In the realm of digital networking, one inevitable challenge arises when attempting to establish connections for communication purposes. Users encounter a perplexing situation whereby the expected functionality fails to materialize. Rather than seizing the chance to seamlessly access external networks, a substantial impediment impedes progress within Windows' virtual container.
This predicament exemplifies a conundrum characterized by the failure of proxy mechanisms to facilitate the desired outcome. As users engage with the digital landscape, forging connections becomes an arduous task due to a peculiar issue within the confined boundaries of a Windows container. Such a complex hurdle necessitates a deeper understanding to decipher the underlying obstacles preventing successful network accessibility.
Within the intricate web of technological intricacies, the designated barrier lies in the elusive nature of the communication framework. The quintessence of connectivity, once anticipated to flow effortlessly, encounters a puzzling roadblock within the confines of a Windows container. This resolute obstruction manifests itself surreptitiously, silently sabotaging the user's prospect of traversing external networks.
Alas, the pursuit of a seamless digital connection is thwarted by a recurring anomaly within the Windows environment. Amidst this intricate maze of obstacles, the importance of grasping the intricacies of network segregation and the limitations of proxy establishment becomes increasingly palpable. To traverse these uncharted digital waters, a comprehensive understanding of the underlying mechanisms is imperative, enabling users to navigate successfully towards the proverbial shores of network connectivity outside the confinements of a Windows container.
Understanding the Importance of Intermediaries in Containerized Environments
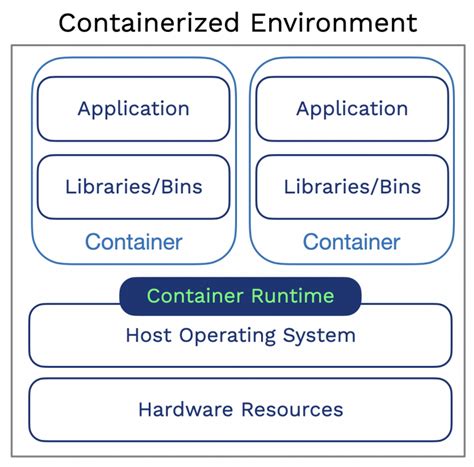
In the realm of containerization, the utilization of intermediaries plays a pivotal role in facilitating seamless communication between various components within a system. These intermediaries, often referred to as proxies, act as essential enablers for efficient data exchange, enhanced security, and improved network performance.
Within a container environment, where applications are encapsulated and isolated, proxies act as intermediaries by intercepting and redirecting network traffic. By doing so, they enable applications to communicate with external entities and access resources beyond the container boundaries. Moreover, proxies offer additional capabilities such as load balancing, caching, and traffic management, which contribute to optimized performance and scalability.
While the primary function of proxies within a containerized environment is to facilitate network communication, they also play a vital role in ensuring security. Proxies act as barriers by inspecting incoming and outgoing traffic, implementing security policies, and filtering potentially malicious requests. This added layer of protection helps safeguard the containerized applications and the underlying infrastructure from external threats.
In summary, the understanding of proxies and their multifaceted role within container environments is critical for efficient network management, enhanced application performance, and robust security measures. By comprehending the significance of intermediaries, organizations can maximize the benefits of containerization while ensuring seamless connectivity and protecting their systems from potential vulnerabilities.
Possible causes for connectivity issues within Windows container relating to external network routing
In this section, we will explore various underlying factors that could contribute to challenges concerning network connectivity within a Windows container environment. By understanding these potential reasons, you can better diagnose and address proxy-related disparities in your containerized applications.
- Configuration discrepancies: The way network settings are configured within the container can differ from the underlying host system, leading to conflicts or inconsistencies when communicating with external networks.
- Incompatible network protocols: Differences in network protocols supported by the container and the host environment can result in proxy issues, hindering proper data transmission and connectivity.
- Firewall restrictions: Firewall settings on the host or container may block necessary network traffic, preventing the proxy from successfully routing requests and responses.
- Network interface conflicts: Conflict can arise when multiple network interfaces, either virtual or physical, are present on the host or within the container, resulting in routing complications.
- Missing or outdated network drivers: Outdated or incompatible network drivers within the container or host system can impede proxy functionality, generating connectivity problems.
- Container network configuration faults: Misconfigurations in the container's network settings, such as incorrect IP addressing or DNS resolution, can hinder proxy operations.
- Container isolation limitations: The container's isolation mode may restrict access to certain network resources or impose restrictions on network functionality, preventing successful proxy usage.
By considering these potential factors, both individually and in combination, you can effectively identify and troubleshoot connectivity issues with proxies in your Windows container environment. Addressing these underlying causes will help ensure seamless network communication and improve the overall performance and reliability of your containerized applications.
Exploring common mistakes in configuring intermediary settings

Introduction: Within the realm of digital environments, it is crucial to establish seamless connectivity by configuring intermediary settings appropriately. However, even the most experienced individuals sometimes stumble upon common oversights that hinder the intended functionality. In this article, we will delve into a comprehensive exploration of these prevalent errors, aiming to enhance your understanding and proficiency in configuring intermediary settings.
1. Overlooking compatibility requirements: In the pursuit of establishing a streamlined network, it is imperative to consider the compatibility of intermediary settings with the existing infrastructure. Neglecting this crucial aspect can lead to undesired consequences, such as connectivity disruptions or limited access to essential resources. Carefully assessing the compatibility requirements ensures smooth communication between diverse components within the digital ecosystem.
2. Neglecting proper authentication: Authentication serves as a crucial layer of security when configuring intermediary settings. Omitting or improperly implementing authentication protocols can expose sensitive information to unauthorized parties. It is paramount to diligently authenticate requests to avoid potential security breaches, ensuring that only authorized entities gain access to the resources.
3. Ignoring network segmentation: The absence of proper network segmentation can introduce complications in intermediary settings. Failure to isolate different components within the network can result in cross-contamination and unintended interference. Segmenting the network appropriately helps in streamlining traffic flow, optimizing resource allocation, and ensuring the effective functioning of intermediary settings.
4. Inadequate monitoring and troubleshooting: One common mistake is underestimating the significance of continuous monitoring and troubleshooting in intermediary settings. Failing to proactively detect and address issues can lead to extended downtimes and disrupted operations. Consistent monitoring, combined with prompt troubleshooting measures, assists in identifying and resolving potential problems in intermediary settings efficiently.
5. Disregarding scalability: Overlooking scalability considerations during the configuration of intermediary settings may impede growth and hinder future expansion. It is vital to implement flexible and scalable solutions to accommodate evolving network requirements. Failure to do so can lead to bottlenecks, diminished performance, and costly infrastructure modifications in the long run.
Conclusion: Avoiding common configuration mistakes in intermediary settings is instrumental in establishing a robust and seamless digital environment. By understanding and rectifying these prevalent errors, individuals can enhance network reliability, security, and performance, ultimately fostering a productive and efficient digital ecosystem.
How to troubleshoot connectivity issues within the Windows container environment
In the realm of Windows containers, occasionally encountering connectivity problems can be a frustrating and challenging issue. This section aims to guide users through effective troubleshooting methods for addressing these problems and restoring optimal network connectivity within their container setups.
- Double-check network configurations
- Inspect firewall settings
- Validate DNS settings
- Check proxy configurations
- Investigate container network drivers
Before diving into more complex troubleshooting steps, it is essential to verify the network configurations within the Windows container environment. Ensure that the appropriate network adapters are assigned and properly configured to facilitate seamless communication within the container.
Firewalls can often hinder network connectivity, so checking the firewall settings within the Windows container is crucial. Verify that the required ports are open and any specific rules allowing network access are correctly defined. Making adjustments to firewall configurations might resolve connectivity concerns.
Problems with the Domain Name System (DNS) can significantly impact network connectivity within Windows containers. Confirm that the DNS settings are correctly configured and that the container can successfully resolve domain names. Troubleshooting DNS-related issues might involve clearing DNS caches or adjusting DNS server settings.
In some cases, issues with proxies can disrupt network connectivity within Windows containers. Thoroughly review the proxy settings and ensure correct configurations are in place. This may involve verifying proxy server addresses, checking proxy authentication settings, or adjusting proxy bypass rules.
Container network drivers could potentially contribute to connectivity problems. Examine the installed network drivers and their compatibility with the Windows container environment. Updating or reinstalling drivers can often resolve network-related issues within containers.
By methodically troubleshooting these potential problem areas, users can overcome connectivity issues and restore the seamless network functionality within their Windows container environments.
Best practices for configuring proxies in Windows container environments
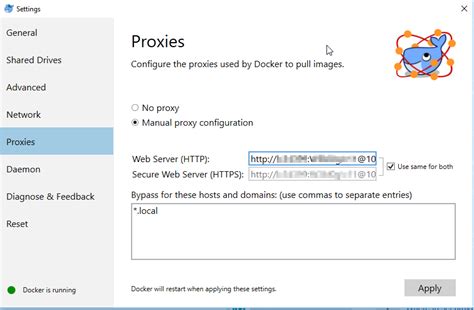
Efficiently configuring proxies in Windows container environments is a vital aspect of establishing seamless network connectivity and ensuring smooth operation within containerized applications. To optimize the proxy configuration process, it is crucial to follow industry best practices and keep certain factors in mind. This section discusses key considerations for configuring proxies in Windows container environments, focusing on efficient network communication and maintaining secure connections.
Consideration 1: Network architecture and communication requirements
Understanding the network architecture and communication requirements of your Windows container environment is essential for effective proxy configuration. Analyzing the network topology and identifying communication patterns can help determine the most suitable proxy setup. Whether it's a complex multi-tier application or a simple microservices architecture, evaluating the network structure enables you to make informed decisions about proxy placement and routing.
Consideration 2: Proxy types and configuration options
There are various types of proxies available, such as forward proxies, reverse proxies, and load balancer proxies. Each proxy type has distinct features and benefits, which can impact the performance and security of your Windows containers. It is crucial to select the appropriate proxy type based on your specific needs and adequately configure it to handle network traffic effectively.
Consideration 3: Security and authentication mechanisms
Securing the communication within your Windows container environment is of utmost importance. Implementing appropriate security mechanisms, such as SSL/TLS protocols and authentication mechanisms, helps protect sensitive data from unauthorized access. This includes configuring proxies to support secure connections and ensuring proper authentication methods are in place.
Consideration 4: Performance optimization strategies
Optimizing proxy performance plays a significant role in enhancing the overall efficiency of your Windows container environment. Employing caching mechanisms, compression techniques, and load balancing strategies can help streamline network traffic and reduce latency. Regular performance monitoring and tuning are essential to continuously improve proxy handling and maintain high-performing containerized applications.
Consideration 5: Scalability and fault tolerance
Designing a scalable and fault-tolerant proxy configuration is crucial for ensuring reliable network connectivity within Windows container environments. Load balancing and clustering techniques enable distributing traffic efficiently and providing redundancy in case of failures. By considering scalability and fault tolerance, you can safeguard against potential network bottlenecks and ensure seamless operation in dynamic containerized environments.
In conclusion, adhering to these best practices when configuring proxies in Windows container environments can significantly enhance network communication, security, and overall performance. By understanding the network architecture, selecting appropriate proxy types, implementing robust security measures, optimizing performance, and ensuring scalability, you can establish a well-structured proxy configuration that supports the seamless operation of your containerized applications.
Exploring Alternate Approaches to Overcoming Limitations in Containerized Environments
In the ever-evolving landscape of container technology, it is not uncommon to encounter challenges related to network connectivity and proxy limitations. While resolving these issues can be a complex endeavor, it is important to explore alternative solutions that can help overcome the constraints imposed by the container environment.
One possible approach involves leveraging advanced networking configurations to route traffic around the limitations posed by proxies. By configuring a secondary network interface or employing network virtualization techniques, containers can potentially bypass proxy restrictions and establish direct connections with external resources.
Another avenue worth exploring involves the use of application-based proxies instead of relying solely on traditional network-based proxies. These proxies work on the application layer, allowing for greater flexibility and control over network traffic. By bypassing the restrictions imposed by traditional proxies, containers can effectively communicate with external resources without hindrance.
Additionally, considering the implementation of proxy auto-configuration (PAC) files within the containerized environment can provide a viable solution. PAC files enable dynamic proxy configurations based on predefined rules, allowing containers to adapt to changing network requirements without manual intervention. This approach not only offers flexibility but also minimizes the reliance on fixed proxy settings.
Furthermore, incorporating secure tunneling protocols such as Secure Shell (SSH) or Virtual Private Networks (VPN) can prove beneficial in bypassing proxy limitations within containers. These protocols establish encrypted connections, effectively masking the container's network traffic and allowing it to bypass any restrictive proxy policies in place.
While proxy limitations in container environments may present challenges, it is crucial to explore and implement alternative solutions. By leveraging advanced networking configurations, application-based proxies, proxy auto-configuration files, and secure tunneling protocols, containers can navigate around these limitations and ensure seamless communication with external resources.
How to fix Windows could not automatically detect this network's proxy settings
How to fix Windows could not automatically detect this network's proxy settings by troubleshooterrors 32,884 views 6 years ago 48 seconds
Self Hosting on your Home Server - Cloudflare + Nginx Proxy Manager - Easy SSL Setup
Self Hosting on your Home Server - Cloudflare + Nginx Proxy Manager - Easy SSL Setup by Raid Owl 328,043 views 2 years ago 15 minutes
FAQ
Why is my proxy not working inside a Windows container?
There could be several reasons for your proxy not working inside a Windows container. One possible reason is that the proxy settings are not properly configured within the container. Make sure that you have set the correct proxy server address and port in the container's network configuration. Additionally, check if any firewall settings or security policies are blocking the proxy connections. Lastly, ensure that the container has proper network connectivity to reach the proxy server.
How can I configure proxy settings inside a Windows container?
To configure proxy settings inside a Windows container, you can use the `netsh` command or modify the proxy settings in the Internet Options of the running container. To use the `netsh` command, open a command prompt inside the container and run `netsh winhttp set proxy proxy-server="http=proxy.example.com:8080;https=proxy.example.com:8080" bypass-list="*.example.com"` where `proxy-server` is the address of your proxy server and `bypass-list` contains the list of URLs that should bypass the proxy. Alternatively, you can open the Internet Options, go to the Connections tab, click on LAN settings, and enter the proxy server details there.
Are there any known issues with proxy usage in Windows containers?
Yes, there have been some known issues with proxy usage in Windows containers. One common issue is that some applications inside the container may not respect the proxy settings configured at the system level. In such cases, you may need to configure the proxy settings specifically for those applications. Another issue is related to authentication, where the container may not have the necessary credentials to authenticate with the proxy server. This can be resolved by providing the appropriate authentication details in the proxy configuration.
Is it possible to use a different proxy server for a specific Windows container?
Yes, it is possible to use a different proxy server for a specific Windows container. To do this, you can either modify the proxy settings within the container individually, or you can launch the container with a custom network configuration that points to a different proxy server. By customizing the proxy settings for a specific container, you can ensure that it uses a different proxy server than the rest of the containers running on the same host.
Can proxy settings inside a Windows container be configured using environment variables?
Yes, proxy settings inside a Windows container can be configured using environment variables. You can set the `HTTP_PROXY`, `HTTPS_PROXY`, and `NO_PROXY` environment variables within the container to specify the proxy server address and bypass list. This allows you to configure the proxy settings without modifying the container's network configuration or individual application settings. Make sure to restart any applications that rely on these environment variables for the changes to take effect.




