Securely managing user data and ensuring authorized access to resources are critical factors in maintaining the integrity of any operating system. With the advent of open-source technology, system administrators have been afforded a plethora of options for setting up robust authentication mechanisms. In this article, we delve into the world of Lightweight Directory Access Protocol (LDAP) and its implementation within the Linux ecosystem.
Establishing a centralized and scalable user management system
LDAP, often referred to as a "directory service," functions as a protocol for querying and modifying directory information. By employing LDAP-based authentication, system administrators can establish a centralized repository for user accounts and related data, enabling a streamlined and scalable approach to managing user access across multiple systems.
Replacing traditional methods of authentication
The traditional approaches to authentication, such as storing user data locally or utilizing plain text files, have significant limitations when it comes to managing large-scale environments. These methods often lack the necessary security measures to protect sensitive information and tend to become unwieldy as the number of users increases. LDAP-based authentication provides a viable alternative with its ability to securely store and retrieve user data in a structured manner, giving administrators granular control over user access rights.
Discovering the Essence of LDAP Authentication
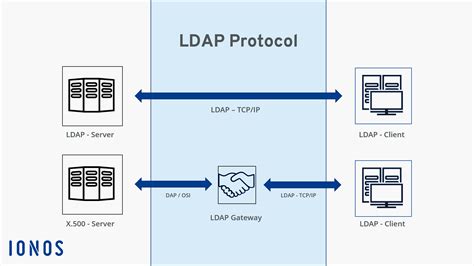
Understanding the fundamental principles behind the implementation of Lightweight Directory Access Protocol (LDAP) authentication is crucial for navigating the intricacies of secure user identification and access control within a Linux environment.
Delving deep into the realms of LDAP authentication unveils a world where user credentials are stored in a centralized directory, facilitating efficient management and authentication processes across multiple systems and applications. By employing the LDAP protocol, organizations can streamline user authentication, enhance security, and achieve seamless integration between diverse platforms and services.
Explore the workings of LDAP authentication, where hierarchical data structures, known as directories, store and organize user information. Learn how LDAP leverages the client-server architecture, where a server, acting as the directory service, responds to queries from clients, empowering authentication services and verifying user identities.
Comprehending the significance of distinguished names, attribute-value pairs, and object classes within an LDAP directory enables system administrators to configure and manage user accounts effectively. Understand the role of access control policies, such as access control lists (ACLs), in determining and enforcing user privileges based on their membership in various groups and organizational units.
Immerse yourself in the world of LDAP authentication, and unlock the potential for secure, centralized user management and seamless integration within the Linux ecosystem.
Discovering the Fundamentals of LDAP
Exploring the fundamental aspects of LDAP (Lightweight Directory Access Protocol) allows us to delve into the essential components that make up this powerful protocol. LDAP serves as a directory service model, providing a standardized method of accessing, searching, and managing directory information. By understanding the core principles of LDAP, we can gain insight into how it works and its significance in various systems and applications.
Directory Services In the realm of computer systems, directory services play a crucial role in managing and organizing vast amounts of data. LDAP acts as a framework for directory services and provides a structured way of storing and retrieving information. | Protocol Concept LDAP operates on a client-server model, where clients send requests to the server to perform specific operations on the directory information. These operations include searching for specific entries, adding new entries, modifying existing entries, and more. |
Data Hierarchy LDAP organizes information in a hierarchical structure known as the Directory Information Tree (DIT). This tree-like structure consists of entries that represent objects, such as users, groups, and resources, and is based on the X.500 directory standard. | Attribute Types LDAP uses attribute types to define the characteristics of directory entries. Attributes can store different types of information, such as names, addresses, phone numbers, and more. Understanding attribute types is essential for effectively leveraging LDAP for authentication and access control purposes. |
Search Filters LDAP enables searching for specific entries based on a set of search filters. These filters allow users to narrow down the search results by specifying criteria such as attribute values, object classes, and more. Mastering search filters is crucial for efficient data retrieval. | Integration with Systems LDAP has widespread adoption and integration with various systems and applications. Its ability to provide a centralized repository of user and group information makes it an ideal choice for authentication and authorization in Linux environments, among others. |
By exploring these foundational concepts of LDAP, we gain valuable insights into its role in directory services, its protocol mechanisms, data organization, attribute types, search filters, and integration capabilities. This understanding serves as a solid foundation for implementing LDAP-based authentication and leveraging its benefits in Linux and other environments.
Understanding the Mechanism of LDAP Authentication
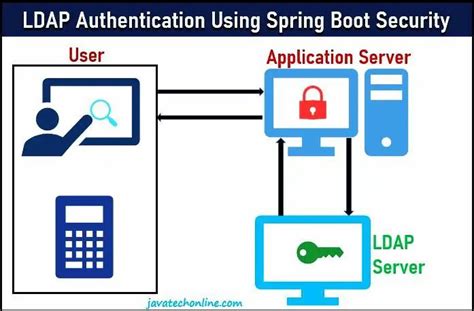
Exploring the functionality and operation of LDAP authentication provides valuable insights into the secure access management system employed by various platforms. This section aims to shed light on the inner workings of LDAP authentication, delving into its fundamental principles and mechanisms.
LDAP authentication is a process that validates user credentials against a central directory service. This authentication method relies on the Lightweight Directory Access Protocol (LDAP), a protocol used for accessing and managing directory information. By leveraging this protocol, organizations can establish a centralized database that contains user identities and associated attributes, such as passwords and permissions.
During the LDAP authentication process, a client application initiates a connection with an LDAP server. The client sends a query to the server, requesting authentication for a specific user or group. The server then searches its directory for the specified user entry and verifies the provided credentials. This verification may involve comparing the entered password hash value with the stored hash value for that user.
If the user's credentials match those stored in the directory, the LDAP server sends a success response to the client. This response typically includes additional information about the user, such as group memberships or access permissions. These details can be crucial for establishing appropriate authorization levels across different systems and resources.
LDAP authentication offers various advantages, including centralized management of user identities, simplified user account provisioning, and enhanced security. By employing LDAP, organizations can streamline the authentication process, reduce the burden of password management, and ensure consistent access controls across multiple platforms.
Preparing the Linux Server for LDAP
In order to establish LDAP-based authentication on your Linux server, certain preparatory steps need to be taken. This section will guide you through the necessary procedures to ensure a smooth implementation.
- Ensure that your Linux server is running a compatible operating system version.
- Install the required packages and dependencies for LDAP integration.
- Configure the firewall settings to allow LDAP traffic.
- Create a dedicated LDAP user account with appropriate permissions.
- Verify that the server has proper network connectivity and DNS resolution.
- Set up secure communication with SSL/TLS for LDAP.
By following these steps, you will create a strong foundation for integrating LDAP-based authentication on your Linux server. It is crucial to complete these preparations accurately to ensure the smooth functionality of the LDAP system.
Setting Up OpenLDAP in a Linux Environment

Establishing the OpenLDAP service on a Linux operating system is a crucial step in implementing LDAP-based authentication. This section will outline the process of installing and configuring OpenLDAP, a robust and flexible directory server.
Begin by obtaining the OpenLDAP software package from a trusted source. It is essential to download the appropriate version that aligns with your Linux distribution. Once the package is acquired, follow the instructions provided by the OpenLDAP project to install it on your Linux machine.
After successful installation, the next step involves configuring the OpenLDAP server. This entails defining the directory structure, setting up access controls, and configuring the necessary database backend. The configuration file for OpenLDAP, typically located in /etc/openldap/slapd.conf, should be carefully edited to specify important parameters such as the server's listening port, security settings, and logging options.
Once the server is configured, it is advisable to perform initial population of the directory with necessary data. This could involve creating the necessary organizational units (OUs), groups, and user entries within the directory structure. The ldapadd command can be utilized to import LDIF (LDAP Data Interchange Format) files that contain the required information into the OpenLDAP server.
Lastly, it is essential to start the OpenLDAP service and ensure that it automatically starts upon system boot. This can typically be achieved by executing commands such as service slapd start and chkconfig slapd on. Verifying the successful startup of the service and checking for any error messages are crucial steps in the deployment process.
In conclusion, installing OpenLDAP on a Linux system is a vital part of enabling LDAP-based authentication. By properly configuring and populating the directory server, organizations can establish a secure and efficient authentication system for their Linux environment.
Configuring LDAP Client on Linux
In this section, we will explore how to set up the LDAP client configuration on a Linux system. We will delve into the necessary steps and parameters needed to establish a connection with the LDAP server for user authentication and access control.
Firstly, it is essential to configure the LDAP client to communicate with the LDAP server efficiently. This involves defining the appropriate parameters in the LDAP client configuration file, which can vary depending on the distribution or version of Linux used. These parameters enable the client to locate and authenticate users against the LDAP directory.
To start the configuration process, locate the LDAP client configuration file, often found at /etc/ldap/ldap.conf or /etc/openldap/ldap.conf. Open the file using a text editor and carefully modify the necessary settings.
One of the crucial settings is specifying the LDAP server's URL, which points the client to the LDAP server. Ensure that the address provided is accurate and accessible from the Linux system. Additionally, parameters such as base DN and bind DN must be configured to define the starting point for LDAP search operations and the distinguished name used for authentication, respectively.
The LDAP client configuration file also allows for specifying various options to fine-tune the client's behavior. These options include timeout settings, logging levels, and encryption requirements, among others. It is advisable to refer to the documentation for the specific Linux distribution or LDAP client software for a comprehensive list of available parameters and their possible values.
Once the necessary modifications are made, save the LDAP client configuration file and restart any LDAP-related services on the Linux system to apply the changes. It is recommended to test the LDAP client configuration by attempting to authenticate a user against the LDAP server to ensure that the setup is functioning correctly.
In conclusion, configuring the LDAP client on Linux involves modifying the LDAP client configuration file to establish a connection with the LDAP server. Defining the LDAP server's URL, base DN, and bind DN are essential parameters for successful authentication. Additional options can also be configured to customize the client's behavior. Remember to save the changes and test the setup to verify its correctness.
Configuring LDAP Server
In this section, we will explore the process of setting up and configuring an LDAP server, a fundamental step in establishing a centralized authentication system. By implementing an LDAP server, organizations can efficiently manage user information, system access, and group memberships.
First and foremost, it is important to plan the LDAP server structure, including the directory tree layout, schema design, and access control policies. This strategic planning ensures that the server can effectively organize and store user information in a secure and efficient manner.
Next, the LDAP server software needs to be installed on the designated Linux server. This can be accomplished by following the specific installation instructions provided by the chosen LDAP server software provider. Once installed, the server needs to be properly configured by editing the relevant configuration files.
When configuring the LDAP server, it is crucial to define the server's hostname, port number, and security settings. Additionally, the administrator must set up the appropriate access controls to ensure that only authorized users and applications can access the directory server's data.
After configuring the basic server settings, it is necessary to define the directory structure and schema. This involves creating the necessary object classes and attribute types to accurately represent the data stored in the LDAP server. Customizing the schema enables organizations to tailor the server to their specific needs and requirements.
Finally, testing the LDAP server's functionality is essential before deploying it in a production environment. This involves verifying that users can successfully authenticate against the server, access and modify their own information, and perform necessary operations within the defined access controls.
By carefully following the steps outlined in this section, administrators can effectively configure an LDAP server, laying the foundation for successful LDAP-based authentication in their Linux environment.
Organizing the LDAP Directory Structure
In this section, we will explore the process of structuring the LDAP directory in an efficient manner to enhance the overall functionality and organization of the system. By carefully designing the directory structure, we can ensure that the LDAP-based authentication system operates smoothly and provides seamless access control for users.
Planning the LDAP Directory Hierarchy: Before setting up the LDAP directory, it is essential to plan the hierarchy that suits the organization's needs. This involves defining the organizational units (OUs) and their subordinates, such as groups, departments, and individuals. A well-structured hierarchy allows for easy administration and management of user accounts and permissions.
Creating the OUs: Once the directory hierarchy is planned, the next step is to create the organizational units (OUs) accordingly. Each OU represents a specific division or entity within the organization, such as departments, teams, or locations. These OUs serve as containers for various user entries and help in categorizing and organizing them.
Defining Object Classes and Attributes: In LDAP, object classes define the types of entries that can be created in each OU. By defining appropriate object classes, we can specify what attributes and characteristics each entry can possess. This ensures consistency and uniformity across the directory structure, enabling streamlined management and search functionalities.
Assigning Access Control Policies: To maintain secure access to the LDAP directory, it is crucial to assign proper access control policies. These policies determine who can read, write, modify, or delete the entries within each OU. By carefully configuring access control, we can enforce strict data protection and privacy measures, safeguarding sensitive information.
Implementing Naming Conventions: A well-defined naming convention for entries within the LDAP directory is essential for easy identification and retrieval. By establishing consistent naming rules, we can ensure that entries are organized logically and can be located efficiently when searching or browsing the directory.
Documenting the Directory Structure: Lastly, it is crucial to document the LDAP directory structure thoroughly. This documentation serves as a reference for administrators and ensures the continuity of the LDAP setup even in the case of personnel changes. It provides insights into the overall architecture and aids in troubleshooting and future expansions or modifications.
By following these best practices in setting up the LDAP directory structure, organizations can efficiently manage user authentication and access control, leading to enhanced security and streamlined operations.
Managing LDAP Users and Groups
In this section, we will explore the process of defining and managing users and groups in an LDAP-based authentication system. By understanding the concepts and procedures involved, you will gain the ability to organize and control access to resources effectively.
LDAP offers a flexible and scalable mechanism for defining users and groups, allowing for centralized management and authentication across multiple systems. By defining user entries in the LDAP directory, you can grant or restrict access to various applications, services, and resources based on a user's membership in specific groups.
When defining LDAP users, it is important to consider the attributes and properties associated with each entry. These attributes can include information such as usernames, passwords, email addresses, and other relevant details. By carefully configuring these attributes, you can ensure that user entries are accurate and comprehensive.
In addition to individual user entries, LDAP also allows for the creation of groups, which serve as containers for multiple users. Group entries can be defined with their own unique attributes and properties, allowing for convenient management and organization. By placing users into appropriate groups, you can assign specific privileges and permissions to individuals based on their role or responsibilities.
By following proper conventions and guidelines, you can establish a robust and well-structured LDAP-based authentication system. This will not only enhance security but also streamline user management processes, making it easier to add, modify, or remove users and groups as needed. Understanding the principles outlined in this section will empower you to effectively define LDAP users and groups within your network infrastructure.
Creating a Secure User Authentication System with LDAP Integration on a Linux Environment
Introduction:
Enhancing the security of user authentication is vital in today's interconnected world. In order to implement a robust and reliable authentication system, organizations often turn to LDAP (Lightweight Directory Access Protocol) integration on their Linux systems. This section elucidates how to set up and configure LDAP authentication, substituting traditional password-based authentication methods with a more secure and efficient alternative. By seamlessly integrating LDAP with Linux, organizations can bolster their security measures while streamlining user management processes.
Benefits of LDAP Authentication:
- Enhanced Security: LDAP authentication provides a centralized user management system, reducing the risk of password leaks and unauthorized access.
- Single Sign-On Integration: LDAP allows users to access multiple systems and services with a single set of credentials, improving convenience and usability.
- Efficient User Management: With LDAP, administrators can easily add, remove, or modify user accounts, groups, and access privileges across the entire network.
- Scalability and Flexibility: LDAP provides a scalable solution, allowing organizations to expand their user base without significant infrastructure changes.
Configuring LDAP Authentication: Step-by-Step Process:
- Setting up the LDAP Server: Begin by installing and configuring an LDAP server on your Linux environment. Ensure proper security measures are in place, such as encryption protocols and access controls.
- Creating the LDAP Database: Define the structure and attributes of the LDAP database, including user information, access rights, and group memberships. This step involves designing an appropriate directory schema.
- Populating the LDAP Database: Add user accounts to the LDAP database, along with relevant information such as usernames, passwords, email addresses, and other necessary attributes.
- Configuring Linux for LDAP Integration: Adjust the Linux system to integrate with the LDAP server. This may involve modifying the PAM (Pluggable Authentication Modules) configuration files and modifying the system's NSS (Name Service Switch) configuration to allow LDAP queries.
- Testing and Troubleshooting: Validate the LDAP authentication setup by attempting to log in with LDAP credentials. Troubleshoot any potential issues, such as network connectivity problems, misconfigurations, or permission conflicts.
- Implementing Additional Security Measures: Enhance the security of the LDAP authentication system by implementing measures like account lockouts, password policies, and two-factor authentication.
Conclusion:
By implementing LDAP authentication in a Linux environment, organizations can fortify their user authentication system, improving security and streamlining user management. This comprehensive guide outlines the advantages of LDAP, the step-by-step process to configure it, and the importance of additional security measures. With proper implementation, LDAP authentication can significantly enhance the security posture of an organization's Linux infrastructure.
Crash Course, Active Directory, DHCP & DNS for Entry Level Tech Support
Crash Course, Active Directory, DHCP & DNS for Entry Level Tech Support by cobuman 553,485 views 1 year ago 1 hour, 23 minutes
LDAP - How to Install and Configure OpenLDAP Client on Ubuntu
LDAP - How to Install and Configure OpenLDAP Client on Ubuntu by ToTatCa 5,389 views 8 months ago 7 minutes, 22 seconds
FAQ
What is LDAP-based authentication?
LDAP-based authentication is a method of authenticating users by using the Lightweight Directory Access Protocol (LDAP) to retrieve user account information from a central directory server.
Why would I want to set up LDAP-based authentication in Linux?
Setting up LDAP-based authentication in Linux offers several benefits, such as centralizing user management and authentication, allowing users to use a single set of credentials for multiple systems, and simplifying the user account management process.
How do I install and configure an LDAP server in Linux?
To install and configure an LDAP server in Linux, you can use software packages like OpenLDAP or 389 Directory Server. These packages provide the necessary tools and configurations to set up the LDAP server and define the directory structure and user accounts.
What is the process of integrating Linux with an LDAP server for authentication?
The process of integrating Linux with an LDAP server for authentication involves modifying the PAM (Pluggable Authentication Modules) configuration files on the Linux system to use the LDAP authentication module. This includes specifying the LDAP server's address, port, and the directory structure to use for user authentication.
Can I use LDAP-based authentication with existing user accounts in Linux?
Yes, it is possible to use LDAP-based authentication with existing user accounts in Linux. You can import the existing user accounts into the LDAP server and modify the PAM configuration files to authenticate the users against the LDAP server. This process requires careful planning and testing to ensure a smooth transition.
What is LDAP-based authentication?
LDAP-based authentication refers to the process of using the Lightweight Directory Access Protocol (LDAP) to authenticate and grant access to users on a Linux system. LDAP is a protocol used for accessing and maintaining distributed directory information services, making it an ideal choice for centralized user authentication.
Why would I want to set up LDAP-based authentication in Linux?
Setting up LDAP-based authentication in Linux offers several benefits. It allows for centralized user management, where all user information is stored in a central LDAP directory rather than in individual system files. This simplifies user administration and enables seamless authentication across multiple Linux systems. Additionally, LDAP-based authentication provides enhanced security and control by enforcing uniform access policies and enabling easier user account management.




