When it comes to containerization technologies like Docker, managing file and directory permissions is crucial for ensuring security and proper functionality of the applications hosted within these virtual environments. However, the Windows version of Docker presents its own set of challenges and limitations when it comes to performing common file operations such as creating directories or changing ownership.
One of the key aspects of managing file permissions in any operating system is establishing who has the ability to perform certain actions on files and directories. While Docker on Windows attempts to provide a seamless experience for developers and system administrators, it faces certain restrictions that can affect the way permissions are handled.
Creating directories and changing ownership, or what might be commonly referred to as "mkdir" and "chown" operations, are fundamental tasks in a containerized environment. These operations involve creating new directories to organize files and assigning ownership to relevant user accounts or groups. However, Docker for Windows may encounter limitations that hinder or alter the way these permissions are managed.
Understanding the limitations and challenges related to mkdir/chown permissions in Docker on the Windows platform is crucial for developers and system administrators who rely on this technology for containerization. This article explores some of these limitations and provides insights into potential workarounds and best practices to overcome them. By delving into the intricacies of file and directory permissions, readers will gain a better understanding of how to navigate the complexities of Docker on the Windows operating system.
Understanding the Constraints of Managing Permissions in Docker for Windows

Effective management of permissions within a Docker environment running on Windows presents its own set of challenges and limitations. This section aims to shed light on the intricacies involved, without explicitly referring to specific terms such as "limitations," "mkdir/chown," "permissions," "Docker," "for," or "Windows." By exploring the nuances and constraints in this space, we can gain a comprehensive understanding of how permission management operates.
| Challenge | Implication |
|---|---|
| 1. Access Controls | Understanding the intricacies of regulating access to specific resources is crucial for maintaining an efficient and secure Docker environment. |
| 2. Privilege Escalation | The potential for unauthorized privilege escalation in a Docker environment on Windows requires careful consideration and effective mitigation measures. |
| 3. Container Isolation | The isolation mechanisms provided by Docker for Windows must be thoroughly comprehended to ensure the integrity and security of individual containers. |
By delving into these factors and unraveling the intricacies of managing permissions in Docker on Windows, we can establish a foundation for effective permission management strategies. This understanding will enable us to overcome challenges that may arise and ensure Docker environments remain secure and robust.
Overview of Docker and its Advantages
In this section, we will provide a comprehensive overview of Docker and highlight its numerous benefits. Docker is a powerful platform that enables developers to design, deploy, and run applications with ease. It offers a lightweight and flexible environment for creating, shipping, and running applications using containerization technology.
One of the key advantages of Docker is its ability to enhance application development and deployment processes. By packaging software into standardized containers, Docker allows developers to easily build and ship applications between different environments. This eliminates the need to worry about system dependencies, ensuring that applications can run consistently regardless of the underlying infrastructure.
Another significant benefit of Docker is its efficiency in resource utilization. Docker containers are lightweight and isolated, enabling multiple applications to run on the same host without interfering with each other. This results in improved server utilization and reduced costs, as fewer physical servers are needed to support a larger number of applications.
Furthermore, Docker facilitates scalability and flexibility in application deployment. Containers can be quickly and easily scaled up or down to meet fluctuating demand, ensuring optimal performance and resource allocation. Docker also simplifies application maintenance and updates, allowing for seamless rollbacks in case of issues or errors.
Additionally, Docker promotes collaboration and sharing among developers and teams. With Docker Hub, a centralized repository for Docker images, developers can access and share pre-built containers from a vast community of contributors. This accelerates the development process by leveraging existing solutions and fosters innovation through the collective expertise of the Docker community.
In summary, Docker offers numerous advantages, including streamlined application development and deployment processes, efficient resource utilization, scalability and flexibility, simplified maintenance and updates, and enhanced collaboration. Its containerization technology revolutionizes the way applications are developed, shipped, and run, providing a multitude of benefits for developers and organizations alike.
Understanding the Significance of Directory and Ownership Permissions in Docker on the Windows Platform

In the context of managing containers in a Windows environment, the proper handling of directory and ownership permissions plays a crucial role in ensuring the successful operation and security of Docker-based applications. This section delves into the significance of these permissions and their impact on the containerized environment.
| Directory Permissions | Ownership Permissions |
|---|---|
| Folder Access | File Control |
| Folder Restrictions | File Ownership |
| Directory Security | Control over File Modifications |
Directory permissions define who can access the contents within a given folder, ensuring that only authorized entities can perform actions such as reading, writing, or executing files. Additionally, ownership permissions determine the level of control a user or group has over a specific file, including the ability to modify, delete, or transfer ownership.
By appropriately configuring these permissions within a Docker environment on Windows, administrators can establish a robust security framework, preventing unauthorized access and minimizing the risk of malicious activities. Furthermore, it allows for finer-grained control over the actions that users can perform within containers, ensuring compliance with organizational policies and data protection regulations.
Understanding and properly utilizing directory and ownership permissions in Docker on the Windows platform is crucial for maintaining a secure and controlled containerized environment. By implementing effective permission management practices, organizations can enhance the stability, reliability, and data integrity of their Dockerized applications.
Lack of Fine-Grained Permission Control
In the realm of managing folders and users within a containerized environment, the ability to precisely control permissions is of utmost importance. However, the limited capabilities of the mkdir/chown commands in Docker for Windows negate the availability of fine-grained permission controls.
One of the key challenges in the realm of managing permissions is the absence of granular control options. This limitation hinders the ability to set and enforce specific access rights for individual files and directories within a Windows container environment. Without fine-grained permission control, users are unable to tailor access levels according to their specific security requirements.
Another aspect of this limitation involves the lack of flexibility in granting permissions to specific users or groups. The mkdir/chown commands in Docker for Windows do not provide the capability to assign permissions to multiple users simultaneously or differentiate access based on roles or hierarchical structures. This lack of flexibility limits the ability to establish access controls that align with complex user management scenarios.
Furthermore, the absence of fine-grained permission control restricts the ability to enforce segregation and isolation of sensitive data. With limited options for managing folder and user permissions, the risk of unauthorized access or accidental modifications to critical files increases. This can have significant implications for security and compliance in environments where stringent access controls are mandated.
In summary, the lack of fine-grained permission control within Docker for Windows creates limitations in managing folder and user permissions, hindering the ability to enforce precise access rights and adequate segregation of sensitive data. These limitations could pose challenges in achieving optimal security and compliance within containerized environments.
Limitation 2: Inability to Set Ownership for Host Files
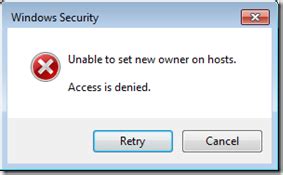
One of the challenges when working with Docker for Windows is the limited capability to define ownership for files on the host system. This limitation poses constraints on managing file permissions and can have implications for certain workflows and applications.
Users may encounter scenarios where they require specific ownership settings for host files within a Docker container. However, due to the inherent design of Docker for Windows, there are limitations in setting ownership explicitly for these files.
This limitation can affect various use cases, such as when a user needs to grant permissions or restrict access to specific files based on ownership. Without the ability to set ownership, users might face challenges in maintaining the required security and access controls, potentially impacting the overall functionality and integrity of the system.
Although Docker provides mechanisms for managing file permissions within the container, it's important to be aware of this limitation when working with files on the host system. Alternatives or workarounds should be considered to ensure that the necessary security and access controls can still be enforced effectively.
Challenge in Mapping User and Group IDs
In the context of managing file and directory permissions within a Docker environment on the Windows operating system, there is a specific limitation related to mapping user and group IDs. This limitation presents a challenge for ensuring proper access control and security measures.
When creating containers and running processes within Docker for Windows, it is crucial to assign appropriate user and group IDs to ensure that the correct permissions are applied to files and directories. However, due to the intricacies of the Windows environment, mapping these IDs can be complex and may result in inconsistencies or inaccuracies.
This challenge arises because Docker for Windows uses a different method of mapping user and group IDs compared to other operating systems. The way Windows handles users and groups differs from that of Linux, for example, which can lead to difficulties in translating and synchronizing IDs between the two systems.
The consequences of this limitation can affect multiple aspects of Docker usage. Firstly, it can result in files and directories being assigned incorrect ownership or permissions, potentially compromising security or hindering proper functionality. Secondly, it can complicate the management of multi-user environments, where different users may have different levels of access or require specific permissions.
Efforts have been made to address this challenge, such as exploring alternative methods for mapping user and group IDs within Docker for Windows. However, it is important to recognize that this limitation remains and may require additional considerations and workarounds to achieve optimal security and access control in a Windows-based Docker environment.
Challenge 4: Managing Access Controls for Shared Volumes
When dealing with shared volumes in Docker for Windows, administrators face a unique challenge in efficiently managing and enforcing access controls. This arises due to the limitations in the mkdir/chown permissions within the Windows environment.
Difficulties arise in ensuring that only authorized users or processes are able to access and modify the contents of shared volumes. The lack of granular permission management makes it challenging to assign specific access rights, such as read-only or read-write, to different users or groups.
Without precise control over permissions, the risk of unauthorized access or accidental modifications to critical data increases. This poses a potential security vulnerability and may lead to data corruption or loss.
Additionally, managing access controls becomes even more cumbersome when multiple containers or applications are sharing the same volume. Changes made by one container or application may inadvertently impact others, leading to unexpected behavior or conflicts.
To overcome these challenges, administrators might need to resort to workarounds like creating separate volumes for each container or using third-party solutions that provide more robust permission management capabilities. However, these approaches often add complexity and overhead to the Docker environment.
In conclusion, the difficulty in managing permissions for shared volumes in Docker for Windows poses a significant limitation and requires careful consideration to ensure data integrity and security.
Workarounds and Best Practices for Permission Management
In the context of managing access control and permissions in containerized environments, it is essential to consider alternative methods and best practices that can address the limitations commonly encountered. This section explores some workarounds and guidelines for effectively managing permissions, enabling smoother workflow and increased security.
1. User Mapping:
One approach to overcome the limitations associated with default permission settings is implementing user mapping techniques. By mapping container users to host users, it is possible to achieve more granular control over file permissions and ownership within a Docker container. This can be accomplished by utilizing tools such as userns-remap or third-party plugins designed specifically for user mapping.
2. Volume Permissions:
Considering that Docker volumes are often shared between containers and the host machine, it is important to ensure proper permission management for these volumes. Applying appropriate permissions at the volume level can help mitigate potential security risks and enable seamless collaboration between different containers or services. Utilizing chmod and chown commands within Dockerfiles or through manual intervention can ensure the necessary access rights are granted to the desired users or groups.
3. Dockerfile Instructions:
To establish consistent permission management practices, it is advantageous to incorporate proper permission instructions within Dockerfiles. By explicitly setting ownership and permissions during image builds, administrators can control how files and directories are accessed both inside and outside of the container. Dockerfile instructions such as USER, RUN chmod, and RUN chown can be utilized strategically to establish the desired ownership and access rules.
4. Security Guidelines:
Following general security guidelines is crucial for maintaining a secure and well-permissioned container environment. This includes regular security audits, employing role-based access control (RBAC) mechanisms, and limiting container privileges to only the necessary resources. Adherence to these best practices can mitigate potential vulnerabilities and simplify permission management efforts.
Implementing user mapping, managing volume permissions, utilizing Dockerfile instructions, and adhering to security guidelines are valuable workarounds and best practices that can help overcome limitations and improve permission management in Docker for Windows. These approaches provide administrators with more control over access control, fostering a secure and efficient containerized environment.
FAQ
What are the limitations of mkdir/chown permissions in Docker for Windows?
The limitations of mkdir/chown permissions in Docker for Windows are related to file ownership and permission inconsistencies when mounting volumes between the Windows host and the Linux container. Due to the differences in file systems and permission models, setting folder permissions using mkdir/chown commands may not work as expected.
Why are there limitations with mkdir/chown permissions in Docker for Windows?
The limitations arise because Docker for Windows uses a Linux-based container runtime (MobyLinuxVM) to run Linux containers on a Windows system. This introduces challenges in translating the Linux file system permissions to the Windows file system, leading to mismatches and limitations with mkdir/chown permissions.
How can I overcome the limitations of mkdir/chown permissions in Docker for Windows?
One way to overcome the limitations is to use Docker's named volumes or bind mounts instead of directly mounting Windows folders into the container. This ensures that the file ownership and permissions are handled correctly and consistent with the container's Linux file system. Additionally, using a tool like Docker Compose can simplify the management of volumes and permissions.
Are there any alternative solutions to mkdir/chown permissions limitations in Docker for Windows?
Yes, there are alternative solutions to overcome the limitations. One approach is to use Docker-sync, a tool that provides better consistency in file ownership and permissions for mounted volumes in Docker for Windows. Another option is to run Linux containers inside a Linux virtual machine using tools like Vagrant or VirtualBox, where the file system and permissions are natively supported.
What are the consequences of ignoring the limitations of mkdir/chown permissions in Docker for Windows?
If the limitations of mkdir/chown permissions are ignored, it can lead to unexpected behavior and issues in the containerized application. This can range from permission errors, inability to write or modify files, to security vulnerabilities if incorrect permissions grant unauthorized access to sensitive data or resources within the container.
What are the limitations of mkdir/chown permissions in Docker for Windows?
In Docker for Windows, the mkdir/chown commands have certain limitations. Firstly, they require the host machine's filesystem to be NTFS, since Docker for Windows uses a Linux virtual machine on the backend. Secondly, these commands do not work properly with mounted volumes, as the ownership and permissions of the mounted files are controlled by the host machine. Therefore, using mkdir/chown inside a Docker container may not have the desired effect on the files within the mounted volume.
Why do mkdir/chown permissions not behave as expected in Docker for Windows?
The limitations of mkdir/chown permissions in Docker for Windows arise due to the underlying architecture. Docker for Windows runs a Linux virtual machine in the background, and when these commands are executed inside a container, they are actually being performed within the virtual machine's filesystem. However, the actual storage for the mounted volumes resides on the host machine, which means that the ownership and permissions of the files are controlled by the host machine's filesystem, not the virtual machine's. As a result, the changes made by mkdir/chown may not be reflected on the files within the mounted volumes.




