In today's digital landscape, ensuring the security and privacy of your online presence has become paramount. As more and more businesses and individuals rely on the internet for communication, commerce, and data exchange, there is an urgent need to protect sensitive information from prying eyes and potential threats. One critical aspect of this is enabling secure communications through the use of HTTPS.
HTTPS, or Hypertext Transfer Protocol Secure, is a protocol designed to establish an encrypted connection between a client and a server. This encryption ensures that the data exchanged between the two parties remains confidential and cannot be intercepted or tampered with by unauthorized individuals. By implementing HTTPS, website owners can guarantee the integrity and privacy of their users' personal and financial information.
When it comes to securing a Linux EC2 instance, employing Docker can greatly simplify the process. Docker brings a lightweight and scalable containerization solution, allowing developers to package applications and their dependencies into isolated containers. This not only enhances the portability and flexibility of the application, but also provides an additional layer of security.
This article aims to guide you through the process of enabling HTTPS on your Linux EC2 instance using Docker. By following these steps, you can ensure that the communication between your server and clients is encrypted, safeguarding sensitive data from potential threats. So, let's dive in and explore the steps required to make your Linux EC2 instance HTTPS-ready using Docker.
Setting up a Secure Linux Virtual Machine on Amazon Web Services

In this section, we will explore the process of configuring a secure Linux virtual machine on the Amazon Web Services cloud platform. By following this guide, you will learn how to establish a secure and reliable environment for hosting applications and services.
We will delve into the necessary steps for creating and launching a Linux EC2 instance on the AWS cloud, taking into consideration the importance of security measures and best practices. Throughout this guide, we will explore various aspects such as selecting suitable instance types, securing the instance with SSH key pairs, and implementing proper network configurations.
Furthermore, we will discuss the significance of choosing an appropriate base Amazon Machine Image (AMI) for your Linux instance, which ensures a stable and reliable foundation for your applications. We will also explore the different Linux distributions available on AWS and their specific advantages.
Additionally, we will touch upon the importance of establishing a robust security group configuration for your instance, which enables you to control inbound and outbound traffic effectively. We will also cover the process of assigning elastic IP addresses to provide a static and persistent public IP for your instance.
By the end of this guide, you will have a comprehensive understanding of the steps involved in setting up a secure Linux virtual machine on the AWS cloud, empowering you to create a highly available and secure environment for your applications and services.
Installing Docker on the Linux Cloud Server
In this section, we will explore the process of setting up Docker on a Linux-based cloud server, allowing for the efficient and secure deployment of containerized applications.
Introduction
Deploying applications on Linux-based cloud servers is becoming increasingly popular due to the flexibility and scalability they offer. Docker, a leading containerization platform, further enhances this process by providing a lightweight and efficient way to package and distribute applications.
Step 1: Updating System Packages
Before installing Docker, it is essential to ensure that all system packages are up to date. This can be done by running the appropriate package manager commands, such as 'apt-get update' or 'yum update' depending on the Linux distribution in use.
Step 2: Installing Docker
Once the system packages are updated, the next step is to install Docker. This can be accomplished by using the package manager's installation command, such as 'apt-get install docker' or 'yum install docker'.
Step 3: Verifying Docker Installation
To ensure that Docker is installed correctly, it is recommended to verify the installation by running the 'docker version' command. This will display information about the installed Docker version, demonstrating that it is successfully installed and running.
Conclusion
By following the steps outlined in this section, you will have successfully installed Docker on your Linux-based cloud server. This will enable you to take advantage of containerization capabilities, allowing for the efficient deployment and management of applications.
Generating SSL/TLS certificates for secure communication
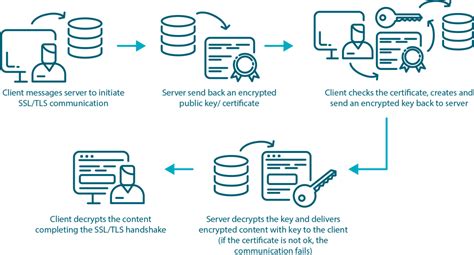
In the realm of secure communication over the internet, SSL/TLS certificates play a vital role in encrypting data and ensuring the integrity and authenticity of online interactions. This section explores the process of generating SSL/TLS certificates, which are essential for enabling secure HTTPS encryption on Linux EC2 instances using Docker.
To establish secure connections, SSL/TLS certificates are required to authenticate the identity of the server and encrypt the data exchanged between the server and the client. This certificate generation process involves several steps, including the creation of a certificate signing request (CSR), obtaining a certificate from a trusted certificate authority (CA), and configuring the certificate on the appropriate server.
The first step in generating SSL/TLS certificates is the creation of a CSR, which contains relevant information about the organization or individual requesting the certificate. The CSR includes details such as the domain name, organization name, location, and public key. This information helps validate the identity of the certificate requester and ensures that the certificate is issued to the correct entity.
Once the CSR is generated, it needs to be submitted to a trusted CA for certificate issuance. The CA verifies the information in the CSR, validates the identity of the requester, and signs the certificate using their trusted digital signature. This process ensures that the certificate can be trusted by clients when establishing secure connections.
After obtaining the signed certificate from the CA, it needs to be configured on the Linux EC2 instance running Docker. This involves installing the certificate on the appropriate web server or load balancer, updating the server configuration to enable HTTPS, and binding the certificate to the appropriate domain or subdomain. These steps ensure that secure communication can take place between clients and the Linux EC2 instance.
In conclusion, generating SSL/TLS certificates is a crucial step in enabling secure HTTPS encryption on Linux EC2 instances using Docker. The process entails creating a CSR, obtaining a certificate from a trusted CA, and configuring the certificate on the server. By following these steps, you can ensure secure and encrypted communication between your Linux EC2 instance and its clients.
Configuring Nginx as a reverse proxy for Secure Web Connections
In this section, we will explore the setup and configuration of Nginx as a reverse proxy to handle secure web connections. By utilizing Nginx's reverse proxy capabilities, we can securely redirect incoming HTTPS requests to the appropriate Docker containers running on our Linux EC2 instance. This ensures that sensitive user data remains encrypted and protected throughout the communication process.
| Key Concepts | Configuration Steps |
|
|
By following these steps, you will be able to effectively configure Nginx as a reverse proxy for HTTPS communication, ensuring secure and encrypted connections between your Linux EC2 instance and the Docker containers running within it.
Testing and Verifying Configuration for Secured Communication on the Linux EC2 Instance

When it comes to ensuring the establishment of a secure connection on a Linux EC2 instance, it is crucial to conduct thorough testing and verification procedures. In this section, we will explore the steps required to verify and test the HTTPS configuration on the Linux EC2 instance, thus ensuring the confidentiality, integrity, and authenticity of the transmitted data.
Configure a Docker Nginx Reverse Proxy Image and Container
Configure a Docker Nginx Reverse Proxy Image and Container 来自Cameron McKenzie 79,640次观看 1年前 10分钟51秒钟
FAQ
What is HTTPS and why is it important for a website?
HTTPS (Hypertext Transfer Protocol Secure) is a secure version of HTTP that encrypts the data sent between a website and a user's browser. It ensures that the communication between the website and the user is private and secure, protecting sensitive information such as login credentials, personal data, and financial transactions from being intercepted or tampered with by attackers.
Why would I want to enable HTTPS on my Linux EC2 instance?
Enabling HTTPS on your Linux EC2 instance ensures that the communication between your website and its users is secure. It adds an extra layer of protection to sensitive data and helps build trust with your users. HTTPS is especially important if your website collects or transmits sensitive information, such as login credentials, personal details, or payment information.
What is Docker and why would I use it to enable HTTPS on my Linux EC2 instance?
Docker is an open-source platform that allows you to automate the deployment, scaling, and management of applications. It uses containerization to package applications and their dependencies into isolated environments called containers. Docker provides a consistent and reproducible environment for running your applications, making it easier to deploy and manage them. Using Docker to enable HTTPS on your Linux EC2 instance allows you to isolate the HTTPS configuration within a container, making it easier to manage and update.
What is HTTPS?
HTTPS stands for Hypertext Transfer Protocol Secure. It is a secure version of the HTTP protocol used for secure communication over a computer network. It encrypts the data sent between the web browser and the server, ensuring privacy and integrity.




