In the modern era of advanced technology, where the need for secure and efficient communication holds key importance, accessing and managing a remote Linux system has become an essential part of various industries. The method of establishing a connection and controlling a server without having direct physical access has revolutionized the way businesses operate, enabling professionals to seamlessly navigate through the digital realm.
For individuals who crave flexibility and desire to carry out intricate operations on a remote Linux server, utilizing the command line interface proves to be an invaluable solution. This first-hand interaction with the server system empowers users with the ability to execute commands remotely, ensuring smooth operations and robust control over crucial aspects of a Linux environment.
By employing a plethora of powerful tools and techniques, administrators are able to establish a secure and reliable connection to their Linux system, mitigating any potential barriers that may arise from physical distance or limited accessibility. Leveraging the command line interface not only saves time but also enhances productivity, enabling professionals to effectively monitor, troubleshoot, and optimize the server, even from a remote location.
With the flexibility offered by the command line interface, one can effortlessly navigate through the intricacies of a Linux operating system, seamlessly configure servers, install software, manage files and directories, modify user permissions, and much more. By utilizing only a set of commands and following best practices, users can effortlessly handle complex tasks, avoiding the need for graphical interfaces that may consume additional system resources.
Understanding the Command Line Interface
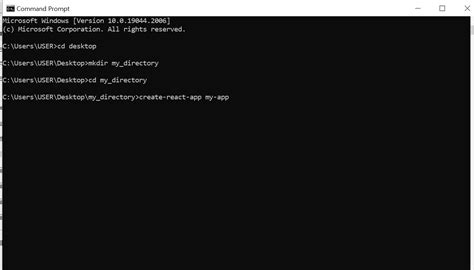
In the digital realm, a powerful tool awaits those seeking a deeper connection with their operating system. This tool, known as the command line interface, provides users with a direct means of interacting with their computers. By utilizing a set of textual commands, the command line interface empowers users to navigate through directories, manipulate files, and execute various tasks, all without the need for a graphical user interface.
The command line interface, often referred to as the terminal, is a text-based interface where users can input commands and receive corresponding output. It serves as a gateway to the inner workings of an operating system, allowing users to execute powerful commands with precision and control. By leveraging the command line interface, users can streamline and automate tasks, troubleshoot system issues, and even remotely access other computers over a network.
While it may seem daunting to those unfamiliar with its capabilities, the command line interface offers a level of flexibility and efficiency unmatched by its graphical counterparts. With a slew of commands at their disposal, users can accomplish complex tasks with just a few keystrokes. Whether you seek to configure network settings, install software, or manage system processes, the command line interface beckons to be explored, promising a new realm of possibilities and a deeper understanding of your Linux system.
Enhancing Connectivity: The Advantages of Command Line Interface for Distant Server Interaction
In the age of high-speed internet and comprehensive technological advancements, the realm of server management has evolved immensely. Today, professionals seek innovative methods to remotely connect with servers. While numerous tools are available, one notable solution stands out from the rest - the command line interface (CLI). This article explores the rationale behind using CLI for distant server interaction, highlighting its unparalleled benefits and unique advantages.
1. Streamlined Efficiency:
The command line interface boasts a streamlined and efficient approach to server interaction. Rather than relying on cumbersome graphical user interfaces or resource-heavy alternatives, CLI ensures swift and responsive communication, facilitating seamless control of the server environment.
2. Versatility and Flexibility:
CLI enables users to perform a vast array of tasks, offering unparalleled versatility and flexibility. From managing system resources to configuring networks, and even deploying applications, the command line interface empowers administrators to exercise complete control over their Linux systems.
3. Enhanced Security:
While security remains a paramount concern for any system administrator, CLI presents an inherently secure mode of remote access. By omitting unnecessary graphical interfaces and focusing solely on text-based commands, potential vulnerabilities associated with graphical applications are mitigated, thereby reducing the attack surface and reinforcing system security.
4. Minimal Resource Consumption:
Command line interaction minimizes resource consumption on both the local and remote systems. Without the need for elaborately designed graphical interfaces, computational resources remain dedicated to the task at hand, resulting in enhanced performance and optimal system utilization.
5. Expertise Utilization:
Utilizing CLI for remote access to Linux servers encourages expert skill development and utilization. By delving into the command line environment, system administrators enhance their knowledge of Linux systems, improving troubleshooting abilities and fostering a deeper understanding of server functionality.
Ultimately, the use of command line interface for remote server access offers a range of distinctive advantages, including streamlined efficiency, versatility, enhanced security, minimal resource consumption, and the promotion of expertise utilization. As servers continue to form the backbone of countless operations, embracing the power of CLI unlocks immense potential for remote server management and operation.
Establishing Remote Connectivity
Creating a secure and reliable remote connection to a Linux server is essential for efficient management and control without physically being present at the server location. In this section, we will explore the steps involved in configuring a remote access solution that allows you to connect to your server from any location, enabling seamless administration and monitoring.
Setting up remote connectivity
Before delving into the technical details, it is important to understand the concept of remote access and its advantages. With remote access, you can remotely connect to your Linux server using a variety of protocols, such as Secure Shell (SSH) or Virtual Network Computing (VNC). This allows you to perform administrative tasks, transfer files, and troubleshoot issues from anywhere with an internet connection.
Enabling secure communication
One of the key aspects of remote access configuration is ensuring secure communication between your local machine and the server. This involves implementing encryption protocols, such as Transport Layer Security (TLS) or Secure Sockets Layer (SSL), to protect your data from unauthorized access and eavesdropping.
Configuring firewall rules
To establish a remote connection, it is necessary to configure the firewall rules on both your server and local machine. This involves allowing specific ports and protocols necessary for remote access, while blocking any unauthorized access attempts.
Creating user accounts
In order to establish a remote connection, you need to create user accounts with the appropriate permissions on the server. These accounts will act as credentials for authentication and will determine the level of access and privileges granted to individual users.
Choosing the right remote access protocol
Depending on your specific requirements and preferences, you can choose from various remote access protocols available for Linux servers. Each protocol has its own strengths and weaknesses, so it's important to select the one that best suits your needs in terms of speed, security, and ease of use.
Testing the remote access setup
After completing the configuration steps, it is vital to test the remote access setup to ensure everything is functioning as intended. This involves connecting to the server from a remote machine, performing basic operations, and verifying the stability and reliability of the connection.
In conclusion, setting up remote access to a Linux server involves configuring secure communication, firewall rules, user accounts, and selecting the appropriate protocol. By following these steps, you can establish a robust and convenient remote access solution that facilitates efficient server management and administration.
Checking the Status of SSH Service
In this section, we will explore how to check the current status of the Secure Shell (SSH) service on your Linux server. SSH is a cryptographic network protocol that allows secure remote access to your server.
Ensuring that the SSH service is running properly is crucial for secure remote administration of your server. By checking the SSH service status, you can verify if it is active and functioning as expected.
There are several methods to check the status of the SSH service on a Linux server. One commonly used way is to use the command line interface (CLI). By accessing the CLI through a terminal emulator, you can execute specific commands to determine whether the SSH service is running or not.
An easy way to check the SSH service status is to use the systemctl command. This command provides a convenient way to manage and control systemd services on a Linux server. To check the status of the SSH service, you can run the following command: systemctl status sshd.
Upon executing the command, the output will display relevant information about the SSH service. It will indicate whether the service is active or inactive, any errors encountered, and the specific port on which the service is listening.
By regularly checking the SSH service status, you can promptly identify any issues or disruptions to the remote access functionality of your Linux server. This allows for efficient troubleshooting and resolution of any problems that may arise.
Configuring SSH for secure and remote management
Ensuring secure and convenient access to a Linux server
When it comes to managing a Linux server from a remote location, having a reliable and secure method is crucial. One commonly used solution is SSH (Secure Shell), a network protocol that allows administrators to securely access and control their servers over an encrypted connection.
Key considerations for configuring SSH
Before setting up SSH for remote access, there are several important considerations to keep in mind. First, it is essential to choose a strong and unique password for the SSH user account, or even better, utilize public key authentication for enhanced security. Additionally, configuring the server to only allow SSH connections from trusted IP addresses can help prevent unauthorized access.
Enabling and configuring SSH on the Linux server
To enable SSH, start by checking if the SSH package is installed on the Linux server. If not, it can be installed using the package manager of the distribution. Once installed, the SSH server daemon needs to be started and configured. This involves modifying the SSH configuration file to define settings such as port number, access permissions, and user authentication methods.
Enhancing security with SSH configuration options
SSH offers various configuration options that can further enhance security. For example, disabling root login and password authentication can help mitigate the risk of unauthorized access. It is also recommended to enable logging of SSH activities for audit purposes, as well as implementing measures like automatic disconnection after a certain period of inactivity.
Testing and troubleshooting SSH connectivity
Once SSH is configured, it is crucial to test the remote connectivity to ensure everything is working as expected. This can involve verifying that the SSH service is running, checking firewall rules, and testing the SSH connection from a remote client. In case of any issues encountered, troubleshooting techniques such as reviewing log files and checking network connectivity can help identify and resolve the problem.
Conclusion
Configuring SSH for remote access is an essential step in managing a Linux server securely. By implementing appropriate security measures and following best practices, administrators can ensure that remote access to their server is both convenient and protected from potential threats.
Establishing a Connection with the Linux Server
In this section, we delve into the process of establishing a connection with the Linux server, ensuring seamless communication and interaction with the remote system. By configuring a reliable interface, users can securely interact with the Linux server for various tasks and operations.
Setting Up the Connection: To begin, users need to establish the means of connectivity to the Linux server. This involves configuring the appropriate network settings and identifying the IP address of the remote system. Ensuring that there is a stable network connection is essential for a successful connection.
Authentication and Authorization: Once the connection is established, users must authenticate and authorize themselves to gain access to the Linux server. This process involves providing the necessary credentials, such as username and password, or utilizing SSH keys for a more secure and convenient authentication method.
Utilizing Secure Protocols: It is crucial to employ secure protocols when connecting to the Linux server to prevent unauthorized access and protect sensitive data. The use of protocols like SSH (Secure Shell) ensures encrypted communication, reducing the risk of interception and potential security breaches.
Connecting via Command Line: Connecting to the Linux server through the command line allows users to execute remote commands and administer the system effectively. By utilizing command line tools such as SSH or Telnet, users can establish a secure connection and navigate the Linux server to perform various administrative tasks.
Remote File Transfer: In addition to remote command execution, establishing a connection with the Linux server enables users to transfer files seamlessly between their local machine and the remote system. This facilitates efficient file management, allowing for the transfer of essential data and resources.
Troubleshooting and Error Handling: Lastly, understanding common connectivity issues and knowing how to troubleshoot and handle potential errors is crucial when connecting to a Linux server. By familiarizing themselves with common problems and their solutions, users can ensure a smoother connection experience and avoid potential interruptions.
Establishing a Secure Connection to the Linux Server using SSH

When it comes to gaining remote access to a Linux server without physically being present at the location, SSH emerges as a powerful and secure solution. This section will guide you through the process of establishing a secure connection to the server utilizing the SSH protocol.
SSH, short for Secure Shell, provides a cryptographic network protocol that enables secure communication over an unsecured network. By utilizing encryption algorithms, SSH ensures the confidentiality of data transmission and protects against unauthorized access to the server.
To connect to the Linux server via SSH, you will need an SSH client software installed on your local machine. There are various SSH clients available, such as OpenSSH, PuTTY, and Bitvise SSH, each offering a user-friendly interface to establish a secure connection.
Key Highlights:
|
Once you have installed an SSH client, you can initiate a connection by providing the necessary credentials, including the IP address or domain name of the server and your login credentials, such as username and password.
It is also possible to enhance the security of the SSH connection by utilizing public key authentication instead of relying solely on passwords. This involves generating a key pair on your local machine and copying the public key to the server.
Once connected, you can execute commands, transfer files, and manage the Linux server remotely with ease. SSH provides a convenient and secure method for system administrators and users to interact with the server from anywhere in the world.
By utilizing SSH to connect to the server, you can effectively and securely manage your Linux environment, ensuring efficient remote administration and troubleshooting capabilities.
Authenticating with SSH keys
In the realm of secure access to a Linux server, authenticating with SSH keys plays a vital role in ensuring enhanced security and convenience.
When it comes to establishing a secure connection to a remote Linux server, the traditional method of using a username and password can be susceptible to various security risks. However, by utilizing SSH keys, a more robust and secure authentication mechanism can be achieved.
An SSH key pair consists of a public key and a private key. The private key is securely stored on the client machine, while the public key is stored on the server. When attempting to access the server, the client presents its private key, and the server verifies the authenticity of the key by matching it with the corresponding public key. This eliminates the need for passwords and significantly reduces the risk of unauthorized access.
Generating an SSH key pair involves the use of cryptographic algorithms that ensure the uniqueness and strength of the keys. The private key should always be kept secret, while the public key can be freely distributed to servers for authentication purposes.
With SSH keys, remote access to a Linux server becomes more convenient. Users no longer need to remember complex passwords or worry about their passwords being compromised, as the security lies within the possession and protection of the private key. Additionally, SSH keys provide a secure and efficient alternative to traditional password-based authentication methods.
In conclusion, by embracing the use of SSH keys for authentication, Linux server administrators can enhance the security of remote access while also simplifying the login process for authorized users.
[MOVIES] [/MOVIES] [/MOVIES_ENABLED]FAQ
What is Terminal?
Terminal is a command-line interface program that allows users to interact with the Linux operating system through a command prompt.
Why would I need to remotely access a Linux server?
There are several reasons why you may need to remotely access a Linux server, such as managing the server from a different location, troubleshooting issues, or performing system administration tasks without physically being present at the server.
How can I remotely access a Linux server using Terminal?
To remotely access a Linux server using Terminal, you can use the SSH (Secure Shell) protocol. Open Terminal on your local machine and use the SSH command followed by the IP address or domain name of the server. For example, "ssh username@server_ip_address". Enter your password when prompted, and you will be connected to the server.
Is it secure to access a Linux server remotely using Terminal?
Yes, accessing a Linux server remotely using Terminal through SSH is generally considered secure. SSH uses encryption to protect the communication between the local machine and the server, ensuring that sensitive information such as passwords or commands are not intercepted by malicious parties.




