
In this section, we will explore the necessary steps to configure OpenVAS, a powerful vulnerability scanning tool, on a Linux system. By configuring OpenVAS for initial setup, users can ensure that the system is properly prepared to perform comprehensive security assessments and identify potential vulnerabilities.
The configuration process involves a series of steps that will enable users to tailor OpenVAS to their specific needs and preferences. By carefully adjusting settings and options, users can optimize the scanning process, define scanning targets, and configure scanning policies to ensure accurate and relevant results. This configuration phase is crucial in ensuring OpenVAS operates effectively and efficiently in identifying security weaknesses within a system or network.
Within this section, we will guide you through the various aspects of OpenVAS configuration, including the tuning of scan configurations, definition of target hosts, and customization of scan policies. By following these steps, users will be able to set up OpenVAS for their individual requirements and maximize the accuracy and relevance of the scan results.
We will explore the different features and settings available within OpenVAS, explaining their significance and potential impact on the scanning process. Additionally, we will provide tips and recommendations to help users make informed decisions during the configuration process.
By the end of this section, readers will have a comprehensive understanding of the configuration process of OpenVAS, equipped with the knowledge to effectively set up OpenVAS for their Linux system. With OpenVAS correctly configured, users can confidently proceed to the subsequent steps of this guide, ready to perform thorough vulnerability assessments and enhance the security posture of their system or network.
Setting Up the OpenVAS Administrator Account

In this section, we will discuss the process of creating and configuring the administrator account for OpenVAS. The administrator account plays a vital role in managing the security scanning tool and its various functionalities.
To get started, it is important to understand the significance of establishing a secure and strong administrator account. This account will serve as the primary point of access to the OpenVAS tool, allowing the user to configure and customize the scanning operations according to their specific requirements.
To set up the administrator account, it is recommended to choose a unique username and a strong password. This will ensure the account remains secure from any potential unauthorized access. Additionally, enabling multi-factor authentication, if supported by the system, can provide an extra layer of protection to the administrator account.
Once the username and password are chosen, it is crucial to follow the necessary steps to configure the account settings. These settings may include defining the administrator's privileges, access controls, and notifications for any critical events. It is important to carefully review and select these settings to ensure the account functions efficiently and effectively.
After the initial setup, it is advisable to regularly update the account credentials, such as changing the password periodically, as a best practice for maintaining account integrity. Furthermore, monitoring the account's activity logs can help in identifying any suspicious or unauthorized activities, allowing for prompt remediation.
By meticulously establishing and managing the OpenVAS administrator account, users can confidently utilize the tool and leverage its capabilities to improve the security posture of their Linux system. The administrator account acts as the cornerstone for effective vulnerability scanning and enables seamless administration of OpenVAS.
Configuring OpenVAS: Setting up Your OpenVAS Environment
In this section, we will delve into the initial configuration of OpenVAS, focusing on establishing the necessary environment for optimal performance. We will explore the essential setup steps to ensure seamless operation and effective vulnerability scanning.
To begin, it is crucial to fine-tune the parameters of your OpenVAS installation. This involves customizing the settings according to your specific requirements, allowing you to tailor OpenVAS to your organization's unique needs. By configuring these options, you can optimize the performance and efficiency of your vulnerability scanning process.
- Start by adjusting the scan schedules to ensure that OpenVAS runs at the most convenient times, minimizing any potential disruption to your network. This will enable you to schedule scans during periods of low network usage or outside of regular working hours.
- Next, take advantage of OpenVAS's ability to define target hosts and scan configurations. By carefully selecting the hosts you wish to scan and specifying the scanning configurations, you can focus on the most critical areas of your network, maximizing the effectiveness of your vulnerability assessment.
- Another essential aspect of configuration involves managing OpenVAS credentials. This includes determining the authentication credentials for accessing targeted hosts during the scan process. By properly managing credentials, you can ensure that OpenVAS can successfully authenticate and perform comprehensive vulnerability checks on your network assets.
- Furthermore, it is crucial to understand how to interpret and tailor the reporting capabilities of OpenVAS. By configuring the reporting settings, you can generate detailed vulnerability reports that provide comprehensive insights into the discovered vulnerabilities, ensuring informed decision-making regarding necessary remediation actions.
- Last but not least, optimizing OpenVAS performance is vital for efficient vulnerability scanning. This includes tuning various performance settings based on your system's available resources, enabling OpenVAS to utilize system assets effectively.
By following these initial configuration steps, you will establish a robust and customized OpenVAS environment that aligns with your organization's specific needs. This will enable you to conduct comprehensive vulnerability scanning and efficiently manage the identified security risks.
Scanning Targets using OpenVAS
In this section, we will explore the key steps involved in scanning targets using the powerful OpenVAS vulnerability scanner. Scanning targets is a crucial phase in the security assessment process as it allows you to identify potential weaknesses and vulnerabilities present in your system or network.
To initiate the scanning process, you need to provide the scanner with a list of targets that you want to assess. These targets can include individual IP addresses, specific ports, or even entire network ranges. OpenVAS offers a variety of scanning options and configurations to cater to different security requirements.
- Defining Targets: Before you can start scanning, you need to define the targets you want to assess. This may involve specifying IP addresses, domains, or other identifying information. OpenVAS provides flexible options for defining targets, allowing you to customize the scanning scope according to your needs.
- Choosing Scan Configurations: OpenVAS offers a range of predefined scan configurations, each tailored to identify specific types of vulnerabilities or security issues. You can select the appropriate scan configuration based on the assets you want to assess and the level of thoroughness required for your security assessment.
- Configuring Scan Parameters: Once you have defined your targets and chosen the appropriate scan configuration, you can further refine the scanning process by configuring various parameters. These parameters include scan options, such as whether to perform a comprehensive or fast scan, and timeout settings, which determine how long the scanner will wait for a response from a target before moving on.
- Running the Scan: After all the necessary configurations are in place, you can initiate the scanning process. OpenVAS will systematically scan each target according to the defined parameters and scan configuration. The scanning process may take some time depending on the number of targets and the complexity of the scan configuration.
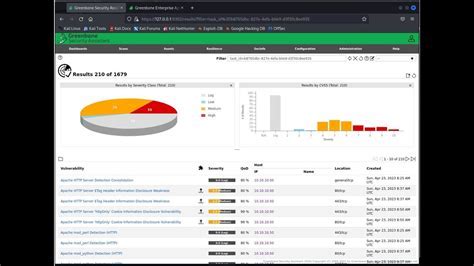
- Reviewing Scan Results: Once the scan is complete, OpenVAS will generate a comprehensive report detailing the vulnerabilities and security issues identified during the assessment. You can review the scan results to gain insights into potential risks and prioritize the remediation efforts accordingly.
By following these step-by-step instructions, you can effectively utilize OpenVAS to scan targets and uncover vulnerabilities in your system or network. Regular scanning and analysis of the scan results can help you maintain a proactive security posture and ensure the integrity of your digital assets.
Adding and Configuring Target Hosts for Scanning
In this section, we will explore the process of incorporating and customizing target hosts for the scanning process. By following the steps outlined below, you will be able to effortlessly configure your OpenVAS setup to effectively scan and assess the security of your target systems.
- Identify the target hosts: Begin by identifying the systems that you wish to scan using OpenVAS. This could include servers, workstations, or any other devices within your network that you want to assess for vulnerabilities.
- Acquire necessary information: Gather the required information for each target host, such as their IP addresses or hostnames. This data will be crucial for configuring OpenVAS to perform accurate scans.
- Access the OpenVAS management interface: Navigate to the OpenVAS management interface using your preferred web browser. Enter your login credentials to access the relevant features and functionalities.
- Navigate to the "Targets" section: Locate and access the "Targets" section within the OpenVAS management interface. This is where you can add, modify, and configure target hosts for scanning.
- Add a new target host: Click on the "Add Target" button to initiate the process of adding a new target host for scanning. Enter the necessary details, such as the target host's IP address or hostname, and specify any additional parameters if required.
- Configure target host settings: Customize the scanning parameters for each target host based on your specific requirements. This includes selecting the appropriate scan types, configuring scanning schedules, and defining the level of thoroughness for vulnerability detection.
- Verify and save the changes: Double-check the entered information for accuracy and ensure that all settings align with your intended scanning objectives. Once satisfied, save the changes to incorporate the target host into your OpenVAS setup.
By diligently adding and configuring target hosts within OpenVAS, you will be able to comprehensively scan and evaluate the security posture of your systems, enabling you to proactively address any vulnerabilities and strengthen your overall defense against potential threats.
Installing And Configuring OpenVAS
Installing And Configuring OpenVAS by HackerSploit 63,195 views 5 years ago 7 minutes, 39 seconds
FAQ
What is OpenVAS and why should I use it on a Linux system?
OpenVAS is an open-source vulnerability scanner that helps you identify security vulnerabilities in your system. It is widely used for security testing and ensures that your Linux system is secure by scanning it for potential vulnerabilities.
Is OpenVAS easy to install on a Linux system?
Yes, setting up OpenVAS on a Linux system is relatively straightforward. This step-by-step guide will walk you through the installation process and help you get started with OpenVAS quickly.
What are the system requirements for running OpenVAS?
OpenVAS requires a Linux system with a minimum of 2 GB of RAM and 10 GB of disk space. It is recommended to have a dedicated machine or virtual environment to run OpenVAS for better performance.
Can I schedule scans with OpenVAS?
Yes, OpenVAS allows you to schedule scans to run automatically at specified intervals. You can set up regular scans to ensure that your system is continuously monitored for vulnerabilities.
What types of vulnerabilities can OpenVAS detect?
OpenVAS can detect various types of vulnerabilities including missing patches, weak passwords, configuration errors, and known software vulnerabilities. It scans your system for these vulnerabilities and provides you with detailed reports and recommendations for remediation.
What is OpenVAS?
OpenVAS is an open-source vulnerability scanning and management system used for detecting security holes in a network or system.




