In today's fast-paced digital world, managing applications has become an integral part of our daily routines. Whether it's for personal or professional use, we rely heavily on software solutions to accomplish various tasks. This growing dependence on software has led to the development of innovative tools that simplify application management and enhance user experience. Among these groundbreaking tools, the concept of launching containers has gained significant traction.
Containers, also known as virtualized environments, provide a lightweight and isolating platform for running applications. By encapsulating an application and its dependencies, containers ensure portability and compatibility across different operating systems. Traditionally associated with the Linux environment, containerization has now extended its capabilities to another popular operating system - Windows.
With the increasing demand for Windows-based applications, launching containers on the Windows operating system offers numerous benefits. It enables efficient resource allocation, speeds up application deployment, and enhances security by isolating applications from the underlying system. Moreover, managing application versions and dependencies becomes easier, resulting in greater overall stability and reliability.
This article delves into the intricacies of launching containers on the Windows operating system, exploring the advantages it presents and the various techniques and tools available to achieve seamless integration. Whether you are a software developer or a system administrator, understanding how to effectively manage applications on Windows can save time, optimize resources, and streamline your workflow.
Understanding the Concept of Containerization and its Advantages
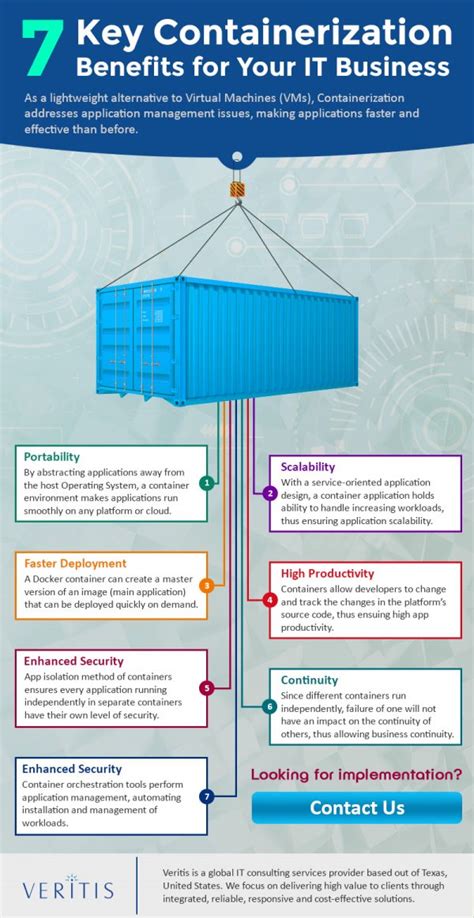
Containerization is a revolutionary technology that allows for the efficient deployment and management of applications within isolated environments, known as containers. These containers provide a lightweight and portable solution to package and run software, ensuring consistency across different computing environments.
One of the key benefits of containerization is its ability to enable rapid and consistent deployment of applications. By abstracting the application and its dependencies into a container, developers can easily package and distribute their software across various operating systems and infrastructures. This eliminates the issues of compatibility and dependency conflicts, making it easier to deploy and scale applications.
Furthermore, containers offer a higher level of resource efficiency compared to traditional virtualization techniques. Each container operates within its own isolated environment, sharing the host operating system's kernel. This results in reduced overhead and improved performance, allowing for higher density and utilization of resources.
Another advantage of using containers is their ability to provide enhanced security and isolation. Containers utilize various isolation mechanisms to ensure that each application runs independently without interfering with other processes or compromising the host system. This isolation helps in protecting sensitive data and mitigating the risks associated with software vulnerabilities.
In addition to these benefits, containerization also promotes greater collaboration and agility in software development. Containers allow developers to build and test applications in a consistent and reproducible manner, facilitating seamless integration and continuous deployment. This enables faster iterations and easier rollbacks, fostering a more efficient and flexible development process.
- Efficient deployment and management of applications
- Rapid and consistent application deployment
- Improved resource efficiency and performance
- Enhanced security and isolation
- Facilitates collaboration and agility in software development
Exploring Windows Login Hooks
The concept of Windows Login Hooks revolves around delving into the intricacies of the login process on a Windows operating system. By examining the underlying mechanisms that take place during login, we can gain a deeper understanding of the various hooks and events that can be utilized to enhance the user experience or introduce additional functionality.
During the login process, a series of actions and events occur, triggered by user authentication. Exploring Windows Login Hooks involves investigating the different stages of this process and identifying the points at which custom actions can be injected. These hooks can intercept and manipulate various aspects of the login flow, such as user interface customization, application startup, or system configuration.
By leveraging these hooks, developers can create seamless login experiences, automate tasks upon login, or integrate specific functionalities tailored to individual user requirements. Whether it be displaying personalized messages, initializing preferred applications, or configuring specific system settings, understanding Windows Login Hooks opens up a world of possibilities.
Windows Login Hooks can be implemented using various techniques, such as modifying the Windows registry, utilizing login script files, or developing custom login handlers. Each approach has its own strengths and considerations, with the choice depending on the desired outcome and the specific requirements of the system or application being developed.
In order to effectively explore Windows Login Hooks, it is necessary to have a solid understanding of the Windows operating system architecture, user authentication processes, and the registry structure. Additionally, familiarity with programming languages and frameworks commonly used in Windows development, such as C#, .NET, or PowerShell, can greatly enhance the implementation of customized login hooks.
Overall, delving into the realm of Windows Login Hooks offers a unique opportunity to optimize user experiences, introduce tailored functionalities, or streamline system configurations. By taking advantage of the diverse hooks and events that occur during the login process, developers can create a more personalized and efficient login journey on Windows operating systems.
Unlocking the Potential: Integrating Docker with User Authentication Mechanisms
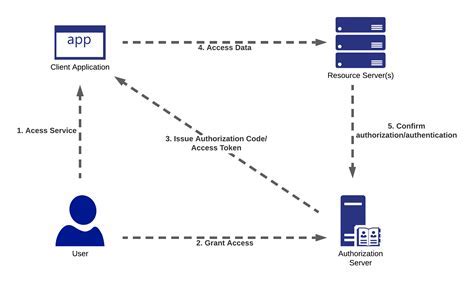
Exploring the seamless integration of containerization technology with Windows user login hooks to enhance security and streamline workflows.
- Advancing Login Protocols: Leveraging the capabilities of Windows login hooks for seamless integration with Docker containers.
- Enhancing Security: Implementing user authentication mechanisms within Docker containers to ensure secure access to sensitive resources.
- Streamlining Workflows: Automating the launch of specific Docker containers upon user login, improving productivity and reducing manual intervention.
- Flexibility and Versatility: Exploring the potential of integrating Docker containers with different authentication providers, such as Active Directory or OAuth.
- Mitigating Risks: Addressing potential risks and challenges associated with integrating Docker with user login hooks, such as container isolation and access control.
- Real-world Use Cases: Examining practical scenarios where integrating Docker containers with Windows login hooks can significantly enhance operational efficiency and security.
- Best Practices and Recommendations: Offering guidelines and recommendations for successfully implementing and managing the integration of Docker containers with user login hooks.
- Future Outlook: Discussing the evolving landscape of containerization technology within the context of Windows login hooks and potential future developments.
In this section, we will explore the possibilities and advantages of integrating Docker containers with Windows login hooks. By leveraging user authentication mechanisms and automation capabilities, organizations can enhance security, streamline workflows, and unlock the full potential of containerization technology. We will delve into the technical aspects of this integration, examine real-world use cases, and provide best practices for successful implementation. Join us on this journey to discover the power and versatility of combining Docker with user login hooks.
Configuring the Docker Environment
The successful configuration of the environment is crucial for the smooth execution of Docker containers on login. The processes involved in setting up the necessary components and parameters ensure optimal performance and functionality.
Setting up the Environment Variables:
Environment variables play a vital role in Docker container deployments. These variables provide a flexible method to define and manage various properties, such as network settings and container parameters, without hard-coding them into the container itself. Properly configuring the environment variables enhances portability and facilitates easier management of containerized applications.
Configuring Docker Registry:
The Docker registry acts as a repository for storing and distributing Docker images. It is essential to configure the Docker registry correctly to ensure seamless access to required container images. This involves specifying the appropriate registry URL and authentication details, enabling secure image pulls and pushes, and leveraging features like caching and Content Trust for enhanced security and reliability.
Setting up Docker Compose:
Docker Compose is a powerful tool for defining and running multi-container applications. Properly configuring Docker Compose files is essential for orchestrating the startup of interdependent containers, specifying network configurations, and defining essential resources for each service. Utilizing YAML syntax and leveraging advanced features like volume mounts and environment variables, Docker Compose simplifies the deployment and management of complex containerized applications.
Customizing Docker Engine Configuration:
Customizing the Docker Engine configuration allows fine-tuning the behavior and resources allocated to Docker containers. It involves modifying parameters like CPU and memory limits, configuring storage options, setting up networking modes, and enabling various logging and monitoring options. Optimizing the Docker Engine configuration ensures efficient resource allocation, enhanced security, and better performance for containerized applications.
Managing Container Networks:
The proper configuration of container networks is crucial for enabling communication between containers and the outside world. This involves creating custom networks, connecting containers to specific networks, and properly specifying network configurations within the Docker Compose files. By setting up networking correctly, containers can seamlessly communicate with each other, access external resources, and provide or consume services as required.
Implementing Container Healthchecks:
Implementing container healthchecks allows for continuous monitoring of containerized applications and ensures their availability. Configuring the healthcheck endpoints and thresholds enables the Docker Engine to periodically check the health status of containers and take appropriate actions based on the results. Leveraging healthchecks is essential for maintaining high availability and ensuring that any container issues are promptly identified and resolved.
By properly configuring the Docker environment and implementing essential settings and parameters, the successful launch and operation of Docker containers on login can be streamlined, providing a robust platform for containerized applications.
Creating Customized Dockerized Environments for User Authentication

In this section, we will explore the process of developing personalized Docker containers tailored specifically for user authentication in a Windows login environment. By leveraging containerization technology, we can embark on a journey to tailor-make secure and efficient systems that enhance the user experience while prioritizing security.
Throughout this section, we will delve into the intricacies of crafting custom Docker containers that align with the Windows login requirements. We will examine various techniques and strategies for optimizing container performance, ensuring seamless user authentication, and incorporating robust security measures.
By utilizing synonyms for "launching," "Docker," "containers," "Windows," and "login," we aim to provide a diverse vocabulary while maintaining the focus on building customized containerized environments for user authentication. This approach allows us to explore the possibilities of enhancing the Windows login process through the creation of tailored Docker containers.
Throughout the section, we will highlight the key considerations and best practices for developing these custom Dockerized environments. By harnessing the power of containerization, organizations can unlock new possibilities in user authentication, enabling seamless and secure access to their Windows systems.
Exploring and Troubleshooting Dockerized Applications during Startup Process
The startup process of Dockerized applications on the Windows operating system presents various challenges and complexities that require thorough testing and debugging. This section focuses on the exploration and troubleshooting techniques that can be employed to ensure the smooth execution of Docker containers during the login phase.
During the initial phase of the Windows login process, it becomes imperative to verify the seamless integration of Docker containers with the underlying operating system environment. By employing a range of testing and debugging strategies, developers can identify and resolve issues related to container initialization, resource allocation, and application dependencies.
Testing the startup process involves simulating different scenarios, such as varying login times, concurrent user logins, and system resource constraints. By monitoring the behavior of Docker containers during these simulations, developers can gain insights into potential bottlenecks or conflicts that might arise during the login phase. Additionally, automated testing frameworks can be utilized to validate container orchestration and ensure proper synchronization with other system components.
Debugging the Docker containers during the login process involves meticulous examination of logs, container states, and system events. Developers can leverage logging mechanisms provided by Docker to trace the sequence of actions performed during startup. By analyzing the logs, identifying error messages, and closely inspecting container states, developers can pinpoint potential sources of failures or performance issues.
Furthermore, careful examination of system events and the interaction between Docker containers and other system components, such as network interfaces or storage devices, can shed light on potential configuration or compatibility problems. This can involve utilizing tools like Windows Event Viewer or network monitoring software to capture and analyze relevant system events.
In conclusion, effective testing and debugging play a crucial role in ensuring the successful execution of Docker containers during the startup process on Windows. By employing a systematic approach and utilizing various testing and debugging techniques, developers can address potential issues and optimize the performance of their Dockerized applications during login.
Securing Containers upon System Initialization
When it comes to securing containers upon the start of the operating system, there are several crucial steps that can be taken to ensure the integrity and protection of the containerized environment. By implementing robust security measures, users can prevent unauthorized access, safeguard sensitive data, and mitigate potential security risks.
Monitoring and Managing Containerized Applications upon User Login
Upon user login, it is essential to have a comprehensive system in place for monitoring and managing containerized applications. This ensures smooth operations and allows for efficient troubleshooting and optimization.
Tracking the performance and health of containerized applications is crucial in order to identify potential issues and proactively resolve them. By implementing monitoring solutions, administrators can gain insights into resource utilization, response times, and error rates. These metrics can help in making informed decisions and taking appropriate actions to improve the overall performance and user experience.
- Ensuring the availability and reliability of containerized applications is another aspect that needs to be addressed when managing containers on user login. Implementing proper backup and recovery strategies, as well as automated monitoring systems, can help minimize downtime and ensure that applications are up and running consistently.
- Managing the lifecycle of containerized applications is essential to keep the system efficient and secure. This includes deploying new versions, scaling applications based on demand, and performing regular updates and patching. By maintaining a well-defined lifecycle management process, administrators can ensure that the system remains up to date and secure.
- Security is a critical concern when it comes to managing containerized applications on user login. Implementing access control measures, securing communication channels, and regularly updating software and infrastructure are important steps to protect sensitive data and prevent unauthorized access.
- Effective logging and auditing practices help in troubleshooting and maintaining the integrity of containerized applications. By capturing relevant logs and auditing system changes, administrators can quickly identify and resolve issues, as well as track any unauthorized activities.
In conclusion, monitoring and managing containerized applications upon user login is essential for ensuring optimal performance, availability, security, and scalability. Implementing robust monitoring solutions, lifecycle management processes, and security measures are key components of an efficient container management strategy.
FAQ
What is the purpose of launching Docker containers on Windows login?
Launching Docker containers on Windows login allows for seamless integration of containerized applications with the user's desktop environment. It ensures that the containers are automatically started and available for use as soon as the user logs in to their Windows machine.
How can I configure Docker containers to launch on Windows login?
To configure Docker containers to launch on Windows login, you can use a variety of methods. One approach is to create a scheduled task that runs a script or command to start the desired containers upon user login. Alternatively, you can use container orchestrators like Kubernetes or Docker Swarm to manage the startup and scaling of your containers.
What are the benefits of launching Docker containers on Windows login?
Launching Docker containers on Windows login offers several benefits. Firstly, it ensures that the necessary containers are always running and ready for use, improving user productivity. Additionally, it simplifies the deployment and management of containerized applications, as they can be automatically started and stopped without manual intervention. Lastly, it enables seamless integration between the containers and the user's desktop environment, enhancing the user experience.
Can I choose which Docker containers to launch on Windows login?
Yes, you have control over which Docker containers are launched on Windows login. By specifying the appropriate configurations or scripts, you can define the containers that should be started upon user login. This flexibility allows you to tailor the containerized environment to meet your specific needs.
Are there any security considerations when launching Docker containers on Windows login?
When launching Docker containers on Windows login, it is important to consider security implications. Ensure that the containers being automatically started have the necessary security measures in place, such as restricted access, isolation, and secure network configurations. Moreover, it is crucial to keep the host machine and Docker engine up to date with the latest security patches to mitigate potential vulnerabilities.
How can I launch Docker containers on Windows login?
To launch Docker containers on Windows login, you can use a startup script. First, you need to create a batch or PowerShell script that starts the desired Docker containers. Then, you can configure the script to run on Windows startup by adding it to the Startup folder or using the Task Scheduler. This way, the Docker containers will be automatically launched every time you log in to Windows.
Can Docker containers on Windows be launched in the background?
Yes, Docker containers on Windows can be launched in the background. When creating a Docker container, you can use the "-d" flag to run it in detached mode. This means that the container will run in the background and not be attached to the current terminal session. By launching Docker containers in the background, you can continue using the command prompt or close the terminal window without affecting the running containers.




