As the digital landscape continues to evolve, safeguarding our devices and data from emerging cyber threats has become a paramount concern. In today's interconnected world, where information is exchanged at an unprecedented pace, it is essential to employ robust security measures to ensure the integrity and privacy of our digital lives.
Within the realm of widely adopted operating systems, there exists a powerful and feature-rich security toolset that goes beyond the realm of basic protection. This array of innovative functionalities grants users the ability to fortify their systems against a variety of potential threats, whether they be viruses, spyware, or other malicious entities. By leveraging these cutting-edge capabilities, users can take proactive measures to shield their devices and personal information from ever-evolving digital dangers.
Unveiling the Realm of Enhanced Protection
Residing within the core of a popular operating system, lies a security powerhouse that acts as the first line of defense against a multitude of digital adversaries. This formidable arsenal is equipped with a myriad of advanced features, each functioning as a vital building block in safeguarding your system and ensuring that only trusted processes run smoothly.
Unlocking the Potential of Your Operating System's Security Suite
By delving into the depths of your operating system's expansive security framework, you gain access to an array of potent tools and functionalities that transcend the realm of basic protection. With the ability to fine-tune the security settings and configure tailored defense mechanisms, you can establish a robust line of defense against potential threats, ensuring the integrity and confidentiality of your digital assets.
Introduction to the Windows Security Solution

In this section, we will delve into a comprehensive overview of an essential component of the Microsoft operating system, aiming to safeguard your computer and data from various threats. Shedding light on an eminent security shield integrated into the Windows environment, we will explore the core functionalities and purpose of this indispensable software package.
Emphasizing the significance of fortifying your system against potential risks, this elucidative segment will unravel the key aspects of the renowned security solution, highlighting its substantial role in ensuring the integrity and confidentiality of your digital experience. We will discover how this robust defense mechanism shields against malware, ransomware, and other malicious entities seeking to exploit vulnerabilities within your system.
- Insight into the core functionalities of this innovative security tool
- Understanding the proactive approach to threat detection and prevention
- Exploring the comprehensive malware scanning and removal capabilities
- An overview of the real-time protection features
- Examining the integration of advanced behavioral analysis techniques
- Understanding the role of machine learning in enhancing threat detection
Through a detailed exploration of the multifaceted aspects of this indispensable software, we will equip you with a comprehensive understanding of the Windows security solution, empowering you to maximize the protection of your valuable information and maintain a secure computing environment.
Activating the Protective System on your Device
In this section, we will explore the steps to enable the robust security solution available for your operating system. By activating the defense mechanism specifically designed to safeguard your device, you can enhance the overall protection against potential threats and intrusions.
1. Invoke the Shield | To initiate the defensive measures, navigate to the appropriate settings menu and activate the shield functionality. By accomplishing this step, you can ensure that your device is shielded from both known and emerging dangers. |
2. Configure Protections | Once the shield is activated, it is essential to configure the range of protections offered by the system. You can customize the settings according to your preferences and requirements, thereby establishing a tailored defense strategy. |
3. Update the Arsenal | To maximize the effectiveness of the protective system, regularly update its arsenal. Keep the defense mechanisms updated with the latest security intelligence, ensuring a proactive response to the ever-evolving landscape of digital threats. |
By enabling Windows Defender on your device, you empower yourself with an advanced security solution that offers a vigilant guard against potential risks. Take advantage of the intuitive interface and extensive customization options available to tailor the protection to your specific needs. Don't forget to keep the software up to date to leverage the latest advancements in threat detection and prevention.
Customizing Security Preferences in Microsoft's Protection System
In this section, we will delve into the various options available for tailoring your security preferences within the formidable system of safeguarding provided by Microsoft. By customizing these settings, you can optimize your experience and enhance the protection of your device against potential threats.
Firstly, we will explore the range of customizable preferences that allow you to personalize the behavior and scanning schedule of your protection system. Discover how to fine-tune the settings to align with your specific needs, ensuring a balance between performance and security.
Next, we will discuss the options for adjusting the notifications and alerts generated by the system. Learn how to configure these settings effectively so that you receive relevant and timely notifications, while maintaining control over the display frequency and level of detail.
Additionally, we will explore the extensive list of exclusions available within the system. Understand how to exclude certain files, folders, or processes from being scanned, allowing trusted programs and files to run without any interruptions.
Lastly, we will explore the advanced settings of Microsoft's protection system, which offer comprehensive control over the behavior of Windows Defender. Gain insights into the fine-grained configurations that enable you to further optimize your security setup, with options such as cloud-based protection, automatic sample submission, and much more.
By the end of this section, you will have gained a comprehensive understanding of how to customize the security settings of Microsoft's protection system, allowing you to tailor the experience to your specific requirements while maximizing the protection of your Windows device.
Configuring Real-time Protection
In this section, we will explore the customization options available for the continuous monitoring and automatic scanning capabilities of your operating system's built-in security application. By modifying the settings related to real-time protection, you can tailor your defense against various threats without relying on third-party software.
- Enable or Disable Real-time Protection:
- Customizing Scan Options:
- Setting Actions for Detected Threats:
- Managing Exclusions:
- Reviewing Protection History:
One of the fundamental choices you have when configuring real-time protection is deciding whether to enable or disable it altogether. Enabling real-time protection ensures that your system actively identifies and blocks potential threats in real-time, providing a proactive defense against malware, viruses, and other harmful entities. On the other hand, disabling real-time protection may be useful in specific scenarios where resource-intensive tasks need to be performed without interruption from security scans.
Real-time protection offers various scanning options to cater to different user preferences and requirements. You can customize the frequency of scans, choose between quick or full scans, and even specify specific folders or file types to include or exclude from the scanning process. These options allow you to strike a balance between the thoroughness of scans and the impact on system performance.
When a threat is detected by real-time protection, it is essential to define the actions to be taken. Configuring these actions enables you to automate the response to potential threats, reducing the need for manual intervention. Depending on the severity and type of threat, you can choose to quarantine, clean, or remove the infected files entirely to prevent further damage to your system.
In some cases, you may want to exclude certain files, folders, or even specific processes from real-time protection scans. This can be necessary for various reasons, such as avoiding false-positive detections or allowing trusted applications to function without interference. By managing exclusions, you can ensure that real-time protection focuses on the areas that require the most attention while minimizing unnecessary scans and impact on system performance.
Monitoring the protection history allows you to gain insights into the effectiveness of real-time protection and your system's overall security. You can review the records of detected threats, actions taken, and any potential issues encountered during the scanning process. This proactive approach enables you to address any areas of concern and fine-tune your real-time protection configuration accordingly.
Configuring real-time protection is a critical step in optimizing your Windows operating system's built-in security capabilities. By understanding and utilizing the available customization options, you can enhance the efficiency and effectiveness of your defense against potential threats without relying on external security solutions.
Optimizing Windows Security: Leveraging the Power of Windows Defender Firewall

Enhancing your security measures on a Windows operating system involves exploring the various resources available to protect your system from potential threats. One such resource that plays a crucial role in safeguarding your computer is the robust Windows Defender Firewall.
Understanding the ins and outs of Windows Defender Firewall can empower you to take control over inbound and outbound network traffic, ensuring that only authorized connections are established and potential vulnerabilities are minimized.
With Windows Defender Firewall, you have the opportunity to create custom rules that dictate which applications and services are allowed to communicate over the network. By configuring these rules thoughtfully, you can fortify your system against unauthorized access, unwanted traffic, and potential breaches.
Windows Defender Firewall is designed to be user-friendly, offering a comprehensive interface that allows you to navigate through essential settings. By familiarizing yourself with the interface, you can efficiently manage your firewall settings and make informed decisions regarding network permissions.
Furthermore, Windows Defender Firewall offers advanced features that enable you to monitor and log network activity, allowing you to keep track of potential threats and suspicious connections. By regularly reviewing these logs, you can identify patterns or anomalies that may indicate a need for further investigation or adjustment of your firewall settings.
In conclusion, harnessing the power of Windows Defender Firewall is vital in establishing a robust defense against potential security threats. By understanding its functionalities, customizing rules, and monitoring network activity, you can optimize your security measures and protect your system from unauthorized access and potential breaches.
Enhancing Security: Enabling Controlled Folder Access
Protecting your digital assets is of utmost importance in today's advanced technological landscape. To further fortify your system's defense against potential threats, leveraging the power of Controlled Folder Access can prove to be a valuable asset.
Controlled Folder Access is a feature that acts as a gatekeeper, allowing only trusted applications to access and modify your designated folders. By restricting unauthorized access, this feature safeguards your sensitive files and prevents malicious software from wreaking havoc on your system.
Enabling Controlled Folder Access enhances your overall security posture by creating an additional layer of protection. By configuring and customizing this feature, you can determine the applications allowed to access your folders, granting you full control over your data's integrity and confidentiality.
- Strengthening your defense: Learn how to enable Controlled Folder Access
- Understanding the benefits: Discover the significance of implementing this feature
- Customizing your settings: Explore the various options for configuring Controlled Folder Access
- Managing exceptions: Gain insights into exempting specific applications from the access restrictions
- Monitoring events: Stay informed about the activities and actions performed by Controlled Folder Access
By familiarizing yourself with the setup and management of Controlled Folder Access, you can ensure a robust security infrastructure that fortifies your valuable data against unauthorized access and potential breaches.
Managing Exclusions in Windows Security
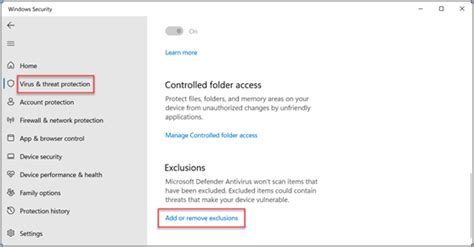
In the realm of enhancing the functionality and control of your computer's security, it is crucial to have the ability to manage exclusions in Windows Security. By specifying exclusions, you can ensure that certain files, folders, or processes are exempted from being scanned or blocked by your security software. This proactive approach allows you to optimize the performance of your system without compromising its protection against potential threats.
Enhancing Performance with Exclusions
In today's constantly evolving digital landscape, it is essential to strike a balance between robust security measures and efficient system performance. Windows Security provides you with the capability to manage exclusions, which can help in maximizing your computer's productivity while maintaining effective protection against malicious activities.
Exclusion Configuration Options
Windows Security offers various configuration options for managing exclusions. These options include excluding specific files or folders, excluding file types, and excluding processes or programs. By utilizing these features, you can tailor your security settings according to your specific requirements and ensure that your system resources are effectively utilized.
Customizing Exclusions
Windows Security allows you to customize exclusions based on your unique preferences. By carefully selecting files, folders, or processes to exclude, you can strike a balance between the need for stringent security and the desire for optimized performance. This flexibility empowers you to create a personalized security environment that caters to the demands of your specific computing tasks.
Best Practices for Managing Exclusions
To ensure the effectiveness of exclusion management in Windows Security, it is imperative to follow best practices. These include regularly reviewing and updating your exclusion list, verifying the legitimacy of excluded files or processes, and being cautious when excluding items of unknown origin. By adhering to these practices, you can maintain a strong security posture while harnessing the benefits of exclusion management.
In conclusion, managing exclusions in Windows Security offers you the ability to customize and optimize the performance of your system while maintaining robust protection against potential threats. By understanding the available options and following best practices, you can strike a delicate balance between security and efficiency, ensuring a seamless and secure digital experience.
Enhancing Security: Maintaining and Checking Your System with Windows Protector
One crucial aspect of safeguarding your computer from potential threats is to ensure your system is consistently updated and scanned for any malicious activity. This section will outline the essential steps to periodically update and perform comprehensive scans using the robust capabilities of your system's built-in security solution.
Updating Windows Protector Definitions Regularly updating your Windows Protector definitions is vital to ensuring it can recognize the latest malware and potential risks. By regularly downloading and installing the latest updates, you can enhance the effectiveness of your system's security solution against emerging threats and vulnerabilities. This proactive approach helps keep your computer safeguarded with the most up-to-date defenses. |
Scheduling System Scans To maintain a secure system, scheduling regular scans with Windows Protector is imperative. By scheduling scans at convenient times, such as when you are not actively using your computer, you can allow the program to comprehensively search for any potential threats throughout your system. These scans help identify and eliminate any malware or suspicious elements that might have infiltrated your computer, ensuring its continued protection. |
Customizing Scan Options In addition to regular system scans, Windows Protector allows you to customize scan options to align with your specific needs. By modifying settings such as scanning specific folders, files, or even external devices, you can target potential areas of concern within your system. This customization enables you to efficiently manage and optimize the scanning process, ensuring maximum security without unnecessary consumption of system resources. |
In conclusion, staying vigilant against potential threats is an ongoing responsibility for every computer user. By following the guidelines outlined in this section, you can maintain an updated and secure system with Windows Protector's advanced features, allowing you to safeguard your valuable data and ensure a smooth computing experience.
Troubleshooting Issues with Windows Defender: Resolving Common Problems
In this section, we will explore various difficulties that users may encounter when using the robust security features provided by Windows Defender, and provide effective solutions to address these issues. By understanding and addressing these common problems, users can ensure the smooth functioning of their system's defense against threats.
| Issue | Solution |
|---|---|
| Performance impact on system | To mitigate performance impact caused by Windows Defender, users can adjust the settings to strike a balance between security and system resources utilization. This can involve reducing real-time scanning frequency or excluding specific files or folders that do not pose a significant security risk. |
| False positive detections | Windows Defender can sometimes identify legitimate programs or files as potential threats. Users should review the details of the detected item carefully and verify its source. If confirmed safe, the file can be added to the exclusion list to prevent future false positives. |
| Update failures | Update failures can occur due to various reasons such as connectivity issues or conflicts with other security software. Users should ensure a stable internet connection and disable any conflicting programs temporarily to allow Windows Defender to update successfully. If the problem persists, resetting the Windows Update components might be necessary. |
| Disabled or turned off status | Windows Defender may sometimes be disabled or turned off unintentionally due to changes in system settings or the presence of third-party security software. Users should check Windows Security settings and restart the Windows Security service to re-enable Windows Defender. |
| Malware removal failures | In cases where Windows Defender fails to remove malware, users can try performing a full scan in Safe Mode, update the virus definitions, or use additional malware removal tools to ensure a thorough removal. Reinstalling Windows Defender might also help in resolving persistent malware-related issues. |
By addressing these common problems systematically, users can troubleshoot Windows Defender issues effectively and maintain an enhanced level of security for their Windows operating system.
FAQ
What are the advanced features of Windows Defender in Windows?
Windows Defender in Windows has several advanced features such as real-time protection, cloud-based protection, automatic scanning, controlled folder access, and network protection.
How can I enable real-time protection in Windows Defender?
To enable real-time protection in Windows Defender, open the Windows Security app, go to Virus & threat protection, and then toggle on the Real-time protection option.
What is controlled folder access in Windows Defender?
Controlled folder access is a feature in Windows Defender that helps protect your valuable data by monitoring and blocking unauthorized changes to files in protected folders. You can enable this feature by going to the Windows Security app and enabling the Controlled folder access option.
How does network protection in Windows Defender work?
Network protection in Windows Defender helps protect your computer from malicious network activity. It uses real-time monitoring to detect and block malicious connections and processes. You can enable this feature by going to the Windows Security app, selecting Firewall & network protection, and toggling on the Network protection option.
Can I schedule automatic scans with Windows Defender?
Yes, you can schedule automatic scans with Windows Defender. Open the Windows Security app, go to Virus & threat protection, click on the Manage settings link, and then under the Scan options section, click on the Add or remove exclusions link. From there, you can create a new scan schedule by clicking on the "New scan" button.




