In today's fast-paced world of technology, it's crucial to stay ahead of the curve when it comes to managing your computing environment. One way to achieve this is through the efficient setup and configuration of a powerful network system. By leveraging the potential of cutting-edge software solutions, you can effortlessly transform your Windows operating system into a well-connected hub that fosters seamless communication and collaboration.
Achieving this level of functionality is possible thanks to the innovative capabilities of Docker, a tool that revolutionizes the way we build, package, and deploy applications. Docker not only enhances the portability of your software but also allows for the creation of isolated environments called containers, each with its own set of dependencies and resources. By leveraging Docker's immense potential, you can create a network that empowers your Windows machine, enabling it to smoothly interact with other devices, systems, and applications.
When it comes to configuring a Docker network in Windows, there are a multitude of factors and techniques to consider. From creating and managing the necessary virtual networks to establishing secure connections between containers, understanding the intricacies of this process is essential. By implementing a robust Docker network, you have the power to optimize your workflow, enhance the scalability of your applications, and ensure that your valuable data is shielded from potential cybersecurity threats.
Understanding the Networking Model of Containerization on the Windows Platform
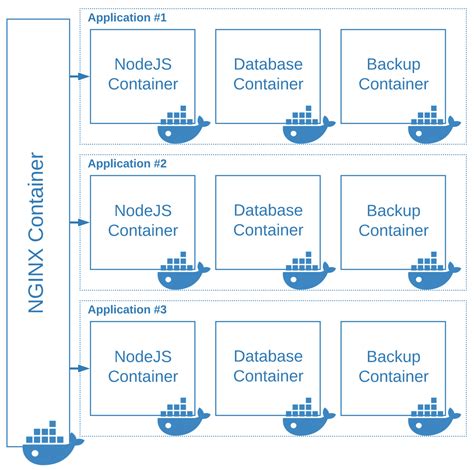
Containerization has revolutionized software development and deployment processes by providing a lightweight and portable environment for running applications. In the context of Windows, understanding the networking model in Docker is crucial to effectively leverage its capabilities.
An essential aspect of containerization on Windows involves comprehending the networking mechanisms that enable seamless communication among containers and with the outside world.
Containers have their own isolated network stack, which allows them to have their own IP address and network interfaces. This isolation ensures that containers can run independently and securely without interfering with each other's networking configurations.
Furthermore, Docker provides multiple networking options that facilitate different communication scenarios.
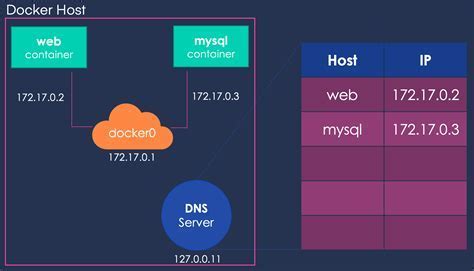
The default network configuration in Docker is the bridge network, which enables containers to communicate with each other using IP addresses assigned by a bridge network interface.
Another networking option is the host network mode, where containers share the host's network stack. In this mode, the containers use the same IP address as the host, allowing them to access network services on the host directly.
Docker also offers the overlay network, which enables container communication across multiple Docker hosts, making it ideal for distributed applications.
Understanding the various networking options and their implications is essential for designing and deploying containerized applications effectively in a Windows environment.
Installing Docker on a Windows Operating System
The process of installing Docker on a Windows operating system involves configuring your system to support containerization technology. This enables you to run and manage applications within isolated containers, providing a lightweight and scalable solution for deploying software.
To begin the installation, you will need to download the Docker Desktop application from the official Docker website. Once downloaded, follow the installation wizard to set up Docker on your Windows machine.
- Launch the Docker installer and select the appropriate installation options for your system.
- Accept the license agreement and choose the location where you want Docker to be installed.
- During the installation process, Docker will prompt you to enable Hyper-V, a Windows feature that allows virtualization. If Hyper-V is not enabled on your system, you will need to restart your computer to complete the installation.
- After the installation is complete, Docker will launch automatically. You can verify its successful installation by opening a command prompt and running the command "
docker version". This will display the version details of Docker installed on your system.
Once Docker is installed on your Windows machine, you can proceed to create and manage Docker containers, build custom images, and run applications in a containerized environment. Docker provides a user-friendly interface that allows you to easily manage and monitor your containers through a web-based dashboard.
By setting up Docker on your Windows operating system, you gain the ability to take advantage of containerization technology, enabling you to streamline your software development and deployment processes.
Configuring Network Settings in Docker: Optimizing Connectivity and Communication
In this section, we will explore the essential steps to fine-tune and customize the network settings in Docker. By adjusting network configurations, you can enhance the efficiency of connectivity between containers, facilitate seamless communication, and ensure optimal performance within your Docker environment.
1. Establishing Connectivity: This step focuses on establishing reliable connections between different containers within the Docker network. We will explore various techniques and strategies to optimize connectivity, including configuring network bridges, setting up virtual networks, and utilizing load balancers for efficient data transmission.
2. Enhancing Communication: Effective communication is vital for the smooth functioning of containerized applications. In this part, we will delve into techniques for enhancing inter-container communication. We will cover topics such as configuring DNS resolvers, implementing network aliases, and utilizing network endpoints to streamline communication channels.
3. Network Security: Security is a significant concern when it comes to Docker networks. In this section, we will discuss best practices and techniques for securing your Docker network to protect against potential vulnerabilities and unauthorized access. Topics to be covered include setting up firewalls, implementing network policies, and leveraging encryption protocols to ensure data integrity.
4. Scalability and Load Balancing: As your Docker deployments grow, ensuring scalability and load balancing becomes crucial. This part will explore how to configure network settings to accommodate high traffic and distribute workloads evenly across containers. Topics include utilizing swarm mode, implementing service discovery mechanisms, and configuring load balancers for optimal resource allocation.
5. Troubleshooting and Debugging: Despite careful configuration, network issues can still arise. In this final section, we will cover essential troubleshooting techniques to identify and resolve common network problems in Docker. We will discuss tools for network monitoring, analyzing logs, and troubleshooting connectivity and performance issues.
By understanding and implementing these network configuration strategies, you can maximize the efficiency, security, and scalability of your Docker setup, enabling robust connectivity and smooth communication between containers within your Windows environment.
Creating a Docker Networking Environment
Exploring the realm of containerization allows for the creation of dynamic and isolated environments, achieving efficient deployment and scalability. One fundamental aspect is establishing a robust networking infrastructure specifically tailored to Docker containers, allowing seamless communication and interconnectivity between them.
In this section, we will delve into the process of creating a custom Docker network system in a Windows environment. By configuring a network, you can define the rules and guidelines for communication between containers, enabling secure and reliable data transfer. We will explore various techniques and options to establish a network that meets your specific needs.
Throughout the article, we will walk through the steps to set up and configure the Docker network, utilizing alternative terminologies such as "constructing," "establishing," or "building" rather than repeatedly using the word "creating." This will ensure a comprehensive understanding of the process while maintaining clarity and readability.
Moreover, we will discuss different scenarios where creating a Docker network becomes essential, highlighting the benefits and advantages obtained from this network architecture. By showcasing real-life use cases, you will gain a practical understanding of how Docker networks can revolutionize your development and deployment workflows.
Lastly, we will provide guidelines and best practices to optimize your Docker networking setup, ensuring efficient resource utilization and robust container communication. By following these recommendations, you can avoid common pitfalls and enhance your overall Docker experience.
Connecting Containers within a Docker Network

In the context of establishing a cohesive and interconnected environment for running multiple containerized applications, the ability to connect containers within a Docker network is essential. This section will explore the various mechanisms and strategies for establishing communication and data exchange between containers, enabling seamless functionality and collaboration.
Container Linking One approach to connect containers is through container linking. This allows containers to communicate directly by creating a secure and isolated network bridge between them. By establishing links between specific containers, data and services can be shared, enabling applications to work in synergy. | Network Bridging Another method for connecting containers is through network bridging. This involves creating a virtual network bridge that enables containers to communicate with one another within a defined network segment. With network bridging, containers can have their own isolated IP address and be reachable by other containers on the same network segment. |
Overlay Networks Overlay networks offer a way to connect containers across multiple hosts. They provide a virtual network that spans across various Docker hosts, enabling seamless communication between containers regardless of their physical location. Overlay networks are particularly useful in distributed applications and container orchestration scenarios. | Service Discovery Facilitating the connection between containers, service discovery mechanisms are crucial. By utilizing service discovery, containers can dynamically locate and connect to other containers or services within a Docker network. This allows for easy scalability, resilience, and adaptability of distributed systems running in containers. |
Network Security Ensuring network security within Docker environments is paramount. This involves implementing access controls, network segmentation, and encryption mechanisms to protect containerized applications and their data. By properly configuring network security measures, vulnerabilities can be minimized, ensuring the integrity and confidentiality of the connected containers. | Load Balancing To optimize the distribution of workload across containers, load balancing techniques can be employed within a Docker network. Load balancers enable even distribution of requests and resources, enhancing performance, scalability, and availability of containerized applications. Various load balancing strategies, such as round-robin or least-connections, can be implemented to meet specific requirements. |
By understanding the different approaches and considerations involved in connecting containers within a Docker network, developers and system administrators can effectively leverage Docker's networking capabilities to build robust and interconnected containerized environments.
Accessing Docker Network from Host Machine
In this section, we will explore the ways to connect to the network created within Docker using your host machine. By establishing a connection with the Docker network, you can access and interact with the containers and their services, even without directly using the Docker CLI or entering the container environment.
Interacting with Docker Containers:
There are several methods to interact with the Docker containers running within the Docker network from your host machine. One approach is by utilizing the container's IP address. Each container within the Docker network is assigned a unique IP address, which can be used to establish a connection with the container directly.
For example, you can use the IP address to access a web server running inside a container from your host machine using a web browser.
Mapping Container Ports:
Another way to access Docker network from the host machine is by mapping container ports to the host machine's ports. This allows you to access the services running inside the container by accessing the specified port on the host machine's IP address. By mapping the ports, you can easily access containerized applications from your web browser or any other client application on the host machine.
For instance, if a container is running a web server on port 8080, you can map this port to port 80 on the host machine, enabling you to access the web server by navigating to http://localhost on your host machine's web browser.
Using Docker Networks:
Docker provides network functionality that allows you to create custom networks for your containers. By setting up a Docker network, you can create a logical grouping of containers and manage their connectivity. This way, you can access the containers within the same network easily from your host machine without having to specify individual IP addresses or port mappings.
By utilizing Docker networks, you can establish seamless communication between your host machine and the containers within the network, providing a more efficient and organized approach to accessing the Docker network.
In conclusion, understanding how to access a Docker network from your host machine is essential for effectively utilizing Docker's capabilities. Whether by utilizing container IP addresses, mapping container ports, or leveraging Docker networks, you can seamlessly interact with the containerized services and applications from your host machine, enhancing your development and deployment workflows.
Exploring Docker Network Port Exposure
This section delves into the topic of exposing ports in a Docker network. Expanding on the concepts discussed earlier, we will explore how to configure and manage port exposure within the context of a Docker network environment. By exposing ports, we enable communication between Docker containers and external applications or services. We will discuss the essential considerations and steps involved in setting up port exposure, ensuring seamless connectivity and efficient data transfer across the network.
| Topic | Description |
|---|---|
| Port Exposure Overview | This subsection provides an overview of port exposure in a Docker network, explaining its significance and the benefits it offers. It highlights the role of ports in facilitating network communication and outlines the key factors to consider when configuring port exposure. |
| Configuring Port Exposure | In this part, we dive into the practical aspects of configuring port exposure in a Docker network. We explore the different methods and techniques available, including the use of Docker commands and configuration files, to enable seamless port exposure. Step-by-step instructions and examples are provided to guide users through the process. |
| Managing Port Exposure | Once port exposure is set up, it becomes essential to manage and monitor the exposed ports effectively. This subsection covers various best practices and tools for managing port exposure, such as security considerations, troubleshooting common issues, and ensuring optimal performance and reliability. |
| Advanced Port Exposure Techniques | For those seeking to expand their knowledge and explore advanced port exposure techniques, this part delves into more complex concepts, including port mapping, port forwarding, and using load balancers. It offers insights into how these techniques can enhance scalability, improve network performance, and maximize the flexibility of Docker networks. |
Connecting Docker Networks
In the context of configuring a Docker environment on a Windows system, one essential aspect is establishing connections between different Docker networks. This section will outline the steps and considerations for connecting Docker networks efficiently and securely, enhancing the overall functionality and flexibility of your Docker setup.
Firstly, it is important to understand the concept of network connectivity in the Docker ecosystem. Instead of relying on physical network connections, Docker networks provide a virtualized networking environment for containers to communicate with each other. By connecting Docker networks, you can maximize the seamless interaction between various containers, enabling them to share resources, exchange data, and collaborate effectively.
When connecting Docker networks, several options are available depending on your specific requirements and preferences. One common approach is to utilize Docker's built-in networking features, such as creating custom bridge networks or leveraging the default bridge network. These methods allow containers within the same network or across different networks to communicate effortlessly, fostering a highly interconnected Docker environment.
Alternatively, you may consider using overlay networks to connect Docker networks. Overlay networks enable container communication across multiple Docker hosts, making it possible to create distributed applications spanning different physical or virtual machines. This approach offers enhanced scalability and flexibility, particularly for complex scenarios where containers need to communicate seamlessly across various hosts and networks.
Furthermore, it is essential to address security concerns when connecting Docker networks. Implementing proper security measures, such as configuring network firewalls, applying access controls, and employing encrypted communication protocols, is crucial to protect sensitive data and ensure a secure network environment. By proactively considering security aspects, you can prevent unauthorized access and mitigate potential risks in your Docker network setup.
In summary, establishing connections between Docker networks is a fundamental aspect of setting up a robust and functional Docker environment. By leveraging Docker's networking features and considering security measures, you can create highly connected and secure Docker networks, enabling seamless communication and collaboration between containers.
Troubleshooting Connectivity Issues in Docker on a Windows OS

In this section, we will explore the common challenges that users may encounter while setting up and working with Docker networks on a Windows operating system. We will discuss various troubleshooting methods and solutions to overcome connectivity issues, fostering a smooth and functional Docker environment.
- Unable to Establish Network Connections
- Network Misconfiguration
- Network Security and Firewall Settings
- DNS Resolution and Name Resolution
- Performance and Network Latency
- Container Networking Conflicts
One prevalent issue faced by Docker users is the inability to establish network connections between containers or between containers and the outside world. We will delve into the root causes for this problem and explore troubleshooting steps to diagnose and resolve network connectivity issues.
A misconfigured Docker network can lead to various network problems, including container isolation, routing issues, and inability to access the internet. We will examine common misconfigurations and provide step-by-step solutions to reconfigure network settings properly.
Docker networks often interact with the host's security and firewall settings, which can cause network connectivity problems. We will guide you through troubleshooting network security-related issues, including adjusting firewall rules and ensuring network ports are open.
Difficulty in resolving DNS and name resolution within Docker networks can hinder connectivity. We will outline techniques to troubleshoot DNS resolution problems, such as configuring custom DNS servers and ensuring accurate name resolution.
Slow network performance or high latency within Docker networks can affect application performance. We will explore techniques to diagnose and mitigate network latency issues, including optimizing network settings and monitoring network performance metrics.
When multiple containers rely on the same network resources, conflicts can arise, resulting in network connectivity problems. We will provide insights into troubleshooting container networking conflicts and suggest best practices to prevent conflicts from occurring.
By addressing these common Docker network issues and following the troubleshooting techniques outlined in this section, users operating Docker on Windows will be equipped to resolve network-related problems effectively and optimize their Docker network setup for enhanced performance and connectivity.
Best Practices for Networking with Docker on the Microsoft Platform
When it comes to setting up a reliable and efficient network for your Docker containers on the Microsoft platform, there are several best practices to consider. In this section, we will explore key strategies and recommendations for optimizing your networking setup, ensuring seamless communication between containers, and maximizing overall performance.
- Choose the Right Network Driver
- Segmentation and Isolation
- Implement Network Load Balancing
- Secure Network Communication
- Monitoring and Troubleshooting
One important aspect of Docker networking in the Microsoft ecosystem is selecting the appropriate network driver. Different network drivers provide varying levels of performance, security, and functionality. Depending on your specific requirements, you can choose from drivers such as transparent, overlay, or MacVLAN, each with its own strengths and weaknesses.
In order to maintain a secure and well-organized network environment, it is crucial to separate and isolate containers based on their functionality. Utilizing network segmentation techniques, such as assigning different subnets or using VLANs, allows you to control traffic flow and access permissions effectively. This ensures that containers sharing the same physical or virtual infrastructure do not interfere with each other or become a vulnerability.
When running multiple containers or services within a network, it is essential to distribute incoming traffic evenly across these instances. Network load balancing helps optimize resource utilization and prevents overloading individual containers. You can achieve this by employing load balancer services, such as the Windows Server Network Load Balancing (NLB) feature or utilizing Docker Swarm mode to automatically load balance across multiple hosts.
To protect sensitive data and ensure secure communication between containers, it is imperative to implement proper encryption protocols. Utilizing Transport Layer Security (TLS) certificates or virtual private networks (VPNs) helps encrypt traffic and authenticate endpoints, mitigating the risk of data breaches or unauthorized access.
Monitoring and troubleshooting are vital aspects of maintaining a healthy Docker network. Implementing robust monitoring tools enables you to track network performance, identify bottlenecks, and proactively address any issues. Furthermore, utilizing network troubleshooting utilities, such as Docker logs, network packet capture tools, or container inspection commands, facilitates the swift resolution of potential connectivity or configuration problems.
By following these best practices, you can optimize your Docker network setup on the Microsoft platform, ensuring seamless communication, enhanced security, and improved overall performance for your containers and services.
[MOVIES] [/MOVIES] [/MOVIES_ENABLED]FAQ
What is Docker and why is it used?
Docker is a platform that allows developers to automate the deployment of applications inside software containers. It provides an efficient and consistent method to package, distribute, and run applications across different environments.
Why should I use Docker on Windows?
Docker on Windows allows developers to create, test, and deploy applications quickly and efficiently in a controlled environment. It enables the seamless transfer of applications across different machines and eliminates compatibility issues.
What is a Docker network and why is it important?
A Docker network is a virtual network that is created to connect Docker containers. It allows containers to communicate with each other, share resources, and access external networks securely. It is important for building complex applications that require multiple containers to work together.
How can I set up a Docker network on Windows?
To set up a Docker network on Windows, you can use Docker's built-in networking features. You can create a network using the `docker network create` command, specify the driver type, and connect containers to the network using the `--network` flag. Detailed steps can be found in the official Docker documentation.
What are the different types of Docker network drivers available in Windows?
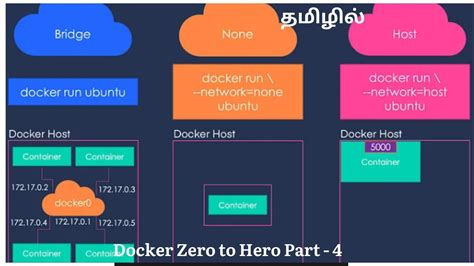
There are several Docker network drivers available in Windows, including bridge, overlay, host, and none. The bridge network allows containers to communicate with each other on the same host, the overlay network enables communication between containers running on different hosts, the host network connects containers directly to the host's network, and the none network disables networking for the container.
What is Docker?
Docker is an open-source platform that allows you to automate the deployment and management of applications in isolated containers, making it easier to package, distribute, and run applications.
Why should I set up a Docker network on Windows?
Setting up a Docker network on Windows allows you to create a virtual network that enables communication between containers, making it possible to deploy and run multi-container applications in a distributed environment.




