Protecting your digital assets in the ever-evolving online landscape is of paramount importance. In today's interconnected world, the safeguarding of sensitive information has become a critical task for individuals and organizations alike. One essential element of a robust security strategy is the implementation of a reliable defense mechanism, which is where the concept of a firewall comes into play.
Creating a strong fortification for your Linux-based operating system against potential threats is crucial to maintaining the integrity and confidentiality of your data. A firewall acts as a vigilant guardian, continuously monitoring and controlling the incoming and outgoing network traffic. By filtering unauthorized access attempts, a firewall ensures that only trusted connections are established, effectively safeguarding your system.
So, how can you employ an effective firewall strategy on your Linux machine? This comprehensive guide will walk you through the steps required to configure and set up a firewall, fortifying your Linux environment and enhancing the overall security posture. By understanding the fundamentals of firewall implementation and utilizing the right tools, you can create a robust defense that adapts to the ever-changing threat landscape.
The Significance of Firewall Implementation on a Linux Environment
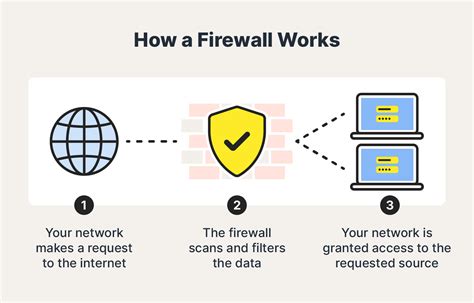
In the realm of security, safeguarding a Linux operating environment from potential threats and unauthorized access is paramount. An indispensable tool for achieving this is the firewall, which acts as a protective barrier by filtering incoming and outgoing network traffic based on a set of predefined rules. Understanding the importance of implementing a firewall in a Linux system is crucial for maintaining the integrity, confidentiality, and availability of sensitive data and resources.
By deploying a firewall, you enhance your system's security posture by effectively fortifying its defenses against various network-based attacks and intrusions. The firewall acts as a gatekeeper, inspecting incoming and outgoing network traffic to identify and block any potentially malicious activity or unauthorized connections. This proactive measure prevents unapproved access attempts and safeguards the system from potential compromises.
A well-configured firewall also assists in preventing data breaches, as it meticulously examines the information packets traveling through the network. By analyzing traffic patterns and scrutinizing packet content, the firewall ensures that only authorized communications are allowed and potentially harmful data is rejected, reducing the risk of data leakage or exposure.
Additionally, a firewall aids in enforcing network policies and controlling network traffic flow. By defining and applying specific rules and access policies, administrators can regulate which services or protocols are permitted or restricted, effectively managing the system's resources and minimizing vulnerability exposure. This fine-grained control empowers system administrators to tailor the firewall settings according to their organization's specific security requirements.
Overall, comprehending the significance of implementing and configuring a firewall on a Linux system is crucial to mitigate potential security risks and protect critical assets. The firewall acts as a robust line of defense, diligently monitoring and filtering network traffic, preventing unauthorized access attempts, and ensuring the confidentiality, integrity, and availability of the Linux environment.
Understanding Different Types of Firewall Solutions for Linux Systems
When it comes to securing your Linux system, implementing a robust firewall is of utmost importance. A firewall acts as a protective barrier between your computer or network and potential external threats. It works by monitoring and controlling incoming and outgoing network traffic based on predefined security rules.
Network-based firewalls: These are positioned at the entry points of a network, such as the border between your local area network (LAN) and the internet. Network-based firewalls filter and inspect traffic at the network layer, examining data packets to determine whether they should be allowed into or out of the network. They can be in the form of hardware appliances or software running on dedicated machines, providing an additional layer of protection.
Host-based firewalls: Unlike network-based firewalls that protect an entire network, host-based firewalls are implemented at an individual host or server level. These firewalls are designed to protect the specific system on which they are installed, monitoring and controlling traffic both from the network and between applications running on the host itself. Host-based firewalls offer granular control, allowing administrators to define specific rules for inbound and outbound traffic on a per-host basis.
Application-level firewalls: As the name suggests, application-level firewalls operate at the application layer of the network stack. These firewalls provide advanced filtering capabilities by examining the content and context of application protocols, allowing them to make more informed decisions when it comes to granting or denying access. Application-level firewalls are particularly useful in situations where specific applications or services need to be tightly controlled.
Stateful firewalls: Stateful firewalls maintain a record of the state of network connections passing through them. By keeping track of the context of each connection, stateful firewalls can make intelligent decisions about whether to allow or block traffic. These firewalls provide an added layer of security by examining the state and history of packets, allowing them to detect and prevent potentially malicious activities.
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS): While not strictly firewalls, IDS and IPS solutions work in tandem with firewalls to enhance the security of your Linux system. IDS continuously monitors network traffic, searching for signs of suspicious or malicious activity. When an intrusion is detected, IDS can generate alerts or take other actions, such as blocking the offending source IP. IPS goes a step further by actively preventing the identified threats from reaching their targets, providing real-time protection against network attacks.
Each type of firewall solution has its own strengths and weaknesses, and the choice depends on various factors such as the specific requirements of your system, the level of control needed, and the nature of the threats you are aiming to protect against. Understanding the different types of firewalls available for Linux systems will empower you to make informed decisions when it comes to implementing an effective and secure firewall solution.
Comparing Packet Filtering and Application Layer Firewalls
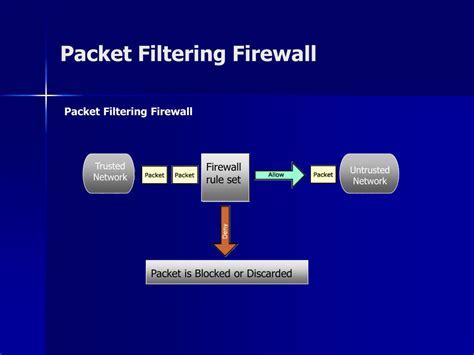
In the realm of network security, there are different approaches to protecting your system from unauthorized access and potential threats. Two commonly used methods are packet filtering firewalls and application layer firewalls. While both aim to secure your network, they differ in their mechanisms and level of protection.
- Packet Filtering Firewalls: These firewalls operate at the network layer and examine packets based on pre-defined rules. They analyze the source and destination IP addresses, ports, and protocols to determine whether to allow or block the traffic. Packet filtering firewalls provide a basic level of security by filtering packets based on their IP attributes.
- Application Layer Firewalls: Unlike packet filtering firewalls, application layer firewalls work at the application layer of the networking stack. They go beyond the basic packet attributes and analyze the content of the packets, including application-specific data. By understanding the context and content of the traffic, these firewalls can provide more granular control and detect more complex threats.
Packet filtering firewalls are typically faster and more efficient due to their simpler rule sets. They also offer a high level of compatibility with various network protocols. On the other hand, application layer firewalls provide better protection against application-specific vulnerabilities and attacks. They can examine the payload of the packets and block suspicious or malicious traffic, even if it meets the basic criteria defined by packet filtering firewalls.
It is important to note that both types of firewalls can be used in conjunction to provide layered security for your Linux system. By combining packet filtering firewalls with application layer firewalls, you can create a robust defense mechanism that protects your network from a wide range of threats. Understanding the strengths and weaknesses of each approach will help you make informed decisions when setting up your firewall configuration.
Securing Your Operating Environment: A Step-by-Step Guide to Enhancing Your Linux Security
In this section, we will explore the essential steps to bolstering the protection of your Linux operating system. By implementing a robust firewall, you can fortify your system against unauthorized access and potential security threats. Through easy-to-follow instructions and practical examples, we will guide you through the process of setting up a reliable and effective firewall, ensuring the safety of your valuable data.
Step 1: Evaluating Your Security Needs Understanding your unique security requirements is crucial before diving into the firewall setup. We will help you analyze potential risks, identify sensitive data, and establish security rules that align with your specific needs. |
Step 2: Researching Firewall Solutions Choosing the most suitable firewall solution can be challenging. We will present you with different options available for Linux systems, highlight their key features, and provide useful insights to help you make an informed decision. |
Step 3: Installing and Configuring the Firewall Once you have selected a preferred firewall solution, we will guide you through the installation process, ensuring proper configuration to maximize your system's security. We will explain essential settings and parameters, enabling you to tailor the firewall to meet your specific requirements. |
Step 4: Defining Firewall Rules Creating effective firewall rules is essential for protecting your Linux system. We will provide you with practical examples and guide you in defining rules to allow or deny access based on various criteria, such as IP addresses, ports, or protocols. |
Step 5: Testing and Monitoring Your Firewall After setting up your firewall, it is crucial to verify its effectiveness and continuously monitor it for potential vulnerabilities. We will show you how to perform comprehensive tests and recommend powerful monitoring tools to keep your system protected round the clock. |
By following this step-by-step guide, you will be equipped with the knowledge and skills to enhance the security of your Linux environment through a well-configured and efficiently managed firewall.
Installation and Configuration of Firewall on Linux
In this section, we will explore the process of setting up a robust security mechanism on your Linux system to protect it from unauthorized access and potential cyber threats. We will delve into the step-by-step installation and configuration of a reliable firewall, which acts as a barrier between your computer network and external malicious entities.
| Step 1: | Exploring Firewall Options |
| Step 2: | Evaluating Firewall Rules and Policies |
| Step 3: | Choosing the Right Firewall Solution |
| Step 4: | Installing the Firewall Software |
| Step 5: | Configuring Firewall Settings |
| Step 6: | Testing the Firewall Setup |
The first step entails familiarizing oneself with the available firewall options, understanding their features and functionalities, and selecting the most suitable one for your specific requirements. Next, we will delve into the intricacies of firewall rules and policies, outlining their significance in establishing the desired level of security.
Following the evaluation of firewall rules, we will proceed with the selection of an appropriate solution that aligns with your operating system and network environment. Once the decision is made, we can move on to the installation process, ensuring smooth integration of the firewall software into your Linux system.
Upon successful installation, we will guide you through the configuration phase, where you will learn how to customize firewall settings according to your network's needs and security objectives. Additionally, we will cover essential topics such as port configuration, IP address whitelisting, and intrusion detection system integration.
Finally, we will test the effectiveness of the firewall setup by simulating various attack scenarios and assessing the system's ability to block unauthorized access attempts. We will provide troubleshooting tips and best practices for maintaining an up-to-date and secure firewall architecture.
By the end of this guide, you will have the necessary knowledge and skills to establish and manage a robust firewall on your Linux system, safeguarding your network from potential threats and minimizing the risk of unauthorized access.
Customizing Protection Policies on Open Source Operating Environment
When it comes to configuring and fine-tuning the security of a Linux-based operating system, one must consider the ability to customize and adapt firewall rules to suit specific needs. In this section, we will explore the process of tailoring protection policies on an open source environment.
Defining Custom Firewall Rules
One of the key aspects of customizing protection policies on a Linux system is the ability to define personalized firewall rules. These rules serve as the foundation for controlling network traffic and determining access permissions for various services and applications running on the system.
Configuring Traffic Filtering
In order to grant or restrict network access, Linux provides various tools and techniques to configure traffic filtering. By utilizing these tools, system administrators can selectively admit or deny incoming and outgoing traffic based on specific criteria, such as IP addresses, protocols, ports, and more.
Implementing Advanced Rule Sets
For more complex security requirements, it may be necessary to implement advanced rule sets that go beyond the basic filtering capabilities. This can involve the use of conditionals, state tracking, and connection tracking modules, enabling administrators to create more sophisticated and granular firewall rules.
Monitoring and Fine-Tuning
Once custom firewall rules have been implemented, it is crucial to regularly monitor and fine-tune them to ensure effectiveness and efficiency. This involves analyzing traffic patterns, detecting potential vulnerabilities, and adjusting rules accordingly to optimize system security.
Conclusion
Customizing firewall rules on a Linux-based operating system allows for a tailored and robust network security configuration. By defining personalized rules, configuring traffic filtering, implementing advanced rule sets, and conducting continuous monitoring and fine-tuning, administrators can optimize the protection of their open source environment.
Defining Inbound and Outbound Traffic Rules
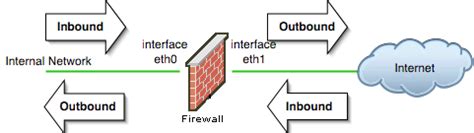
In the realm of securing your Linux environment, it is essential to establish a robust set of rules governing the flow of network traffic. These rules define how incoming and outgoing data is handled, ensuring that only authorized connections are allowed while mitigating potential security vulnerabilities.
Enhancing Network Security: Applying Custom Firewall Rules based on Application-Specific Requirements
When it comes to fortifying the security of your Linux-powered system, it is vital to go beyond the basic firewall configurations. One powerful approach to bolstering network defense involves the implementation of application-specific firewall rules tailored to the unique requirements of different software applications.
By enabling application-specific firewall rules, you can exercise granular control over network access and effectively mitigate risks associated with individual applications. Through the precise configuration of these rules, you can monitor and regulate the communication paths and behaviors of specific applications running on your Linux system.
The utilization of application-specific firewall rules allows you to detect and prevent unauthorized access attempts, block potentially malicious traffic, and protect sensitive data in a more targeted manner. This approach empowers administrators to tailor network security measures according to the specific needs and circumstances of their Linux environment.
- Identify critical applications: Begin by identifying the applications that require a higher level of network security due to their nature, level of importance, or potential vulnerabilities.
- Define rule sets: Create custom rule sets that specify the allowed and restricted network communication patterns for each identified application.
- Conduct traffic analysis: Monitor incoming and outgoing traffic to identify patterns and establish baseline behavior for each application.
- Implement rule configurations: Using the appropriate firewall management tools, apply the predefined rule sets to restrict or permit network traffic based on the defined criteria.
- Review and adapt: Regularly review and adjust the application-specific firewall rules to adapt to changes in your network environment or the application's behavior.
By taking these steps to enhance network security through application-specific firewall rules, you can strengthen your Linux system against potential threats and achieve a higher level of control over your network traffic.
Configuring Firewall Settings for Web Servers and Database Servers
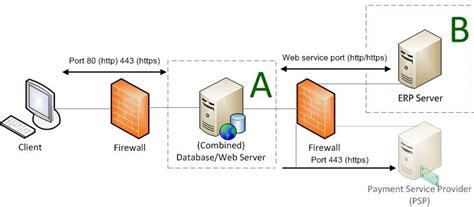
In this section, we will discuss the necessary steps to optimize the security of your web servers and database servers by configuring firewall settings. By implementing these techniques, you can effectively safeguard your servers from unauthorized access, malicious attacks, and potential data breaches.
When it comes to protecting web servers and database servers, having a reliable firewall is crucial. Firewalls act as a barrier between your servers and external networks, filtering and controlling incoming and outgoing traffic. By configuring firewall settings, you can define specific rules and restrictions to allow or deny access based on various parameters, such as IP addresses, ports, protocols, and more.
First, it is important to identify the specific services and ports that your web servers and database servers require for their normal operation. This can include HTTP (port 80), HTTPS (port 443), SSH (port 22), FTP (port 21), MySQL (port 3306), and many others, depending on your specific setup. By understanding the necessary services, you can create firewall rules to allow traffic only for these required ports while blocking all others.
Additionally, it is recommended to implement a DMZ (Demilitarized Zone) architecture for your servers. A DMZ is a separate network segment that sits between your internal network and the external network, providing an additional layer of security. By placing your web servers and database servers in the DMZ, you can isolate them from the rest of your infrastructure while still allowing necessary communication with external entities.
Furthermore, consider implementing network address translation (NAT) to further secure your servers. NAT allows you to mask the IP addresses of your internal servers, making it more difficult for potential attackers to identify and target them. This technique can effectively hide the actual IP addresses of your web servers and database servers, adding an extra layer of anonymity and protection.
Regularly reviewing and updating your firewall rules is essential to ensure that your web servers and database servers remain secure. Monitor your servers' logs, perform periodic security audits, and stay updated on the latest security vulnerabilities and patches. By staying proactive, you can continuously enhance the security of your servers and mitigate potential risks.
By carefully configuring your firewall settings for web servers and database servers, you can reinforce the protection of your Linux systems, minimizing the risk of unauthorized access and potential security threats. Implementing these best practices will help safeguard your valuable data and ensure the smooth operation of your servers.
Beginner's Guide to Set up a Full Network using OPNsense
Beginner's Guide to Set up a Full Network using OPNsense מאת Home Network Guy 37,887 צפיות לפני 6 חודשים 41 דקות
FAQ
What is a firewall?
A firewall is a network security device that monitors and filters incoming and outgoing network traffic based on predetermined security rules.
Why do I need to set up a firewall on my Linux system?
Setting up a firewall on your Linux system is crucial to protect your system from unauthorized access, malware, and other network threats.
How can I check if a firewall is already installed on my Linux system?
You can check if a firewall is already installed on your Linux system by running the command "sudo ufw status" or "sudo iptables -L" which will show the status and rules of the firewall, respectively.
Can you recommend any firewall software for Linux?
Sure! Some popular firewall software for Linux are UFW (Uncomplicated Firewall), Firewalld, and Iptables. They are all powerful and easy to use.
What is a firewall?
A firewall is a security device or software that monitors and controls incoming and outgoing network traffic based on predetermined security rules.




