In today's digital landscape, ensuring the security of your network infrastructure is paramount. As organizations continue to rely on technology for their daily operations, the need for robust authentication mechanisms becomes increasingly crucial. One such mechanism that has gained popularity is Kerberos, a secure protocol for authentication and authorization. In this article, we will explore how to effectively manage event logging in a Windows environment while leveraging the power of Kerberos.
Authentication and event logging play a vital role in monitoring and safeguarding your network against potential threats and unauthorized access. By configuring the appropriate settings, you can ensure that every event related to authentication and authorization is securely logged and readily available for analysis.
However, managing event logging efficiently can be a challenging task, especially when dealing with the complexities of Kerberos. The ability to track and log every authentication attempt accurately can provide valuable insights into potential security breaches or unusual activity. Through effective configuration and fine-tuning, you can leverage the power of Kerberos to enhance your network's security posture.
Understanding the Significance of Windows Event Logging
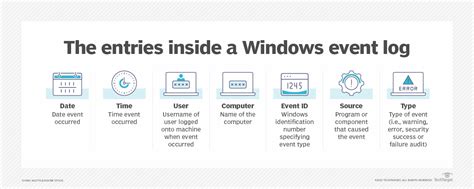
Within the broader context of configuring Windows Event Logging with Kerberos, it is important to first gain a solid understanding of the role and importance of event logging in the Windows operating system. Windows Event Logging plays a critical role in monitoring and tracking various events that occur within a computer system. These events can include both system-level activities and user interactions, providing valuable insights into the overall health, security, and performance of the system.
By recording and documenting events in a structured and organized manner, Windows Event Logging enables administrators to analyze and troubleshoot issues, detect potential security threats, and ensure compliance with various regulatory requirements. Event logging serves as a reliable source of information for system administrators, allowing them to identify patterns, pinpoint root causes of problems, and make informed decisions to enhance system functionality and security.
Without a comprehensive understanding of Windows Event Logging, it would be challenging to effectively configure and optimize it in conjunction with Kerberos, a network authentication protocol. Therefore, familiarizing oneself with the fundamentals of event logging is crucial to establish a solid foundation for successfully configuring and leveraging its capabilities in combination with Kerberos.
An Overview of Windows Event Logging and the Significance of System Monitoring
Windows Event Logging plays a crucial role in monitoring the performance and security of a system. It provides valuable information about different events and activities happening within the system infrastructure. By analyzing these logs, administrators can gain insights into system operations, identify potential issues or security breaches, and take necessary action promptly.
System Monitoring: System monitoring is an essential practice in managing the overall health and performance of a computer system or network. It involves actively monitoring various system components, including hardware, software, applications, and network connections, to ensure their proper functioning and identify any deviations or anomalies that may indicate potential risks or performance issues.
Event Logging: Event logging is a mechanism that captures detailed information about specific events occurring within a system. These events can include user actions, device operations, security-related activities, error conditions, and more. By logging these events, administrators can easily examine and review the history of system activities, helping them to troubleshoot problems, analyze system behavior, and track any significant changes or occurrences.
Importance in System Monitoring: Windows Event Logging plays a crucial role in system monitoring as it allows administrators to monitor real-time and historical events, providing a comprehensive overview of system operations. By enabling event logging, organizations can gain visibility into user activities, system health, security incidents, and various other critical aspects. This enables timely detection of anomalies, potential threats, or performance issues, facilitating proactive measures and ensuring the overall stability and security of the system.
In conclusion, event logging and system monitoring are inseparable components for maintaining a well-functioning and secure system infrastructure. Through the collection and analysis of event logs, administrators can proactively identify and address potential issues, ensuring the efficient operation of the system and safeguarding valuable resources and data.
Exploring the Kerberos Protocol and Its Advantages in Authentication and Security
Authentication and security are fundamental aspects of any computer system. In the context of network communication, the use of a robust authentication protocol is essential to protect sensitive data and ensure the trustworthiness of users and services.
The Kerberos protocol stands out as a reliable and widely adopted authentication protocol, known for its strong security features and efficiency. With its roots in the MIT Project Athena, Kerberos has evolved into a trusted solution that provides mutual authentication between clients and servers in a networked environment.
At the core of Kerberos lies its ticket-based authentication mechanism, which utilizes symmetric encryption techniques to establish secure communication channels. This protocol enables users to prove their identities to servers and gain access to resources, all while preventing unauthorized access and protecting against common security threats.
One notable advantage of using Kerberos is its ability to provide single sign-on (SSO) capabilities. With SSO, users only need to authenticate once to access multiple resources within a domain, reducing the need for repeated authentication and enhancing overall user experience. This streamlined approach not only improves productivity but also reduces the risk of password-related vulnerabilities.
Moreover, Kerberos employs the concept of mutual authentication, offering protection against various attacks such as replay attacks and man-in-the-middle attacks. By relying on timestamp-based authentication and session keys, Kerberos ensures the integrity and confidentiality of communication, making it a reliable choice for secure network environments.
As organizations continue to prioritize the security of their systems, understanding the Kerberos protocol and its advantages becomes crucial. By leveraging its robust authentication mechanisms, companies can enhance their network security posture, protect sensitive data, and mitigate the risks associated with unauthorized access.
In conclusion, the Kerberos protocol offers a powerful solution for authentication and security, combining strong encryption and mutual authentication to protect network resources. With its advantages including single sign-on capabilities and resistance against common attacks, Kerberos stands as a valuable tool in ensuring the integrity and trustworthiness of network communication.
Enhancing Windows Event Tracking Configuration
In this section, we will explore how to optimize the configuration of your event tracking system on a Windows operating system. By fine-tuning the settings and parameters related to event logging, you can ensure a more efficient and effective logging process, leading to improved security and troubleshooting capabilities.
By adjusting the event tracking configuration, you can tailor the system to meet your specific needs and requirements. This includes defining the level of detail captured in the event logs, controlling the types of events that are logged, and selecting the appropriate log storage options. Additionally, we will discuss techniques for filtering and analyzing the log data to extract valuable insights and detect potential security incidents.
Furthermore, we will delve into the various strategies for managing event logs, including establishing retention policies, automating log maintenance tasks, and integrating with third-party log management solutions. By implementing these best practices, you can ensure that your event logging system remains scalable, reliable, and compliant with industry standards.
Throughout this section, we will provide step-by-step instructions and practical tips to guide you through the process of configuring and fine-tuning your Windows event logging system. By following these recommendations, you can optimize the utilization of event logs in your organization, thereby enhancing security, troubleshooting, and compliance capabilities.
Step-by-Step Guide: Achieving Efficient Monitoring through Windows Event Logging Setup
In this section, we will provide you with a detailed step-by-step guide on how to properly configure and set up Windows Event Logging to ensure effective monitoring of your system. By following these instructions, you will be able to enhance your system's security, identify potential issues, and optimize performance, without relying on Kerberos authentication.
Step 1: Determining Logging Requirements
Prior to the configuration process, it is crucial to assess your monitoring needs and establish the specific events you want to log. By identifying the critical areas and events, you can focus your efforts on configuring Windows Event Logging accordingly.
Step 2: Understanding Event Log Types
An essential aspect of setting up Windows Event Logging is understanding the different log types available, such as Security, Application, and System logs. We will explore the characteristics of each log type, enabling you to make informed decisions on which logs you should enable and monitor.
Step 3: Configuring Windows Event Logging Settings
Once you have determined your logging requirements and familiarized yourself with the available log types, it is time to configure Windows Event Logging settings. We will guide you through the process of accessing and modifying the necessary configurations using the Event Viewer tool, allowing you to optimize logging based on your specific needs.
Step 4: Enabling Advanced Logging Features
To further enhance your monitoring capabilities, we will cover advanced features available in Windows Event Logging, including Event Forwarding, Custom Views, and Task Scheduler integration. These features provide more flexibility and customization options to meet the unique monitoring requirements of your system.
Step 5: Analyzing Event Logs
Once your Windows Event Logging is set up, it is crucial to know how to interpret and analyze the collected event logs effectively. We will provide you with guidance on using filtering, sorting, and searching techniques within the Event Viewer tool to identify valuable insights and troubleshoot any potential issues efficiently.
Step 6: Monitoring and Alerting Best Practices
Lastly, we will discuss best practices for monitoring and alerting using Windows Event Logging, including setting up centralized log management, establishing proper alert thresholds, and integrating with third-party monitoring tools. These practices ensure proactive monitoring and timely response to critical system events.
By following this step-by-step guide, you will be able to configure Windows Event Logging to its full potential, empowering you with an effective monitoring solution for your system without the reliance on Kerberos authentication.
Understanding Kerberos Authentication in Windows
Kerberos authentication plays a crucial role in securing access to resources in the Windows operating system environment. This section aims to provide a comprehensive understanding of Kerberos authentication and its significance in ensuring the integrity and confidentiality of user and system interactions.
- Introduction to Kerberos Authentication
- Principles of Kerberos Authentication
- Kerberos Authentication Process
- Ticket Granting Service (TGS) and Ticket-Granting Ticket (TGT)
- Key Distribution Center (KDC) and Active Directory
- Types of Kerberos Authentication Tokens
- Advantages and Limitations of Kerberos Authentication
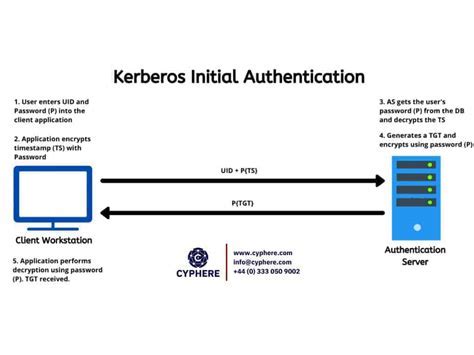
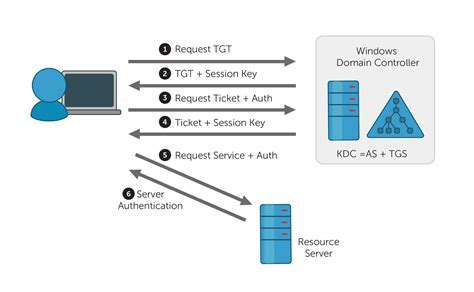
The concept of Kerberos authentication revolves around the exchange of encrypted tickets between clients, servers, and the Key Distribution Center (KDC) in a network. Understanding the principles of Kerberos authentication, including the use of shared secret keys, timestamps, and session tickets, is essential to comprehend the entire authentication process.
The Kerberos authentication process involves the client requesting a Ticket-Granting Ticket (TGT) from the Key Distribution Center (KDC), which is then used to obtain service tickets from the KDC for accessing specific resources. This process ensures the mutual authentication between the client and the server, as well as secure communication through the encrypted tickets.
In a Windows environment, the Active Directory serves as the Key Distribution Center (KDC), managing the authentication process and securely storing the shared secret keys. The integration of Kerberos authentication with Active Directory provides a centralized and efficient approach to managing user access and ensuring the security of the overall system.
Kerberos authentication tokens, namely TGTs and service tickets, are integral components of the authentication process. Understanding the types of tokens, such as ticket flags and session keys, allows for a deeper insight into the mechanisms employed by Kerberos to verify the authenticity and integrity of user requests.
While Kerberos authentication offers numerous advantages, including strong encryption and minimal reliance on password storage, it is important to be aware of its limitations. Factors such as clock synchronization and network availability can impact the effectiveness of Kerberos authentication in a real-world environment.
By comprehending the complexities of Kerberos authentication, system administrators and security professionals can effectively configure and troubleshoot Kerberos-related issues, ensuring the integrity and security of Windows-based systems.
An in-depth exploration of the inner workings of Kerberos authentication in the Windows OS
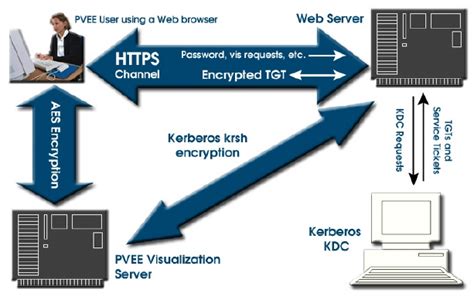
In this section, we delve into the intricacies of how Kerberos authentication functions within the Windows operating system. We will examine the underlying mechanisms and processes involved in establishing secure communication and verifying the identities of users and services. This comprehensive analysis aims to provide a deeper understanding of the inner workings of Kerberos authentication, shedding light on the key components and protocols involved.
To comprehend the intricacies of Kerberos authentication, it is essential to first grasp the fundamental concepts and principles behind its operation. We will explore the concepts of tickets, principals, realms, and key distribution centers (KDCs), elucidating how these elements play crucial roles in the authentication process. Through a step-by-step examination, we will trace the journey of a user request, from the initial authentication request to the final validation of the user's identity.
Furthermore, we will uncover the cryptographic algorithms and techniques that underpin Kerberos authentication and ensure the confidentiality and integrity of authentication messages. Understanding the encryption and decryption processes not only enhances our knowledge of the technology but also offers insights into the security measures employed to safeguard sensitive information within the Windows OS.
Moreover, we will explore the various factors that can impact the overall performance and reliability of Kerberos authentication in a Windows environment. From network latency to ticket expiration policies, we will delve into the considerations and configurations that can be fine-tuned to optimize the authentication process while maintaining a robust security posture.
By comprehensively examining the intricacies of Kerberos authentication in the Windows operating system, this section aims to equip readers with a deep understanding of the underlying mechanisms and protocols. Understanding the inner workings of Kerberos authentication empowers system administrators and security professionals to effectively configure and troubleshoot authentication processes, ensuring a secure and reliable operating environment.
| Keywords: | Kerberos authentication, Windows OS, authentication mechanisms, tickets, principals, realms, key distribution centers, KDCs, cryptographic algorithms, security measures, performance optimization. |
Enabling Kerberos Audit Trail
In this section, we will explore the steps to activate the Kerberos Audit Trail feature. By enabling this functionality, you can track and monitor various Kerberos events that occur within your Windows system. This enhanced visibility allows you to identify and respond to potential security threats and access violations in a timely manner.
Enabling the Kerberos Audit Trail involves configuring your Windows system to record and log specific Kerberos events. These events can include successful or failed Kerberos authentication attempts, ticket-granting ticket (TGT) requests, authorization failures, and more. By understanding and analyzing these events, you can gain insights into potential security breaches and enhance the overall security posture of your environment.
To enable Kerberos event logging, you need to modify the security policy settings on the target Windows system. This can be achieved by using the Group Policy Management Editor or the Local Security Policy tool. By choosing the appropriate policy settings, you can specify which Kerberos events to log, the maximum log size, and the retention period of the event logs.
Once the Kerberos event logging is enabled, the system will start capturing and storing the defined Kerberos events in the Windows Event Log. You can then leverage event log management tools or security information and event management (SIEM) systems to centrally collect, analyze, and correlate these Kerberos events. This centralized approach allows for efficient monitoring and detection of any anomalous activities related to Kerberos authentication in your network.
In conclusion, enabling Kerberos event logging provides valuable insights into the security and integrity of your Windows system. By properly configuring and monitoring the Kerberos Audit Trail, you can proactively identify and mitigate potential security risks, ensuring a secure and reliable network environment.
Improving Troubleshooting and Analysis with Enhanced Kerberos Event Logging
Enhancing the Kerberos event logging functionality can significantly improve troubleshooting and analysis capabilities within a Windows environment. By enabling and configuring Kerberos event logging, administrators gain valuable insights into authentication and authorization events, empowering them to swiftly identify and resolve potential security issues.
1. Enable Kerberos Event Logging
To begin harnessing the power of Kerberos event logging, it is crucial to enable this feature. This involves modifying the appropriate registry settings to ensure that Kerberos events are recorded and stored for further analysis. By enabling Kerberos event logging, you open the door to a wealth of information related to authentication processes, ensuring a comprehensive view of security events.
2. Configure Kerberos Event Logging Levels
After enabling Kerberos event logging, it is essential to fine-tune the logging levels to suit the specific needs and requirements of your environment. By utilizing different logging levels, you can control the granularity of the recorded events, ensuring that the log file does not become overwhelmed with unnecessary information. Careful configuration of the logging levels allows for more focused troubleshooting and analysis, granting a clearer perspective on potential security issues.
3. Analyze Kerberos Event Logs
With Kerberos event logging enabled and properly configured, it is crucial to regularly analyze the generated event logs. This involves using appropriate tools or scripts to parse and interpret the logged events, uncovering crucial information about authentication and authorization actions. By analyzing Kerberos event logs, administrators can proactively identify anomalies, detect potential attacks or breaches, and take appropriate remedial actions in a timely manner.
4. Leverage Kerberos Event Logging for Troubleshooting
In addition to security analysis, Kerberos event logging provides essential troubleshooting capabilities. The logged events reveal valuable insights into authentication-related issues, such as failed logon attempts, ticket requests, or key distribution center (KDC) errors. By leveraging these logs, administrators can quickly pinpoint the root cause of authentication problems, enabling speedy resolution and minimizing downtime.
5. Periodically Review Kerberos Event Logging Configuration
Lastly, it is crucial to periodically review and update the Kerberos event logging configuration. As security landscapes evolve and new threats arise, adjusting the logging levels, auditing settings, and event retention policies ensures continued effectiveness in troubleshooting and analysis efforts. Regularly revisiting the Kerberos event logging configuration guarantees that the log captures relevant events and aligns with the organization's security goals.
By enabling and configuring Kerberos event logging, administrators empower themselves with a powerful tool for troubleshooting and analysis. This proactive approach to monitoring Kerberos events ensures that potential security issues are identified promptly, enabling timely remediation actions to safeguard the Windows environment.
Understanding Kerberos Event Logs
In this section, we will delve into the detailed analysis of Kerberos event logs and how to interpret the information they provide. Kerberos event logs serve as a valuable resource for troubleshooting authentication issues and understanding the flow of Kerberos tickets in a Windows environment.
To effectively interpret Kerberos event logs, it is essential to familiarize ourselves with the various event codes and their meanings. Each event code represents a specific action or stage in the Kerberos authentication process, offering valuable insights into potential security issues or anomalies. By understanding the significance of these event codes, administrators can gain a deeper understanding of the Kerberos protocol and troubleshoot authentication errors more effectively.
| Event Code | Description |
|---|---|
| 4768 | A Kerberos authentication ticket (TGT) was requested. |
| 4771 | An attempt was made to create a Kerberos service ticket. |
| 4776 | A Kerberos authentication ticket request failed. |
| 4778 | A Kerberos ticket was renewed. |
| 4779 | A Kerberos ticket was invalidated. |
By carefully analyzing the event logs, administrators can identify potential security threats such as suspicious authentication attempts or unauthorized access attempts. Additionally, the interpretation of Kerberos event logs can aid in identifying configuration errors or issues in the Kerberos infrastructure, enabling administrators to take appropriate corrective actions.
It is important to note that interpreting Kerberos event logs requires a comprehensive understanding of both the Kerberos protocol and the Windows environment. With this knowledge, administrators can effectively troubleshoot authentication issues, enhance security, and maintain a robust and secure Kerberos infrastructure.
How to configure Kerberos security Microsoft server
How to configure Kerberos security Microsoft server by ALittleBitOfTech Again 15,489 views 3 years ago 2 minutes, 5 seconds
FAQ
What is Windows Event Logging?
Windows Event Logging is a feature in Windows operating systems that allows the recording of various system and application events into log files. These log files contain important information about the operation of the system, including security-related events, errors, warnings, and other relevant information.
Why is it important to configure Windows Event Logging with Kerberos?
Configuring Windows Event Logging with Kerberos is important because it allows for enhanced security monitoring and auditing in a Windows environment. Kerberos is a robust authentication protocol, and when integrated with Event Logging, it ensures that all relevant security events related to Kerberos authentication are captured and logged for analysis and troubleshooting purposes.
What types of events can be logged with Windows Event Logging and Kerberos?
Windows Event Logging with Kerberos can log various authentication events, such as successful logons, failed logons, ticket requests, ticket granting ticket (TGT) requests, service ticket requests, and ticket granting service (TGS) tickets. Additionally, it can also log events related to Kerberos delegation, account lockouts, and password changes.
Why is Windows Event Logging important?
Windows Event Logging is important because it allows the monitoring and troubleshooting of events that occur within the Windows operating system. It helps in the identification of security breaches, system errors, and performance issues.
What is Kerberos authentication in Windows?
Kerberos authentication is a network authentication protocol used in Windows environments. It provides a secure means of authenticating clients and servers over a network connection.




