When it comes to managing and operating containerized applications on the Windows operating system, an array of challenges arise in providing appropriate access permissions to the files and directories within. Ensuring seamless access to container data while maintaining robust security measures can be a complex endeavor.
Containerization has revolutionized the world of software development, offering numerous advantages such as scalability, portability, and isolation. However, in the context of accessing container data on Windows, special considerations need to be taken into account. The process of granting access rights to container files possesses its own intricacies, requiring meticulous attention to detail.
Efficient management of permissions for container data involves striking a delicate balance between granting necessary privileges for applications to function optimally and safeguarding the integrity and confidentiality of the underlying system. Overlooking the access requirements or misconfiguring permissions can lead to a host of issues, such as data breaches, system instability, and unauthorized modifications.
Thus, administrators must grapple with devising comprehensive strategies to handle access rights for container files. This involves understanding the interplay between various security mechanisms, such as user accounts, groups, and permissions, and the unique challenges posed by containerized applications within the Windows environment.
Understanding the Functionality of Windows Containers in Docker
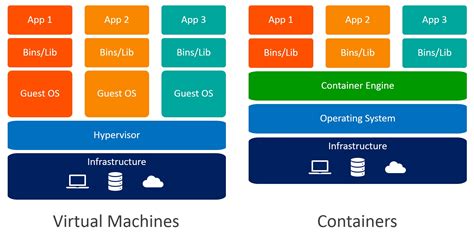
Windows containers in Docker provide a powerful and efficient way to run applications in isolated environments, allowing for flexibility, scalability, and ease of deployment. To fully comprehend the functionality of Windows containers in Docker, it is essential to delve into their core concepts and capabilities.
When utilizing Windows containers in Docker, developers can encapsulate their applications and dependencies into lightweight, standalone executable packages. These packages, known as containers, include everything needed to run the application, such as the code, runtime, system tools, libraries, and settings.
- Isolation: Windows containers ensure strong isolation between applications by leveraging the underlying host operating system's capabilities. Each container runs as an independent entity, providing a secure and isolated environment for the application to operate.
- Resource Efficiency: Windows containers optimize resource utilization by sharing the same kernel with the host operating system. This allows for efficient utilization of CPU, memory, and storage resources, enabling the deployment of multiple containers on a single host machine.
- Portability: Windows containers enable seamless portability across different environments. Once a container is created, it can be easily moved between development, testing, and production environments, ensuring consistent behavior regardless of the underlying infrastructure.
- Scalability: Docker's orchestration tools, such as Docker Swarm and Kubernetes, empower developers to scale their containerized applications effortlessly. By leveraging container clustering, automatic load balancing, and scheduling capabilities, Windows containers facilitate the process of scaling applications to meet ever-changing demands.
- DevOps Integration: Windows containers seamlessly integrate with DevOps practices, streamlining the software development lifecycle. Containerization allows for easy deployment and rollback of applications, facilitating continuous integration and continuous delivery processes.
Overall, understanding the functionality of Windows containers in Docker provides developers with a comprehensive understanding of how to leverage this technology to build, deploy, and manage their applications effectively.
Challenges in Managing Access Privileges
When it comes to the management of access privileges, there are several hurdles that need to be overcome. These obstacles revolve around the administration of rights, permissions, and restrictions to ensure appropriate access is granted to authorized individuals.
- Permission Control Complexity
- Security Vulnerabilities
- User Authorization and Authentication
- The Complexity of Role-based Access
- Auditing and Compliance
Controlling access privileges can often be a complex task, requiring the implementation of reliable tools and methodologies. However, the process may become challenging due to the inherent complexity of managing and maintaining access control lists, permission hierarchies, and user roles.
Moreover, security vulnerabilities pose a significant challenge when it comes to managing access privileges. As threats evolve, organizations need to stay up-to-date with the latest security measures to mitigate potential risks and safeguard sensitive information.
User authorization and authentication also present challenges, as organizations need to ensure that only authenticated and authorized individuals have access to specific resources, systems, or data. The process of verifying identities and assigning appropriate access rights can be intricate, especially in large organizations with numerous users and resources.
The complexity of role-based access further adds to the challenges. Organizations need to define and manage various roles within the system, assigning different access rights to each role based on job responsibilities and security needs. This task can be time-consuming and intricate, requiring careful planning and execution.
Finally, auditing and compliance play a crucial role in managing access privileges. Organizations must monitor and track access activities, ensuring compliance with legal and regulatory requirements. The implementation of audit controls and the continual monitoring of access privileges can be demanding, yet necessary for maintaining a secure and compliant environment.
Lack of File System Compatibility
The challenge of file system compatibility arises when working with Docker containers in a Windows environment. This issue pertains to the inability of different file systems to seamlessly interact, causing complications in accessing and manipulating files within the container.
One of the primary concerns revolves around the divergence in file systems between the host operating system and the container. Windows containers typically use the NTFS file system, while Linux containers are compatible with the ext4 file system. As a result, any attempts to access or modify files that reside within a container may encounter compatibility conflicts.
- Difficulties in achieving file system compatibility can lead to errors and functionality limitations. File permission conflicts may prevent certain operations from executing successfully, hindering the overall functionality of the containerized application.
- The lack of file system compatibility can also impact the ability to share files between different containers, which is a common requirement in complex application environments. This limitation can hinder the overall collaboration and integration of multiple containers.
- In addition, file system compatibility issues increase the complexity of deploying and managing applications within a mixed environment. This complexity can introduce additional maintenance efforts and potentially contribute to a less efficient and unified deployment process.
Addressing the lack of file system compatibility is crucial to ensure the seamless operation of Docker containers in a Windows environment. Various strategies, such as implementing file system translation layers or leveraging file system plugins, can help mitigate compatibility conflicts and enable smoother file interactions within containers.
Permissions Incompatibility between Host and Container
In the context of the topic "Issues with Access Rights to Docker Windows Container Files", this section delves into the discrepancies in permissions that often arise between the host system and the container environment. By examining the permissions mismatch, we aim to shed light on the underlying challenges faced in managing file access and control within Docker containers.
Impact on Data Security and Integrity
When it comes to the management of access privileges, the performance and reliability of a system is of utmost importance. In the context of the aforementioned subject, it is imperative to comprehend the far-reaching repercussions that any vulnerabilities in access controls may have on data security and integrity.
Data security refers to the protection of confidential information from unauthorized access, modification, or destruction. It encompasses various aspects such as authentication, authorization, and encryption. In the context of Docker Windows containers, any shortcomings in access rights management can potentially expose sensitive data to unauthorized individuals or entities.
Integrity, on the other hand, refers to the trustworthiness and reliability of data. It ensures that data remains intact, unaltered, and consistent throughout its lifecycle. Access control issues within Docker Windows containers can compromise data integrity by allowing unauthorized modifications, deletions, or insertions. This can lead to serious consequences, such as data corruption or malicious tampering, which can undermine the reliability and accuracy of the system.
Furthermore, the impact on data security and integrity extends beyond the immediate consequences of unauthorized access or modifications. Breaches in access controls can also result in legal and regulatory compliance challenges. Organizations may face penalties, reputational damage, and loss of customer trust if they fail to adequately safeguard their data.
| Impact | Implications |
|---|---|
| Data Breaches | Exposure of confidential information, potential legal consequences. |
| Data Manipulation | Inaccurate or tampered data, loss of trust in the system. |
| Compliance Challenges | Potential penalties, reputational damage. |
To mitigate the impact on data security and integrity, organizations need to implement robust access rights management strategies, including proper authentication mechanisms, role-based access controls, and regular security audits. Additionally, it is crucial to stay updated with the latest security patches and ensure the proper configuration of Docker Windows containers to minimize the likelihood of access control vulnerabilities.
Strategies for Resolving File Access Challenges in Windows Container Environments
When operating in Windows container environments, it is not uncommon to encounter difficulties related to file access permissions. These challenges can impede the smooth functioning of containerized applications and hinder collaboration between teams. To address these issues effectively, it is crucial to implement appropriate strategies that enable seamless file access for different user roles.
| Strategy | Description |
|---|---|
| 1. Fine-Grained Permissions | Implementing granular file access permissions tailored to each user's role. This approach ensures that individuals have the necessary level of access to specific files and directories without compromising security. By granting access rights based on role-specific needs, organizations can strike a balance between collaboration and data protection. |
| 2. Role-Based Access Control (RBAC) | Utilizing RBAC mechanisms to manage file access rights. RBAC enables organizations to define roles and assign permissions accordingly. This approach simplifies the administrative process by allowing for centralized control and easier management of user access to files. By assigning roles effectively, organizations can ensure that users have the right level of access without granting unnecessary permissions. |
| 3. Containerized File Systems | Exploring containerized file system options that offer better control over file access within containers. By utilizing container-specific file systems, organizations can implement features such as access control lists (ACLs) or using a more robust file sharing mechanism. This approach helps avoid conflicts between host and container file systems and enables more precise file access control. |
| 4. Continuous Monitoring and Auditing | Implementing monitoring and auditing mechanisms to ensure ongoing compliance with access policies. By regularly reviewing file access logs, organizations can identify any unauthorized access attempts or potential vulnerabilities. This strategy aids in detecting and promptly addressing access rights issues, enhancing the overall security posture of the containerized environment. |
By implementing these strategies, organizations can effectively tackle file access challenges in Windows container environments. The combination of fine-grained permissions, RBAC, containerized file systems, and continuous monitoring can help establish a robust and secure file access framework, enabling smooth collaboration and efficient application performance.
Implementing Explicit Permissions for Shared Volumes

In the realm of managing access rights within Docker containers on Windows systems, a noteworthy consideration emerges surrounding the implementation of explicit permissions for shared volumes. Addressing this issue requires a comprehensive understanding of the intricacies involved in controlling file access and ensuring secure data sharing among containers.
Enhancing Security through Access Control:
When it comes to shared volumes within Docker Windows containers, it becomes imperative to implement explicit permissions as a means to enhance security measures. Explicit permissions enable administrators to explicitly define the level of access granted to various containers, ensuring that only authorized parties can modify or access specific files. By implementing access control mechanisms, organizations can effectively mitigate the risk of unauthorized alteration or disclosure of sensitive information.
Configuring Fine-Grained Permissions:
Implementing fine-grained permissions within shared volumes offers a granular approach to access control. Administrators can assign specific permissions to individual files or directories, dictating who can read, write, or execute them. This level of control ensures that containers can interact with shared data while limiting potential security breaches. By explicitly defining these permissions, organizations can maintain data integrity and prevent unauthorized modifications.
Managing Permissions across Multi-Container Environments:
In scenarios where multiple containers access shared volumes, managing permissions becomes a complex task. Organizations need to devise a comprehensive strategy that ensures consistent and synchronized permissions across all participating containers. Implementing mechanisms such as role-based access control (RBAC) can streamline the process and enable efficient management of permissions within a multi-container environment.
Implementing Auditing and Monitoring:
Part of an effective permissions management strategy involves implementing auditing and monitoring mechanisms. By keeping track of file access and modifications, organizations can identify any potential security incidents, track suspicious activities, and take appropriate actions. Regular monitoring and analysis of access logs help maintain the integrity of shared volumes and promptly address any access-related issues.
Conclusion:
Implementing explicit permissions for shared volumes within Docker Windows containers is critical in achieving secure data sharing and maintaining controlled access. By leveraging fine-grained permissions, organizations can enhance security measures, manage permissions across multiple containers, and augment their overall access control strategies. With the implementation of auditing and monitoring mechanisms, organizations can proactively identify and respond to any unauthorized access attempts, ensuring the confidentiality and integrity of shared data.
Leveraging Docker Security Options
In this section, we will explore various techniques to enhance the security of Docker containers by leveraging the available security options and features. By understanding and implementing these options, you can mitigate potential security risks and ensure the confidentiality, integrity, and availability of your containerized applications.
1. Harden Container Images:
- Utilize security-focused base images to ensure a secure foundation.
- Regularly update and patch container images to address known vulnerabilities.
- Minimize the attack surface by removing unnecessary software and dependencies.
2. Implement Access Controls:
- Employ user namespaces to isolate container processes from the host.
- Restrict container capabilities and privileges to minimize the impact of potential security breaches.
- Implement resource limitations to prevent container abuse and resource exhaustion.
3. Secure Container Communications:
- Enable secure network configurations, such as using encrypted connections and limiting exposed ports.
- Utilize container networking solutions that offer additional security controls, such as network segmentation and isolation.
- Implement appropriate firewall rules to control inbound and outbound traffic.
4. Monitor and Audit Container Activities:
- Implement container logging to track and monitor container activities for potential security incidents.
- Utilize container runtime security tools to detect and alert on malicious activity.
- Regularly review container logs and perform security audits to identify and mitigate any security vulnerabilities.
By leveraging these Docker security options, you can strengthen the overall security posture of your containerized applications and protect them from various potential threats and vulnerabilities.
Best Practices for Managing Privileges in Windows Containers

Introduction:
In the world of Windows containers, ensuring proper access rights and privileges is crucial to maintaining a secure and efficient system. This section explores some best practices for managing access rights within Docker Windows containers, focusing on strategies to enhance security, optimize performance, and minimize potential issues.
1. Defining Appropriate User Roles:
One of the fundamental steps in managing access rights is defining appropriate user roles within your Windows containers. By carefully assigning specific privileges to each user role, you can restrict access to critical resources, ensuring that only authorized individuals can perform certain actions.
2. Implementing Least Privilege Principle:
Following the principle of least privilege is a crucial aspect of managing access rights within Docker Windows containers. This principle dictates that each user or process should have the minimal level of privilege required to perform its intended function. By minimizing privileges, you can mitigate the risk of potential vulnerabilities and limit the impact of any potential security breaches.
3. Regularly Auditing Access Rights:
To maintain a secure environment, it is essential to regularly audit and review access rights within your Windows containers. This includes periodically reviewing user roles, permissions, and privileges to ensure they align with the desired security policies. By conducting audits, you can identify any potential weaknesses or unauthorized access and take necessary actions to rectify them.
4. Consistent Security Updates:
Keeping your Windows containers up-to-date with the latest security patches is critical for minimizing access-related vulnerabilities. Regularly applying security updates and patches can address known vulnerabilities and strengthen the overall security posture of your Docker Windows containers. It is recommended to follow a systematic approach to ensure timely and comprehensive updates across all containers.
5. Monitoring and Logging:
Implementing robust monitoring and logging mechanisms is essential for managing access rights effectively. By collecting and analyzing logs, you can detect any suspicious activities or unauthorized access attempts within your Windows containers. This enables you to promptly respond to security incidents and mitigate potential risks before they escalate.
Conclusion:
Managing access rights within Docker Windows containers is crucial for maintaining a secure and well-optimized environment. By implementing the best practices discussed in this section, you can enhance the overall security posture of your containers, minimize potential issues, and ensure the smooth operation of your applications and systems.
FAQ
What are the common issues with access rights to Docker Windows container files?
Common issues with access rights to Docker Windows container files include permission errors when trying to access or modify files within the container, inability to delete or modify certain files, and difficulty in mounting host volumes with correct access permissions.
Why am I encountering permission errors when trying to access files within a Docker Windows container?
You may encounter permission errors when trying to access files within a Docker Windows container due to mismatched user and group IDs between the container and the host system. This can occur when files are created within the container by processes running as a different user than the one used on the host system.
How can I resolve permission issues when accessing files in a Docker Windows container?
To resolve permission issues when accessing files in a Docker Windows container, you can try setting explicit permissions for the files or directories within the container, ensuring that the user and group IDs within the container match those on the host system, or using workarounds such as running processes within the container as the same user as the one used on the host system.
What should I do if I am unable to delete or modify certain files within a Docker Windows container?
If you are unable to delete or modify certain files within a Docker Windows container, you can try checking the file's ownership and permissions, ensuring that the user running the container has the necessary privileges, or using administrative access within the container to modify or delete the files.




