In the realm of digital frontiers, operating systems wield the power to revolutionize how we interact with our data. Among these modern marvels, one system stands above the rest, offering unparalleled versatility, security, and control: the revered Linux. With its robust architecture and dynamic ecosystem, Linux empowers users to harness the true potential of their servers, opening the gateway to optimized file access.
The key to unlocking this realm lies within the realm of user permissions, serving as the fundamental building blocks of Linux's file access structure. By granting or restricting privilege levels to specific entities or groups, administrators can meticulously tailor access controls, ensuring sensitive data remains safe and accessible only to those with the proper authorization. However, navigating the intricacies of user permissions can appear daunting at first glance.
This article will serve as your guide through the intricate labyrinth of Linux's file access, providing valuable insights and step-by-step instructions on how to navigate this virtual maze. Whether you're a seasoned Linux enthusiast seeking to expand your skill set or a newcomer eager to improve your server's security, this comprehensive exploration of user permissions will equip you with the knowledge and tools necessary to optimize file access on your Linux system.
Understanding File Permissions and User Roles in a Linux Environment
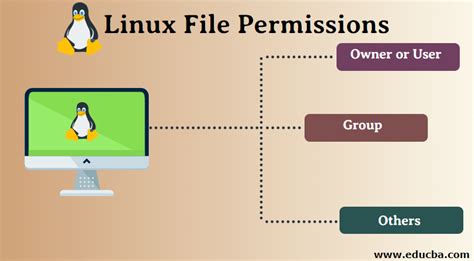
In a Linux system, the way files are accessed and managed is controlled by a set of permissions and user roles, ensuring maximum security and control over the system. By understanding these concepts and how they work together, you can effectively manage file access and ensure that only authorized users have the necessary permissions to interact with specific files or directories.
File permissions refer to the specific rights and restrictions assigned to a file or directory, determining who can read, write, or execute them. These permissions are categorized into three groups: owner, group, and others. Each group has its own set of permissions, allowing or restricting various actions.
Additionally, user roles play a critical role in managing file access on a Linux server. User roles provide a way to group users with similar permissions and access requirements, simplifying the process of assigning and managing file access rights. By assigning users to specific roles, you can ensure that they only have the necessary privileges to perform their tasks without compromising the overall system security.
| Permission | Description |
|---|---|
| Read | Allows the user to view the contents of a file or directory. |
| Write | Enables the user to make changes to a file or directory. |
| Execute | Allows the user to run executable files or access directories. |
Understanding file permissions and user roles is essential for managing file access in a Linux environment. By properly configuring these settings, you can ensure that sensitive files are protected and accessible only to authorized users, enhancing the overall security and integrity of your system.
Understanding File Permissions
In the world of Linux, every file and directory has its own set of permissions that dictate who can access, modify, or execute them. Understanding these file permissions is crucial for effectively managing your server and maintaining the security of your data.
Overview of File Permissions
File permissions are essentially a set of rules that determine what actions a user or group of users can perform on a particular file or directory. There are three main types of permissions:
- Read: This permission allows a user to view the contents of a file or the list of files in a directory.
- Write: With write permission, a user can make changes to a file or create, delete, and rename files within a directory.
- Execute: Execute permission grants a user the ability to execute a file as a program or access a directory.
Note that these permissions are assigned separately for three different categories of users: the file owner, the group owner, and others.
Permission Representation and Symbolic Notation
In Linux, permissions are represented using a combination of letters and symbols. Each permission type has its own symbol:
- r indicates read permission
- w indicates write permission
- x indicates execute permission
The permissions for each category of users are represented in a 10-character sequence. The first character represents the file type, while the following nine characters represent the three sets of permissions for the file owner, group owner, and others.
Changing File Permissions
To change file permissions in Linux, you can use the chmod command followed by the desired permission settings. Permissions can be modified using either symbolic or numeric notation. Symbolic notation uses letters as mentioned earlier, while numeric notation assigns a value to each permission type.
Understanding and properly managing file permissions in Linux is essential for maintaining the security and integrity of your server and its files. By grasping the concepts outlined above, you will be empowered to control access to files and directories effectively.
Configuring User Access Control
In the realm of managing user permissions and security on a Linux-based system, it is crucial to have a robust access control configuration in place. This ensures that authorized users are granted appropriate rights and privileges while safeguarding against unauthorized access and potential system vulnerabilities.
Defining User Roles and Permissions: As a critical step in configuring user access control, it is essential to define distinct user roles and assign appropriate permissions to each role. User roles can be categorized based on their responsibilities, such as administrators, managers, or general users. Once roles are established, permissions can be assigned to each role, specifying what actions and operations they are allowed to perform.
Implementing Role-Based Access Control: Role-Based Access Control (RBAC) is a widely adopted approach for managing user access control on Linux servers. RBAC allows for centralized administration and simplifies the process of granting or revoking permissions by associating them with roles instead of individual users. This enables easier management of access control policies, especially in environments with a large number of users.
Utilizing Access Control Lists: Access Control Lists (ACLs) provide a more granular level of control over file and directory permissions. ACLs allow for defining permissions not only for the owner and group but also for specific users or groups, allowing more flexibility in managing access to files and directories. This enables fine-tuning of permissions based on individual requirements or project-specific needs.
Enforcing Strong Password Policies: User access control should also include the implementation of strong password policies. This involves enforcing password complexity requirements, regular password expiration, and account lockouts after a certain number of unsuccessful login attempts. By promoting the use of strong passwords, the risk of unauthorized access due to weak or easily guessable passwords is minimized.
Regular Auditing and Review: To maintain the integrity of user access control, regular auditing and review of user permissions and roles should be conducted. This helps identify any discrepancies or vulnerabilities in the access control configuration and allows for timely updates or adjustments to ensure the system remains secure.
Note: Properly configuring user access control is essential for maintaining a secure Linux server environment. By defining user roles, implementing RBAC, utilizing ACLs, enforcing strong password policies, and conducting regular auditing and review, system administrators can effectively manage access rights and minimize the risk of unauthorized access or security breaches.
Creating a Shared Folder for Collaborative File Management
In this section, we will explore the process of establishing a designated folder on your Linux system that can be accessed and modified by multiple users. By enabling file sharing, you can facilitate seamless collaboration and efficient management of documents and other resources among a team. We will delve into the necessary steps to configure the shared folder and adjust its permissions to ensure secure and smooth file accessibility for authorized users.
Step 1: Creating the Shared Folder
The initial step involves defining a shared folder on your Linux server. This folder will serve as a centralized location where team members can upload, download, and update files. By giving it a meaningful name and placing it in a convenient location, you can optimize usability and streamline file management. Remember to choose a directory that is easily accessible for all intended participants.
Step 2: Setting Proper Permissions
Once the shared folder is created, it is crucial to configure appropriate permissions to govern access and modification rights. By setting up user groups and assigning specific permissions to each group or individual, you can control who can read, write, or execute files within the shared folder. Implementing careful access management ensures data security and minimizes the risk of unauthorized modifications.
Step 3: Establishing User Accounts
To enable file sharing, it is essential to create user accounts for each individual who needs access to the shared folder. By granting appropriate user privileges and aligning them with the designated user groups, you can ensure that each team member can interact with the shared files based on their assigned permissions. Proper user account setup guarantees that the right individuals possess the necessary access to manage the collaborative folder effectively.
Step 4: Accessing the Shared Folder
After completing the initial setup steps, it is time to provide users with access to the shared folder. Each individual can connect to the Linux server using various protocols such as SSH, FTP, or Samba, depending on their specific requirements and the available network configuration. By authenticating their user credentials, team members can securely connect to the shared folder, view its contents, and perform authorized operations.
Step 5: Monitoring and Maintenance
Once the file sharing system is up and running, it is crucial to monitor its usage and ensure continuous maintenance. Regularly check for any potential security issues, make necessary updates to user permissions or groups, and regularly backup the shared folder to prevent data loss. By proactively managing the file sharing system, you can guarantee its reliability, security, and optimal performance.
By following these steps, you will be able to set up file sharing on your Linux server, enabling efficient collaboration and seamless file management among a designated group of users.
[MOVIES] [/MOVIES] [/MOVIES_ENABLED]FAQ
Can I set up file access on a Linux server?
Yes, you can easily set up file access on a Linux server. By configuring permissions and user groups, you can control who can read, write, or execute files and directories.
What are the steps to set up file access on a Linux server?
To set up file access on a Linux server, you first need to identify the files or directories you want to control access to. Then, you can use the chmod command to modify the file permissions, and use the chown and chgrp commands to change the owner and group of the files. Finally, you can create user groups and assign users to those groups to control access.
What are file permissions in Linux?
File permissions in Linux determine who can read, write, or execute a file. There are three types of permissions: read (r), write (w), and execute (x). These permissions can be set for three different groups: the owner of the file, the group the file belongs to, and others.
How can I change file permissions on a Linux server?
To change file permissions on a Linux server, you can use the chmod command followed by the permission code and the file name. For example, to give read and write permissions to the owner of a file, you can use the command "chmod u+rw filename".
Can I restrict file access to specific users on a Linux server?
Yes, you can restrict file access to specific users on a Linux server. By assigning users to different user groups and setting the appropriate file permissions, you can control which users can access certain files or directories.




