
In the vast realm of digital security, there exists a powerful and essential component that ensures the protection of critical systems and sensitive data. This key authentication mechanism, known by a distinct name that resonates with security aficionados worldwide, plays a pivotal role in the realm of Windows security.
Exploring the intricacies of this authentication process allows IT professionals and system administrators to establish a solid foundation for safeguarding their networks against potential threats and unauthorized access. While the name of this instrument might evade us for the moment, its significance in the realm of digital security should not go unnoticed.
Within the universe of Windows operating systems, this security mechanism acts as a gatekeeper, granting or denying access to resources based on an intricate web of cryptography, cryptography that allows for secure communication and authorized interactions within a network. This cornerstone of digital security, in all its complexity and technical brilliance, captivates the minds of those who dare to delve into its inner workings.
Understanding the Fundamentals of Kerberos Authentication
Ensuring secure authentication is a critical aspect of any network or server setup. In order to establish a secure connection and validate the identity of users and services within a Windows environment, the concept of Kerberos authentication comes into play. While configuring Kerberos on a Windows Server may seem daunting, it is essential to understand the underlying principles of this authentication protocol.
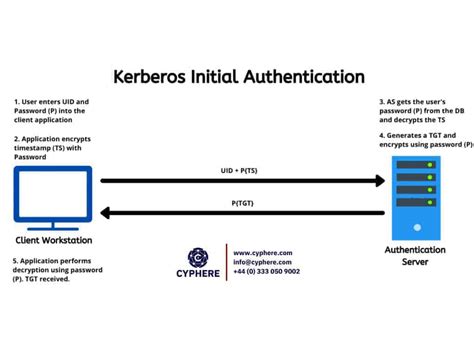
Kerberos authentication is a network protocol that provides strong authentication for client/server applications over a non-secure network. It utilizes a trusted third-party entity known as the Key Distribution Center (KDC) to authenticate both users and services. By using symmetric key cryptography, Kerberos ensures that only the intended recipient can decipher the authentication information.
The core concept behind Kerberos authentication can be likened to a ticket-based system. When a user or service requests access to a resource within the network, a ticket is issued by the KDC. This ticket is then presented to the resource server, which verifies its authenticity using the shared secret key. This process enables secure and efficient authentication without the need for constantly transmitting passwords over the network.
Key principles within the Kerberos authentication model include the realm, principal, and ticket granting ticket (TGT). The realm represents a logical administrative domain, while the principal refers to a unique identity within that domain. The TGT is the initial ticket obtained from the KDC, granting the user or service access to request further tickets for specific resources.
By comprehending the basics of Kerberos authentication, administrators can better configure and troubleshoot its implementation within a Windows Server environment. Understanding the role of the KDC, the principles involved, and the ticket-based system provides a solid foundation for establishing secure and efficient communication across the network.
Setting up Kerberos Authentication on a Windows Server
In this section, we will explore the process of configuring the authentication mechanism known as Kerberos on a Windows Server environment. By utilizing this powerful security protocol, administrators can establish a trustworthy and robust authentication framework for their network infrastructure.
To begin with, it is crucial to comprehend the fundamental concepts and principles behind Kerberos. This protocol ensures secure communication between clients and servers by utilizing a ticket-based authentication mechanism. By employing encrypted tickets and a trusted third-party authentication server, Kerberos greatly enhances the security of your network.
Before diving into the configuration process, it is important to gather the necessary prerequisites. These may include a Windows Server operating system, proper administrative credentials, and a thorough understanding of the network infrastructure. With these components in place, administrators can proceed with configuring Kerberos authentication.
Next, we will explore the step-by-step process of configuring Kerberos within a Windows Server environment. This includes activities such as setting up a Key Distribution Center (KDC), defining realms and domains, configuring service principal names (SPNs), and establishing trust relationships with other entities.
Throughout the configuration process, it is essential to ensure that all necessary components are correctly installed, configured, and integrated. Additionally, proper testing and validation measures should be conducted to verify the successful implementation of Kerberos authentication.
In conclusion, by following the guidelines outlined in this section, administrators can successfully configure Kerberos authentication on their Windows Server environment. Utilizing this robust security protocol will enhance the overall security and integrity of the network infrastructure, ensuring secure communication and trusted authentication between clients and servers.
Step-by-Step Guide: Establishing Kerberos Configuration on a Microsoft Server Platform
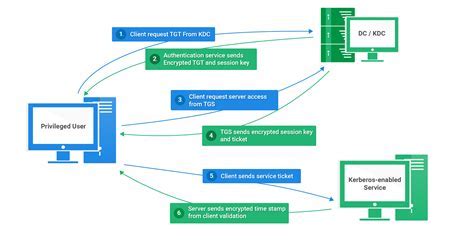
Setting up a secure authentication system for your Windows Server environment is of utmost importance in today's digitally-driven age. By implementing Kerberos, a trusted protocol for network authentication, you can ensure that your server communications are protected from unauthorized access and data breaches. This step-by-step guide will walk you through the process of configuring Kerberos on your Windows Server, allowing you to establish a robust and reliable authentication system.
| Step | Description |
|---|---|
| 1 | Installing and Configuring Active Directory Services |
| 2 | Creating and Configuring a User Account for Kerberos |
| 3 | Configuring Firewall Settings for Kerberos Communication |
| 4 | Enabling Kerberos Authentication in IIS |
| 5 | Testing and Troubleshooting Kerberos Configuration |
Once you have followed these step-by-step instructions, you will have successfully set up Kerberos on your Windows Server. This will ensure that your server environment is equipped with a secure authentication system, providing peace of mind and protecting sensitive data from unauthorized access. By implementing Kerberos, you can enhance the overall security of your Windows Server environment, creating a strong foundation for your network communication.
Setting up the Active Directory Domain Services Role
In this section, we will explore the process of installing and configuring the Active Directory Domain Services (AD DS) role on your Windows Server environment. This role is crucial for managing and organizing your network resources, including user accounts, security policies, and group management.
Before proceeding with the installation, it is essential to understand the significance of AD DS. It serves as the foundation for a Windows Server domain, allowing central authentication and authorization services, as well as ensuring seamless integration with other network services and applications.
By installing the AD DS role, you enable your Windows Server to function as a domain controller. This role empowers you to create a domain and establish a hierarchical structure for managing your network. Additionally, it facilitates the integration of scalable security measures, such as Kerberos authentication protocol, which enhances the security and privacy of your network resources.
To install the AD DS role, you need to follow a series of steps, including selecting the appropriate server, initiating the installation wizard, configuring the role settings, and validating the installation process. These steps will be covered in detail in the following sections.
By the end of this process, you will have successfully set up the AD DS role on your Windows Server, laying the foundation for implementing Kerberos authentication and other advanced network functionalities.
Managing Kerberos Realms and Domains
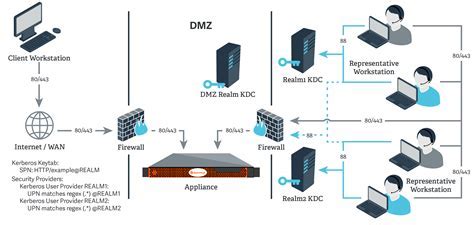
In this section, we will explore the process of configuring realms and domains for Kerberos authentication on a Windows Server environment. By defining and organizing realms and domains, administrators can establish secure authentication and access control mechanisms within their network.
Understanding Realms
Kerberos realms serve as administrative boundaries that define a set of network resources and entities. By delineating different realms, organizations can maintain separate authentication services and access policies for different parts of their infrastructure. This enables enhanced security and segregation of network resources.
Example sentence: Kerberos realms act as administrative boundaries, allowing organizations to divide their infrastructure into distinct security domains.
Configuring Realms and Domains
Configuring realms and domains involves defining the mapping between Kerberos realms and Windows Server domains. This mapping allows for the integration of Kerberos authentication with the existing Active Directory infrastructure. Additionally, administrators can establish trust relationships between realms to enable cross-realm authentication.
Example sentence: By configuring realms and domains, administrators can establish a seamless connection between Kerberos and Active Directory, enabling unified authentication across the network.
Managing Trust Relationships
Trust relationships between realms enable users and services from one realm to access resources in another realm. Proper management of trust relationships ensures secure and authenticated cross-realm communication. Administrators can define rules and policies to govern access permissions and controls between realms.
Example sentence: Effectively managing trust relationships between realms ensures secure and controlled access to resources across multiple administrative boundaries.
By understanding and properly configuring Kerberos realms and domains, administrators can establish a robust authentication framework that enhances security and facilitates seamless access to network resources.
Active Directory: Episode 6 - IIS Windows Authentication
Active Directory: Episode 6 - IIS Windows Authentication by Professor Andrew 33,692 views 3 years ago 14 minutes, 14 seconds

FAQ
What is Kerberos and why is it important for Windows Server?
Kerberos is a network authentication protocol that provides strong security for client/server applications by using secret key cryptography. It is important for Windows Server because it allows for secure authentication and authorization, helping to prevent unauthorized access to resources.
How do I enable Kerberos authentication on Windows Server?
To enable Kerberos authentication on Windows Server, you need to first install the Kerberos client software. This can be done through the Server Manager tool by selecting the Kerberos client feature and following the installation wizard. Once installed, you can configure Kerberos authentication by modifying the server's security settings and configuring the appropriate service principal names (SPNs).
What are the benefits of using Kerberos authentication?
There are several benefits of using Kerberos authentication on Windows Server. Firstly, it provides strong security by encrypting the authentication process, making it difficult for attackers to intercept sensitive information. Secondly, Kerberos supports mutual authentication, where both the client and the server verify each other's identities. Finally, Kerberos supports single sign-on, allowing users to access multiple network resources without needing to enter their credentials again.
What are some common issues that can occur when configuring Kerberos on Windows Server?
When configuring Kerberos on Windows Server, some common issues that can occur include: incorrect configuration of SPNs, which can result in authentication failures; clock synchronization issues between the client and server, which can cause authentication tickets to be rejected; and firewall rules blocking the necessary Kerberos traffic, preventing authentication from occurring. It is important to carefully follow the configuration steps and troubleshoot any errors that may arise.




