Welcome to a detailed exploration of the intricate process of installing and configuring the Nmap tool on the Linux operating system to enhance your network scanning capabilities. By utilizing this step-by-step guide, you will gain insights into the seamless integration of Nmap into your Linux infrastructure, thus empowering you with cutting-edge network exploration techniques.
Built on a foundation of innovation and robustness, Nmap presents itself as a versatile and indispensable tool for network administrators, security professionals, and enthusiasts alike. With its myriad of features and flexibility, Nmap provides an extensive range of network scanning techniques, equipping you with invaluable insights into network architectures, vulnerabilities, and potential security threats.
Throughout this tutorial, you will embark on a journey filled with comprehensive explanations, practical code snippets, and invaluable tips to ensure a seamless installation and configuration process. From mastering the installation prerequisites to harnessing the power of command-line options, you will develop the skills needed to unleash the full potential of Nmap in all your network scanning endeavors.
Prepare to immerse yourself in the world of network scanning as we delve into the intricacies of installing and configuring Nmap on Linux, enabling you to become a proficient network explorer and defender. So, let us embark on this exciting expedition to elevate your network scanning capabilities and better protect your digital assets.
Step 1: Preparing the Linux System for Nmap Installation
Before you can install and configure Nmap on your Linux system for network scanning, it's crucial to ensure that your Linux system meets the necessary requirements and is properly set up. This step will guide you through the necessary preparations to successfully install Nmap.
1. Check System Requirements:
Start by verifying that your Linux system meets the minimum hardware and software requirements for Nmap. Ensure that you have a compatible operating system version installed and that your system has sufficient memory and CPU resources.
2. Update Your System:
Before proceeding with Nmap installation, it's recommended to update your Linux system to ensure you have the latest software packages and security patches. Use the appropriate package manager command to update your system, such as 'apt-get update' for Debian-based systems or 'yum update' for Red Hat-based systems.
3. Install Dependencies:
Nmap has certain dependencies that need to be installed on your Linux system for it to function properly. Identify these dependencies based on the documentation or official Nmap website, and use the package manager to install them if they are not already present.
4. Create a Non-Privileged User:
For security purposes, it is recommended to create a dedicated non-privileged user to run Nmap. This user will have limited privileges, reducing the potential impact of any vulnerabilities or misconfigurations. Use the appropriate command to create a new user with restricted permissions.
5. Configure Firewall Rules:
If you have a firewall installed on your Linux system, ensure that the necessary ports are open to allow Nmap scanning. Review the documentation or consult the firewall's configuration guide to configure the firewall rules accordingly.
By following these preparatory steps, your Linux system will be ready for the installation of Nmap, enabling you to proceed with the network scanning tasks effectively.
Checking System Requirements and Dependencies
Before proceeding with the installation and configuration of Nmap on your Linux system for network scanning, it is important to ensure that your system meets the necessary requirements and has the required dependencies installed.
Start by checking if your Linux system meets the minimum hardware requirements for running Nmap effectively. You should have a capable processor, sufficient RAM, and available disk space to accommodate the tool's operation and the results it generates.
In addition to hardware, Nmap also relies on certain software dependencies that must be present on your Linux system. These dependencies provide the necessary libraries and support for Nmap to function properly. It is essential to verify if the required dependencies are already installed or if you need to install them before proceeding.
While the exact dependencies may vary depending on your specific Linux distribution and version, some common dependencies include libpcap, OpenSSL, zlib, and libgtk2.0. You can use your package manager to check the availability and version of these dependencies on your system.
To ensure a smooth installation and configuration process, it is advisable to update your Linux system to the latest available version. This helps ensure compatibility with the latest versions of Nmap and its dependencies, as well as providing potential security enhancements and bug fixes.
Once you have confirmed that your system meets the necessary requirements and that the required dependencies are installed, you can proceed with the installation and configuration steps outlined in the rest of the guide.
Step 2: Obtaining and Installing Nmap
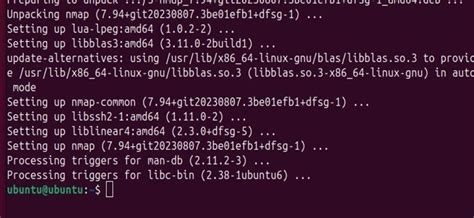
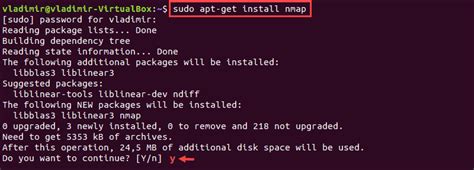
Once you have familiarized yourself with the necessary prerequisites for network scanning using Nmap, the next step is to download and install the Nmap tool on your Linux system. This section will guide you through the process of obtaining and installing Nmap, allowing you to effectively perform network scans.
Here are the steps to follow:
- Start by visiting the official Nmap website or the reliable software repository for your Linux distribution.
- Locate the download section or package manager for your Linux distribution.
- Choose the appropriate version of Nmap that is compatible with your Linux system.
- Click on the download link or use the package manager command to initiate the download process.
- Once the download is complete, navigate to the location where the Nmap package is saved.
- Extract the downloaded package using the appropriate command or graphical interface.
- Open a terminal or command prompt within the extracted Nmap package directory.
- Run the installation command, which may vary depending on your Linux distribution (refer to the documentation for specific instructions).
- Follow the prompts and provide any necessary permissions or passwords to complete the installation process.
- After the installation is finished, verify that Nmap has been successfully installed by running the command "
nmap --version" in the terminal.
Once you have successfully obtained and installed Nmap on your Linux system, you will be ready to move on to the next step of configuring it for network scanning.
Obtaining the Latest Version of Nmap
In this section, we will explore the process of acquiring the most up-to-date release of Nmap, a powerful network scanning tool for Linux. By obtaining the latest version, you can take advantage of the newest features, improvements, and security enhancements provided by the developers.
Ensuring that you have the latest version of Nmap installed is essential for maintaining the efficacy and reliability of your network scanning activities. Regular updates help to keep pace with evolving networking technologies and address any vulnerabilities that may be present in older versions.
To obtain the latest version of Nmap, you can visit the official website of the Nmap project or explore reputable software repositories specifically designed for Linux distributions. The official website offers the most recent releases, as well as additional resources such as documentation, release notes, and user forums for community support.
If you prefer to utilize the software repositories provided by your Linux distribution, you can use package management tools like apt or yum to search for and install the latest version of Nmap. These repositories ensure that the software you obtain is compatible with your specific Linux distribution and has been tested for stability.
Before installing the latest version of Nmap, it is recommended to verify the authenticity and integrity of the downloaded package. This can be accomplished by checking the cryptographic signatures and hashes provided by the developers. These security measures ensure that the software has not been tampered with or corrupted during the download process.
In conclusion, obtaining the latest version of Nmap is crucial for staying up-to-date with the latest network scanning capabilities and security enhancements. Whether you choose to download it from the official website or utilize the software repositories provided by your Linux distribution, make sure to verify the authenticity of the package before installation.
Step 3: Setting Up Nmap for Network Exploration

In this section, we will delve into the process of configuring Nmap, putting all the necessary pieces together to enable effective network scanning. By fine-tuning various parameters and options, you will be able to customize Nmap to suit your specific scanning requirements while ensuring optimal performance.
First and foremost, it is crucial to comprehend the importance of target specification in Nmap. We will explore different ways to define targets, such as specifying individual IP addresses, using CIDR notation for a range of IPs, and even reading targets from a file. Understanding these methods will equip you with the flexibility to focus your scanning efforts on specific subsets of your network.
Additionally, we will discuss the significance of Nmap scripting engine (NSE) and highlight how it can dramatically enhance your scanning capabilities. The NSE allows you to execute pre-written scripts or even create custom scripts to perform specific network reconnaissance tasks, providing valuable insights into vulnerabilities, open ports, and various other aspects of your network.
Furthermore, we will guide you through the process of fine-tuning scan techniques in Nmap. By familiarizing yourself with different scan types, including TCP, UDP, Stealth, and others, you will gain a deeper understanding of how Nmap approaches network scanning. We will also delve into advanced scanning techniques, such as timing options, parallelization, and decoy scanning, allowing you to tailor your scans for optimal efficiency and stealth.
To ensure a smooth scanning experience, we will address various common errors and troubleshooting techniques. We will cover topics such as handling firewalls and bypassing filters, dealing with false positives and negatives, and optimizing performance when scanning large networks or limited resources. Understanding these troubleshooting strategies will empower you to overcome potential obstacles and extract accurate and reliable information from your network scans.
In conclusion, this section will provide you with a comprehensive understanding of the configuration options available in Nmap, enabling you to fine-tune the tool to meet your specific network scanning needs. By exploring target specification methods, harnessing the power of NSE, mastering different scan techniques, and learning valuable troubleshooting techniques, you will gain the necessary expertise to conduct effective network exploration and gather crucial information about the security posture and vulnerabilities present in your network.
Understanding Nmap Configuration Files
In this section, we will explore the importance of Nmap configuration files in the context of network scanning. Configuration files play a crucial role in customizing the behavior and settings of Nmap to meet specific scanning requirements.
By delving into the structure and format of Nmap configuration files, users gain a deeper understanding of the various options and parameters available for fine-tuning their network scanning processes. These files provide a centralized location for managing Nmap preferences, allowing users to easily modify and save their preferred settings for future use.
- Default Settings: Learn about the default values and settings that Nmap uses when there is no specific configuration file provided. Understanding the defaults helps users grasp the baseline behavior of Nmap and make informed decisions when customizing the configuration.
- Structure and Syntax: Explore the structure and syntax of Nmap configuration files, including the different sections and options available. Understand how to navigate and modify the various settings to suit specific scanning objectives.
- Common Configuration Options: Gain knowledge of the most commonly used configuration options and their respective effects on Nmap's scanning behavior. This includes options for scan types, scan targets, timing and performance, output formats, and more.
- Creating Custom Configurations: Learn how to create custom configuration files tailored to specific network environments or scanning requirements. Understand the process of selecting and combining appropriate options to optimize the scanning process for different scenarios.
- Best Practices: Discover important best practices and considerations when working with Nmap configuration files. Understand how to avoid common pitfalls and ensure the efficiency and accuracy of network scanning results.
By developing a comprehensive understanding of Nmap configuration files, users can unleash the full potential of this powerful network scanning tool and enhance their ability to gather valuable insights about their network infrastructure.
Step 4: Essential Nmap Commands and Scanning Techniques
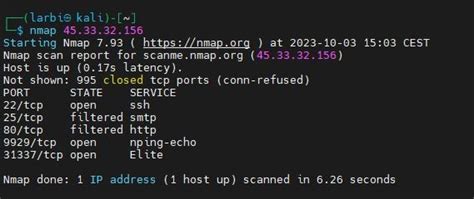
In this section, we will explore a set of fundamental Nmap commands and various scanning techniques to help you effectively analyze and gather vital information about the target network. By utilizing a range of tactics, you'll be equipped with the knowledge needed to understand the network's vulnerabilities and potential security risks.
1. Reconnaissance Scans: Get started by performing basic reconnaissance scans to identify open ports, discover live hosts, and determine the operating system running on the target machines. These scans provide a foundation for further analysis and evaluation.
2. Port Scanning Techniques: Learn about different port scanning techniques, such as TCP connect scanning, SYN scanning, and UDP scanning. Understand their advantages, disadvantages, and when to use each technique for a comprehensive evaluation of the target network's security posture.
3. Service and Version Detection: Dive into the world of service and version detection to gain insight into the software and services running on the target hosts. Learn how Nmap can interrogate open ports to extract valuable information about the applications and their versions, enhancing your understanding of potential vulnerabilities.
4. OS Fingerprinting: Discover the art of OS fingerprinting and its significance in determining the operating system being used on target hosts. By analyzing various network attributes and responses, Nmap can provide valuable insights into the technology stack, aiding in identifying potential security weaknesses.
5. Advanced Scan Techniques: Explore advanced scanning techniques, including timing options, firewall evasion, and fragmentation, to overcome obstacles and effectively scan networks that are protected or heavily fortified. These techniques will help you bypass security mechanisms and gather critical information.
By mastering these essential Nmap commands and scanning techniques, you'll be equipped with the knowledge and skills necessary to conduct thorough network scans, identify potential vulnerabilities, and enhance the overall security of your environment.
Learning Nmap Syntax and Usage
In this section, we will explore the fundamentals of Nmap, focusing on its syntax and how to effectively utilize its features for network scanning tasks. Understanding the syntax and usage of Nmap is vital for conducting accurate and comprehensive network scans, identifying vulnerabilities, and ensuring network security.
First, we will delve into the various command-line options that Nmap offers. These options provide flexibility and control over the scanning process, allowing you to specify target hosts, scan types, and various scan parameters. Familiarizing yourself with the available options will enable you to tailor your scans to meet specific requirements and maximize the efficiency of your network reconnaissance.
Next, we will examine the different scan techniques that Nmap supports. Whether you need to perform a stealthy, unobtrusive scan or an aggressive and comprehensive scan, Nmap offers a range of scan types to suit your needs. Understanding the purpose and characteristics of each scan technique is essential for selecting the right approach and achieving desired results.
Furthermore, we will explore Nmap's scripting engine and the extensive library of NSE scripts. These scripts provide additional functionality and automation capabilities, allowing you to perform tasks beyond basic network scanning. Learning how to utilize the NSE scripts effectively will empower you to automate repetitive tasks, gather detailed information, and even exploit vulnerabilities within the scanned network.
Last but not least, we will discuss best practices and tips for efficient and effective network scanning using Nmap. From optimizing scan configurations to understanding scan output and interpreting results, these guidelines will help you make the most of Nmap's capabilities while minimizing false positives and enhancing overall scan accuracy.
By the end of this section, you will have a solid understanding of Nmap's syntax and usage, enabling you to confidently navigate through its extensive features and unleash the full potential of this powerful network scanning tool.
How to Install Nmap on Ubuntu and Run Basic Scans
How to Install Nmap on Ubuntu and Run Basic Scans 作成者: Enkripsan 2,757 回視聴 1 年前 3 分 45 秒
FAQ
What is Nmap and why would I want to install it on Linux?
Nmap is a powerful network scanning tool that allows you to probe computer networks to find out what devices are running on them, what services those devices are offering, and what operating systems they are running. Installing Nmap on Linux can greatly enhance your ability to discover and manage devices on your network.
How do I install Nmap on Linux?
To install Nmap on Linux, you can use the package management system of your distribution. For example, on Ubuntu or Debian-based systems, you can run the command "sudo apt-get install nmap" to install Nmap. On Red Hat or CentOS systems, you can use the command "sudo yum install nmap". Alternatively, you can download the source code from the official Nmap website and compile it manually.
What are the basic command line options for running Nmap?
There are several basic command line options you can use when running Nmap. One of the most common is "-sn", which stands for "ping scan" and is used to discover live hosts on a network. Another commonly used option is "-p", which allows you to specify the ports you want Nmap to scan. For example, you can use the command "nmap -p 80,443 example.com" to scan for open ports 80 and 443 on the host "example.com".
Can Nmap be used for stealthy network scanning?
Yes, Nmap offers several options for stealthy network scanning. One of the most popular stealth scanning techniques is called "TCP SYN scan" or "half-open scan", which allows Nmap to bypass some types of network firewalls or intrusion detection systems. To perform a TCP SYN scan, you can use the command "nmap -sS target". However, it's important to note that stealthy scanning techniques may still be detected by some security systems.
Are there any graphical user interfaces available for Nmap on Linux?
Yes, there are several graphical user interfaces (GUIs) available for Nmap on Linux. One popular GUI is "Zenmap", which provides a user-friendly interface for running Nmap scans and analyzing the results. Zenmap allows you to easily configure scan options, view live scan results, and generate reports. It's a great option if you prefer a graphical interface over the command line.




