In the fast-paced world of technology, where innovation is rapidly reshaping industries, the need for seamless connectivity among various systems and applications has become more crucial than ever before. Companies across different sectors are leveraging cutting-edge solutions to enhance their network infrastructure and optimize their operations. One such technology that has gained significant attention in recent years is the network overlay for containerization.
Imagine a network where containers can seamlessly communicate with each other, irrespective of their physical locations or underlying network architecture. This is precisely what the Windows Docker Network Overlay aims to achieve - an efficient and reliable solution that enables containers to seamlessly connect and communicate. By abstracting the underlying networking layer, this innovative approach eliminates the complexities associated with traditional network infrastructure and empowers containers to function as independent entities.
With the Windows Docker Network Overlay, containers can establish secure and scalable network connections, allowing them to effortlessly share data and resources. This technology utilizes advanced algorithms and protocols to create a virtual network overlay, effectively providing containers with their own isolated network environments. By leveraging this network overlay, containers can operate in a distributed and decentralized manner, enhancing scalability, flexibility, and fault tolerance.
Understanding Network Overlays in Windows Docker
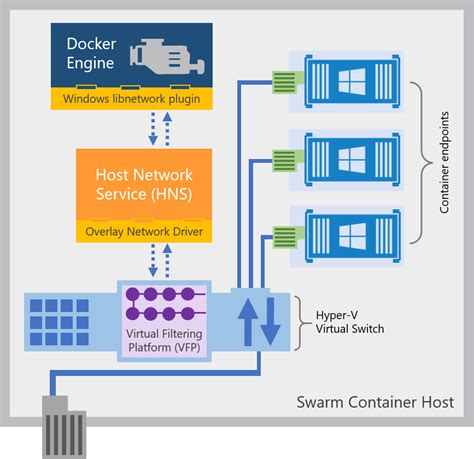
In this section, we will explore the concept of network overlays in the context of Windows Docker. By leveraging the power of overlays, containers can seamlessly communicate and collaborate within a network infrastructure, without being restricted by the limitations of traditional networking methods.
One of the key advantages of network overlays is their ability to create a virtual network that spans across multiple hosts. This means that containers running on different machines can be connected as if they were on the same network, allowing for efficient and scalable communication. Instead of relying on physical connections or complex configurations, network overlays provide a flexible and dynamic solution for container networking.
Within a network overlay, containers are assigned unique IP addresses, allowing them to easily identify and communicate with each other. This enables the creation of distributed applications that can seamlessly span across multiple containers and hosts, facilitating efficient load balancing and fault tolerance.
Network overlays also provide isolation and security for containers by encapsulating their traffic within an overlay network. This ensures that communication between containers remains private and protected, even in complex and dynamic environments.
By understanding the concepts and benefits of network overlays in Windows Docker, developers and administrators can effectively design and implement containerized applications that leverage the full potential of scalable and flexible networks.
Benefits of Utilizing Network Overlays in Container Environments
Modern containerized architectures require robust networking solutions that can effectively connect and manage communication between containers across various hosts. To overcome the limitations of traditional networking approaches, the implementation of network overlays offers several distinct advantages.
One major benefit of using network overlays in container environments is enhanced scalability and flexibility. By decoupling the container network from the underlying physical network infrastructure, overlays allow for the creation of virtual networks that can span multiple hosts and data centers. This enables seamless communication and eliminates the need for complex physical network configurations.
Another advantage is increased security and isolation. Network overlays provide a layer of abstraction that isolates containerized applications from the underlying physical network. This isolation helps prevent unauthorized access and reduces the risk of cyber threats spreading across the entire network. Additionally, network overlays can enable more granular control over network traffic, allowing for secure and fine-grained access control policies.
Network overlays also contribute to improved simplicity and ease of management. By abstracting networking complexities, overlays simplify the deployment and maintenance of containerized applications. They offer a centralized and programmable approach to network management, allowing administrators to dynamically configure and manage networks without manual intervention. This greatly reduces the administrative burden and enables faster deployments and updates.
Furthermore, network overlays facilitate seamless cross-platform and cross-cloud communication. They provide a consistent networking environment regardless of the hosting infrastructure, making it easier to migrate containers between different environments. This portability enables hybrid and multi-cloud deployments, allowing organizations to leverage the benefits of different cloud providers without compromising network connectivity.
In conclusion, the utilization of network overlays in container environments provides numerous benefits, including enhanced scalability, increased security, improved simplicity, and seamless cross-platform communication. By leveraging the power of overlays, organizations can optimize their containerized architectures and achieve a highly efficient and agile network infrastructure.
Step-by-Step Guide to Establishing a Seamless Network Connection in a Windows Docker Environment
In this section, we will provide you with a comprehensive step-by-step guide on how to configure and set up a network connection overlay for your Windows Docker environment. By following these instructions, you will be able to seamlessly integrate your containers into a cohesive network infrastructure.
Step 1: Preparing the Environment
Before setting up the network overlay, it is crucial to ensure that your Windows Docker environment is properly configured and ready for the integration. This involves verifying network connectivity, updating necessary software components, and installing any dependencies required for the overlay.
Step 2: Designing the Overlay Network
In this step, you will need to analyze your network requirements and design the overlay network accordingly. Consider factors such as scalability, security, and performance objectives. Determine the appropriate network topology and define the subnet ranges and gateway configuration for each container.
Step 3: Configuring the Network Overlay
Once the overlay network design is finalized, it's time to configure the overlay network on your Windows Docker environment. This involves creating virtual networks, assigning subnets to each network, and setting up network endpoints and gateway connections.
Step 4: Testing Connectivity
Now that the network overlay is configured, it's essential to validate the connectivity between containers within the overlay. Run test scenarios to ensure that containers can communicate seamlessly with each other and access resources outside the overlay network.
Step 5: Monitoring and Troubleshooting
After the network overlay is up and running, it is important to monitor the network performance and troubleshoot any issues that may arise. Utilize appropriate tools and techniques to monitor network traffic, identify bottlenecks, and diagnose connectivity problems.
Step 6: Scaling the Network Overlay
As your containerized environment grows, you may need to scale the network overlay to accommodate increased traffic and resource demands. In this step, you will learn how to add new nodes or expand existing ones within the overlay network without disrupting the overall connectivity.
Step 7: Ensuring Security
The final step in setting up the network overlay involves implementing security measures to protect your containers and data. Explore options such as network segmentation, access controls, and encryption techniques to safeguard your network infrastructure from potential threats.
By following this step-by-step guide, you will be able to establish a robust and seamlessly connected network infrastructure for your Windows Docker environment, enabling efficient communication and resource sharing among your containers.
Considerations for Optimizing Network Overlays with Windows-Based Docker Containers
In this section, we will explore a range of best practices to configure and optimize network overlays when using Windows-based Docker containers. By adhering to these guidelines, you can enhance the efficiency and reliability of your containerized applications, without compromising performance or security.
1. Mindful Subnet Allocation: While configuring network overlays, it is crucial to thoughtfully allocate subnets to avoid conflicts and ensure seamless communication between containers. Consider utilizing subnetting schemes that are scalable and align with your specific network requirements.
2. Efficient IP Address Management: Proper management of IP addresses is essential for maintaining network stability and preventing address pool exhaustion. Implement mechanisms for automatic IP assignment, such as DHCP, and regularly monitor and audit IP usage to detect and resolve any conflicts or inconsistencies.
3. Secure Network Segmentation: To bolster security within your containerized environment, it is advisable to segment your network overlays into distinct subnets or VLANs. This separation helps restrict access between different parts of your infrastructure and enables granular control over network traffic.
4. Redundancy and High Availability: Implement redundancy measures to ensure high availability and fault tolerance for your containers. Utilize load balancers, cluster managers, or container orchestrators that support network overlays to distribute the network load efficiently and provide seamless failover capabilities.
5. Quality of Service Optimization: Consider prioritizing network traffic within your overlays to provide a consistent level of service for critical applications or communication channels. By utilizing Quality of Service (QoS) mechanisms, you can allocate bandwidth and set latency requirements to guarantee optimal performance.
6. Logging and Monitoring: Establish comprehensive logging and monitoring practices to gain insights into network overlay behavior and troubleshoot potential issues proactively. Utilize network monitoring tools that provide visibility into network performance, traffic patterns, and security events.
7. Regular Updates and Patches: Stay vigilant regarding updates and patches for both your Windows-based Docker containers and the underlying network overlay technology. Ensuring that you are running the latest versions helps mitigate security risks and guarantees compatibility with newer features and improvements.
By following these best practices, you can optimize your network overlays within Windows Docker containers, creating a robust and efficient infrastructure for your containerized applications.
Security Considerations for Network Overlays in Windows Container Environments
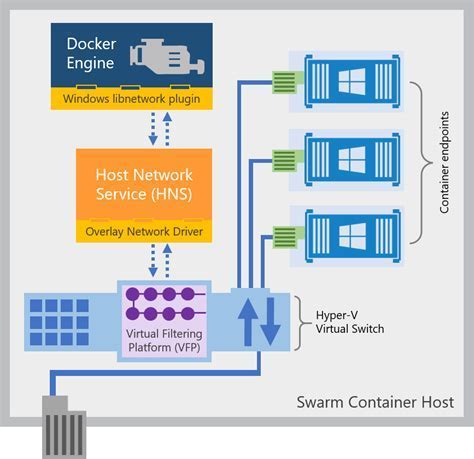
When deploying network overlays in Windows container environments, it is crucial to carefully consider the security implications that arise from this technology. By leveraging network overlays, organizations can create a seamless and scalable network infrastructure for their containers. However, it is important to assess and address potential security risks to protect sensitive data and ensure the integrity of the system.
| Consideration | Description |
|---|---|
| Isolation and Segmentation | One of the primary security concerns with network overlays is ensuring proper isolation and segmentation of containers. Misconfigurations or vulnerabilities in the overlay network can potentially expose sensitive data to unauthorized access. It is essential to implement strong security measures, such as network segmentation and access controls, to mitigate these risks. |
| Encryption | Encryption plays a crucial role in securing data transmission over network overlays. Implementing strong encryption protocols, such as TLS or IPsec, helps safeguard against eavesdropping and data tampering. By encrypting the traffic between containers, organizations can protect sensitive information from potential threats. |
| Authentication and Authorization | Proper authentication and authorization mechanisms are vital to control access to the container network overlay. Implementing strong user authentication protocols, such as multi-factor authentication, can prevent unauthorized individuals from gaining access to the network. Additionally, role-based access controls (RBAC) should be employed to restrict access privileges based on user roles and responsibilities. |
| Monitoring and Logging | Effective monitoring and logging practices are essential for detecting and responding to security incidents in a timely manner. Implementing robust monitoring tools and techniques allows organizations to identify any potential network overlay vulnerabilities or breaches. Additionally, maintaining comprehensive logs enables forensic analysis and facilitates incident response efforts. |
| Regular Updates and Patching | Keeping the network overlay infrastructure up to date with the latest security patches is critical. Regularly updating the underlying software components and applying security patches helps mitigate potential vulnerabilities that malicious actors could exploit. Organizations should have a well-defined patch management process in place to ensure timely updates. |
By considering these security aspects and implementing appropriate measures, organizations can build a secure and reliable network overlay infrastructure for their Windows containers. It is crucial to approach network overlays with a proactive mindset, continuously evaluating and improving security practices to stay ahead of potential threats.
Future Development and Enhancements for Next-Level Network Overlays
In this section, we will explore the exciting prospects and potential advancements in the realm of network overlays for the Windows container ecosystem. Building upon the foundation we have established, the future of network overlays holds immense opportunities for refinement and innovation, ultimately aiming to achieve enhanced networking capabilities and seamless container communication.
One area of future development lies in the optimization of network overlay performance. As containers continue to gain prominence in the world of application deployment, the demand for faster and more efficient networking solutions becomes evident. Efforts are underway to refine the underlying technologies and algorithms used to power network overlays, with a particular focus on reducing latency, improving scalability, and enhancing overall network performance.
Another avenue for enhancement is the introduction of advanced security measures within network overlays. As the container landscape evolves, it becomes crucial to address potential security vulnerabilities that may arise in container communication. Future developments aim to integrate robust encryption protocols, access control mechanisms, and identity management systems to ensure the secure and private exchange of data between containers across the network overlay.
Furthermore, efforts are being made to enhance the flexibility and extensibility of network overlays. As container environments become increasingly diverse and complex, the need for adaptive networking solutions becomes paramount. Future developments aim to provide more seamless integration with existing infrastructure, including compatibility with various network architectures and protocols, enabling greater interoperability and ease of deployment.
Lastly, scalability and management are essential aspects being considered for future enhancements. As containerized applications continue to scale and proliferate, the ability to efficiently manage and monitor the network overlay becomes critical. Future developments seek to introduce better tools and frameworks for administering network overlays, enabling seamless scaling, monitoring, and troubleshooting capabilities, thus ensuring a stable and resilient networking infrastructure for containers.
| Key Areas of Future Development: |
|---|
| Optimization of network overlay performance |
| Integration of advanced security measures |
| Enhanced flexibility and extensibility |
| Scalability and management improvements |
In conclusion, the future of Windows Docker network overlays holds immense potential for further development and enhancements. Through continuous innovation and optimization, we can expect to witness even more seamless, secure, and scalable networking capabilities for containers in the days to come.
FAQ
What is Windows Docker Network Overlay?
Windows Docker Network Overlay is a technology that allows for the creation of a seamless network infrastructure for containers running on the Windows operating system. It enables containers to communicate with each other across multiple hosts as if they were on the same network.
How does Windows Docker Network Overlay work?
Windows Docker Network Overlay works by creating an overlay network that sits on top of the host networks. This overlay network allows containers to be connected to different hosts and still communicate with each other as if they were on the same network. It uses the VXLAN protocol for encapsulating and delivering network traffic between containers.
What are the benefits of using Windows Docker Network Overlay?
The benefits of using Windows Docker Network Overlay include seamless communication between containers across multiple hosts, improved scalability by allowing containers to be distributed across different hosts, and increased flexibility in managing the network infrastructure for containerized applications.
Can Windows Docker Network Overlay be used with both Windows and Linux containers?
No, Windows Docker Network Overlay is specifically designed for Windows containers and cannot be used with Linux containers. However, there are similar technologies available for Linux containers, such as Docker Swarm and Kubernetes.
Are there any requirements for using Windows Docker Network Overlay?
Yes, there are some requirements for using Windows Docker Network Overlay. It requires the Windows Server 2016 or later operating system, Docker Engine installed and running on each host, and the overlay network driver enabled. Additionally, the hosts need to be connected to a network that supports multicast for the overlay network to function properly.
What is a Windows Docker Network Overlay?
A Windows Docker Network Overlay is a network infrastructure that allows for seamless communication between containers in a distributed container environment. It enables containers to communicate with each other regardless of the host they are running on.
How does a Windows Docker Network Overlay work?
A Windows Docker Network Overlay works by creating a virtual network that spans across multiple hosts. It uses overlay networking technology to connect containers by encapsulating the network traffic and routing it between hosts.




