In today's ever-evolving world of technology, robust and secure communication is paramount. In our quest to establish reliable connections, we often encounter challenges when it comes to directing the flow of data through different ports. However, fear not, for in the vast realm of network administration, there exists a powerful tool that can effectively reroute traffic without compromising security.
Imagine a scenario where you have a Windows Server, a fortress of your network's stability, and you desire to streamline the process of communication. By leveraging the capabilities of port redirection, you can effortlessly guide data packets from one port to another, ensuring seamless transmission and facilitating remote access. This ingenious technique allows for efficient resource allocation, enhanced network performance, and even increased flexibility in managing incoming connections.
Within the realm of networking, SSH (Secure Shell) plays a vital role in enabling secure remote administration and data transfer. And yes, you guessed it right – our focus today lies on discovering the art of port redirection specifically for SSH! By skillfully redirecting SSH ports, you can establish an impregnable fortress of connectivity, safeguarding your system against unauthorized access while conveniently managing the traffic flow.
Throughout this insightful article, we will unravel the secrets of port redirection on Windows Server and equip you with the knowledge of redirecting SSH ports like a seasoned network ninja. You'll explore various techniques, understand their benefits, and learn how to effortlessly implement these redirection mechanisms. Get ready to unlock the true potential of your Windows Server and elevate your network administration skills to new heights!
Exploring Port Redirection Concepts in the Windows Server Environment
In this section, we will delve into the fundamental concepts of port redirection within the Windows Server ecosystem. By comprehending the underlying principles, you will gain a deeper understanding of how different network ports can be rerouted to enhance connectivity and improve security while efficiently managing network traffic.
By examining the intricacies of port redirection, we can establish a foundation for effective network management strategies. We will explore alternative methods for steering network traffic, redirecting data, and ensuring seamless communication between different applications and services within the Windows Server environment.
As we unravel the complexities of port redirection, we will explore the mechanisms that enable the establishment of efficient communication channels. Consequently, we will be able to direct network traffic towards highly optimized routes while maximizing resource utilization.
Furthermore, we will investigate potential use cases and scenarios in which port redirection can prove to be indispensable. By understanding these practical implications, you can make informed decisions when it comes to implementing port redirection techniques within your Windows Server environment.
With a comprehensive comprehension of port redirection, you will be equipped to leverage its benefits to enhance network security, streamline network traffic, and optimize communication pathways within your Windows Server setup.
A Novice's Guide to Directing SSH Connections
In the world of network administration and secure remote connections, the ability to direct SSH ports is a fundamental skill that every beginner should grasp. By understanding the concepts and methodologies behind SSH port redirection, individuals can ensure efficient and secure communication between different network entities.
This section aims to introduce newcomers to the art of directing SSH connections, without getting tangled in the technical jargon. It will shed light on the basic principles and techniques used to reroute SSH traffic, enabling users to establish secure connections across multiple networks.
Throughout this guide, we will explore the importance of SSH port redirection and its various applications in enhancing network security and accessibility. We will delve into the concepts of port forwarding, tunneling, and the different tools and protocols that facilitate this process. By gaining a clear understanding of these fundamental principles, beginners will be equipped with the necessary knowledge to successfully redirect SSH ports in practical scenarios.
Understanding the Concept of Port Redirection
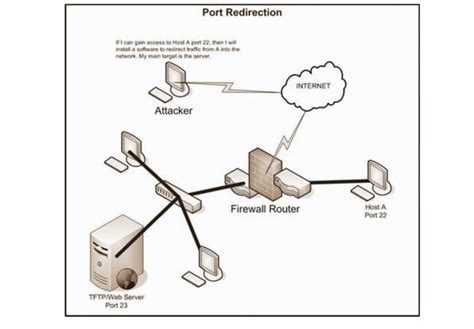
Port redirection, also known as port forwarding or port mapping, plays a crucial role in network communication, facilitating the seamless transfer of data between different systems. It involves the process of redirecting network traffic from one port to another, enabling the communication between two or more devices or services. The fundamental principle behind port redirection is the rerouting of data packets to a designated destination port, ensuring efficient and secure transmission.
Why is port redirection important?
Port redirection serves as a vital component in network infrastructure, allowing for various functionalities such as load balancing, security, and network optimization. By redirecting traffic to specific ports, organizations can optimize the efficiency of their network resources and streamline communication between different applications or services. Additionally, port redirection plays a crucial role in enhancing security measures, as it enables the implementation of firewall rules and permits the translation of external requests to internal systems.
How does port redirection work?
Port redirection operates by intercepting incoming data packets and modifying their destination port information before forwarding them to the appropriate destination. This process involves establishing a set of rules or configurations within the network infrastructure to govern the redirection. These rules can be defined at the router, firewall, or server level and ensure that network traffic is efficiently directed to the desired destination port.
The benefits of utilizing port redirection
By utilizing port redirection, organizations can achieve greater flexibility and scalability in their network architecture. It allows for the seamless integration of different systems and services, enabling efficient communication between them. Additionally, port redirection aids in load balancing, enabling the distribution of network traffic across multiple servers, thus improving overall system performance and resilience. Moreover, by employing port redirection techniques, organizations can enhance their network security by implementing stricter control measures and mitigating the risks associated with malicious network attacks.
Enhancing Network Security: The Importance of SSH Port Redirection
In the ever-evolving world of cybersecurity, it is crucial for organizations to employ effective measures to protect their network infrastructure. One such measure that plays a vital role in enhancing network security is the practice of redirecting SSH ports. By implementing SSH port redirection, organizations can strengthen their defenses against unauthorized access and potential cyber threats.
Ensuring Enhanced Protection:
Redirecting SSH ports involves modifying the default configuration settings to direct incoming SSH traffic to alternative ports. This process adds an extra layer of security by obfuscating the standard port commonly used for SSH connections, making it harder for malicious actors to identify and exploit potential vulnerabilities.
Preventing Unauthorized Access:
By redirecting SSH ports, organizations significantly reduce the risks associated with unauthorized access attempts. Changing the default SSH port can deter automated scanning tools that are typically programmed to target the standard port numbers. This proactive method helps to safeguard network resources by minimizing the potential threats posed by brute force attacks and unauthorized access attempts.
Enhanced Stealth and Concealment:
SSH port redirection provides organizations with increased control over their network infrastructure's visibility. By utilizing non-standard SSH ports, organizations can limit their exposure to potential attackers. Through this method, organizations can conceal their SSH services and minimize the chances of being targeted by malicious actors scanning for vulnerable systems.
Improved Network Performance:
An additional benefit of redirecting SSH ports is the potential improvement in network performance. By diverting SSH traffic away from the standard port, organizations can reduce congestion and distribute network resources more efficiently. This redirection helps optimize network performance, ensuring that critical resources are readily available for other essential tasks.
Elevating Network Security Best Practices:
Overall, redirecting SSH ports is a fundamental practice that aligns with industry-leading network security guidelines. It demonstrates a proactive approach to protect sensitive information, bolster network defenses, and mitigate potential security risks. By adopting this measure, organizations can enhance their overall cybersecurity posture and ensure the utmost protection for their network infrastructure.
Enhancing Security and Network Efficiency
In today's interconnected world, businesses rely heavily on secure and efficient networks to protect their sensitive information and ensure smooth operations. To achieve this, it is crucial to implement robust security measures and optimize network efficiency. In this section, we will explore various strategies and best practices that can enhance both the security and efficiency of your network.
Strengthening Security:
One of the key aspects of enhancing network security is the implementation of strong authentication protocols. By utilizing advanced authentication methods, such as multi-factor authentication and biometric authentication, organizations can significantly reduce the risk of unauthorized access to their networks. Additionally, employing robust encryption techniques, like AES (Advanced Encryption Standard), can protect data in transit and at rest from potential threats.
Furthermore, establishing a comprehensive network access control policy can help restrict unauthorized access to sensitive resources. By implementing measures such as role-based access control (RBAC), organizations can ensure that only authorized individuals have access to specific systems or data. Regular security audits and penetration testing can also identify vulnerabilities in the network infrastructure, allowing organizations to proactively address any potential security risks.
Improving Network Efficiency:
To optimize network efficiency, organizations need to carefully manage network traffic and minimize unnecessary congestion. Implementing Quality of Service (QoS) techniques can prioritize critical applications and ensure uninterrupted service for essential operations. By leveraging techniques like traffic shaping and bandwidth allocation, network administrators can allocate resources efficiently and prevent bottlenecks.
Another approach to enhance network efficiency is through the use of caching and content delivery networks. These technologies store frequently accessed data closer to the end-users, reducing latency and improving overall network performance. Additionally, implementing load balancing mechanisms can distribute network traffic evenly across multiple servers, further enhancing efficiency and scalability.
Conclusion:
By focusing on both security and network efficiency, organizations can create a robust and reliable network infrastructure. Implementing strong authentication protocols, encryption techniques, and access control policies can safeguard sensitive information from potential threats. Simultaneously, employing QoS techniques, caching, and load balancing mechanisms can optimize network performance and ensure smooth operations. By incorporating these strategies and best practices, businesses can enhance their overall network security and efficiency, enabling them to thrive in today's digital landscape.
The Various Approaches for Redirecting Connections to Secure Shell Ports
In the realm of network security, there exist a variety of techniques to reroute incoming traffic targeting secure shell ports, enabling administrators to enhance the security and availability of their systems. This section explores the different methods that can be employed to redirect connections intended for secure shell services, allowing for a more comprehensive understanding of the possibilities available to system administrators.
- 1. Port Forwarding
- 2. NAT Mapping
- 3. Tunneling
- 4. Proxying
Each method possesses its unique strengths and weaknesses, making them suitable for diverse scenarios and requirements. Port forwarding involves transmitting network traffic from one port to another, potentially on a different network device. NAT mapping utilizes the network address translation technique to redirect incoming connections to a specific internal address and port. Tunneling establishes an encrypted tunnel within an existing network connection, ensuring secure transport of data. Lastly, proxying involves an intermediary server acting as a bridge between clients and servers, effectively redirecting SSH traffic.
Understanding the different methods available for redirecting SSH ports allows administrators to choose the most appropriate technique for their specific network setup and security goals. By leveraging the knowledge of these approaches, system administrators can enhance the security posture and operational integrity of their systems while providing reliable, secure access to remote users.
A Comparison of NAT, Firewall, and Proxy Solutions
When it comes to managing network traffic and ensuring security, various solutions can be utilized. In this section, we will explore and compare three commonly used methods: Network Address Translation (NAT), Firewall, and Proxy. Each of these solutions plays a crucial role in network communication and offers its own set of benefits and limitations.
- Network Address Translation (NAT): NAT acts as an intermediary between a private network and the public internet, allowing multiple devices within the private network to share a single public IP address. By modifying the source and destination IP addresses in network packets, NAT enables communication between internal and external networks while providing a certain level of security.
- Firewall: A firewall serves as a security measure by controlling incoming and outgoing network traffic based on predetermined rules. It acts as a barrier between trusted and untrusted networks, ensuring that only authorized connections are allowed. Firewalls can be implemented as hardware or software and offer various levels of protection against external threats.
- Proxy: A proxy acts as an intermediary between clients and servers, forwarding requests on behalf of the client and returning responses from the server. Proxies are commonly used to enhance performance, provide anonymity, and control access to certain resources. They can be configured to block or allow specific types of traffic, and can also serve as a caching mechanism to improve network efficiency.
While each of these solutions serves a distinct purpose, they can also complement each other in a network environment. NAT provides network address translation and enables access to the internet for multiple devices, while firewalls add an extra layer of security by filtering incoming and outgoing traffic. Proxies, on the other hand, offer additional functionality by acting as intermediaries for client-server communication.
Ultimately, the choice of solution depends on the specific requirements and objectives of a network infrastructure. By understanding the characteristics and capabilities of NAT, firewalls, and proxies, network administrators can make informed decisions to ensure optimal network performance and security.
A Step-by-Step Guide to Rerouting Secure Shell Connections in Windows Server
In this section, we will explore the process of modifying the default route of Secure Shell (SSH) connections on a Windows Server. By redirecting SSH ports, you can enhance the security and efficiency of your server by controlling the flow of incoming and outgoing traffic. This comprehensive step-by-step guide will walk you through the entire process, providing detailed instructions accompanied by helpful visuals and explanations.
Table of Contents:
| Step 1: Assessing the Current SSH Configuration |
| Step 2: Configuring Port Forwarding |
| Step 3: Modifying Firewall Rules |
| Step 4: Testing the SSH Port Redirection |
Step 1: Assessing the Current SSH Configuration
Before diving into the process of redirecting SSH ports, it is crucial to understand the current configuration of your Windows Server. This step will guide you through the necessary steps to assess the existing SSH settings, including identifying the default ports and any potential conflicts.
To start, open the Command Prompt and enter the appropriate commands to retrieve the SSH configuration details. This will provide you with the necessary information to proceed with the next steps of the port redirection process.
Step 2: Configuring Port Forwarding
Once you have a clear understanding of the current SSH configuration, it's time to configure the port forwarding settings. This step involves modifying the network settings to reroute the SSH traffic to the desired ports.
Within this section, you will learn how to open the necessary ports in the Windows Firewall and create port forwarding rules to reroute the SSH connections. Detailed instructions, accompanied by screenshots, will guide you through the entire process to ensure a seamless and error-free configuration.
Step 3: Modifying Firewall Rules
After configuring the port forwarding settings, it is vital to modify the firewall rules to allow SSH traffic through the new port redirection. This step will guide you through the process of updating the firewall rules to ensure uninterrupted communication with your Windows Server.
Through a detailed walkthrough, you will learn how to add inbound and outbound rules to the Windows Firewall, enabling SSH traffic to pass through the newly redirected ports successfully.
Step 4: Testing the SSH Port Redirection
Now that you have completed the configuration and modification steps, it is time to test the SSH port redirection to ensure its effectiveness. This final step will guide you through the process of verifying the changes done to the SSH configuration and ensuring the successful rerouting of secure shell connections.
By running various tests and troubleshooting techniques covered in this section, you will be able to confirm that your Windows Server is securely redirecting SSH traffic through the newly configured ports.
By following this step-by-step guide, you will gain the necessary knowledge and skills to redirect SSH ports in your Windows Server efficiently. Enhance the security and performance of your server by taking control of the SSH traffic flow and ensuring optimal connectivity.
Configuring Port Forwarding in the Firewall of a Windows Server
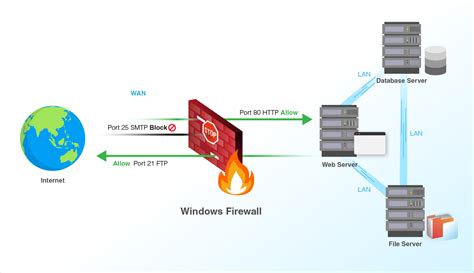
In this section, we will explore the process of setting up port forwarding in the firewall of a Windows Server. This feature allows you to direct incoming network traffic from specific ports to different destinations within your network, enabling efficient network management and improved security.
The configuration of port forwarding involves modifying the firewall settings in order to redirect incoming requests from one port to another. By doing so, you can effectively route traffic to specific applications or devices within your network, allowing them to receive and respond to requests from external sources.
To begin the configuration process, you will need to access the Windows Server Firewall settings. Within these settings, you can create rules that define how incoming traffic is handled for specific ports. By specifying the source and destination ports, as well as the intended destination IP address, you can determine the path that network traffic will take.
It is important to note that proper configuration of port forwarding requires an understanding of both the network topology and the services being deployed. By carefully considering the needs and requirements of your network infrastructure, you can define port forwarding rules that optimize network performance and enhance security.
Step 1: Accessing Windows Server Firewall Settings
To begin the configuration process, open the Windows Server Firewall settings. This can be done by navigating to the Control Panel, selecting "System and Security," and then clicking on "Windows Firewall." Within the firewall settings, you will find the options to create and modify inbound and outbound rules.
Step 2: Creating an Inbound Rule for Port Forwarding
Once you are in the Windows Server Firewall settings, click on "Advanced settings" to access more advanced configuration options. From there, navigate to the "Inbound Rules" section and click on "New Rule" to create a new rule for port forwarding. Follow the wizard, specifying the source and destination ports, as well as the desired action for incoming traffic.
Step 3: Testing and Verifying Port Forwarding
After creating the port forwarding rule, it is crucial to test and verify its functionality. You can do this by attempting to establish a connection from an external source to the specific port you have forwarded. If the connection is successful, it indicates that the port forwarding configuration is correctly directing traffic to the desired destination within your network.
In conclusion, configuring port forwarding in the Windows Server firewall allows you to selectively redirect incoming network traffic based on predefined rules. This feature enables efficient management of network resources and enhances the security of your infrastructure by directing traffic to specific applications or devices within your network.
Understanding the Potential Risks of Network Port Forwarding
Within the realm of network communication, it is crucial to comprehend the various hazards that may arise when employing techniques such as port forwarding or port mapping. This section aims to shed light on the potential risks associated with redirecting network traffic from one port to another on a server, without explicitly referring to the specific context of Windows Server or SSH ports.
1. Unauthorized Access One major concern is the possibility of unauthorized access to the designated destination port, allowing potential malicious actors to exploit vulnerabilities or gain unauthorized entry into protected systems. By redirecting network traffic, an unintended entry point may be created, providing an opportunity for unauthorized individuals to compromise the system. | 2. Raising Attack Surface Network port redirection can inadvertently increase the attack surface of a server or network environment. By forwarding traffic to an alternate port, potential vulnerabilities specific to that port may be exposed, which were initially protected due to the lack of direct access. This expanded attack surface presents an elevated risk of exploitation by threat actors. |
3. Misconfiguration and Inconsistent Policies A misconfigured port redirection setup poses a considerable threat to the network security posture. If the redirection is implemented improperly, it may result in unintentional exposure of sensitive information or services, rendering them vulnerable to unauthorized access. Additionally, inconsistent policies regarding port redirection across different systems and environments can lead to confusion and potential security gaps. | 4. Interference with Network Services Redirection of network traffic can potentially interfere with essential network services and applications. By redirecting ports, the intended functionality may be disrupted, causing operational issues, delays, or even the temporary unavailability of critical services. It is essential to carefully evaluate and test the implications of port redirection to avoid any adverse effects on network infrastructure. |
5. Logistical Challenges in Monitoring and Troubleshooting Implementing port redirection introduces logistical challenges in terms of monitoring and troubleshooting network traffic. With multiple redirected ports, it becomes more complex to identify and analyze potential anomalies, making it harder to detect and mitigate security incidents or network performance issues. | 6. Compliance and Regulatory Considerations Port redirection practices need to align with applicable compliance standards and regulations, imposing additional requirements and considerations on organizations. Failure to comply with these guidelines can result in severe consequences, including financial penalties or loss of reputation. |
Addressing Security Concerns and Best Practices
In the realm of enhancing security measures and ensuring optimal performance, it is crucial to address various concerns and follow industry best practices when redirecting network traffic. By implementing effective strategies, businesses can safeguard their systems and protect sensitive data from potential threats.
Enhancing Data Encryption: To bolster security during port redirection, it is essential to prioritize data encryption. Utilizing robust encryption algorithms and protocols ensures that sensitive information remains protected during transmission.
Implementing Access Controls: Controlling access to redirected ports is vital in mitigating unauthorized access attempts. By implementing access control mechanisms such as firewalls and access lists, organizations can regulate network traffic and allow only authorized users to connect to specific redirected ports.
Regularly Updating Security Patches: Keeping systems and software up to date plays a critical role in addressing security vulnerabilities. Regularly applying security patches and updates helps to patch any known vulnerabilities and strengthen the overall security posture of the server.
Monitoring and Logging: Implementing robust monitoring and logging practices allows for the proactive identification and mitigation of potential security incidents. By regularly reviewing logs and analyzing network traffic, organizations can detect and respond to any suspicious activities promptly.
Continuous Security Training: Educating personnel about security best practices and potential threats is crucial for maintaining a secure network environment. Conducting regular security awareness training sessions ensures employees are equipped with the knowledge and skills to recognize and respond effectively to security incidents.
Regular Security Audits: Conducting periodic security audits assists in identifying any weaknesses in the network infrastructure and redirecting ports. By assessing the overall security posture, organizations can make necessary changes and enhance security measures accordingly.
Implementing Multi-factor Authentication: Employing multi-factor authentication adds an extra layer of security when redirecting ports. By requiring multiple forms of verification, such as passwords, physical tokens, or biometrics, organizations can significantly reduce the risk of unauthorized access.
Maintaining Secure Network Segmentation: Implementing network segmentation helps in isolating redirected ports and limiting the potential impact of security breaches. By dividing the network into separate segments, organizations can contain any potential threats and control the flow of network traffic more effectively.
Regular Security Assessment: Periodically assessing the security measures in place allows for the identification of any gaps or weaknesses that may have arisen over time. Regular security assessments enable organizations to take proactive steps towards strengthening their overall security stance.
In conclusion, addressing security concerns and adhering to industry best practices is critical when implementing port redirection for SSH ports. By following these guidelines, businesses can ensure a secure and optimized network environment, safeguarding their systems and data from potential threats.
Troubleshooting Common Issues with SSH Port Redirection
When it comes to redirecting ports for SSH, there can be various challenges that users may encounter. In this section, we will explore some of the common issues that can arise during the process, and provide tips on how to troubleshoot them effectively.
1. Connectivity Problems:
- Failed connection attempts
- Connection timeouts
- Unresponsive SSH service
2. Firewall Configuration:
- Blocked incoming or outgoing connections
- Incorrect firewall rules
- Misconfigured network settings
3. NAT and Router Settings:
- Port forwarding issues
- Incorrect NAT configurations
- Router compatibility problems
4. Authentication and Authorization:
- Incorrect login credentials
- Permission denied errors
- Invalid public or private keys
5. Network Infrastructure:
- Network congestion
- Bandwidth limitations
- Unreliable internet connection
6. Software and Dependency Conflicts:
- Outdated SSH client or server software
- Incompatible third-party software
- Dependency conflicts
7. Log Analysis:
- Reviewing SSH logs for error messages
- Identifying patterns or inconsistencies
- Troubleshooting based on log information
By understanding these common issues and implementing targeted troubleshooting strategies, users can overcome challenges related to SSH port redirection and optimize the performance and security of their remote server connections.
How to Setup Port Forward For a VM in Virtualbox
How to Setup Port Forward For a VM in Virtualbox by root tech 17,899 views 2 years ago 3 minutes, 40 seconds
FAQ
What is port redirection in Windows Server?
Port redirection in Windows Server is a technique used to redirect network traffic from one port to another. It allows you to redirect incoming SSH traffic from a specified port to a different port on the same or a different machine.
Why would I need to redirect SSH ports in Windows Server?
You may need to redirect SSH ports in Windows Server for several reasons. One common scenario is when you want to secure your server by changing the default SSH port. Another reason could be if you have multiple servers behind a firewall and you want to redirect SSH traffic to a specific server.
How can I redirect SSH ports in Windows Server?
To redirect SSH ports in Windows Server, you can use either the built-in Windows Firewall or a third-party firewall software. You need to create an inbound rule that maps the incoming SSH port to the desired port on your server. Detailed steps on how to do this can be found in the article.




